Exchange 2013 EDGE as a SmartHost with Basic over TLS authentication
Because I had a recent request to use an Exchange 2013 Edge server as a Smarthost with Basic over TLS I decided to share the steps I took to make this.
Assuming we already have installed the Exchange and Edge server
I started by reviewing this TechNet article :
Configure Internet mail flow through an Edge Transport server without using EdgeSync
https://technet.microsoft.com/en-us/library/bb232082%28v=exchg.150%29.aspx
But I think it lacks some information regarding the certificate issues we might run into.
On the Edge server I created the Send/Receive connectors :
New-SendConnector -name "Outbound" -AddressSpace * -Usage Internet -DNSRoutingEnabled $true
$MailboxCredentials = Get-Credential
New-SendConnector -name "To Wingtip Internal" -Usage Internal -AddressSpace *.wingtiptoys.com -DNSRoutingEnabled $false -SmartHosts Wingtip-e2k13.wingtiptoys.com -SmartHostAuthMechanism BasicAuthRequireTLS -AuthenticationCredentiaI $MailboxCredentials
Set-ReceiveConnector "Default internal Receive connector Wingtip-Edge2013" Name "From Internet" -Bindings 10.1.1.200: 25
New-ReceiveConnector -Name "From WingtipOrg" -Usage Internal -AuthMechanism TLS, BasicAuthRequireTLS, ExchangeServer -Bindings 192.168.0.202:25 -RemoteIPRanges 192.168.0.113
To verify everything was set successfully use :
Get-SendConnector I Format-List Name , Usage , AddressSpaces , SourceTransportServers , DSNRoutingEnab1ed , SmartHosts , SmartHostAuthMechanism
Get-ReceiveConnector I Format-List Name, Usage, AuthMechanism, Bindings, RemotelPRanges
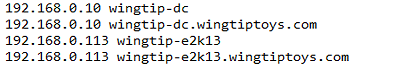
I also made sure that I am able to resolve DNS names so I added some entries in the Hosts file
At this point you have two options :
- create a certificate with a 3rd party Certificate Authority
- create a certificate in the Local Certificate Authority
I chose the second option to work with the Local Certificate Authority.
On the Exchange 2013 server I created a certificate request and included the usual host names I would need, because I want to use this certificate on all services I included more subject alternative names. You have the option to only use the certificate for SMTP communication so you will only need to have both host names in the SAN.
Here is the certificate I created :
New-ExchangeCertificate -PrivateKeyExportable:$true -FriendlyName 'wingtipmail3' -SubjectName 'C=US,S="WA",L="Seattle",O="Wingtiptoys",OU="IT",CN=Wingtiptoys.com' -DomainName @('wingtip-e2k13.wingtiptoys.com','AutoDiscover.Wingtiptoys.com','Wingtiptoys.com','wingtip-edge13.wingtiptoys.com','smtp.wingtiptoys.com','owa.wingtiptoys.com','wingtip-e2k7.wingtiptoys.com','wingtip-e2k10.wingtiptoys.com') -RequestFile '\\wingtip-dc\cert\edgenew2.req' -GenerateRequest:$true -Server 'ba68d970-aaa2-44dd-b303-f2666ea1d8b9' -KeySize '2048'
I went to the Local Certificate Authority and issues the certificate that I enabled for SMTP service
Enable-ExchangeCertificate 6B138B7F7492A3E57BCAD0813BA67CC58DAEF805 -Thumbprint -Services SMTP
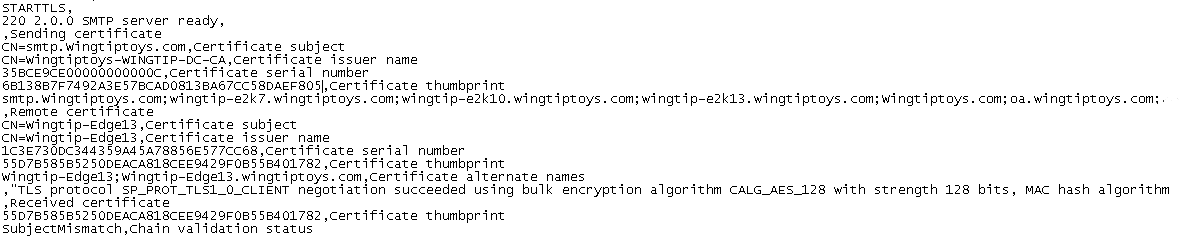
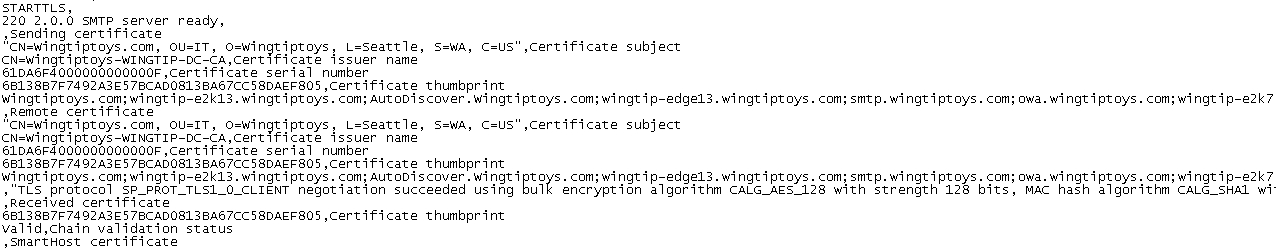
Because I haven't added the certificate on the Exchange 2013 EDGE server I was receiving the error : "SubjectMismatch, Chain validation status"
I then added the certificate on the Exchange 2013 EDGE server and enabled the certificate for SMTP TLS communication.
Import-ExchangeCertificate -FileData ([Byte[]]$(Get-Content -Path c:\certificates\ExportedCert.pfx -Encoding byte -ReadCount 0)) -Password:(Get-Credential).password
Restarted Microsoft Exchange Transport service on the Microsoft Exchange 2013 EDGE server
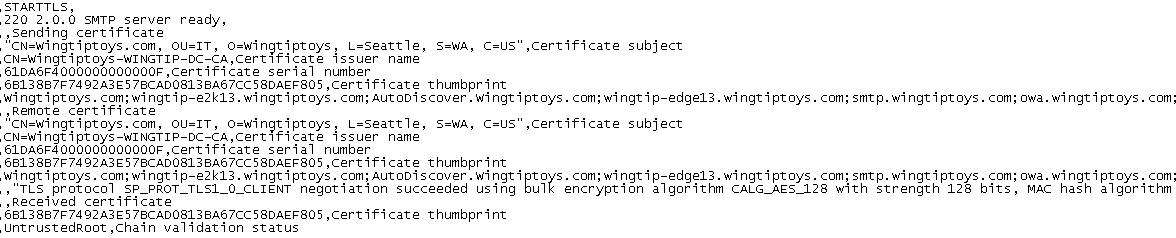
I now get the error "UntrustedRoot, Chain Validation Status"
This is because on the Exchange 2013 Edge server I haven't installed the RootCA certificate and CRL Revocation list from the Local Certificate Authority.
Using PKI on the Edge Transport Server for Domain Security
https://technet.microsoft.com/en-us/library/bb124817%28v=exchg.141%29.aspx
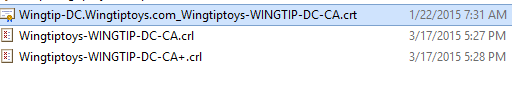
You should be able to get this from the Certificate Authority server \\Server\CertEnroll\
Here is what I found
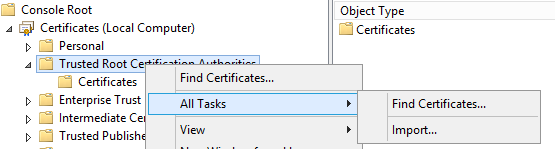
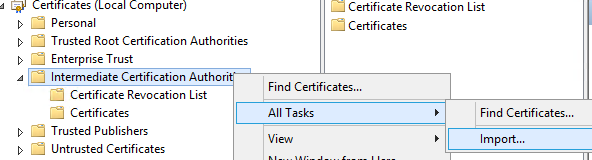
To import this certificate and revocation list please start mmc.exe and add Certificates Snap-in for the Computer Account.
The Root Certificate will be installed in Trusted Root Certificate Authorities with Import
The Certificate Revocation List will be installed in Intermediate Certificate with Import
After I installed the Root certificate and CRL list I had another issue as the credentials I was using to authenticate on the Edge server were not accepted so I had to create a new Local User and add it to Administrators group on the Microsoft Edge 2013 server to use on the Send connector from the Exchange 2013 server.
I am now able to relay emails through my Exchange 2013 Edge server using BasicAuthRequireTLS
If you have any questions please feel free to send an email to cristi.timofte@microsoft.com