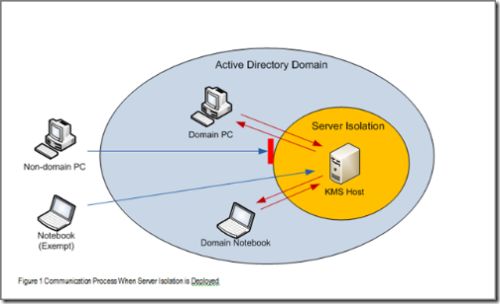
Using Server Isolation to Protect Your KMS Servers
Did you know that you can use a targeted IPsec-based Isolation solution to help reduce the risk of unauthorized access to your Key Management Service (KMS) Servers?
Yup. It's true. This is a great example of using "Server Isolation" as a means to add granular network access controls and end-to-end host authentication to critical services and applications. Think of it as a mini-virtual network that doesn't require any mucking around with your switches or router ACLs.
Like Domain Isolation, it leverages IPsec policies and credentials managed and distributed via Active Directory.
Well, let's cut to the chase...here a link to the IT Pro white paper that includes step-by-step guidance on using "Server Isolation with IPsec and Active Directory to secure access to KMS hosts, and provides step-by-step guidance for deploying such a solution on Windows Vista, Windows Server “Longhorn” or Windows Server 2003."
Using Server Isolation to Protect the Key Management Service (KMS)
If you've been curious about how IPsec-based solution scenarios -- like Server and Domain Isolation -- can work in your organizations, but were concerned about the wider scale impact to your network, solution scenarios like the one outline in the aforementioned white paper are a great place to start. Service Isolation of your KMS servers offers you a way to get your "hands dirty" with IPsec, deliver immediate value, while not "biting off more than you're ready to chew."