Use the BSonPoSH PowerShell Module to Check AD Replication
Summary: Learn how to use the BSonPoSH Windows PowerShell module to check Active Directory replication and other tasks.
![]() Hey, Scripting Guy! Your article yesterday left me wondering. If there are so many cool things in the BSonPoSH module, why did you only show a couple of commands? Are there other things you can do with that module?
Hey, Scripting Guy! Your article yesterday left me wondering. If there are so many cool things in the BSonPoSH module, why did you only show a couple of commands? Are there other things you can do with that module?
—CL
![]() Hello CL,
Hello CL,
Microsoft Scripting Guy Ed Wilson here. Today, I have the Virtual PowerShell Users Group meeting at 1:00 PM Eastern Time. I will be talking about using Windows PowerShell to work with performance counters for SQL Servers. It will be way cool, and as you know, it is something I have been looking forward to for quite some time. Tomorrow (July 21, 2011), we will be in Columbus, Ohio, for the Central Ohio PowerShell Users Group meeting. They have announced a location for this meeting, so make sure you check it out. On Saturday, July 23, 2011, we will be at the SQLSaturday in Wheeling, West Virginia, so there is lots of fun this week. Check out the Scripting Guys Community page for upcoming virtual and live events.
CL, in yesterday’s article I talked about downloading and installing the BSonPoSH module. Today, I would like to continue exploring the BSonPoSH module, and see some of the cool things it can accomplish.
One of my favorite commands is the Ping-Subnet command. It allows me to ping all the devices on my subnet or any other subnet. The command returns the IP addresses that reply, it but does not return the ones that do not reply. It is quick and easy to use. The command and associated output follow:
PS C:\> Ping-Subnet -IP 192.168.1.0 -netmask /24
192.168.1.40
192.168.1.41
192.168.1.42
192.168.1.88
192.168.1.101
192.168.1.103
192.168.1.97
192.168.1.130
192.168.1.151
192.168.1.152
192.168.1.153
192.168.1.154
192.168.1.161
192.168.1.254
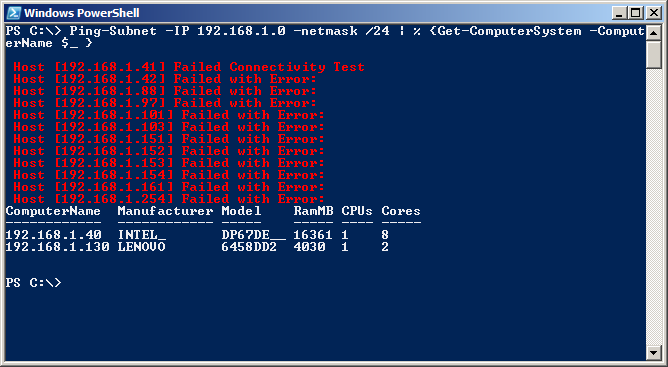
I can pipe the IP address to other commands. For example, I can send the output to Get-ComputerSystem and retrieve system names and other information. The command for such a task is shown here (the % symbol is the alias for the ForEach-Object cmdlet):
Ping-Subnet -IP 192.168.1.0 -netmask /24 | % {Get-ComputerSystem -ComputerName $_ }
The command and associated output are shown here.
The same technique can be used to obtain uptime information or other information as required. For example, the Get-Uptime command is shown here, with the associated output:
PS C:\> Get-Uptime | fl *
Seconds : 14
Days : 0
Uptime : \\NEWMRED has been up for: 0 days, 2 hours, 5 minutes, 14 second
s
Minutes : 5
ComputerName : NEWMRED
Hours : 2
Note Most of the cmdlets do not have a credential parameter; therefore, it is necessary to start the Windows PowerShell session using the credentials that will apply to the remote destination, or to use Windows PowerShell remoting. In either case, access to the BSonPoSH module becomes a consideration. If you install in the default user location, it will not be easily available to other accounts. If you install in the $psHome location, you will need administrator rights to perform the installation. If you install in a network location, the module will not show up when using the listavailable switched parameter from the Get-Module cmdlet. In addition, you will need to provide the complete path each time you load the module.
One of my favorite commands is the NetStat command. The problem with it is that it returns strings, and as a result, it requires parsing to allow one to work with the returned data. The BSonPoSH module solves this problem with the Get-NetStat command. The basic command returns all information. The command and associated output are shown here.
PS C:\> Get-NetStat
Warning: column “ProcessID” does not fit into the display and was removed.
Protocol LocalAddress LocalPort RemoteAddress RemotePort State ProcessNam
TCP 0.0.0.0 135 0.0.0.0 0 LISTENING svchost
TCP 0.0.0.0 445 0.0.0.0 0 LISTENING System
TCP 0.0.0.0 554 0.0.0.0 0 LISTENING wmpnetwk
TCP 0.0.0.0 1025 0.0.0.0 0 LISTENING wininit
TCP 0.0.0.0 1026 0.0.0.0 0 LISTENING svchost
TCP 0.0.0.0 1027 0.0.0.0 0 LISTENING svchost
TCP 0.0.0.0 1058 0.0.0.0 0 LISTENING services
TCP 0.0.0.0 1060 0.0.0.0 0 LISTENING lsass
TCP 0.0.0.0 2869 0.0.0.0 0 LISTENING System
TCP 0.0.0.0 5985 0.0.0.0 0 LISTENING System
TCP 0.0.0.0 10243 0.0.0.0 0 LISTENING System
TCP 0.0.0.0 47001 0.0.0.0 0 LISTENING System
TCP 192.168.1.40 139 0.0.0.0 0 LISTENING System
TCP 192.168.1.40 46023 192.168.1.151 445 ESTABLISHED System
TCP 192.168.1.40 46026 192.168.1.101 445 ESTABLISHED System
In addition, the Get-NetStat command returns a custom object. This object, a NetStatInfo object, is shown in the following output (gm is an alias for the Get-Member cmdlet):
PS C:\> Get-NetStat | gm -MemberType *property*
TypeName: BSonPosh.NetStatInfo
Name MemberType Definition
LocalAddress NoteProperty System.String LocalAddress=0.0.0.0
LocalPort NoteProperty System.String LocalPort=135
ProcessID NoteProperty System.String ProcessID=972
ProcessName NoteProperty System.String ProcessName=svchost
Protocol NoteProperty System.String Protocol=TCP
RemoteAddress NoteProperty System.String RemoteAddress=0.0.0.0
RemotePort NoteProperty System.String RemotePort=0
State NoteProperty System.String State=LISTENING
One of the things that is fun to use is the Out-Voice command. It accepts pipeline output, and using the Speech API, it “reads” the output. For example, I can pipe the results from the Get-Process cmdlet to Out-Voice, and it will “read” the results. The command is shown here:
Get-Process | Out-Voice
The Out-Voice cmdlet is also able to read text files. I can combine the Get-Content cmdlet and Out-Voice to accomplish this task. A sample command is shown here:
Get-Content C:\fso\myTextFile.txt | Out-Voice
One word of caution here: after I pipe data to the Out-Voice command, there is no way to stop it from reading the data, except to close the Windows PowerShell console. The normal break command, Ctrl+C, cannot halt execution of the command.
The Test-ADReplication cmdlet is one of my favorites. I wrote a Hey, Scripting Guy! Blog post about this in regards to GPOs. This cmdlet works great and is as simple as typing the command. The command and associated output are shown here.
CL, there are lots of other commands in the BSonPoSH module. These are just some of the highlights.
Community Week will continue tomorrow when Guest Blogger Jeremy Engel introduces his Excel module. It is good stuff, so make sure not to miss it.
I invite you to follow me on Twitter and Facebook. If you have any questions, send email to me at scripter@microsoft.com, or post your questions on the Official Scripting Guys Forum. See you tomorrow. Until then, peace.
Ed Wilson, Microsoft Scripting Guy


 Light
Light Dark
Dark
0 comments