A great example of “a social engineering” attack : my Polynesian friend Marceline attacked me this morning !!
The context/purpose of this blog
It is always interesting to use real world examples to explain security, especially how “bad guys” manipulate people to steal information.
This is a true story, “My” True story.
This morning, I was listening to a very nice presentation in Copenhagen, and suddenly my friend Marceline started to chat with me. Marceline is native from Tahiti, so speak French and Tahitian, but not English at all (you will understand later why I mention that).
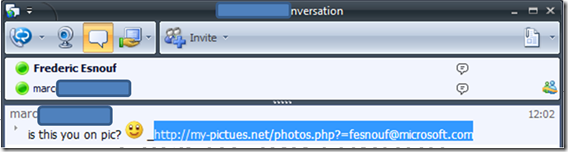
Here is what I saw on my screen:
The problem, analysis of the attack
Because I am working in security, I quickly saw a lot of good reasons to consider this as an attack from a cybercriminal (a real person or a robot).
Look at the screenshot and “think” like a hacker:
· My friend is talking to me
o Fact: A friend of mine, Marceline is chatting with me.
o Unfortunate assumption: This is not a problem, only my friend can chat with me... and I know her so no risk
o Conclusion: this is true, you trust your friend, but how can you be sure that this is in fact your friend? If someone call you and say “hi, this is your mother on the phone, can you give me your credit card number”, are you going to do so ?
· This is a common discussion, about pictures of me on internet, in English.. what is the problem ?
o Fact: this discussion seem very common, no specific reason to be warned.
o Unfortunate assumption: a generic discussion like this is not a problem. Why should I be afraid by this ?
o Conclusion: even standard behaviors could be a problem. A few month ago someone nocked at the door of my grandma, asked to “break a 20 euros bills”... my Grandma said yes, took her purse... the guy took the purse and ran. This is not computer problem at all; this is just “bad guy” way of working. They engage a common discussion with you, and then attack you.
· She is talking to me in English ?
o Unfortunate assumption/ Conclusion: Either my friend is trying to have fun… or this is not my friend. she does not speak english !
· When I clicked the link, I saw that the name of the file to download was not “Jpg” or “BMP”… but an “EXEcutable”.
o Conclusion: As a computer specialist, I can see that this is an attack. They try to make me “execute” a program (not display a picture) that will of course will contain some code that will compromise my machine.
· Etc …
What is the appropriate behavior? How to react ?
So obviously it was an attack for me, but I needed to be sure.
I decided to have fun with this “hacker”.
ð What I want to emphasize here is how you need to react to prevent this attack.
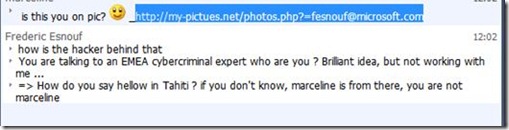
The key question to ask yourself is “who is behind that chat? I think this is not Marceline, what I can do to make sure this is her (or a hacker)”.
So, I used a very basic approach. Ask a “question” to that “potential Marceline”, that I know only my friend can answer.
I must say that here, I was “sure” that it was a hacker. So I had fun. Here is the discussion:
And guess what, a few seconds after, the “green” light in communicator turned into yellow, which means disconnected. I don’t know if a real person (flesh and blood) was behind (or a robot) but for sure the trick did not work, and I did not execute this “Executable”.
Note : After investigation, in fact my friend Marceline had the same attack, and unfortunately “executed” this application. This is how she has been infected. This means that this “Bad program” is stealing her list of contact in Messenger, and then tries to attach each of them the same way. We can imagine that this program is also stealing other information, pretty much every “keystroke” (so bank account number, Credit Card numbers, passwords.. etc).
Only for IT/Security Experts
NEVER DO THAT if you are just a standard user (only for IT Pros)!!!!!! but I decided to continue the investigation.
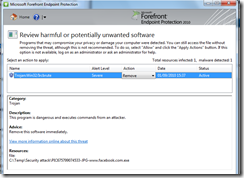
I download the file (but not executed it), and guess what “My Forefront EndPoint Protection Antivirus program” just discovered a “Malware” (Trojan Type) in this file:
So this Executable contains in fact code that will hack your machine. Based on the Online Database, this EXE contains a “Win32/IRCBrute” attack:
Trojan:Win32/Ircbrute Description: Trojan:Win32/Ircbrute is a generic detection for multiple families of malware. Many of these are backdoor Trojans that use Internet Relay Chat (IRC) for remote command and control of the affected machine. Published Date: Mar 30, 2010 Alert level: Severe |
A short conclusion. Using a computer
So as you can see, using a computer is the same as being a “citizen”. If you are walking on the street, and see a “strange guy” (based on your own criteria of what a bad guy is)… you may say “hum, I need to be prudent, and prevent any problem to take place: I go on the other side of the road”.
With computer it is the same. Be always “aware”, and “tuned”. Don’t be afraid by “the computers” (if you are afraid, also be afraid to walk on the street), but rather “try to think” like bad guy:
· Don’t go on web site that may contain malicious code: free software, hacking, … even if you have strong and up-to-date security products such as Microsoft FEP.
· Try to detect strange behavior, and if you are not “100% sure”, don’t click or give what you are requested to give (pin code, Password, etc…).
I have been hacked (my friend Marceline) how to react now that I am infected
So how to react? 2 key things:
· PREVENT THIS ATTACK
· and if you detect that you have been hacked, MAKE SURE THAT THESE ATTACKERS WILL NOT CAUSE YOU TROUBLES
For my friend, for sure she has been targeted. Having her “messenger” password is not that important, but having her “credit card number” is a really a problem. Her machine is obviously running a “spy” application that is logging all the keystroke: password, email, and credit card numbers.
More important, the hackers had access to her (messenger) contacts list, so all her friends are now a “target”. They will receive the same attack (messenger attack) as me this morning. If they run this “spy” application, they are hacked ! same as my friend Marceline.
So here is the action plan I proposed to her:
PRIORITY 1: Prevent other problems
· Contact all your friends. Send them an email and inform them about the attack. If they have the same “attack attempt”, they have to do the same as me: “do not click this link” !
· Contact your bank, ask them to check your account and change your credit card number (if you use your credit card to pay stuff on the internet).
PRIORITY2: Clean your machine.
In fact, the best advice is to reinstall it from scratch. Once reinstalled : Install a powerful and up-to-date security product. I advise to use Microsoft security essentials ( https://www.microsoft.com/security_essentials/default.aspx?mkt=fr-ca). This is free and very efficient. For me and my friend Marceline, this “EXEcutable” has been in real time identified as a virus.
Conclusion
Even if this attack came via the computer, this is in fact a very old/Standard way of stealing things : You knock at the door, you say “I am a policeman”, and you access the house, and steal everything.
Computers or real world, there is no difference : you always need to be prudent.
By the way, how do you say “hello in Tahitian” : ia ora na !