Gone Firewallin' with WS08 and WinVista
For those of you who read my standalone blog, you already know that I'm a huge fan of the Windows Firewall with Advanced Security.
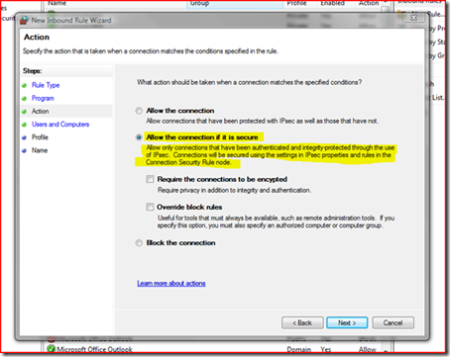
You can do bunch with this firewall functionality, including some hugely intelligent authenticating firewall rules.
That is, you can not only create your traditional inbound and outbound allow or block filters. You also have the ability to create "Allow if secure" rules that combines IPsec authentication (known as Connection Security in the Windows Firewall) with Inbound filters.
This results in the ability to only allow the traffic through, say to your critical business server, if the connecting host and/or the user on that host can be successfully authenticated at the network layer via IPsec.
I demonstrated how this works with Network Access Protection (aka NAP) and Forefront Client Security at my "Enabling Policy-Driven Network Access" session at TechEd SEA this last September.
Now, thanks to the great work from our bud's over in the Windows Server User Assistance team, we've got even more stuff to help you get most out of this neat Windows Server 2008 (and Windows Vista) technology:
Step-by-Step Guide to Deploying Policies for Windows Firewall with Advanced Security
Check this stuff out!
Really...I mean it...it's worth the read.
When used in combination with FCS, the Windows Firewall really enables you to implement a powerful a proactive defense-in-depth approach, i.e. NAP + Windows Firewall with Advanced Security + FCS.
Enjoy...