techdays follow-up: remote powershell, what’s encrypted?
Yesterday Scott Schnoll and I had the honor to deliver a one-day pre-conference fully dedicated to the wonderful world of Microsoft Exchange 2010.
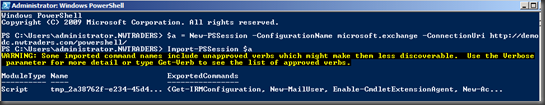
A few questions came up during and after the sessions, and one of them came from Tom De Caluwé who was interested in seeing how secure Remote PowerShell is. During my talk on Managing Exchange, I gave a demo on how you can use PowerShell v2, and connect to your Exchange server by establishing a persistent connection to it using the cmdlet new-pssession, as shown in the figure below:
$a = New-PSSession –ConfigurationName microsoft.exchange –ConnectionUri http://<FQDN of your CAS Server/powershell/
Import-PSSession $a
It is save to connect using http, since you use Kerberos encryption. Tom was interested in knowing what was encrypted, if the entire session was encrypted, or just the initial setup.
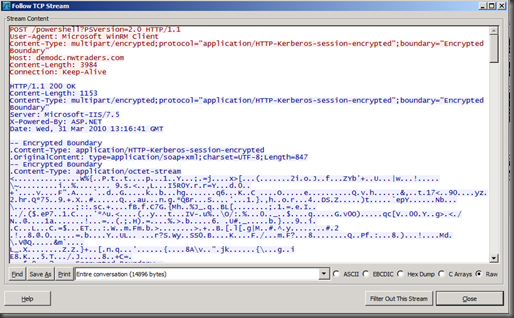
To make sure, we sat down, and used a network monitoring tool to see what happens when connecting to Exchange from another domain-joined machine using Remote PowerShell.
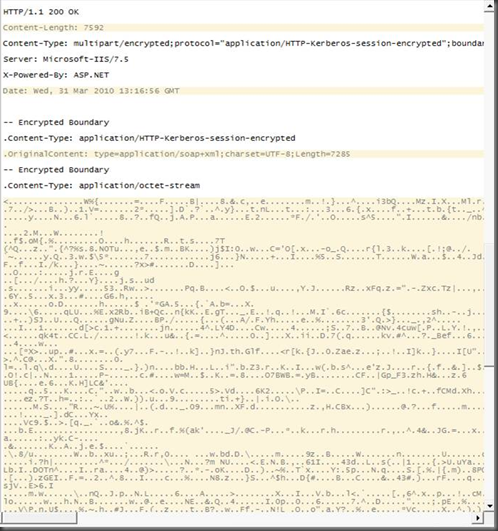
After establishing the persistent connection to my Exchange 2010 Client Access server named demodc.nwtraders.com, we decided to create a mailbox-enabled user called Bumbalu, and this is what the sniffering gave us:
Looking at the output, it was clear that the session was HTTP-Kerberos-session encrypted :-)
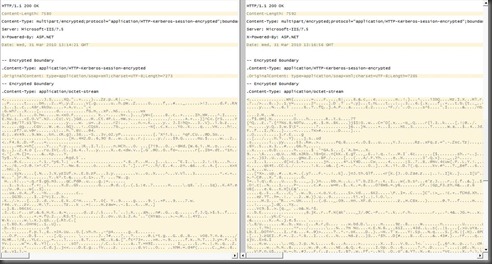
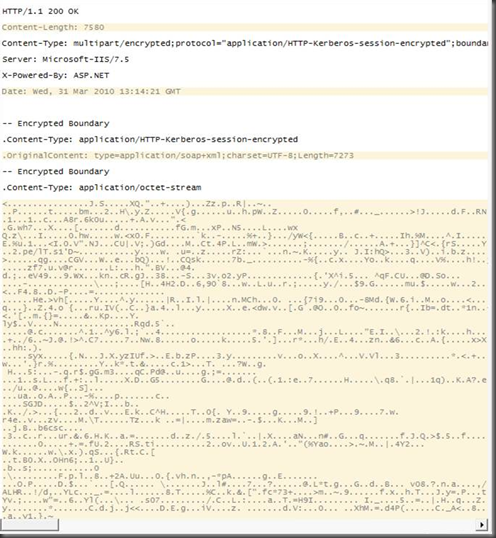
Just as a double-check, we removed our user Bumbalu and we created it again, with a different password (all the rest was the same).
And then Tom used a tool to compare both sniffer results and the differences between the two streams came down to:
- different time
- different content-length
- different content all-together :-)
Remote PowerShell rocks :-)
Ilse