Introducing Forefront Network Inspection System (NIS) in TMG Beta 3 release
You may have had the opportunity to experiment with NIS when it was first released with TMG Beta 2 andich provies preliminary insights into the new technology provided technology preview of the new Network Inspection System. NIS is a protocol decode-based traffic inspection system that uses signatures of known vulnerabilities, to detect and potentially block attacks on network resources. TMG Beta 3 release is the first release in which NIS provides comprehensive protection for Microsoft network vulnerabilities, researched and developed by Microsoft Malware Protection Center - NIS Response Team, as well as an operational signature distribution channel which enables dynamic signature snapshot distribution.
What is the motivation behind NIS?
As information worker users increasingly find it more difficult to achieve anytime anywhere access in a re-perimeterized world, ubiquitous and comprehensive protection for the “outbound access” scenario is paramount. Outbound access is defined as user initiated network access whether it is the Internet or corporate network regardless of application or protocol. End users are predominately accessing the Internet using a web browser which creates an easy attack surface for malicious hackers. The nature of the web demands unique protections around protocol vulnerabilities, including the frequently used HTTP and HTTP/s protocols as well as other protocols such as RPC, SMB and the different mail protocols. Forefront Network Inspection System (NIS) is Microsoft’s response to this new and growing IT concern. In its first release NIS is integrated with Threat Management Gateway (TMG) as a component of its Intrusion Prevention System (IPS) offering.
Motivated by the large number of application-level protocols and new ones constantly emerging, Microsoft Research (MSR) have architected a Generic Application-level Protocol Analyzer (GAPA), consisting of a protocol specification language (GAPAL) and an analysis engine that operates on network streams and traces. GAPA allows rapid creation of protocol analyzers, greatly reducing the development time needed (See the MSR research paper: http://research.microsoft.com/pubs/70223/tr-2005-133.pdf ). In TMG, we have implemented NIS based on the GAPA research as a signature-based Intrusion Prevention System (IPS).
As we are seeing increasing number of zero-day attacks at the network and application layer, we are constantly looking for ways to protect hosts and networks against exploitation of the discovered vulnerabilities.
One of the key problems is that attackers can usually develop and use exploits for the disclosed vulnerabilities faster than software vendors can develop patches and customers can deploy the patches. Reviewing past vulnerabilities shows that it can take up to a month from the initial attacks reports to develop and release patches, and on top of this another 1-2 weeks for the customer to deploy the patch across the vulnerable computers. This leaves computers for over a month vulnerable to attacks and exploitation. As stated, NIS is a signature-based IPS leveraging the GAPA technology for the purpose of developing and deploying vulnerability-signatures. The main purpose and value proposition of NIS is to close the vulnerability window between vulnerability disclosures and patch deployment from weeks to few hours.
What is so special about NIS?
NIS main differentiator is Signature Quality (minimum False Positive and False Negative) on Microsoft focused vulnerabilities. NIS vulnerability signatures (versus exploit based) cover all flavors of exploit attacks leveraging vulnerability in contrast to exploit specific detections which are susceptible to evasion.
Microsoft assets (Operating Systems and Application) may be extremely important to protect. Therefore, even if you have existing IPS solution, we encourage NIS deployments as first or second line of defense to strengthen MS assets protection.
One important and not obvious benefit for using NIS is protection for retired OS and applications. Once a product is retired (not supported by Microsoft) it is not supported for security patches (See Microsoft’s Support Lifecycle pages for details). Recently, Windows Server 2003 Service Pack 1 was retired - on April 14, 2009. The Conficker for instance attacked un-patched machines, as well as many older versions of Windows for which patches are not available. The only way to protect retired OS and applications is by using Virtual Patching such as NIS.
Following are a few samples of NIS Signatures Protection on Microsoft Malware Protection Center Security Portal:
Well, now all that is left to do is to enable NIS on TMG Beta 3 and try it out!
Enabling NIS through the NIS IPS – Property Configuration Pane:
Just click on Configure Properties the main NIS Property Configuration Pane.
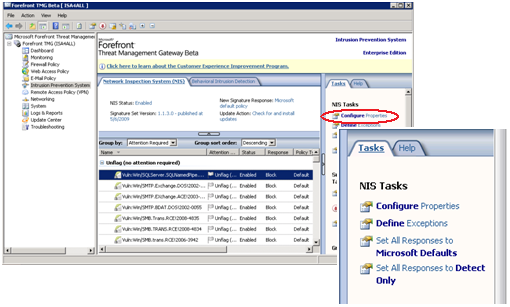
Check Enable NIS à you are ready to go!
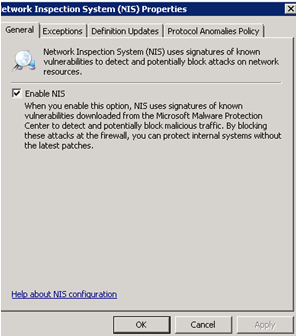
Basically, NIS comes with a pre-defined recommended policy out of the box – this is the recommended configuration for NIS. The NIS Response Team set the Recommended Policy based on multiple factors including the vulnerability severity, business impact, Signature Category and others. We will leave this discussion for another blog including detailed NIS configuration blog. The NIS Response Team may change the recommended policy automatically through signature snapshot update. You may note in Beta 3 lifecycle, that gradually most signatures that are set to "Detect Only" will be updated to “Block” mode once we gain confidence in them. With that said, though NIS supports granular control and policy configuration, we recommend in Beta 3 to enable NIS in Microsoft Recommended mode.
You can choose to Enable or Disable NIS at anytime. If you choose to Disable NIS, your policy configuration (signature overrides, new signature policy, exception list etc) are saved. Once you enable NIS you are up and running again with no further action required.
What’s next?
Please look for our upcoming blog entries and whitepapers planned for the near future discussing NIS deployment, configuration, monitoring and troubleshooting in depth.
Authors:
Avi Ben-Menahem, GAPA Group Manage – Forefront TMG
Moshe Golan, GAPA Program Manager – Forefront TMG