Joint IPv6 White Paper Scales to 256-Bit Length Addresses
Okay, that was a little bit sensational, if not an outright fib.
What's no joke is a newly published joint white paper Juniper Networks and Microsoft have co-developed to talk about deploying end-to-end IPv6 scenarios.
Heck, we felt that whole end-to-end bit was such a good thing we named the white paper after it (which you can find here):
Enabling the Next Generation of Networking with End-to-End IPv6
In addition to us lackeys from the product groups, we had folks from the US Federal/public sector teams at both Juniper and Microsoft collaborate on this paper to ensure it spoke to the requirements that you folks in the federal agencies and related industries are facing as you seek to deploy IPv6.
Hey, how are those deployments going, by the way?
Here's a sampling of the white paper brought to you by way of the infamous executive summary:
As connectivity converges and develops ubiquity many devices are added to the Internet. This trend has created projections of address shortages. Internet Protocol version 6 (IPv6) has promised a solution to this issue. In this paper, Microsoft and Juniper combine their leading networking knowledge to show customers how to adopt IPv6 technology. The paper first looks at the changing expectations of IPv6 with the growth of IPv6-enabled applications like Microsoft Windows Meeting Space in Windows Vista. Next the paper discusses the relationship of each component in an IPv6 implementation. The paper closes with some suggestions on functionality, equipment and deployment scenarios that highlight key aspects of a robust end-to-end IPv6 transition.
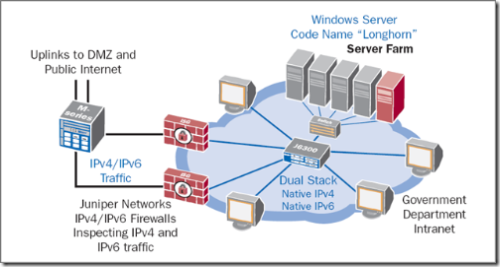
As the summary mentions, the white paper covers off a bunch of flexible deployment strategies that leverage transitional technologies baked into Windows Vista and Windows Server "Longhorn" to full blown dual-stacking Juniper gear working in concert with the native IPv6 support in the aforementioned Windows releases (like the graphic below illustrates).
STOP THE PRESSES! DID YOU ACTUALLY THINK YOU'D GET AWAY WITHOUT GETTING AN IPsec PITCH? SUCKER!
I'll admit the above was a bit silly, if not juvenile, but this is the little fun I get to have blogging offline while drinking horrific coffee cruising at 35,000 ft en route to Los Angeles to support the big joint Forefront/System Center launch on Wednesday.
Well, back to the IPsec pitch. As you all know, my day job is minding the Internet protocols suite in Windows Server. Since there are way too many to count on the knurled fingers of the guy siting next to me (yeah, this dude was chewing and picking at his nails for a good 30 minutes until we took off and the engine noise lulled him to sleep), we primarily focus on a few key ones that enable our major networking scenarios (like Server and Domain Isolation and NAP which uses IPsec).
I happen to think IPv6 migration is a pretty significant scenario that can also benefit from the cost-effective end-point authentication features of IPsec (as it was originally intended and realized with IPv6). I also happen to know that IPsec can potentially introduce a full list of interoperability challenges that you may not wish to tackle. We're trying to work out how to strike the right balance between true end-to-end host authentication (not just at the network on ramps) while still preserving the network management and optimization features you've deployed are will consider deploying (say, WAN optimization).
Well, it's important to look to the larger challenges (and risks) you are looking to address and we could certainly use your feedback to make sure we drive the right set of features into the platform and through our partner eco-system. I'm not going to reiterate the IPsec makes IPv6 better pitch, since I already blogged on this many times. Instead, I ask you to share your thoughts about how you think IPsec can help make your future IPv6 work more secure and scalable.
Well, time to close up since we're about to land at LAX. Hope to see you at the launch event on Wednesday!