An Introduction to the new Spam Filter Allow and Block Lists
Rather than start this article with an appetizer, I’m going to switch things up and dive right into the meat and potatoes. Very soon, if not already, you will see two new entries in your Spam Filter in Exchange Online Protection, Allow Lists & Block Lists.
As suggested by the name, this is a new way to manage allow and block lists within EOP. These new entries certainly don’t replace using Transport Rules to manage allow and block lists, but instead offer a simpler alternative.
In fact, I would still recommend using Transport Rules when there is a need for more complex allow and block lists. For example, creating a Transport Rule to safe list a partner domain only if the DMARC checks also passes. Or creating a Transport Rule that deletes messages from particular senders or domains for the case where your spam action is set to something other than Delete Message.
New Spam Filter Verdict Values
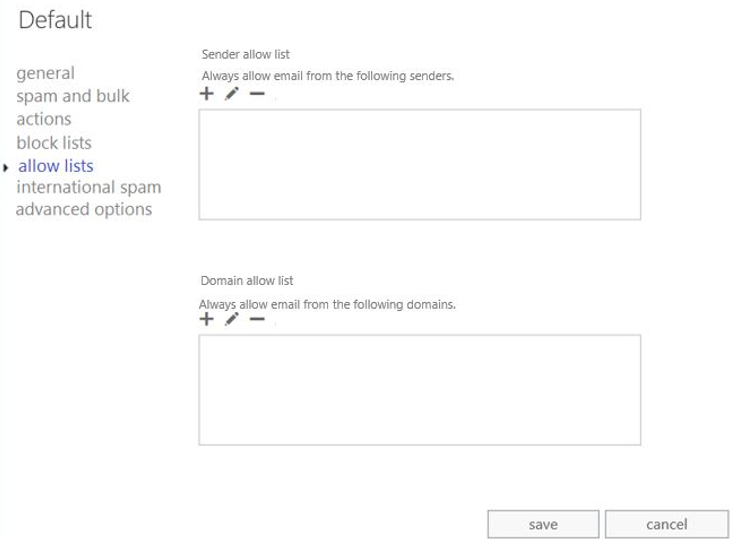
In addition to these new lists, there are new also new Spam Filter Verdict (SFV) values that will be stamped in the X-Forefront-Antispam-Report for senders/domains that are in the Spam Filter Allow and Block lists.
- SFV:SKA - Indicates the sender or sending domain is on the Spam Filter Allow list. You will also see SCL:-1 stamped by EOP.
- SFV:SKB - Indicates the sender or sending domain is on the Spam Filter Block list. You will also see SCL:9 stamped by EOP. In this scenario, the message will take the action set for High Confidence Spam in your Spam Filter.
This is one of the benefits to using the Spam Filter Allow and Block lists. If a message was safe listed or marked as spam because the sender is in the new Allow or Block list, you will see evidence of this right in the message header. Whereas if a safe or block list Transport Rule triggers, you won’t see evidence of it in the header, unless of course you have added that action to the rule – See my previous post Easily tell which transport rules a message triggered.
For reference, we have also updated the Anti-spam message headers TechNet page with these new values.
Enforcement Priority
The enforcement priority is listed below, with the Connection Filter taking the highest priority, and the Spam Filter taking the lowest priority.
- Connection Filter
- End user Safe and Blocked senders
- Exchange Transport Rules
- Spam Filter Allow and Block lists
- Spam Filter
History and when to use
As mentioned above, you can continue to use Transport Rules to manage allow and block lists and completely ignore the Allow and Block lists in the Spam Filter. Think of the new Allow and Block lists as a less complex, and less cumbersome method for managing block and allow strategies.
Also keep in mind the down side of Allow lists. If an attacker spoofs a sender or domain that you have safe listed, they get a free ride to the inbox. For very trusted partners that you would like to safe list, I recommend the Transport Rule listed above to do the safe listing, where it will look not only at the sender, but will also verify that DMARC or SPF checks pass. For these more complex allow scenarios, they will need to stay as a Transport Rules.
Deployment
Spam Filter Allow and Block lists are currently rolling out so if you do not see them yet in your tenant, you soon will.
Cheers!
Resources
Anti-spam message headers
Configure your spam filter policies