A Developer’s Brief Introduction To Network Administration (part 2)
In part one Dave McMahon looked how developers should acquire the basics of IP networking – an understanding of IP addresses, default gateways and subnet masks, here he looks at other building blocks of TCP/IP network design
Command Line Utilities
Command line utilities will begin to take over your life as a network admin. The IT Pro guys do seem to love them, and to be honest they are normally pretty good and very flexible. I guess they are pretty cheap to produce too relative to their GUI counterparts! So let's look at a few:
- Ping. This is used to test for IP connectivity between machines. Some firewalls block this call, so it may not always work or give reliable results. If your DNS is working properly this should also resolve any domain names you try to ping.
- Ipconfig. This is used to configure your network settings on the local machine. There are a number of options available. One option which is very useful if you are configuring or changing and Domain Naming Services settings is /flushdns. This empties the local DNS cache so that if you have changed any DNS settings they will be correctly refreshed.
- Tracert . This is useful for seeing where you traffic goes once its left your machine. For a useful article on how to use this utility checkout http://www.windowsnetworking.com/articles_tutorials/Using-Tracert.html
- Route. This is used to view the Windows Routing Table and to add /edit and remove entries from it.
- Nslookup – a sort of do-it-yourself DNS, type in a domain name and it will give back information about the host name server.
All of the above are used for working with TCP/IP. For a comprehensive listing of the utilities and their options see http://www.microsoft.com/resources/documentation/windowsnt/4/server/reskit/en-us/net/sur_util.mspx?mfr=true
Other Useful Tools
The Windows Event Log. This is probably your prime source of information about problems on the network. Basically the less red error icons you see the better. So whenever I have time, I have a trawl through the event logs and set about getting them eliminated. The links to KB article from the event log entries are getting better all the time and I have found about 60-70% of the time the actions recommended have solved the problem.
Performance Monitor. A great tool for logging the general performance of machines on the network. A short and simple article on setting up basic benchmarking can be found here: http://techrepublic.com.com/5102-10878-1060425.html
Task Manager. Don't forget the Task Manager (Cntl + Alt + Del)as a great 'snap-shot' tool for seeing how your machines are performing.
OK so that's some basics, let's have a quick look at some network design. Once again this is not a rigorous treatment, but should give you some practical pointers.
Designing Your Network
If you have the opportunity, you should design your network first, this is where your IT Pro friend can really help. If you inherit a network, you should map it out, and also I would recommend you mapping out how you would like the network to look. How do you start to design your network? Very simply, you should decide what services you require on your network. Probably some of the general services you want are:
- Security Control of Users and Computers
- Organisation of Users and Computers
- Internet Access
- Backup
- Remote Access (Virtual Private Network)
If you host your own web-site you may well want
- Web Hosting
- Database Services
As a result of wanting some of the above services you will find that you need the following:
- Active Directory Services AD)
- Domain Naming Services (DNS)
- Dynamic Host Control Protocol (DHCP) Services
- Anti-Virus Services
- Firewall Services
- Web Proxy Services
- Routing and Remote Access
Tip No 3: When starting out decide what user services you need to provide. This will invariably drive the 'shape' of your network
Let's consider a few scenarios. If you don't host a web site you may just want a simple internal/external network where a firewall protects you from unwanted traffic from the internet. You may still decide to do this option even if you have a web-site as it is a very simple setup. Be aware that running a web-site which allows anonymous access is a potential security loophole, if a hacker manages to break your web application the chances are he/she will gain at the least, some access to your internal network.
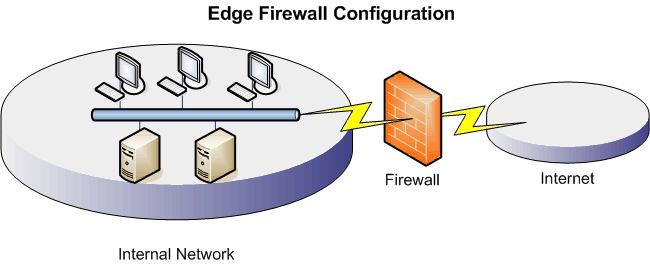
If you host a web site you will probably want to set up what is known as a De-Militarized Zone as shown simplistically below. This allows you to protect you web-sites but keep them separate from your main domain, thus if the website security is breached, further barriers protect your main network.
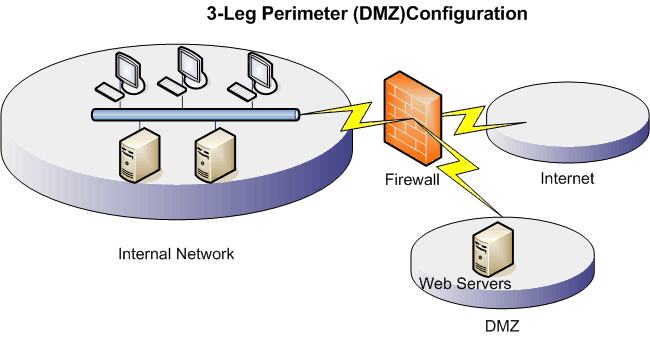
From the diagrams you can see that you have options and many more exist. As this is a brief run through, I won't dwell on the finer details check out the TechNet and other websites for articles on network design.
Controlling and Coordinating the Network
To control and coordinate the network and all the above services, I would recommend using a service known as Active Directory Services, and in order to make use of this service on the Windows platform, you should run your computers within a domain. I say 'should'. You don't actually need to, you can run some of these services without a domain, but using Active Directory does make things easier and more secure, if administered properly.
AD uses a protocol called the Lightweight Directory Access Protocol (LDAP) which is not a Microsoft specific technology and allows interaction with other LDAP based Directory Services. An overview of Active Directory is at: http://technet2.microsoft.com/WindowsServer/en/Library/6f8a7c80-45fc-4916-80d9-16e6d46241f91033.mspx?mfr=true
To install Active Directory you need to 'promote' one or more of your servers to be Domain Controllers (DCs). For a small network, one DC should suffice, but you can have more. One DC is always designated the Operations Master (OM), which is not the overall controller but is the overall master as far as replication of AD schema changes (alterations to computers, users, groups etc) goes.
To find out how you install active directory. Check out http://www.petri.co.il/how_to_install_active_directory_on_w2k.htm for installing a DC in a Windows 2000 based domain, and http://www.petri.co.il/how_to_install_active_directory_on_windows_2003.htm for installing a DC on a Windows 2003 based domain.
If you are installing Windows 2003, it is recommended that you do so with SP1 already included. SP1 enables Windows Firewall until all the relevant Post Setup Security Updates (PSSU) have been installed, thereafter it is deactivated until activated by you configuring the server. Having had a frustrating 2 to 3 days battling blaster viruses getting onto a clean Windows 2003 Server before I could get the updates downloaded, I can say from experience this really is a 'Best Practice'.
Domain Name Services (DNS)
During the promotion to a domain controller, you will be prompted to install Domain Name Services if they are not available. What do Domain Name Services do? DNS naming is used in TCP/IP networks, such as the Internet, to locate computers and services through user-friendly names. IP numbers are not that easy to remember really and it's far better to have computers with easy to remember names such as OFFICESERVER or DEV1SERVER for example. Extend that out to publically viewable web-sites such as www.microsoft.com, www.google.co.uk, www.amazon.com. These are all recognisable names and easy to remember. What DNS is to translate those names into IP addresses and vice-versa in order that we as humans can more easily interact with multiple distributed computers. So DNS does name resolution. DNS is one of the key fields in network administration that you should master to some degree as a good percentage of the network problems you will need to solve will come down to DNS name resolution issues.
An overview of the DNS on Windows 2003 is at http://technet2.microsoft.com/WindowsServer/en/Library/726b7340-198c-488d-aeb4-c2f8ed24f8581033.mspx?mfr=true
Tip No 4: Get at least a passing knowledge of how DNS works, as a great majority of issues you are likely to come across will be DNS related
Dynamic Host Control Protocol (DHCP)
One other thing you will need early on is the installation of Dynamic Host Control Protocol (DHCP) Server for your internal network. If you have a smallish network, then you can install this on the same server as your domain controller and DNS. Be aware however that a number of events may appear in the event log which you should rectify by carrying out the recommended action in the relevant KB articles.
What does DHCP do? It issues out IP addresses to machines in your network and to other devices that request one. DHCP is pretty easy to setup, and can be used to centrally configure what IP, subnet, default gateway and DNS servers get assigned to client machines. It can also serve up a different set of settings for those clients connecting to the network via a Virtual Private Network (VPN). You may for instance decide that all your internal workstations will have IP addresses in the range 10.0.0.1 to 10.0.0.255 and set the subnet mask for all the internal machines to 255.255.255.0. Check out the following reference for how to configure DHCP http://technet2.microsoft.com/WindowsServer/en/Library/283b8068-3568-48e3-b03b-a74c3898b1191033.mspx?mfr=true