Getting “Login failed for user 'NT AUTHORITYANONYMOUS LOGON'” when browsing External list on a Claims + Kerberos Web Application
Problem
Pass through authentication not working for BCS on a WebApplication which is Claims based and using Kerberos.
While you try to access the External List based on User’s Identity you received the following error
Login failed for user 'NT AUTHORITY\ANONYMOUS LOGON'
PreReq
In this post I will talk about the reason and what are the different workarounds for this issue. I will not be discussing the steps of how to create Web Application in Kerberos or how to set up SPN
Reason
For Service Applications which are not claims aware have the ability to utilize claims to windows token service to convert Claims token. At this time BCS does not leverage C2WTS. More details can be found in the following Guide
Workaround 1 – Classic Mode
Use Web Application in Classic Mode
Unfortunately conversion of Claims > Classic is not supported. So you will need to create new web Application migrate all the contents again.
Workaround 2 – Revert to Self (BCS Authentication)
1) By Default Revert to Self is disabled. We will need to run following CMDlets from PowerShell to enable it
Get-SPServiceApplication
#Copy the ID of BCS Service Appliction
$bcs = Get-SPServiceApplication -ID "BCS ServiceApp ID"
$bcs.RevertToSelfAllowed = $true
$bcs.update()
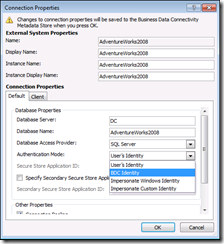
2) We will need to modify External Content type by using SharePoint designer and have it use BDC Identity
Select BDC Identity under Default and Client TAB and click on OK.
Now it will let all the users browse to the external list.
Note - Whenever end user brows to the external list, it is the BCS AppPool account which is used to pull the data and not the User’s Identity. Please ensure that BCS App Pool have permissions on the database.
Workaround 3 – Impersonate Windows Identity
If you need to use User’s Identity and do not wish to move to Classic mode then we will need to setup Secure Store Service for this.
Secure Store service will help in converting Claims
1) Browse to Manage Service Application > New >Secure Store Service
2) Browse to Secure Store Service Application. If you get the following error
“Cannot complete this action as the Secure Store Shared Service is not responding. Please contact your administrator”
Please ensure Secure Store Service is started in Central Administration
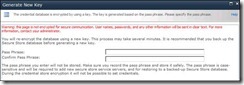
3) Click on Generate New Key and Provide a Pass Phrase
It’s not mandatory to provide your Farm Pass Phrase, this can be different then Farm Pass Phrase which you would have provided while creating the farm.
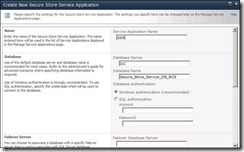
4) Click on New and provide the details.
Target Application ID can be anything; it’s not required to be same as Service Application Name
5) Click on Next
6) Accept all the default options and click on Next
Provide account which would manage Secure Store Service, this account should also have permissions on BCS Service Application.
7) Now we need configure External Content type to use Secure Store Service
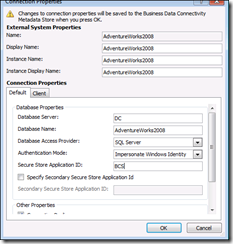
8) Edit External Content type connection properties from SharePoint designer
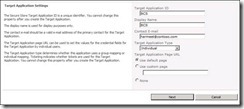
a. Authentication Mode – Impersonate Windows ID
b. Secure Store Application ID - BCS (This is the value which we provided in Target Application ID in Secure Store Service )
Make these changes in both Default and Client TAB
9) Click OK and Save the changes made in SharePoint Designer.
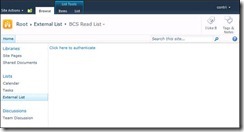
10) Browse the External list as end user and it will ask you to Authenticate.
Users will need to go through this trouble only once as Secure Store Service needs to store the account details in its database.
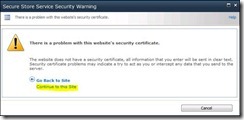
11) Click on Continue to this site
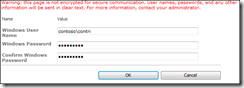
12) Provide user credentials and click on OK
13) You will notice that it still did not show you the contents. This is because now we are trying to pull this data as the end user.
If our end user does not have permission on the SQL database then it will give error. This can be confirmed from the SQL Logs
Grant end users permission on the database, minimum would be data reader.
14) Now Authenticate again to the list and this time it should show you the results.
I would like to thank Hiran Salvi for his contribution in finding the resolution.