Windows Server 2016 - What's new for Service Providers
Windows Server 2016 is finally released, and it's a breakthrough version of Microsoft's server operating system. Windows Server 2016 is packed with great new features, that make it the best-in-class IaaS platform, the most secure Windows Server ever, and the best platform for Windows-based microservices. In this series I will write about new features in Windows Server 2016, that can be valuable for Service Providers and Hosters. The first post is a high-level overview of the new features, and in the next posts I will uncover more details of the most important enhancements.
Windows Server 2016 is the part of the overall IaaS solution, which sometimes called "Microsoft Datacenter vNext". That solution also includes System Center 2016 for management and operations purposes, and Windows Azure Pack for tenant cloud experience. Yes, we are still talking about the Azure Pack (WAP), and this story is a little bit parallel to Azure Stack story. System Center 2016 was released on the same day with Windows Server 2016, and current version of Azure Pack already supports Windows Server 2016.
There are 2 perspectives of Windows Server 2016: Windows Server on the host and Windows Server inside the Guest VM. I understand that the majority of service providers still run non-Hyper-V platforms for their IaaS solutions, but it doesn't meant that new Windows Server 2016 features won't be valuable for them. Yes, some of the features require Hyper-V on the host to be used, but the majority of features is hypervisor agnostic.
Windows Server 2016 on the Host
If service provider currently uses Windows Server 2012 R2 (or earlier) to provide IaaS services, then Windows Server 2016 upgrade will definitely be a great choice, because it will introduce new features for tenants, reduce the total cost of ownership, make IaaS solution more reliable and robust, and it will increase the overall security of the infrastructure. Service Providers, that use other solutions as IaaS platform, will also be able to achieve that.
Microsoft uses the idea of "Software-defined Datacenter", which is a next step from traditional Private Cloud to the solution, similar to what used in Public Clouds. In a concept of Software-defined Datacenter, the generic hardware can be used for IaaS, without the need to buy expensive proprietary hardware. Compute (virtualization layer), Network and Storage layers are managed by the software, which is Windows Server and System Center in our case. Let's look at the new features of Windows Server 2016, related to Software-defined Datacenter.
Software-defined Compute
Trendy term "Compute" when we talk about Software-defined Datacenter means the regular "virtualization" that you are already aware of. In our case Software-defined Compute layer is provider my Hyper-V. Windows Server 2016 Hyper-V (aka "Hyper-V 2016") compared to Windows Server 2012 R2 introduces these new great features:
- Nano Server - super-thin and light version of OS on Hyper-V hosts (I will talk about Nano Server later in this post).
- Increased Scale-limits - now you can run VMs with up to 240 virtual CPUs and 12Tb of RAM.
- New capabilities for Linux-based VMs, that were available only for Windows-based VMs before - Secure Boot, vRSS, Hot-add and resize for virtual disks, enhanced backup, PowerShell DSC.
- Nested Virtualization Support - now you can run Hyper-V VMs inside Hyper-V VMs. It can be valuable for lab scenarios.
- Production Checkpoints - new type of VM checkpoints (snapshots), that leverage VSS functionality inside guest VMs to assure app consistency of the checkpoint.
- NIC Hot-add - now you can add a network adapter to the VM without any downtime. It works for Generation 2 VMs only.
- Memory reconfiguration without downtime - now you don't need to shut down the VM to enable or disable Dynamic Memory, or if you want to change the amount of assigned Static Memory.
- PowerShell Direct - allows to send PowerShell commands directly to VM. Now you can manage the VM from the host's PowerShell environment and don't care about their network configuration.
- Discrete Device Assignment - allows to take some of the PCI Express devices on a host (GPUs, network cards etc.) and pass them through directly to a guest VM. This is actually much of the same technology that was used for SR-IOV networking in the past.
- Hyper-V integration components are now being automatically updated through Microsoft Update. This makes integration components update process much easier for service providers, because tenant can handle it itself.
- Shielded VMs - a new way to run tenant VMs in a secure way. Killer feature of Windows Server 2016 for service providers, unique for Hyper-V.
- Cluster OS Rolling Upgrade can be used to reinstall every Hyper-V host from 2012/2012R2 to 2016 without rebuilding the cluster. It reduces the complexity of the upgrade process and minimizes the downtimes.
Shielded VMs
Shielded VMs is a great new solution, that protects tenant secrets from service provider admins in a virtualized environment (IaaS/VDS). Some customers don't use service provider IaaS because they are afraid that their competitor will bribe service provider admin and ask him/her to copy the customer's VM to a shared resource. If service providers runs Windows Server 2016 or any other IaaS platform from our competitors (even the latest one), there is always a risk that fabric admin will copy the customer's VM on a flash drive (or upload it to OneDrive or similar service) and send it to customer's competitor to get some money for that. Competitor will be able to get all the data inside that VM - for example, CRM database with contacts of all customer's customers. Technically it can be done easily:
- Fabric admin has admin (root) rights on the virtualization hosts. It means that he/she can connect to VM using Console, change the bootloader or inject malware using hypervisor integration components. If you have Console access to Windows Server or Linux OS, you can easily change the password or local admin or root user and get full admin access in the VM. Rogue admin can reset the local admin password through Console Access and gather secret data from the VM.
- When you have access to VM virtual disk, you can inject any scripts into the VM. It will require a short downtime (1-10 seconds), and tenant will see that VM was unexpectedly rebooted. To hide this, rogue admin can do that trick during planned maintenance windows, and it won't look suspicious for tenant.
- Even if the VM virtual disk is encrypted, fabric admin can copy the VM to run it outside trusted environment. VM with encrypted disk is still a network member, and after running the VM on a malicious user laptop, it can be brute forced though the blazing fast virtualization but instead of LAN. Service Provider security systems won't detect that, because VM will run outside the service provider environment. With snapshots technology VM can be copied without any downtime, tenant won't be able to detect that. And copying a VM is super easy - you just need to copy a small VM configuration file, and a VM virtual disk file (or files).
- VM disk encryption usually adds complexity, because you can't provide TPM functionality inside the VM (before Windows Server 2016). Tenants will need to type secret keys to unlock the disk and boot the OS after every reboot. It also may reduce the performance of the VM because virtual CPUs will be loaded with encryption process.
- VMs in IaaS are usually created from templates or images. Rogue admin can inject a malicious script into the template, and customer's VM will be affected immediately after creation from the template/image. That malicious script can be run one day and send the customers secrets to the external location, owned by the rogue admin.
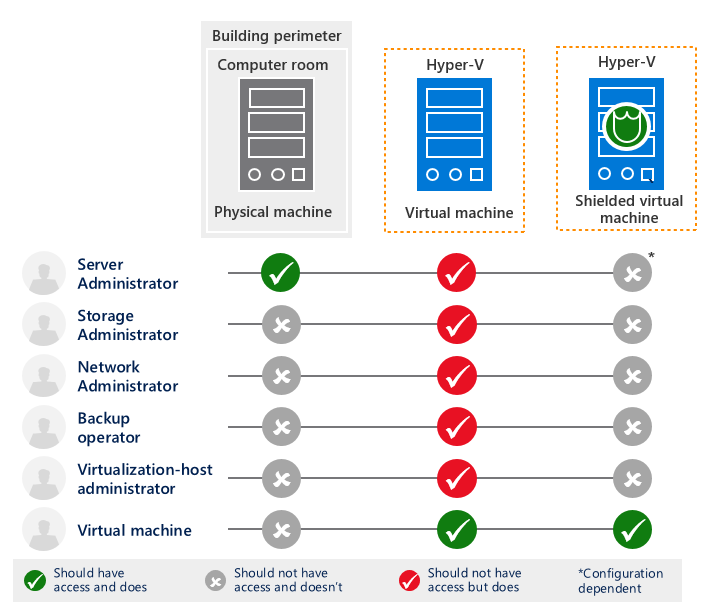 Shielded VMs is the ultimate solution to protect sensitive customer's data from all those risks. If provide several brand-new technologies in Windows Server 2016 for the comprehensive data security:
Shielded VMs is the ultimate solution to protect sensitive customer's data from all those risks. If provide several brand-new technologies in Windows Server 2016 for the comprehensive data security:
- Shielded VM Mode - disables some Hyper-V integration component capabilities, that may be used by rogue admins (PowerShell Direct, Console Access, Guest File Copy Integration Components).
- A hardened VM worker process (VMWP) that encrypts live migration traffic in addition to its runtime state file, saved state, checkpoints, and even Hyper-V Replica files.
- Host Guardian Service - separate service, owned by different unit in service provider organization. It checks the health of the host, where VM wants to run, and checks if it is allowed to run that VM on that host.
- Bitlocker encryption using vTPM - virtual TPM inside a VM, that is used to encrypt the virtual disk with a key, securely stored inside a TPM chip.
- Microsoft-based library of trusted images - tenant may be sure that they create VMs from images, provided to service provider by Microsoft, and that those images weren't changed (e.g. no malicious scripts were injected).
As you may see, Shielded VMs is the great solution to prove service provider potential customers that their sensitive data won't be stolen. Tenants have a choice on Azure Portal - create a VM using regular mode, or using Shielded VMs mode.
More details about Shielded VMs are available here.
Software-defined Network
Software-defined Network (SDN) was introduced in Windows Server 2012. It allowed fabric admins to create and manage isolated networks for different tenants without any network hardware configuration changes. Tenants could use Virtual Networks instead of Hardware-based VLANs, that provided the same level of isolation, but with rich self-service capabilities and without VLAN limitations. SDN allows network management and extensions from the software perspective.
Windows Server 2012 used NVGRE as a protocol for virtual network traffic encapsulation inside physical network traffic. System Center Virtual Machine Manager acted as an SDN brain and was responsible for configuration distribution among different Hyper-V hosts. Windows Server 2012 R2 introduces RRaS-based multi-tenant gateway that was used to provide external connectivity with Site-to-site VPN and NAT capabilities to tenants.
Service Providers, that used SDN based on Windows Server 2012 R2, usually provided a feedback, that our SDN solution was very complex to deploy, hard to operate, and that it wasn't fully compatible with their complex network configurations. Despite that, service providers agreed that SDN is a breakthrough comparing to traditional proprietary network solutions.
Windows Server 2016 solves all that issues with new SDN features:
- New role was added to Windows Server 2016 - Network Controller. Network Controller is the highly-available brain of you SDN. It manages the configuration changes and distribute them across Hyper-V hosts, gateways and routers. VMM is not required for SDN anymore. Network Controller dramatically simplifies the deployment and operations of SDN in a service provider environment, and that new architecture provides much better stability.
- VXLAN support - while NVGRE is still there, SDN in Windows Server 2016 uses industry standard VXLAN protocol for Virtual Network traffic by default. It allows SDN integration with existing traditional network solutions and other SDNs.
- Software Load Balancer (L4) - embedded solution to distribute network traffic at the cloud scale. It allows load balancing of any network traffic inside virtual networks, support HTTP/HTTPS probes, and works very similar to Azure Load Balancer. Great alternative to Microsoft Network Load Balancing (which was introduced in Windows Server 2003 and wasn't changed since then) and 3rd party expensive L4 and L7 load balancers. Also NAT capabilities were transferred from Multi-tenant gateway to the Load Balancer.
- Switch Embedded Teaming (SET) - teaming, embedded into Hyper-V Switch. As an alternative to Software Network Teaming (introduced in Windows Server 2012), SET adds network teaming capabilities directly into the Hyper-V switch. You don't need to separate RDMA networks from teamed networks, because SET supports RDMA. And because SET works much closer to the hypervisor, it can show better performance results.
- Datacenter Firewall
- GRE Site-to-Site VPNs
- Network Performance optimizations - even more network performance on modern 25/50/100GbE network interfaces with RDMA.
SDN in Windows Server 2016 can work it 2 modes:
- SDNv1 - the same SDN solution, that was used in Windows Server 2012 R2. It allows to quickly upgrade from Windows Server 2012 R2 to Windows Server 2016 without rebuilding the network architecture. It exists for backwards capability only and doesn't introduce anything new.
- SDNv2 - default SDN solution, if you build SDN from scratch in Windows Server 2016. All the new features, that I've described earlier, are available only in SDNv2. If you've just upgraded the hosts from Hyper-V 2012/2012R2 to 2016, then the next logical step is to re-deploy SDN as SDNv2.
Software-defined Storage
Storage is the very important part of IaaS solution, because virtual disks of the VMs need to be stored in a reliable location with the required level of performance. Windows Server 2016 works great with traditional storage systems, connected to hosts through Fiber Channel, FCoE or iSCSI. But there is a trend, that we see among service providers from different regions. They move from complex and expensive traditional storage systems to reliable software-defined storage (SDS) systems. Such systems are built on top of commodity server hardware and managed by the software. They allow to build performant and resilient storage solutions, packed with required modern storage features, but at the dramatically reduced price, comparing to enterprise storage systems.
Microsoft is not a new player on the software storage market. We started that journey in 2003 with Windows Storage Server 2003 . Some of the major storage features like deduplication were also added to traditional Windows Server 2012. Also Windows Server 2012 introduced a new way to build software-defined storage - Storage Spaces, as an alternative to traditional RAID arrays.
But Software-defined Storage (SDS) in Windows Server 2012 R2 had several disadvantages:
- Storage Spaces wasn't showing it's full performance out-of-the-box. It required a fine tuning of the disks, volumes and caching to work with a full speed. Also it was hard to troubleshoot issues with Storage Spaces, though a detailed troubleshooting guide was published for Windows Server 2012 R2.
- Storage Spaces required SAS disk drives for high-availability, which are more expensive then SATA drives.
- It was hard to scale-out the solution due to SAS but limitations.
- It was hard to limit disk IOPS for different tenants to protect from performance bursts. Storage QoS feature was added in Windows Server 2012 R2, that allowed to configure minimum IOPS (alert is generated if virtual disk can't get the amount of performance, specified in the threshold) and maximum IOPS (performance limit) values for a virtual disk. But those settings were dropped when VM moved to another host, and it was very hard to manage the Storage QoS configuration in a real-life service provider IaaS solution.
- 3rd party storage replication solutions were required to replicate storage data from one site to another. In real world service providers weren't using Windows Server 2012 R2 SDS because they've prefer all-in-one storage solutions from other vendors, which also included storage replication.
These issues are solved in Windows Server 2016 with new SDS stack:
- A new feature called Storage Spaces Direct (S2D) was added. S2D allows to build a reliable and fast storage, based on local disk drives. No need to use SAS anymore - just SATA SSD, SATA HDD and fancy NVMe SSD drives. S2D requires some drives on every host for caching (SATA SSD or NVMe SSD) and other drives for capacity. It supports mirroring, parity and erasure coding volumes. SDN is your SAN now, no need in expensive FC, FCoE or iSCSI solutions. Scale-out capacity and performance easily by adding new hosts with local drives into the cluster. 1 million IOPS can be easily achieved now, and even 5 million IOPS is not the limit. Storage Spaces Direct is a game changer in our SDS story and I will cover it in details in future posts.
- Storage Spaces (classic, not S2D) now works great out of the box. No need to fine tune it anymore, just click Next Next Next and you'll get the maximum performance for your needs.
- Windows Server Health will help you to understand what went wrong in your SDS and will help you to find the root cause of performance issues.
- Storage QoS Policies allow service providers to manage Storage QoS centrally. IOPS limits are moved when VM moves, and service providers can easily apply such policies across the whole IaaS environment.
- Storage Replica - built-in storage replication solution, that works on a block level using SMB protocol. Now service providers can easily replicate storage data from one DC to another. It supports synchronous and asynchronous replication modes. It can be used as an alternative to Hyper-V Replica if you need synchronous VM replication, or if you need asynchronous replication, but with seconds lag (not minutes, like in Hyper-V Replica). Storage Replica can leverage the advantages of SMB 3.0 - multi-pathing, RDMA, consistent failover etc. It can be used for Stretched Clusters - Failover Clusters, that span among different sites. Storage Replica is included in Windows Server 2016 at no additional charge.
Hyper-Converged Solutions
Hyper-converged architecture is a type of hardware and software approach, which combines compute, network and storage in one layer. Typical Hyper-converged solutions are based on servers with local disk drives, that are connected into one reliable storage system, spanned among virtualization hosts. Advantages of Hyper-converges systems:
- No single point of failure - all hosts are equal, and the overall environment is protected from the failure of any host.
- Rich Scale-out capabilities - add new hosts to the cluster to add capacity and performance to run Hyper-V VMs and store their virtual disks
- SAN is based on traditional LAN, which can be Software-defined Network.
Public Clouds and services, that operate at large scale, usually built using Hyper-converged architectures. Service Providers also like Hyper-converged architectures, and we saw a lot of examples, when service providers chose competitor Hyper-converged solutions for IaaS instead of expensive storage and network systems.
With new SDS and SDN features, Windows Server 2016 allows service providers to build best-in-class Hyper-converged IaaS solutions:
- SDN, based on fast RDMA Ethernet (25/50/100GbE) - much faster, then traditional SANs, that use FC/FCoE.
- Storage, based on Storage Spaces Direct (S2D) and local disk drives. With a proper combination of NVMe SSD drives for caching, SATA SSD for host tier and SATA HDD for cold tier, service providers can get great storage performance for a reliable price.
- Microsoft works with major server and network hardware vendors to build and test in-a-box Hyper-converged solutions, based on Windows Server 2016. Such solutions provide the easiest and the most cost efficient way to build IaaS on Windows Server 2016.
As you may see, Windows Server 2016 introduces a lot of great new features on the host level, that make it the best-in-class solution for IaaS. Some of the features (like Shielded VMs) are unique and not available on competitor platforms, and all of them are included in Windows Server 2016 at no additional cost.
Windows Server 2016 inside the Guest VM
OK, now let's switch to the Guest OS level. Even if you don't run Hyper-V on hosts, Windows Server 2016 is packed with a great new features, that can be used on any virtualization platform.
Nano Server
I've already mentioned Nano Server earlier when I wrote that thin and light Nano Server can be used for Hyper-V hosts. Nano Server is an additional installation type of Windows Server 2016, even lighter then Server Core. Nano Server is "headless" - it doesn't have any GUI and it should be managed remotely.
It installs faster, runs less processes in the background, requires less patches etc. As such, Nano Server in Windows Server 2016 is ideal for the following scenarios:
- Compute Host for Hyper-V
- Container Host
- Host for Scale-Out File Server
- Web server running IIS
- Application platform for micro-services.
Less running processes also means less attack field and less security vulnerabilities. Service Providers will definitely like Nano Server.
Containers
Containers appeared in a Linux world a long ago and already may heard about that concept. Windows Server 2016 adds the same container capabilities to Windows platform, powered by the most popular container management engine - Docker.
"Container" is an isolated environment in which you can run an application without fear of changes due to applications or configuration. Containers share key components (kernel, system drivers, and so on) that can reduce startup time and provide greater density than you can achieve with a VM.
Two types of containers are available in Windows Server 2016:
- Windows Server Containers
- Hyper-V Containers
You can consider Windows Server containers to be the equivalent to Linux containers. Windows Server container types isolate applications on the same container host. Each container has its own view of the host system, including the kernel, processes, file systems, the registry, and other components. In the case of Windows Server containers, they work between the user mode level and the kernel mode level.
Hyper-V containers are based on a container technology that is rooted in hardware-assisted virtualization. With hardware-assisted virtualization, Hyper-V containers' applications are provided a highly isolated environment in which to operate, where the host OS cannot be affected in any way by any running container.
The Docker runtime engine works as an abstraction on top of Windows Server containers and Hyper-V containers. Docker provides all of the necessary tooling to develop and operate its engine on top of Windows containers, be it Hyper-V containers or Windows Server containers. This will afford the same flexibility of developing an application in one container and being able to truly run it anywhere.
While you can connect to the running container through command line tools, you should consider containers and stateless micro-services. There is no GUI inside the container, and if something goes wrong inside a container - just kill it and redeploy from the same Docker template.
Security
Windows Server 2016 has a lot of new security features and enhancements, that make is the most secure Windows Server ever.
- Control Flow Guard - highly optimized platform security feature makes it much more difficult to run arbitrary code through exploits such as buffer overflows.
- Device Guard - when activated, allows only centrally authorized apps to run. Device Guard will block drivers from loading dynamic code and block any driver that is not on the safe-programs list. If there is a compromised driver that tries to modify code in memory, it cannot be run on the machine. Device Guard also provides User mode protection (UMCI), meaning that you can create Code Integrity (CI) policies that define what’s trusted and authorized to run on individual servers.
- Credential Guard - isolates secrets by using virtualization-based technologies so that only privileged systems can access them. Credential Guard blocks the credential theft attack techniques and tools used in many attacks. Malware running in the OS with administrative privileges cannot extract secrets that are protected by virtualization-based security.
- Remote Credential Guard - provides protection against credentials being stolen when an end-user is remotely connected to a system via a remote desktop (RDP) session. When a user attempts to remote desktop to a remote host, the Kerberos request is redirected back to the originating host for authentication. The credential simply does not exist on the remote host any more. If a remote host has malicious code running on it that can obtain credentials, remote credential guard will mitigate this because no credentials will be passed into the remote host.
- Windows Defender Anti-malware engine is included and running by default when you install Windows Server 2016.
- AD FS in Windows Server 2016 contains a built-in Azure MFA adapter to simplify the process of using Azure Multi-factor Authentication. There is no longer a need to deploy On-Premises Azure MFA Server if you wish to add Azure Multi-factor Authentication capabilities for ADFS authentications.
- Just-in-Time (JIT) administration - a simple way to allow some admin capabilities to users in organization only for a limited time. With JIT mechanics the privileges are requested just before they are actually needed, then approved, and then granted to the account for a specific time period. This ensures that the task can be carried out successfully with the correct amount of privileges for the allotted time.
- Just Enough Administration (JEA) - a feature, that allows to assign specific privileges (just enough of them) to a user account that are needed to perform a given required function. This means that you don’t need to assign a user to an administrator account and then remember to remove that person later. JEA usually used in a conjunction with JIT.
- Nano Server - as the most secure way to run Windows Server 2016.
- Shielded VMs - as the most secure way to protect tenant VMs from fabric rogue admins.
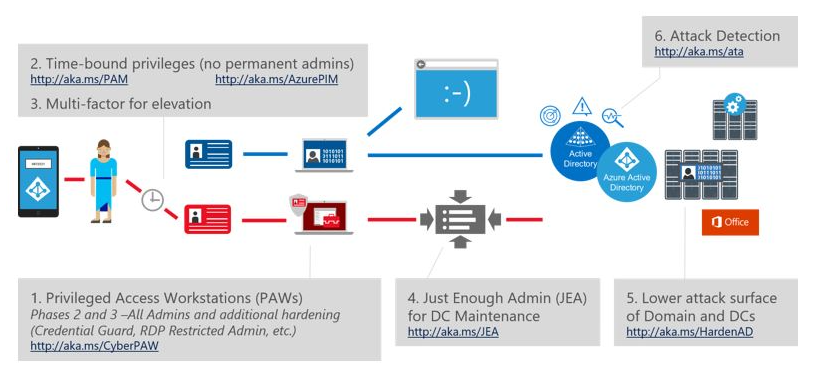
With a release of Windows Server 2016, Microsoft also published a new framework called "Securing Privileged Access". It helps to dramatically increase the security in the Enterprise, that leverages new Windows Server 2016 features in a conjunction with EMS (Azure AD Premium, ATA) and other Microsoft solutions. It is available here. I recommend everybody to read it and implement in your organization.
RDS 2016
Remote Desktop Services in Windows Server 2016 capabilities were significantly improved. Service providers can build Desktop-as-a-Service solutions much easier:
- Connection Broker redesigned and rebuilt to be capable to work with huge amount of End-user connections. Now RDS 2016 can handle thousands of end-user simultaneous connections without any issues, comparing to hundreds in RDS 2012 R2.
- RemoteFX now supports Windows Server 2016 on a Guest VM. Previously it worked only with Windows Client OS. Old problem with "Windows Client, not available for VDI" can now be fully solved by using Windows Server 2016 on a Guest VM, and licensed through Windows Server Datacenter license though SPLA (that allows to run unlimited number of Windows Server VMs on the host). Windows Server 2016 has Windows10-like desktop experience, that should suit the needs of the end-users needs, and now service providers can add RemoteFX capabilities to the solution.
- RemoteFX now supports OpenGL and OpenCL as an addition to DirectX. It now supports up to 1Gb of video RAM per VM, 4K resolution and native pen support. Now it covers even more scenarios with heavy graphics usage.
- Direct Device Assignment (DDA) support - now you can fully assign the GPU into the VM. End-users will be able to manage the drivers and settings of the GPU by themselves, and can leverage full GPU capabilities (e.g. CUDA) inside Guest VM.
- RDP v10 protocol uses H.264 AVC compression to deliver rich graphics experience (4K, 60fps) even through non-reliable network connections.
- Azure SQL Database can be used to host Connection Broker DB. Azure AD Application Proxy can be used to publish RDS farm to external networks in a secure way.
- Remote Credential Guard - provides protection against credentials being stolen when an end-user is remotely connected to a system via a remote desktop (RDP) session.
More details about RDS 2016 are available here.
PowerShell 5.1
Windows PowerShell is the de facto standard for managing Microsoft technologies. With increased support across our private and public cloud offerings, you will not find a single management solution that provides the vast capabilities that Windows PowerShell offers today. It has become so popular, in fact, that many third-party vendors are including Windows PowerShell support directly with their application portfolio. Windows PowerShell now has been open-sourced, which means the community can get involved and contribute to it and make it even better than before. Another fantastic area that Microsoft announced in 2016 is support for Linux. Now, you can use the same interfaces and coding standards you have developed in Windows PowerShell to manage your Linux environments. PowerShell 5.1 in Windows Server 2016 reflects the investment Microsoft is making to ensure that it is not just the primary choice for managing Windows Environments, but Linux, as well.
SMT
Server Management Tools (SMT) is a web-based management shell, hosted in Azure. For instance, administrators can manage Nano Server or Server Core easily from this GUI without affecting the footprint of those deployments. The tool currently has the following capabilities
- View and change system configuration
- View performance across various resources and manage processes and services
- Manage devices attached to the server
- View event logs
- View the list of installed roles and features
- Use a Windows PowerShell console to manage and automate repeatable tasks.
SMT is a great new way to manage Windows Server 2016 environments and it can act as a good alternative to classic Server Manager.
System Center 2016
Windows Server 2016 and System Center 2016 were released the same day. System Center 2016 can manage new features of Windows Server 2016, for example - VMM 2016 provides the simplest way to deploy SDNv2. System Center 2012 R2 won't work with Windows Server 2016, so I assume that service providers will upgrade to System Center 2016 for Windows Server 2016 management purposes. And yes - Windows Azure Pack UR10 (or later) already supports Windows Server 2016.
Verdict
Windows Server 2016 is great. It has a lot of new features, so it's really worth to upgrade. Different service providers and hosters will find different reasons for that:
- If you run IaaS on a previous version of Hyper-V, then you will like new features like Shielded VMs, Hyper-V Containers, Nano Server, SDNv2 and Hyper-V 2016 enhancements.
- Even if you run IaaS on a different hypervisor for hosting purposes - you will definitely like new security features then can make your environment even more secure.
- Shielded VMs is a killer feature, that opens new opportunities for your business. Customers won't be afraid anymore to host VMs with their sensitive data in your environment.
- If you are tired of paying $$$ for enterprise storage systems or SDS from other vendors - then Storage Spaces Direct and Storage Replica will be your saviors.
- If you offer Desktop-as-a-Service to your customers using the solutions from other vendors, then you will be able to reduce the internal cost of the service by migrating to RDS 2016.
- You customers will ask for VMs with Windows Server 2016 anyway. A lot companies already tried Nano Server, Containers and other new great features of Windows Server 2016, and they expect that this OS will available in the cloud of their favorite Service Provider.
If you want to get more details about the changes in Windows Server 2016, I recommend you to read this relatively short (181 pages), but very useful free e-book: Introducing Windows Server 2016.
That's all for today. I plan to cover main Windows Server 2016 new features in details in the nearest future. So stay tuned and don't forget to subscribe :)