Parsing an AuditPol.exe Report with Windows PowerShell 2.0
![]() Hey, Scripting Guy! I have been using AuditPol.exe to verify the audit policy that is configured on our network. The problem is that the report that is generated has a lot of text, and it is not easy to see exactly what is being audited or not. Is it possible to use Windows PowerShell 2.0 to parse the report generated by AuditPol.exe to make the settings information easier to find?
Hey, Scripting Guy! I have been using AuditPol.exe to verify the audit policy that is configured on our network. The problem is that the report that is generated has a lot of text, and it is not easy to see exactly what is being audited or not. Is it possible to use Windows PowerShell 2.0 to parse the report generated by AuditPol.exe to make the settings information easier to find?
— PS
![]() Hello PS,
Hello PS,
Microsoft Scripting Guy Ed Wilson here. It is amazing how many people seem to want to talk to me each week. That is really cool. Teresa (my better half) will tell you that I love to talk, and if I get to talk about scripting—in particular, Windows PowerShell—that is all the better. On Thursday, July 29, I will be talking to the Charlotte SQL Users group. They are a great bunch of people; this meeting was arranged back in March when I was in Charlotte for SQL Saturday. It is always fun to talk to people who are interested in Windows PowerShell, and the cool thing is the way that Windows PowerShell and SQL Server have been brought together.
In a meeting last week, we were talking about the way we had used Live Meeting during Tech·Ed 2010 in New Orleans. Because I am not allowed to fly due to ear surgery, Craig and I used Live Meeting so that I could talk to people who were attending the conference. I then had the idea about trying to arrange to do the same thing for TechEd Europe 2010 that will be in Berlin. The only bad thing about Live Meeting is you do not actually get to go to the place where the meeting is held. Berlin is an awesome place. The following photo is one I took there while I was teaching a Windows PowerShell workshop a few years ago.
Tech·Ed 2011 North American will be in Atlanta, Georgia, and even if I am not allowed to fly by then, I will be able to drive to that conference. By the way, there are also Tech·Ed conferences in Australia, Japan, Brazil and other places this year.
When using the AuditPol.exe executable to generate an audit report, you need to run the program with administrator rights. I like to use the Windows PowerShell console to do this. In fact, I cannot remember the last time I opened an actual command prompt. Here is the AuditPol.exe command I used to generate an audit policy report, as well as the results generated from the report. You will notice that the Windows PowerShell command prompt is open to the C:\Windows\System32 folder. That is a feature of starting the Windows PowerShell console with administrator rights.
PS C:\Windows\system32> auditpol /get /category:*
System audit policy
Category/Subcategory Setting
System
Security System Extension Success and Failure
System Integrity No Auditing
IPsec Driver No Auditing
Other System Events No Auditing
Security State Change No Auditing
Logon/Logoff
Logon No Auditing
Logoff No Auditing
Account Lockout No Auditing
IPsec Main Mode No Auditing
IPsec Quick Mode No Auditing
IPsec Extended Mode No Auditing
Special Logon No Auditing
Other Logon/Logoff Events No Auditing
Network Policy Server No Auditing
Object Access
File System No Auditing
Registry No Auditing
Kernel Object No Auditing
SAM No Auditing
Certification Services No Auditing
Application Generated No Auditing
Handle Manipulation No Auditing
File Share No Auditing
Filtering Platform Packet Drop No Auditing
Filtering Platform Connection No Auditing
Other Object Access Events No Auditing
Detailed File Share No Auditing
Privilege Use
Sensitive Privilege Use No Auditing
Non Sensitive Privilege Use No Auditing
Other Privilege Use Events No Auditing
Detailed Tracking
Process Termination Success and Failure
DPAPI Activity No Auditing
RPC Events No Auditing
Process Creation Success and Failure
Policy Change
Audit Policy Change No Auditing
Authentication Policy Change No Auditing
Authorization Policy Change No Auditing
MPSSVC Rule-Level Policy Change No Auditing
Filtering Platform Policy Change No Auditing
Other Policy Change Events No Auditing
Account Management
User Account Management No Auditing
Computer Account Management No Auditing
Security Group Management No Auditing
Distribution Group Management No Auditing
Application Group Management No Auditing
Other Account Management Events No Auditing
DS Access
Directory Service Changes No Auditing
Directory Service Replication No Auditing
Detailed Directory Service Replication No Auditing
Directory Service Access No Auditing
Account Logon
Kerberos Service Ticket Operations No Auditing
Other Account Logon Events No Auditing
Kerberos Authentication Service No Auditing
Credential Validation Success and Failure
PS C:\Windows\system32>
To store the report in a text file, you can simply redirect the output to a file. This is shown here:
auditpol /get /category:* > c:\fso\audit.txt
The easy way to parse a text file is to use the Select-String cmdlet. If fact it is so easy, it is almost like no work at all. You mentioned you were interested in the things you are not auditing. Here is how to parse your audit.txt file and retrieve only the items you are not auditing:
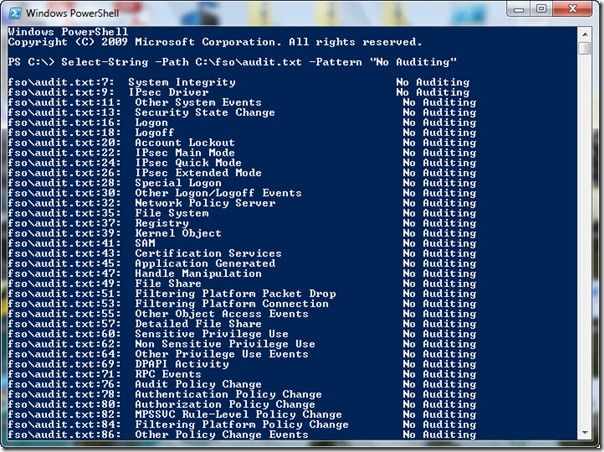
Select-String -Path C:\fso\audit.txt -Pattern “No Auditing”
The output from the Select-String command is shown in the following image.
If you are not interested in the line number where the match occurs, you can filter it out. To filter out results from Select-String, it is important to realize that the command returns a matchinfo object. When you know the members of a matchinfo object, you can select the specific properties you are interested in receiving. The members of the matchinfo object are shown here:
PS C:\> Select-String -Path C:\fso\audit.txt -Pattern “No Auditing” | get-member
TypeName: Microsoft.PowerShell.Commands.MatchInfo
Name MemberType Definition
—- ———- ———-
Equals Method bool Equals(System.Object obj)
GetHashCode Method int GetHashCode()
GetType Method type GetType()
RelativePath Method string RelativePath(string directory)
ToString Method string ToString(), string ToString(string directory)
Context Property Microsoft.PowerShell.Commands.MatchInfoContext Context {g…
Filename Property System.String Filename {get;}
IgnoreCase Property System.Boolean IgnoreCase {get;set;}
Line Property System.String Line {get;set;}
LineNumber Property System.Int32 LineNumber {get;set;}
Matches Property System.Text.RegularExpressions.Match[] Matches {get;set;}
Path Property System.String Path {get;set;}
Pattern Property System.String Pattern {get;set;}
PS C:\>
By only choosing the line property, you can see the policy setting that is not being audited. This is shown here:
PS C:\> Select-String -Path C:\fso\audit.txt -Pattern “No Auditing” | Select-Object l
ine
Line
—-
System Integrity No Auditing
IPsec Driver No Auditing
Other System Events No Auditing
Security State Change No Auditing
Logon No Auditing
Logoff No Auditing
Account Lockout No Auditing
IPsec Main Mode No Auditing
IPsec Quick Mode No Auditing
IPsec Extended Mode No Auditing
Special Logon No Auditing
Other Logon/Logoff Events No Auditing
Network Policy Server No Auditing
File System No Auditing
Registry No Auditing
Kernel Object No Auditing
SAM No Auditing
Certification Services No Auditing
Application Generated No Auditing
Handle Manipulation No Auditing
File Share No Auditing
Filtering Platform Packet Drop No Auditing
Filtering Platform Connection No Auditing
Other Object Access Events No Auditing
Detailed File Share No Auditing
Sensitive Privilege Use No Auditing
Non Sensitive Privilege Use No Auditing
Other Privilege Use Events No Auditing
DPAPI Activity No Auditing
RPC Events No Auditing
Audit Policy Change No Auditing
Authentication Policy Change No Auditing
Authorization Policy Change No Auditing
MPSSVC Rule-Level Policy Change No Auditing
Filtering Platform Policy Change No Auditing
Other Policy Change Events No Auditing
User Account Management No Auditing
Computer Account Management No Auditing
Security Group Management No Auditing
Distribution Group Management No Auditing
Application Group Management No Auditing
Other Account Management Events No Auditing
Directory Service Changes No Auditing
Directory Service Replication No Auditing
Detailed Directory Service Replication No Auditing
Directory Service Access No Auditing
Kerberos Service Ticket Operations No Auditing
Other Account Logon Events No Auditing
Kerberos Authentication Service No Auditing
PS C:\>
On the other hand, if you wish to see only the items that are audited, you can modify the pattern to return lines that contain the string “Success and Failure” as shown here:
PS C:\> Select-String -Path C:\fso\audit.txt -Pattern “Success and Failure” | Select-
Object line
Line
—-
Security System Extension Success and Failure
Process Termination Success and Failure
Process Creation Success and Failure
Credential Validation Success and Failure
PS C:\>
You can get much more sophisticated in the way you parse text files by including more complex regular expression patterns. Check out the Hey, Scripting Guy! archives for a good introduction to using regular expressions with Windows PowerShell.
PS, that is all there is to using Windows PowerShell to work with strings. String Week will continue tomorrow when we will talk about splitting strings into an array.
We would love for you to follow us on Twitter or Facebook. If you have any questions, send email to us at scripter@microsoft.com, or post your questions on the Official Scripting Guys Forum. See you tomorrow. Until then, peace.
Ed Wilson and Craig Liebendorfer, Scripting Guys


 Light
Light Dark
Dark
0 comments