Manage the list of services in Azure CSP Subscriptions
In some cases CSP Partners wish to limit the list of Azure services, available in Azure subscriptions of their customers. For example, service providers wants to allow Azure Recovery services only, but don't allow customers to use Azure Virtual Machines or other services. You can achieve this by using Azure Resource Manager Policies.
What you can do with that functionality:
- Allow only specified Azure services for customers
- Allow only specified Azure regions
- Block specific SKUs (e.g. don't allow G-series VMs to reduce the risk of enormous Azure usage growth)
In this example, I will do the following:
- Create new Azure subscription for the customer
- Apply Resource Manager Policy for this subscription, that will allow only Azure IaaS services (Compute, Network, Storage) and block all other Azure services
- Create a Resource Group and assign Owner role for this group to Customer's admin account.
I use this approach because:
- Resource Manager policy is applied on the subscription level
- Customer don't have any edit rights for the subscription, so he won't be able to override the policy
- Customer has owner rights for the Resource Group. This Resource Group will inherit the policy from the subscription level. So Customer will be able to manage the Resource Group, but won't be able to manage the policy.
This approach won't hide blocked services on the portal - tenants still will be able to see those services, but they won't be able to deploy them and see the corresponding error.
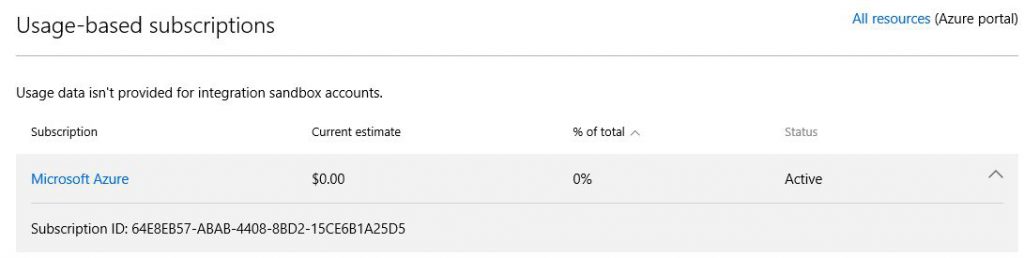
Go to Partner Center portal, create new Customer (or use existing one), create new Azure subscription and check Tenant ID (Customer's Azure Active Directory name) and Azure Subscription ID, will need it later. In my case customer's Tenant ID is romashkatest.onmicrosoft.com and Azure Subscription ID is 64E8EB57-ABAB-4408-8BD2-15CE6B1A25D5.
There are 2 ways to work with Azure Resource Manager policies - using API or using PowerShell. There is no GUI on a portal to manage policies yet. In my example I will use PowerShell.
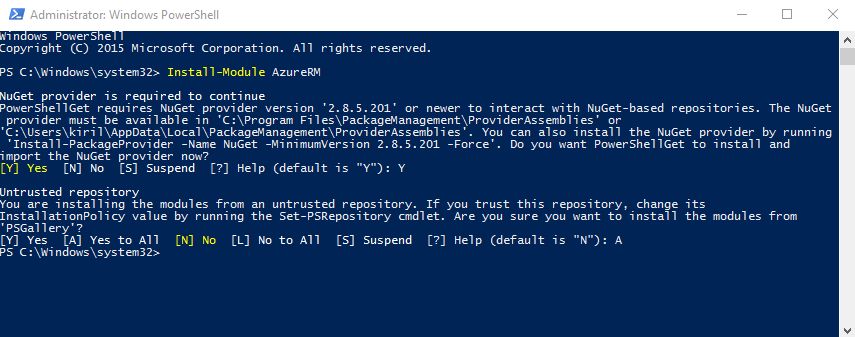
First of all, you need to install Azure Resource Manager modules for PowerShell. To do this, launch PowerShell as Administrator and run one command:
Install-Module AzureRM
Wait until all Azure Resource Manager PowerShell modules will install, it can take several minutes (depending on your network connection speed). After that, launch PowerShell again and connect to your Azure subscription using CSP Partner user account:
Login-AzureRmAccount
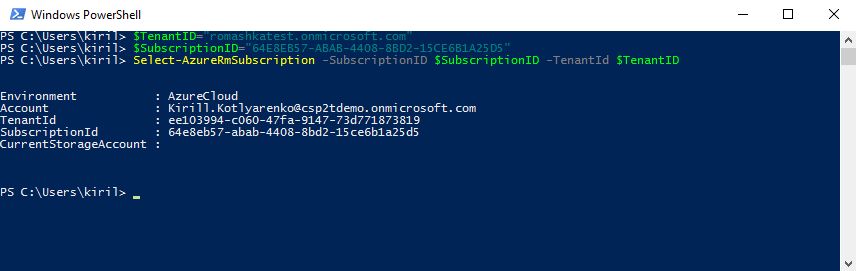
Use these commands to select Customer's Azure Subscription that we've created recently:
$TenantID="romashkatest.onmicrosoft.com"$SubscriptionID="64E8EB57-ABAB-4408-8BD2-15CE6B1A25D5"Select-AzureRmSubscription -SubscriptionID $SubscriptionID -TenantId $TenantID
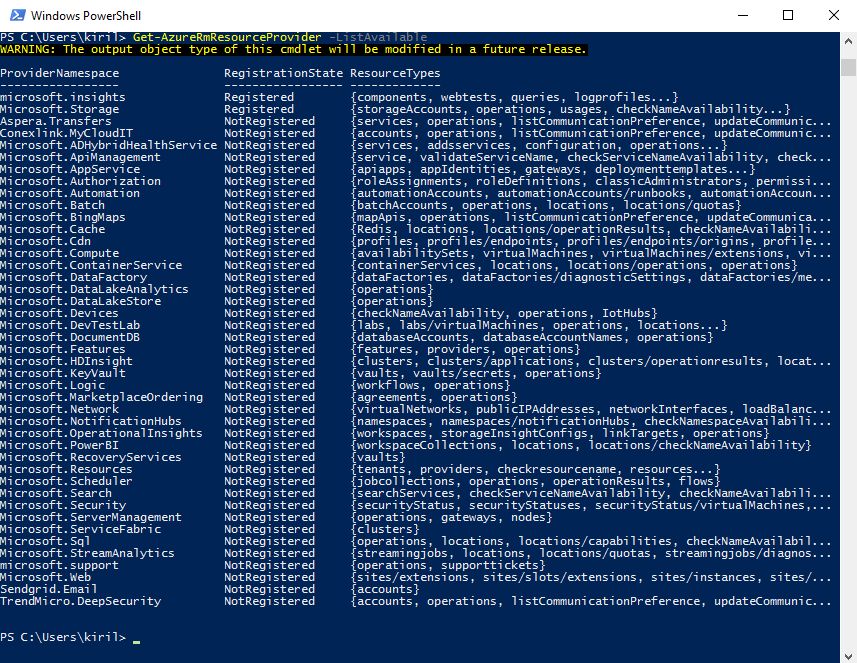
We'll limit the available services in Azure Subscriptions by allowing only several Resource Providers while blocking all others. To get list of all available Azure Resource Providers, run this command:
Get-AzureRmResourceProvider -ListAvailable
We'll allow only Compute, Storage and Network resource providers. Also we'll allow Resources resource provider, which is required, because it is responsible for Resource Groups.
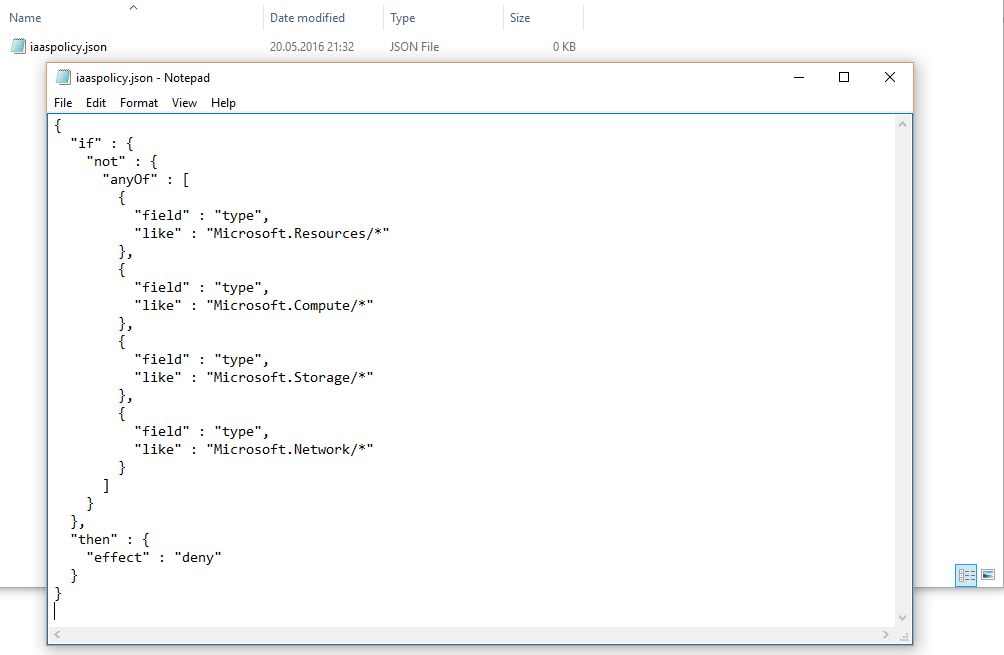
Create a text file and put a policy definition into it. In my case it will be C:Azureiaaspolicy.json. Don't close the PowerShell window yet.
Here is my policy, that will allow customers to use only IaaS services:
{
"if" : {
"not" : {
"anyOf" : [
{
"field" : "type",
"like" : "Microsoft.Resources/*"
},
{
"field" : "type",
"like" : "Microsoft.Compute/*"
},
{
"field" : "type",
"like" : "Microsoft.Storage/*"
},
{
"field" : "type",
"like" : "Microsoft.Network/*"
}
]
}
},
"then" : {
"effect" : "deny"
}
} 
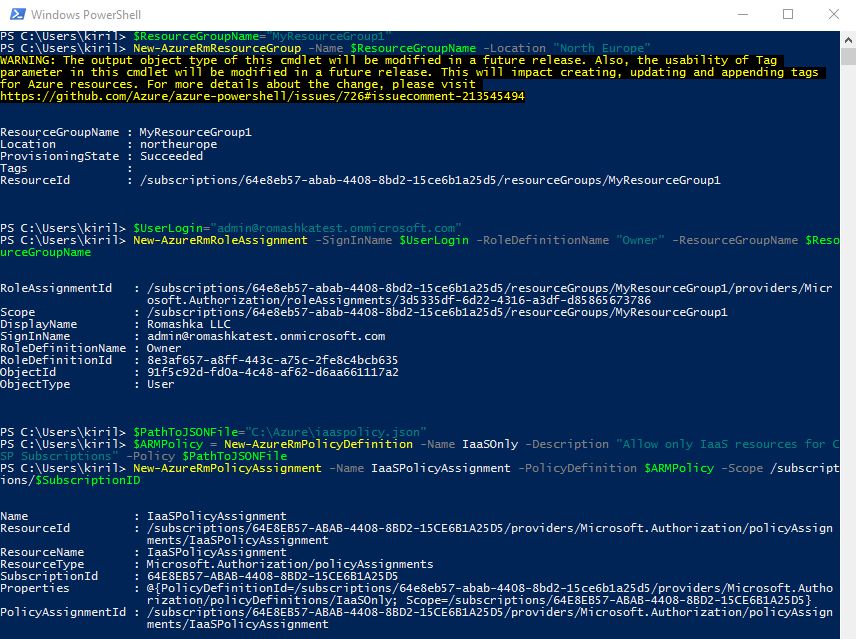
Then run these PowerShell commands to create new Resource Group in the Azure Subscription, that we've selected previously, and apply policy on it. In my case, Resource Group is called MyResourceGroup1, user admin@romashkatest.onmicrosoft.com is assigned Owner rights for that group, and after that a new Resource Group Policy object is created and assigned on this Resource Group.
$ResourceGroupName="MyResourceGroup1"
New-AzureRmResourceGroup -Name $ResourceGroupName -Location "North Europe"
$UserLogin="admin@romashkatest.onmicrosoft.com"
New-AzureRmRoleAssignment -SignInName $UserLogin -RoleDefinitionName "Owner" -ResourceGroupName $ResourceGroupName
$PathToJSONFile="C:Azureiaaspolicy.json"
$ARMPolicy = New-AzureRmPolicyDefinition -Name IaaSOnly -Description "Allow only IaaS resources for CSP Subscriptions" -Policy PathToJSONFile
New-AzureRmPolicyAssignment -Name IaaSPolicyAssignment -PolicyDefinition $ARMPolicy -Scope /subscriptions/$SubscriptionID
That's all. Now let's check how it works. I've logged on to https://portal.azure.com using admin@romashkatest.onmicrosoft.com credentials. I still can see all Azure services, and I can create new VMs in MyResourceGroup1 (but I can't create any other Resource Groups in this Azure Subscription).
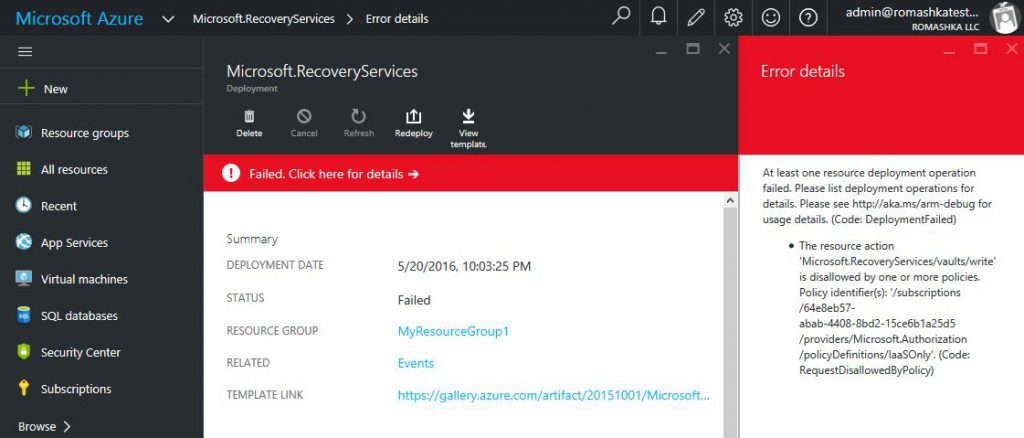
But when I try to create new Azure Recovery Vault, for example, I will this error with policy violation message:
By the way, if you need to create a policy, that will allow customers to use Azure Backup and Azure Site Recovery only (but won't allow them to create VMs or use any other Azure services), then you can create another Azure subscription and apply this policy in a similar way:
{
"if" : {
"not" : {
"anyOf" : [
{
"field" : "type",
"like" : "Microsoft.Resources/*"
},
{
"field" : "type",
"like" : "Microsoft.Storage/*"
},
{
"field" : "type",
"like" : "Microsoft.RecoveryServices/*"
}
]
}
},
"then" : {
"effect" : "deny"
}
}