Combating Display Name Spoofing
My lack of updates around these parts can be attributed to the craziness of work over the last few months. This afternoon I have some time and am typing this out as quickly as I can before someone notices and gives me something else to work on. Let’s begin.
I’ve recently seen a very big rise in display name spoofing. With technologies in place like DMARC, DKIM, and SPF, attackers are finding it harder and harder to spoof sending domains. Instead, they have reverted to something quite simple, changing their sending display name to be that of an executive in the targeted organization.
For example, an attacker will register a free email account and use any email address. Sometimes the addresses contain the name of the executive that they are trying to spoof. The attacker would then set their display name to match your CEO or some other executive, and then send phishing messages into your organization. The hope is that the recipient won’t look at the sending address, and instead just look at the sending display name. Some recipients may even assume that the sending email is the personal email of the executive and believe it to be real.
The other problem with an attacker using a consumer email account, or even their own domain, is that all checks like DMARC, DKIM, and SPF will all pass (as long as the records are set up correctly) as there is no domain name spoofing happening.
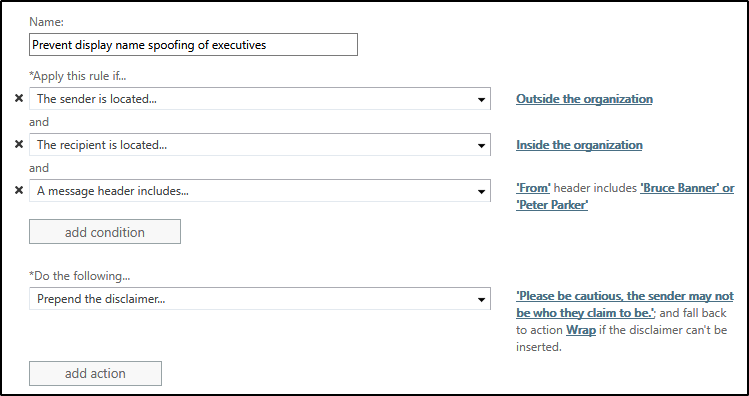
To combat this, I have had customers implement a transport rule that identifies messages that contain the names of key executives in the From field, and which originate from outside of the tenant. The transport rule would look something like that.
Under exceptions, you would add the personal addresses that the executives may use to send mail to the company to ensure those messages aren’t caught by this rule.
The rule is simple and straightforward, but I’ve had customers report having much success with it capturing phishing attempts.
Cheers!