Using Kerberos Event Logging for Troubleshooting ISA KCD Issues
Introduction
I see a fair amount of ISA Server cases where customers are using Kerberos Constrained Delegation (KCD). In a nutshell, KCD allows published Web servers to authenticate users after ISA Server has identified them using a non-Kerberos authentication method. A common method is to issue your users SSL client certificates which would be presented to the ISA Server for authentication. Once ISA Server verifies the identity it is not allowed to pass the SSL client certificate directly to the published Web server. It can, however, impersonate the user and obtain a Kerberos service ticket used for authenticating the user to the published server. For a very detailed description of Kerberos Constrained Delegation in ISA Server 2006 please refer to http://technet.microsoft.com/en-us/library/bb794858.aspx and another good reference to troubleshooting KCD can be found at http://download.microsoft.com/download/1/e/e/1ee86ce4-8234-4aa1-94f4-a37039837729/Troubleshooting_Kerberos_Delegation.DOC
A Generic 403
In a recent case I had the customer was getting an “HTTP Error 403 – Forbidden” when trying to access OWA published through ISA Server using KCD. The user was initially prompted for their SSL client certificate and after choosing it they would get an error in their web browser (See Figure 1).
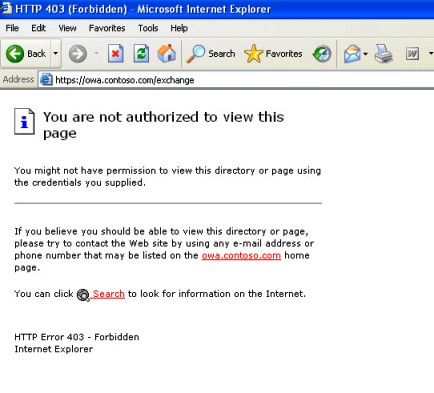
Figure 1
The usual network traces didn’t give a clear picture of exactly what the problem was with authentication. This particular ISA Server was working up until about a week prior. Something had changed and was now causing authentication to fail. For additional clues I decided to enable Kerberos Event logging on the ISA Server itself. For instructions on how to do this please see the following KB http://support.microsoft.com/kb/262177
The Culprit
With Kerberos Event Logging enabled we tested again using the client. I was now seeing some Kerberos errors show up in the Event Viewer (See Figure 2).
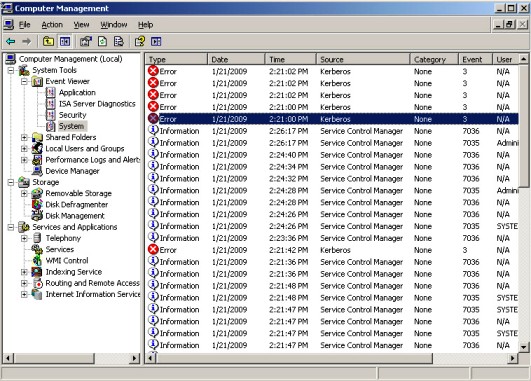
Figure 2
There was one error message that was particularly interesting (See Figure 3).
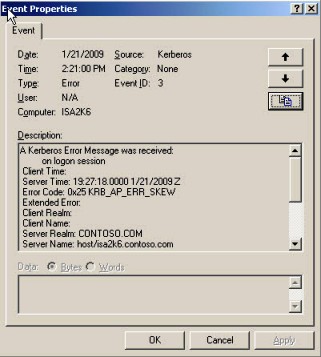
Figure 3
According to KB230476 the error KRB_AP_ERR_SKEW means:
“…a client computer sends a timestamp whose value differs from that of the server’s timestamp by more than the number of minutes found in the Maximum tolerance for computer clock synchronization setting in Kerberos policy.”
I found that it related to time skew between the ISA Server and the DC. It was greater than 5 minutes in this case which would definitely cause an issue with Kerberos. We corrected the time and the client was able to successfully authenticate again.
Conclusion
Troubleshooting web servers published through ISA Server using Kerberos Constrained Delegation (KCD) can sometimes be tricky. We need to use all of the tools at our disposal to quickly diagnose and fix these issues. In this article I showed you how to enable Kerberos Event Logging to assist you in this diagnosis.
Author
Keith Abluton
Security Support Engineer
Microsoft CSS Forefront Security Edge Team
Technical Reviewers
Billy Price
Security Support Engineer
Microsoft CSS Forefront Security Edge Team
Yuri Diogenes
Security Support Engineer
Microsoft CSS Forefront Security Edge Team