Account lockout not working using UPN format to logon with forms-based authentication in ISA Server 2006
1. Introduction
Recently we received a support call from a customer saying that one of his network users was able to logon on to a secure web site published by ISA Server 2006 after typing a wrong password five times and finally typing the correct password on the sixth attempt. The account lockout policy for his company was set up to accept four attempts before it locks up the user account. This was an alert for his security staff since it could expose the page to a password brute force attack.
After assessing the environment we also noticed that if he typed the user account using domain\username such a thing did not happen and the account correctly locked up. The only way to bypass the account lockout policy was using the UPN (User Principal Name) to logon.
2. Environment
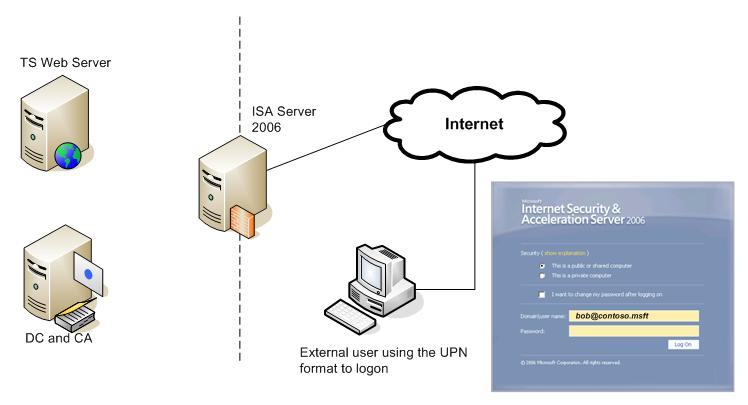
We were able to reproduce the problem in a lab. The lab was set up like this:
Figure 1 – Lab used to simulate the behavior.
As you can see in the lab above we were using the secure forms provided by ISA Server. In figure two we have the Web server publishing rule:

Figure 2 – ISA Server Rule
This rule uses a Web listener that uses LDAP authentication to validate the user’s credentials as shown below:
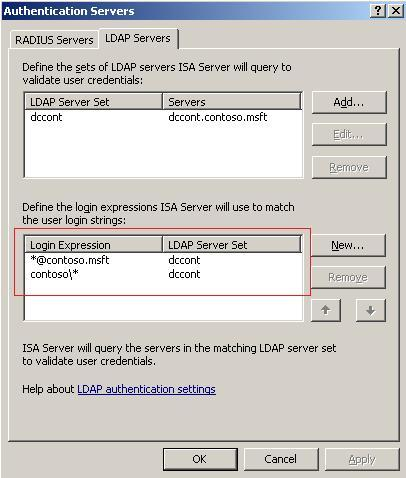
Figure 3 – LDAP Components
In Login Expression we have both formats available: SAM Based and UPN Based.
For more information on the LDAP configuration see the article Secure Application Publishing on Microsoft Technet.
3. Understanding the Logon Process
To better understand the logon attempts we enabled the netlogon logging on the domain controller. To do this run the following command on the Domain Controller:
nltest /dbflag:0x2080ffff
3.1. Using the SAM Account Name
When the user Bob tries to logon with the ISA Server 2006 Secure Form using the domain\username format and types the wrong password the following event is recorded on the netlogon log:
11/20 21:19:34 [LOGON] CONTOSO: SamLogon: Network logon of contoso\bob from ISACONTN2 Entered
11/20 21:19:34 [LOGON] CONTOSO: SamLogon: Network logon of contoso\bob from ISACONTN2 Returns 0xC000006A
11/20 21:19:40 [LOGON] CONTOSO: SamLogon: Network logon of CONTOSO\Administrator from DCCONT Entered
11/20 21:19:40 [LOGON] CONTOSO: SamLogon: Network logon of CONTOSO\Administrator from DCCONT Returns 0x0
11/20 21:19:40 [LOGON] CONTOSO: SamLogon: Network logon of contoso\bob from ISACONTN2 Entered
11/20 21:19:40 [LOGON] CONTOSO: SamLogon: Network logon of contoso\bob from ISACONTN2 Returns 0xC000006A
11/20 21:19:45 [LOGON] CONTOSO: SamLogon: Network logon of CONTOSO\Administrator from DCCONT Entered
11/20 21:19:45 [LOGON] CONTOSO: SamLogon: Network logon of CONTOSO\Administrator from DCCONT Returns 0x0
11/20 21:19:45 [LOGON] CONTOSO: SamLogon: Network logon of contoso\bob from ISACONTN2 Entered
11/20 21:19:45 [LOGON] CONTOSO: SamLogon: Network logon of contoso\bob from ISACONTN2 Returns 0xC000006A
The error code 0xC000006A means that the value provided as the current password is not correct. After four attempts (which was the company policy) we have the following event on the netlogon log:
11/20 21:19:51 [LOGON] CONTOSO: SamLogon: Network logon of contoso\bob from ISACONTN2 Returns 0xC0000234
The error code 0xC0000234 means that the user account has been automatically locked. Also we have the event below on the Event Viewer:
Event Type: Success Audit
Event Source: Security
Event Category: Account Management
Event ID: 644
Date: 11/20/2007
Time: 9:19:45 PM
User: NT AUTHORITY\SYSTEM
Computer: DCCONT
Description:
User Account Locked Out:
Target Account Name: Bob
Target Account ID: CONTOSO\Bob
Caller Machine Name: ISACONTN2
Caller User Name: DCCONT$
Caller Domain: CONTOSO
Caller Logon ID: (0x0,0x3E7)
3.2. Using UPN Format
When the user Bob tries to logon into the ISA Server 2006 Secure Form using the username@domain format and types the wrong password the following event is recorded on the netlogon log:
11/20 21:22:04 [LOGON] CONTOSO: SamLogon: Network logon of (null)\bob@contoso.msft from ISACONTN2 Entered
11/20 21:22:04 [LOGON] CONTOSO: SamLogon: Network logon of (null)\bob@contoso.msft from ISACONTN2 Returns 0xC0000225
The error code that it is recorded in this scenario is not 0xC000006A, instead we log 0xC0000225, which means STATUS_NOT_FOUND. Even when typing the incorrect password we do not lock the user account and the reason is because the number of unsuccessful logon attempts is not incremented by the authenticating domain controller.
4. How to Fix It
This is actually a problem already fixed in Windows Server 2003 SP2, however if you did not apply this recommended Service Pack yet you can apply the hotfix below to address this specific issue:
921063 Unsuccessful authentications are not counted as incorrect password logon attempts when you use the IADsOpenDSObject::OpenDSObject method to specify a UPN in a Windows Server 2003 domain http://support.microsoft.com/default.aspx?scid=kb;EN-US;921063
Note: make sure to also apply on the domain controllers.
Yuri Diogenes
Security Support Engineer – ISA Server Team
Microsoft Texas