Disable automatic forwarding in Office 365 and Exchange Server to prevent information leakage
This article is describing a brief guide on how to prevent internal users from auto-forwarding emails to external mailbox users and on how to disable automatic email forwarding in Office 365 and Exchange Server.
Allowing users to use mail auto-forwarding brings the risk of information leakage. Additionally, users can select the option to not keep a copy of the message in the mailbox which could also result in data loss.
How to remove the automatic email forwarding options from Outlook on the web (OWA) in Exchange Server and Exchange Online 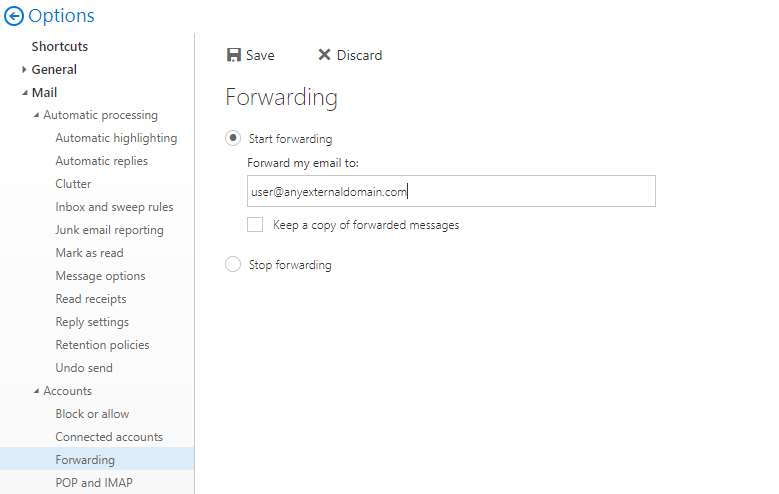
Automatic email forwarding options in Outlook Web App in Exchange Server and Exchange Online
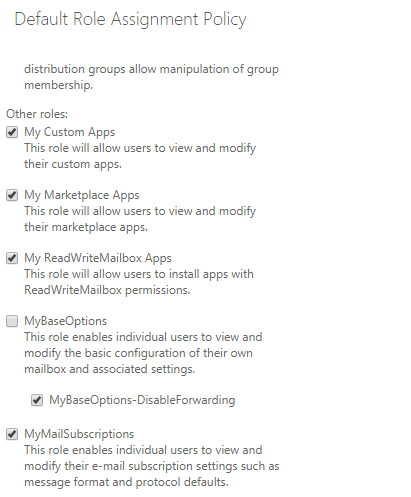
In Exchange administrators control which actions can be performed by the users through Role Based Access Control. To remove the option shown in the picture above you need to modify the Default Role Assignment Policy. The Default Role Assignment Policy contains a Management Role called MyBaseOptions which is holding the parameters responsible for the forwarding and letting users perform the desired changes through the graphical interface of OWA by running Set-Mailbox on the background :
DeliverToMailboxAndForward
The DeliverToMailboxAndForward parameter specifies the message delivery behavior when a forwarding address is specified by the ForwardingAddress or ForwardingSmtpAddress parameters.
ForwardingAddress
The ForwardingAddress parameter specifies a forwarding address for messages that are sent to this mailbox. A valid value for this parameter is a recipient in your organization. You can use any value that uniquely identifies the recipient.
ForwardingSmtpAddress
The ForwardingSmtpAddress parameter specifies a forwarding SMTP address for messages that are sent to this mailbox. Typically, you use this parameter to specify external email addresses that aren't validated.
As you can’t modify the build-in role MyBaseOptions, you need to create a new role to replace it with.
Create a new management role based on the MyBaseOptions role:
New-ManagementRole MyBaseOptions-DisableForwarding -Parent MyBaseOptionsRemove the forwarding parameters from the MyBaseOptions-DisableForwarding role
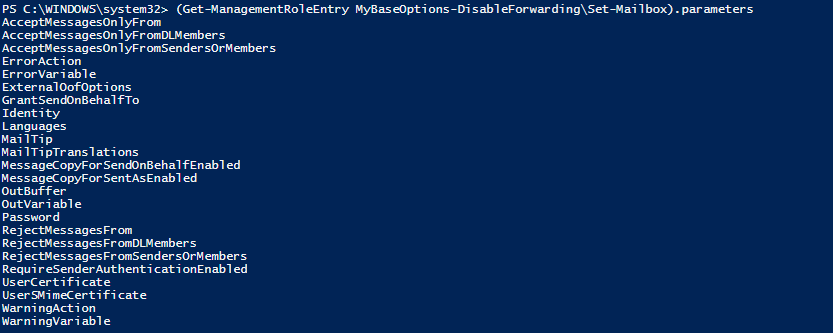
Set-ManagementRoleEntry MyBaseOptions-DisableForwarding\Set-Mailbox -RemoveParameter -Parameters DeliverToMailboxAndForward,ForwardingAddress,ForwardingSmtpAddressNote: If you want to retrieve the parameters that will be left available for the Set-Mailbox cmdlet after the modification of the role which you’ve created:
(Get-ManagementRoleEntry MyBaseOptions-DisableForwarding\Set-Mailbox).parameters
As you have created the role, you have 2 options – modifying the default policy for all users or creating a different policy and assign it to a targeted group of people.
3.1. Modify the Default Role Assignment Policy for all users by replacing MyBaseOptions with MyBaseOptions-DisableForwarding.The easiest way to do this is from Exchange Admin Center > Permissions > User Roles > edit the Default Role Assignment Policy > clear MyBaseOptions and then select MyBaseOptions-DisableForwarding.3.2. Create a new role assignment policy which will contain the MyBaseOptions-DisableForwarding role
New-RoleAssignmentPolicy -Name DisabledForwardingRoleAssignmentPolicy -Roles MyBaseOptions-DisableForwarding,MyContactInformation,MyRetentionPolicies,MyMailSubscriptions,MyTextMessaging,MyVoiceMail,MyDistributionGroupMembership,MyDistributionGroups, MyProfileInformationAfter creating the new policy, you can apply it to targeted user for example:
Set-Mailbox –Identity user@domain.com -RoleAssignmentPolicy DisabledForwardingRoleAssignmentPolicy Note: Give it some time to replicate after the change.The expected result of both of the actions is the following:
Removing any existing auto-forwarding left from before the implementation of the new role
As the forwarding can be set to both internal and external recipients you might want to export a list of the mailboxes which had configured the settings before the Role Assignment Policy modifications. This will allow you to remove only the forwarding to external addresses with precision:
Get-Mailbox -ResultSize Unlimited -Filter {(RecipientTypeDetails -ne "DiscoveryMailbox") -and ((ForwardingSmtpAddress -ne $null) -or (ForwardingAddress -ne $null))} | Select Identity | Export-Csv c:\ForwardingSetBefore.csv -append
If you want to remove any kind of forwarding regardless the location:
Get-Mailbox -filter {(RecipientTypeDetails -ne "DiscoveryMailbox") -and ((ForwardingSmtpAddress -ne $null) -or (ForwardingAddress -ne $null))} | Set-Mailbox -ForwardingSmtpAddress $null -ForwardingAddress $null
Disable forwarding set through Inbox Rules
As the Inbox Rule are frequently created by the users and can’t be blocked on server side (unless you disable the creation of Inbox rules which allow forwarding and redirection as described HERE), you need to disable this on a Remote Domain level.
The cmdlet below will disable the forwarding to all external domains. If you want to restrict this for particular domains only replace you can do so as well.
Set-RemoteDomain Default -AutoForwardEnabled $false
Or you can clear the selection for the Default Remote Domain settings from Exchange Admin Center > Mail Flow > Remote Domains 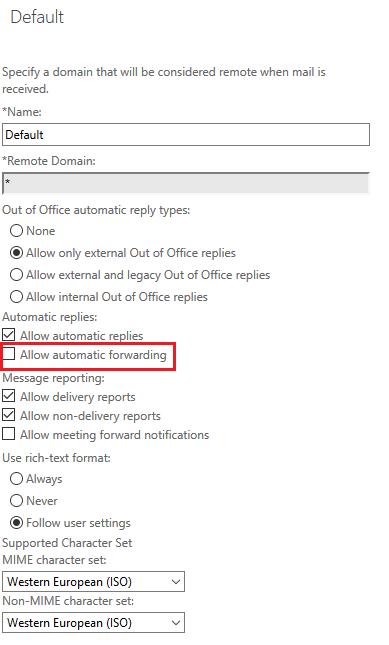
As that setting will be applicable for all newly sent emails but will not eliminate the rules, you can use the cmdlet below will export a list of the mailboxes which have forwarding, redirection or message deletion rules configured, review them and remove them upon demand as well:
foreach ($a in (Get-Mailbox -ResultSize Unlimited |select PrimarySMTPAddress)) {Get-InboxRule -Mailbox $a.PrimarySMTPAddress | ?{($_.ForwardTo -ne $null) -or ($_.ForwardAsAttachmentTo -ne $null) -or ($_.DeleteMessage -eq $true) -or ($_.RedirectTo -ne $null)} |select Name,Identity,ForwardTo,ForwardAsAttachmentTo, RedirectTo, DeleteMessage | Export-Csv c:\temp\InboxRules.csv -append }
Remove-InboxRule -Mailbox user@domain.com -Identity "RuleName"
Note: In case you are facing an issue with corrupted or hidden Inbox rules, yet you still want to remove them, please consult the following article.
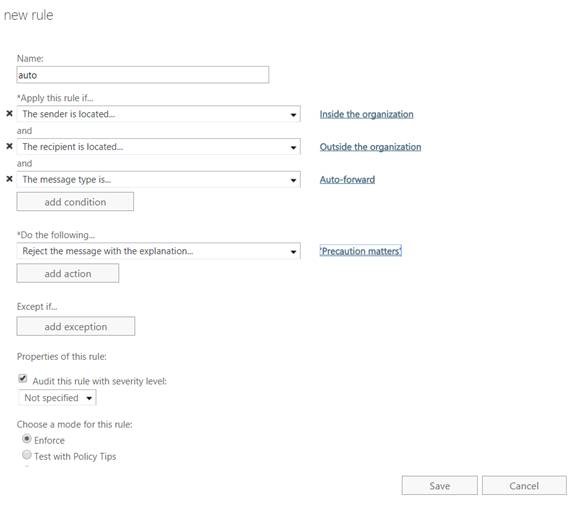
Another option which you might consider, as it will be notifying your users as well, is to configure a transport rule to handle the blocking of any auto-forward message types:
Note: Applying the following action 'Enable Client Rules Forwarding Block Advanced Action' from Secure Score in Office 365 Security and Compliance Center will create a new transport rule for your organization.
It will stop external messages leaving your Tenant, that are of the type AutoForward, mitigating the use of Client created external mail forwarding rules and malicious Remote Domain entries as a data exfiltration vector.
If The Sender is located 'Inside the organization'
If The Recipient is located 'Outside the organization'
If The message type is 'Auto-Forward'
Reject the message with the explanation 'External Mail Forwarding via Client Rules is not permitted'
The steps mentioned above aren't going to be reflected in the Secure Score. In order for you to obtain the Action Score Points you need to apply the rule from Secure Score.