SCCM 2012 RBA Example
Delegating permissions in SCCM can be a trial and error process to get those permissions exactly as you need them. This blog goes through a common scenario where you need to allow an IT administrator limited access into SCCM by letting them create or modify existing collections then deploy software to them using existing applications, packages or task sequences. You can use this scenario to help you build your own delegation security model.
Let's say your organization in North America and Europe has decided to delegate some responsibilities to remote IT administrators to offload some of the work from the SCCM Administrators. These admins should not be able to affect other remote sites. Your organization has decided to grant the popular Nick Burns access into SCCM to manage the systems in North America.
As background information I built a single server SCCM environment and configured it with the below items to support this scenario.
- Created an AD Domain User called Nick Burns
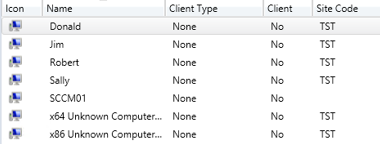
- Import 4 devices called:
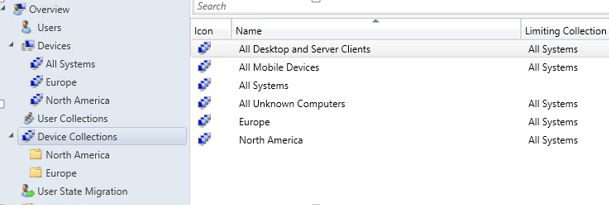
- Create the following Collection folders
- North America
- Europe
- Created the following collections:
The goal is to allow Nick Burns the same permissions that all the remote IT Staff members will have but only on the North American devices. He should not be able to see any device in Europe.
He should be able to:
- Create new or change existing collections
- Delete North America collections but not the North America collection itself
- Deploy Applications
- Deploy Packages
- Deploy Task Sequences
- Remote Control a device
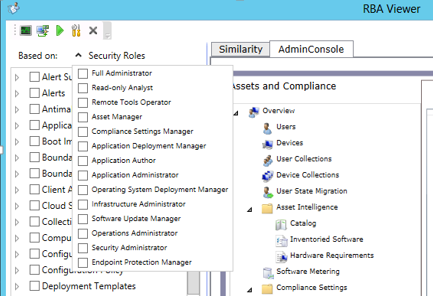
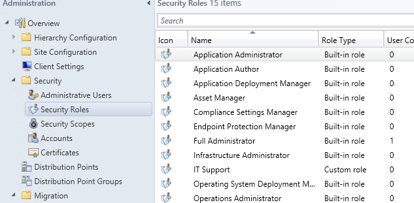
The first thing is to create a new Security Role for the IT Staff members
- Open RBA Viewer from the SCCM 2012 SP1 Toolkit
- This can be found here: https://www.microsoft.com/en-us/download/details.aspx?id=36213
- Click Security Roles then uncheck Full Administrator to uncheck all the boxes
- Check the following permissions:
- Application
- Read
- Collection
- Read
- Modify
- Delete
- Remote Control
- Create
- Read Resource
- Deploy Packages
- Deploy Applications
- Deploy
Task Sequences
- Package
- Read
- Task Sequence Package
- Read
- Application
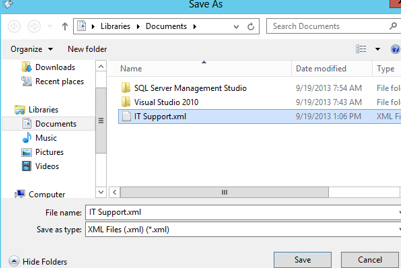
- Click the Export button and save it to the Documents folder called IT Support.xml
Next is to import the policy into SCCM
- Launch the SCCM Console
- Click Administration
- Expand Security
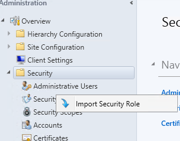
- Right click Security Roles --> Click Import Security Role
- Select the IT Support.xml file in the documents folder --> Click Open
- Click Security Roles and you should see the IT Support security role listed
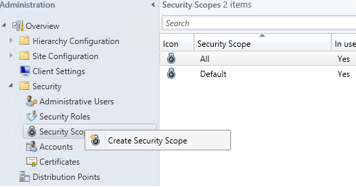
Next create the security scope that will define what the permissions can apply to.
- While still in the SCCM console right click Security Scopes --> Create Security Scope
- Name the security scope North America
- Click OK
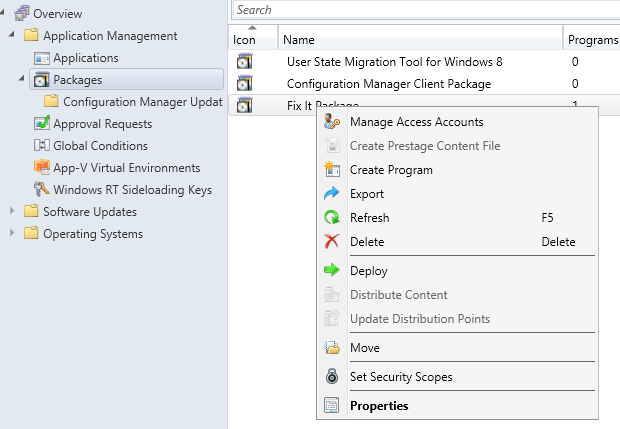
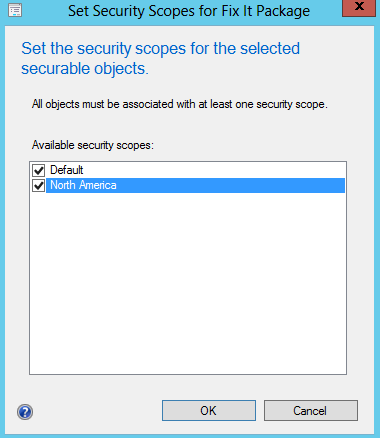
- Right click each package that the scope will have access to --> Click Set Security Scopes
- Select the North America scope
- Click OK
- Perform the same action on the Applications and Task Sequences to add them to them to the North America scope
The final step is to grant Nick Burns access into SCCM with the new IT Staff permissions
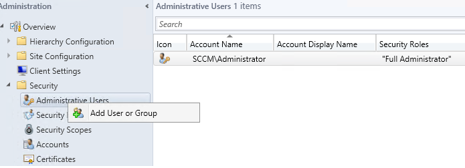
- While still in the SCCM console right click Administrative Users --> Add User or Group
- Click Browse and select Nick Burns domain account
- It is recommended to use security groups instead of an individual account
- Click Add for Assigned security roles:
- Select the IT Support role --> Click OK
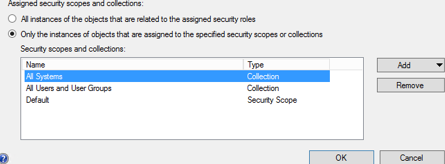
- Under Security scopes and collections, remove all existing collections and scopes
- Click Add --> Collection
- Select the North America collection --> Click OK
- This step is very important as this determines what Nick is limited to support
- Click Add --> Security Scope
- Select North America --> Click OK
- Click OK
When Nick Burns launches the SCCM console he will be limited to what he can see and can do.
With these permissions there are a couple of items to take note of:
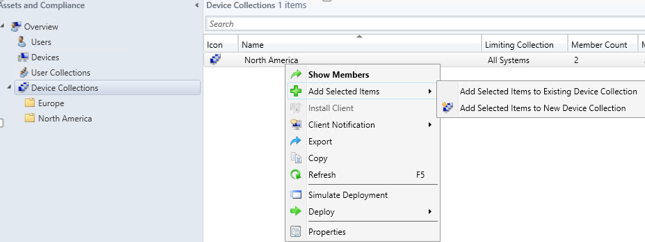
- Nick is only able to create a collection by right clicking an object then selecting Add Selected Items to New Device Collection.
- Nick doesn’t have permissions to move a collection. The ConfigMgr Administrator would need to move the collection he created if it is in the wrong location or he would need the Move Folder Item permission under Collections to move it. With this permissions he would be able to move it to any folder as permissions can not be set directly to folders however, he would not be able to see any other collection in that folder.
- Nick is only able to see the devices assigned to the North America collection due to the collection limitation that was defined with his user permissions even if he tries to create a query rule to select all systems. He cannot delete or modify the North America collection.
If you are looking for more detailed information on SCCM 2012 RBA you may find these links helpful:
- https://technet.microsoft.com/en-us/library/gg699359.aspx
- https://blogs.technet.com/b/hhoy/archive/2012/03/07/role-based-administration-in-system-center-2012-configuration-manager.aspx
- https://technet.microsoft.com/en-us/library/gg682088.aspx#FAQ_Security
- https://msdn.microsoft.com/en-us/library/hh948344.aspx