Unable to Change Password through ISA Server 2006
Before we go through this specific scenario it is important to remember some good references on how to troubleshoot issues related to change password feature on ISA Server:
1. The "change password" feature does not work as expected after you install ISA Server 2006 Service Pack 1
http://support.microsoft.com/kb/957859
2. Configuring and Troubleshooting the Password Change Feature in ISA Server 2006
http://technet.microsoft.com/en-us/library/cc514301.aspx
3. Troubleshooting Forms Base Authentication using Secure LDAP Authentication on ISA Server 2006
http://technet.microsoft.com/en-us/library/dd316279.aspx
2. Current Scenario
For this specific issue the scenario was:
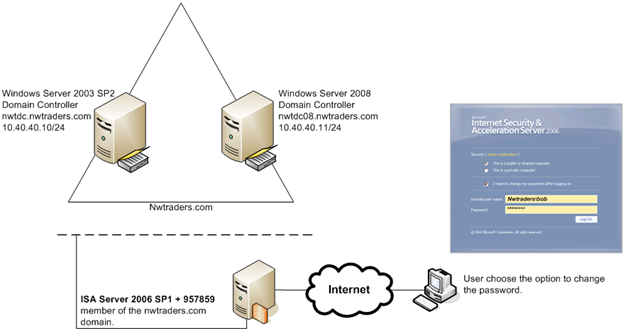
Figure 1 – Environment with Windows Server 2003 and 2008 DCs.
Users that were created while the domain just had Windows Server 2003 could change their password without any problem. New users, created after the promotion of a new Windows Server 2008 were unable to change their password. Any user created physically on the Windows Server 2003 DC or Windows Server 2008 DC were affected at that point.
2. Troubleshooting
Using the troubleshooting techniques that the articles mentioned in the begining of this post has, we were able to see in the traces (using ISA Data Packager – parsing isalog.bin file) that when the change a new user tried to change his password the error received was 8000500D, which translates to E_ADS_PROPERTY_NOT_FOUND.
Note : you can download the ERR.EXE tool from http://www.microsoft.com/downloads/details.aspx?familyid=be596899-7bb8-4208-b7fc-09e02a13696c&displaylang=en to review HEX errors.
The error was happening when reading the attribute msDS-User-Account-Control-Computed from this new account. We registered the schema management supporting dll, schmmgmt.dll (regsvr32 schmmgmt.dll) to review the schema. After reviewing we confirmed that the attribute was there. This means that ISA probably didn’t find the attribute for this user account because of a lack of permission. Reviewing the permissions from an account that can change the password and a new account that cannot change the password we notice some differences.
3. Solution
Through troubleshooting we had discovered that the group “Pre-Windows 2000 Compatible Access Security Group” was missing the “Nt Authority\Authenticated Users” (found by looking at Active Directory Users and Computers with the advanced features view, in the “ForeignSecurityPrincipals” container). The group also did not contain the “Everyone” or “Anonymous Logon” which would have given the proper permissions for the ISA machine to read the User attributes.
The “Pre-Windows 2000 Compatible Access Security Group” contains the “NT Authority\Authenticated Users” by default which is referenced here: http://technet.microsoft.com/en-us/library/cc779140.aspx
Note 1:
Both Everyone and Anonymous are members of Pre-Windows 2000 Compatible Access group by default in Windows Server 2003. This is true if the domain was built with the following selection during the creation of the domain:
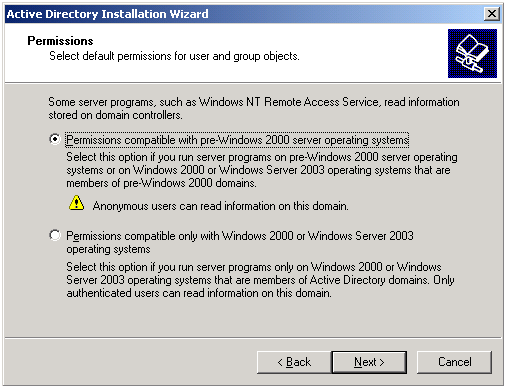
Figure 2 – Option used during the domain promotion.
Security group “Pre-Windows 2000 Compatible Access” properties with the above selected:
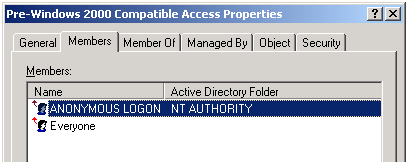
Figure 3 – Members of this group in this case.
Note 2:
If the Domain was built with the following option during the domain creation the following are the defaults:
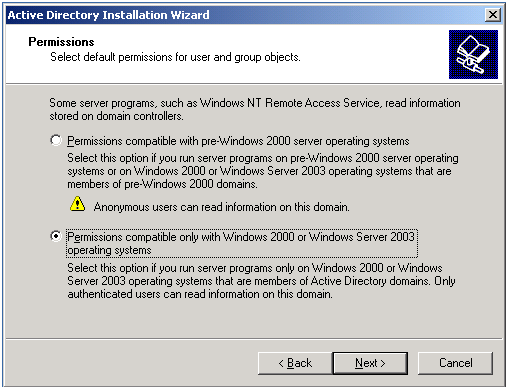
Figure 4 – Second possible option.
Security group “Pre-Windows 2000 Compatible Access” properties with the above selected:
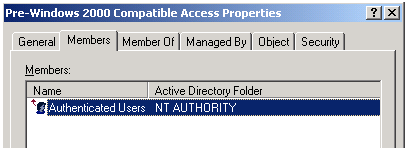
Figure 5 – Group membership when this second option is in use.
To add the “NT Authority\Authenticated Users” to the “Pre-Windows 2000 Compatible Access” group:
· Open Active Directory Users and Computers
· Select the “Advanced View” from the view menu
· Locate the container “ForeignSecurityPrincipals
· Open the “NT Authority\Authenticated Users” group and select the “Member Of” tab
· Select “Add” to include the “Pre-Windows 2000 Compatible Access” group
In the scenario described above, it was determined that the “Authenticated Users” was a better selection to add due to security.
Authors
Yuri Diogenes
Security Support Engineer
Microsoft CSS Forefront Edge Team
Bob Drake
Sr Technical Lead
Microsoft Directory Services Team
Technical Reviewers
Vic Singh Shahid
Escalation Engineer
Microsoft CSS Forefront Edge Team