Curious Greg builds a Lab–Part I
I remember as a kid those days I would read Curious George and wonder how did he end up there. Well usually the man in the yellow hat had something to do with that. I don’t have a man in the yellow hat but I starting thinking about helping customers (not starting mischief) and I thought it best to start a series on how to transition to the cloud. In the first blog in this series I’ll start with setup of Active Directory Federation Services (ADFS). I do think the first step should be planning but this is going to vary based on your parameters which would take a book to go through all the permutations. So I’ll only focus this series on the technical practicality.
Mark recently posted on some of the requirements for setting up ADFS. Including the guide to setting up ADFS which can be found here.
Setup UPN.
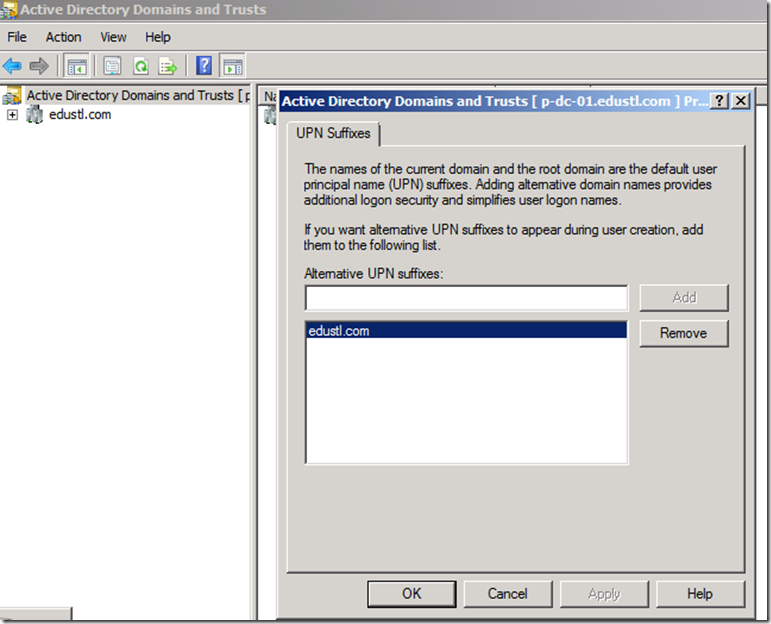
One of the most important pre-req’s for ADFS is to ensure you have identified what the UPN suffix will be and to configure this for each user. In my lab edustl.com is the UPN. Keep in mind that UPNs for federation can only contain letters, numbers, periods, dashes, and underscores.
To configure open ‘AD Domains and Trusts’, Right-Click on on Domains and Trusts and select “properties”. Add UPN suffix and Click “OK”.
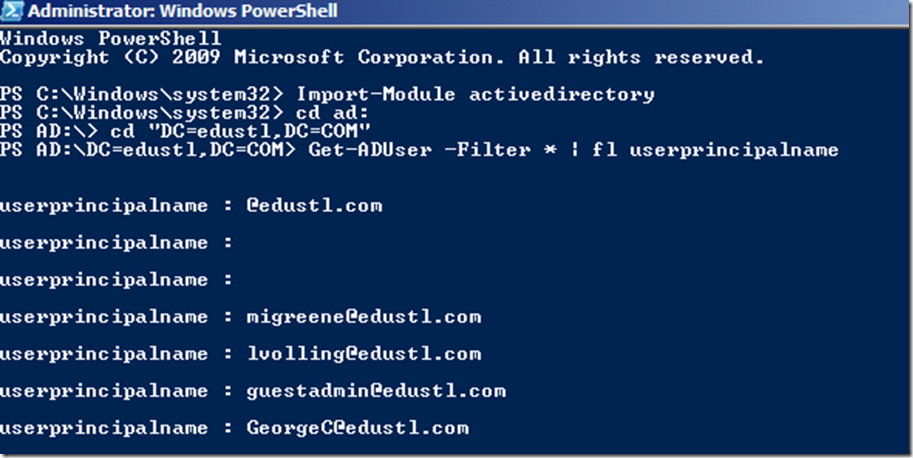
Being a big fan of PowerShell I also check for my users for UPNs.
Today I’m only describing the installation of the ADFS server. A production environment should also have ADFS Proxy servers for security.
Create DNS records for your ADFS environment. Since I only have the 1 ADFS server I did the following:
Create a DNS Host Record for Active Directory Federation Services.
a. On DC1, click Start, point to Administrative Tools, and then click DNS.
b. Expand DNS Server name (XYZ) , expand Forward Lookup Zones, and then click the edustl.com DNS zone.
c. Right-click edustl.com zone and then click New Host (A or AAAA) .
d. In the New Host window, in the Name box, type adfs
e. In the IP address box, type 192.168.1.211 (whatever your IP Address is) and then click Add Host.
f. In the DNS dialog box, click OK.
g. In the New Host window, click Done.
h. Close DNS Manager.
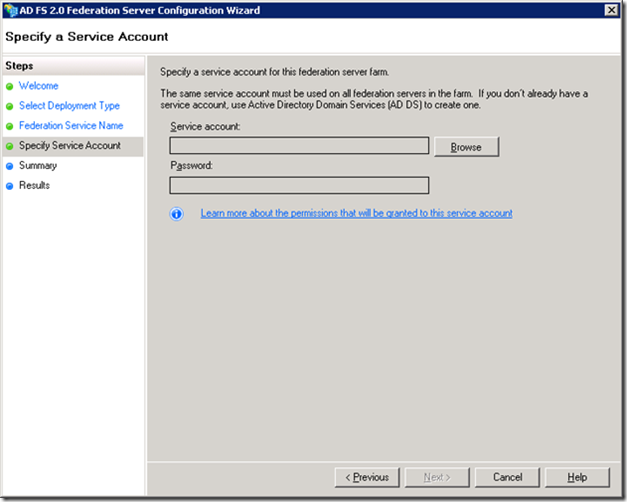
Service account.
Next step is to create a service account for use with ADFS, this can be a domain user account – no special permissions need to be added.
a. Create service account for ADFS – this can be a regular Domain User, no special permissions needed.
b. Add internal ADFS server to AD forest.
IIS and Certificate.
Download and Install ADFS
· Download ADFS 2.0 (here). During the install process, the following Windows components will be automatically installed:
o Windows PowerShell
o .NET Framework 3.5 SP1
o Internet Information Services (IIS)
o Windows Identity Foundation
· Download Microsoft Online Services Identity Federation Management Tool (64-bit)
· Configure external DNS A record for ADFS Proxy (fim01.exchangefederation.edustl.com)
Installing and configure ADFS 2.0 on internal server:
· Double-click AdfsSetup.exe (this is the ADFS 2.0 download)
· Click Next on the Welcome Screen and Accept the License Agreement
· On the Server Role Option screen, select Federation Server
· Finish the rest of the wizard, this will install any necessary prerequisites
· At the end of the wizard, uncheck box to Start the ADFS 2.0 Management Snap-in
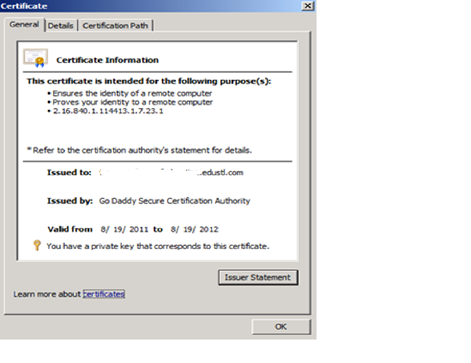
· Request and provision public certificate through Entrust
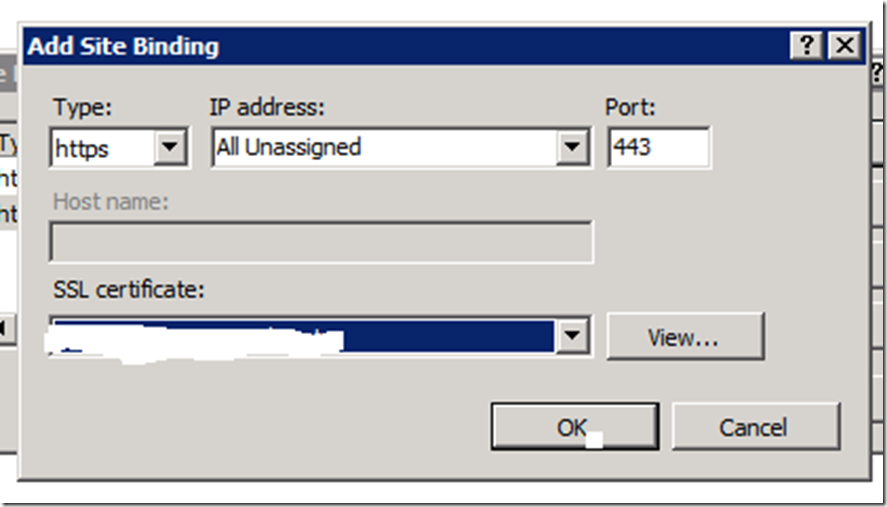
· Bind certificate to IIS on port 443 (remove binding for port 80)
- In Lab we also had to do port mapping for internal server (68.188.39.211 – 172.16.3.52)
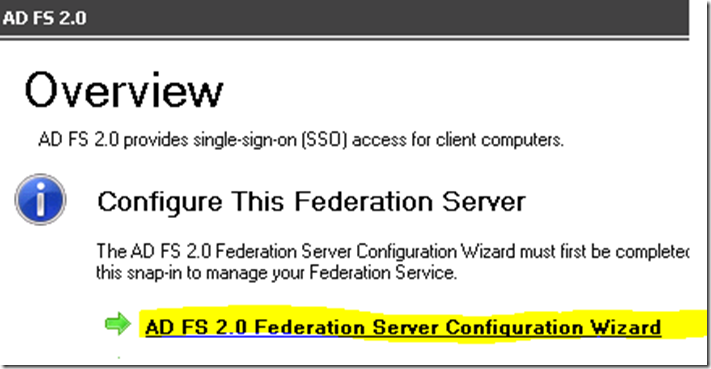
· Configure ADFS utilizing ADFS 2.0 Management
· Select ADFS 2.0 Federation Server Configuration Wizard
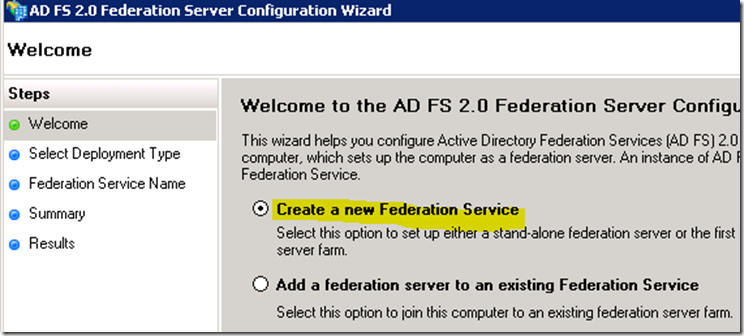
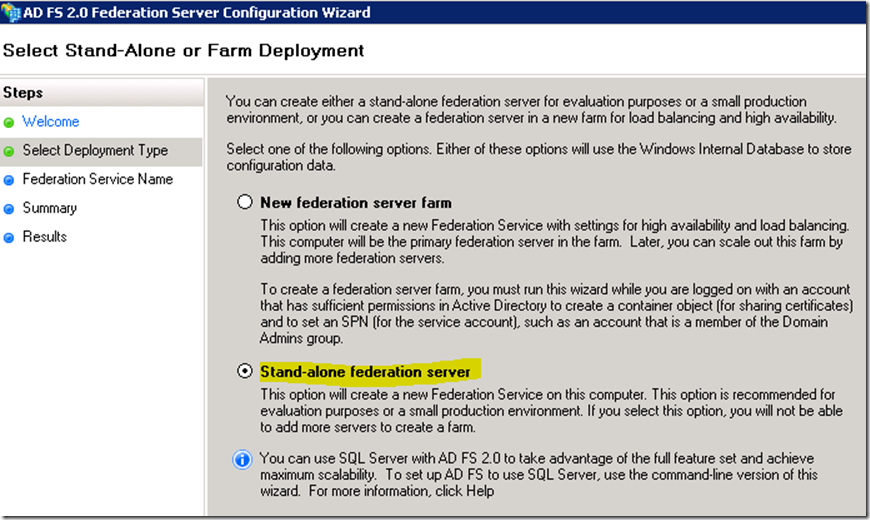
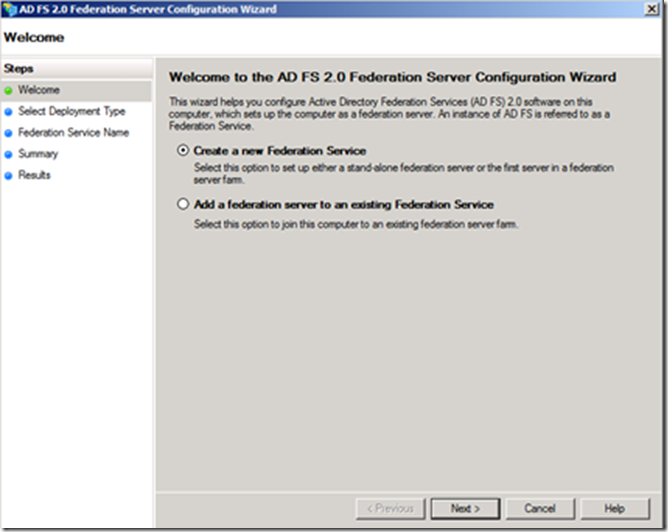
· Select Create a new Federation Service
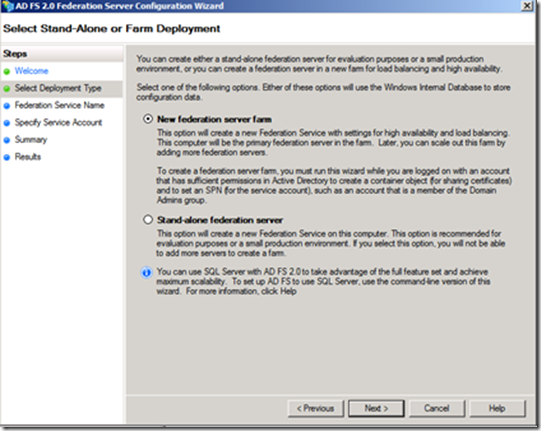
· Select New Federation server farm (during the POC we did a Stand-alone configuration to prevent the need to add a container to the production AD for certificate sharing in the farm)
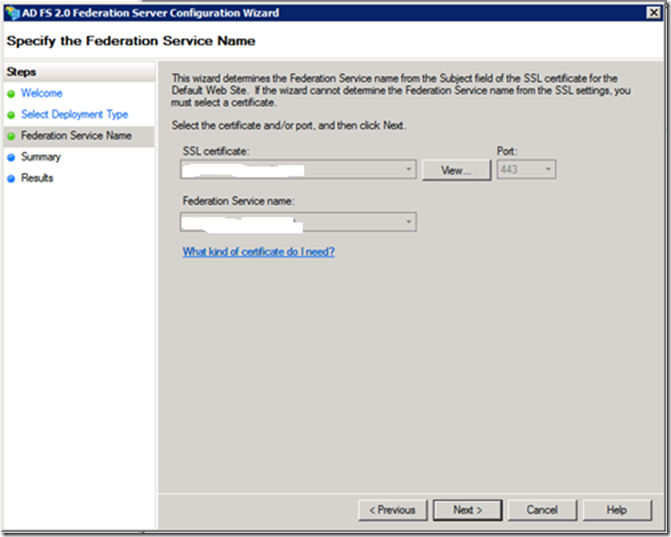
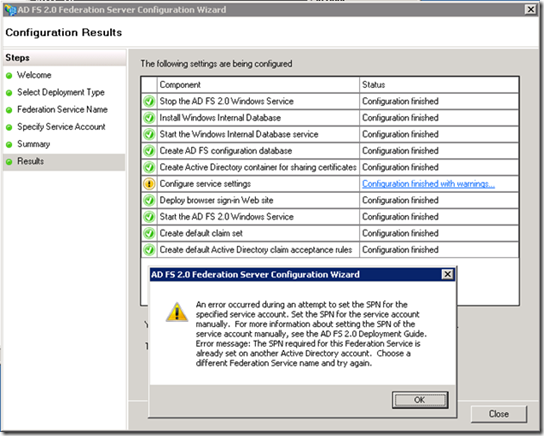
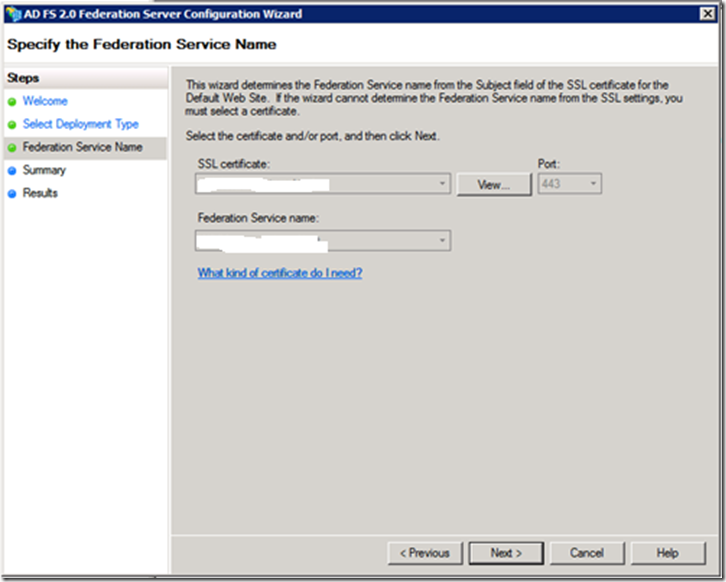
· Select the public certificate and validate the Federation Service name. This will automatically fill in the name on the certificate Subject Name. (My FQDN was horrible as I used an existing VM HINT: Planning is very important! Now I’m stuck with a name I don’t like ![]() )
)
Finish the Wizard.
Run Office 365 Desktop Setup from the Office 365 portal. Unselect all tools (Outlook, Sharepoint, & Lync) to install the Microsoft Online Connector.
· Install Identity Federation Management Tool (FederationConfig.msi, use default install parameters)
The tool could be installed and run on a workstation, but the remote administration for the internal server needs to be activated and configured to trust the workstation.
Enable Identity Federation within Office 365 portal.
Launch the Identity Federation Management Tool
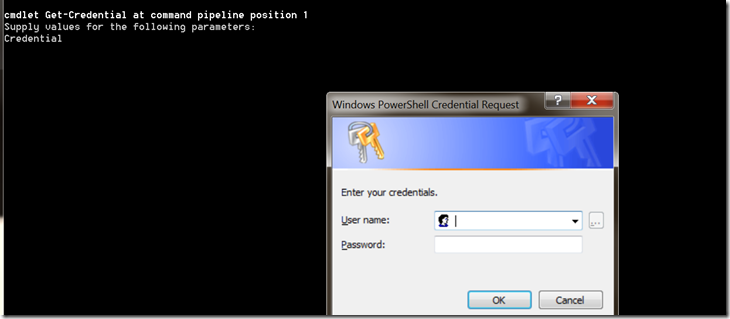
a. Type $cred=Get-Credential and press Enter.
b. Note: It’s a really good idea to setup an admin account that is not part of the domain you are converting to SSO
· Enter you Microsoft Online Services administrator logon and password and click ok (ours was a user@liveatedu.onmicrosoft.com)
c. Use the admin account the is NOT a member of the domain being converted
· Type Set-MSOLContextcredential –msolAdminCredentials $cred and press enter
d. This logs you into the Online Services
· For a new domain - Type Add-MSOLFederatedDomain –domainname edustl.com
· For existing domain - Type Convert-MSOLDomainToFederated –domainname edustl.com (also needed to add service.edustl.com) Ensure not added at first to web admin portal. If it is then you’ll have to ensure no users, mailboxes, or distribution groups are associated with that domain) adding or converting will add the domain to the portal.
· Type Update-MSOLFederatedDomain –domainname edustl.com
e. This updates and activates the SSO
Exit the Federation Management Tool
Check installation.
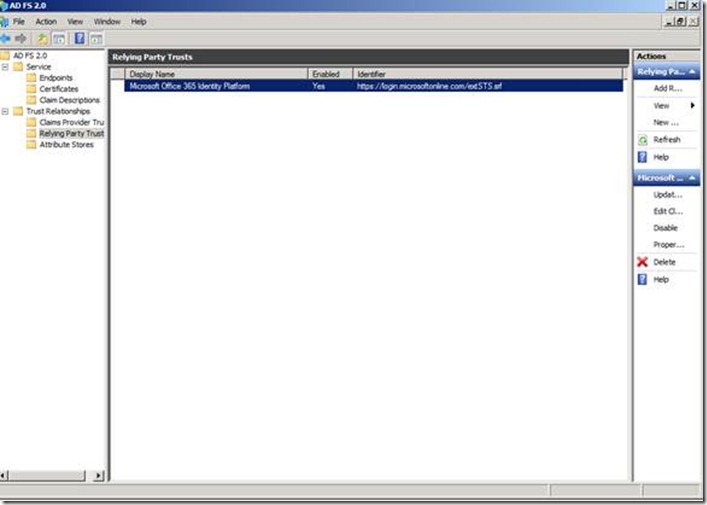
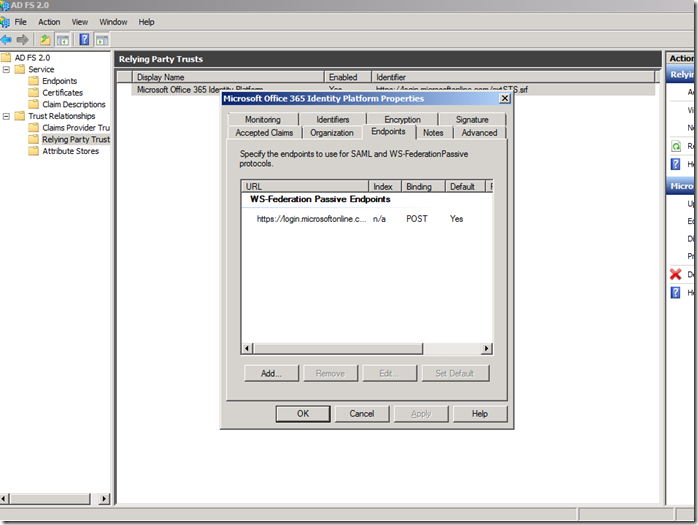
Launch the ADFS Management console and check the Relying Party Trust to see if Microsoft Federation Gateway was added to the list.
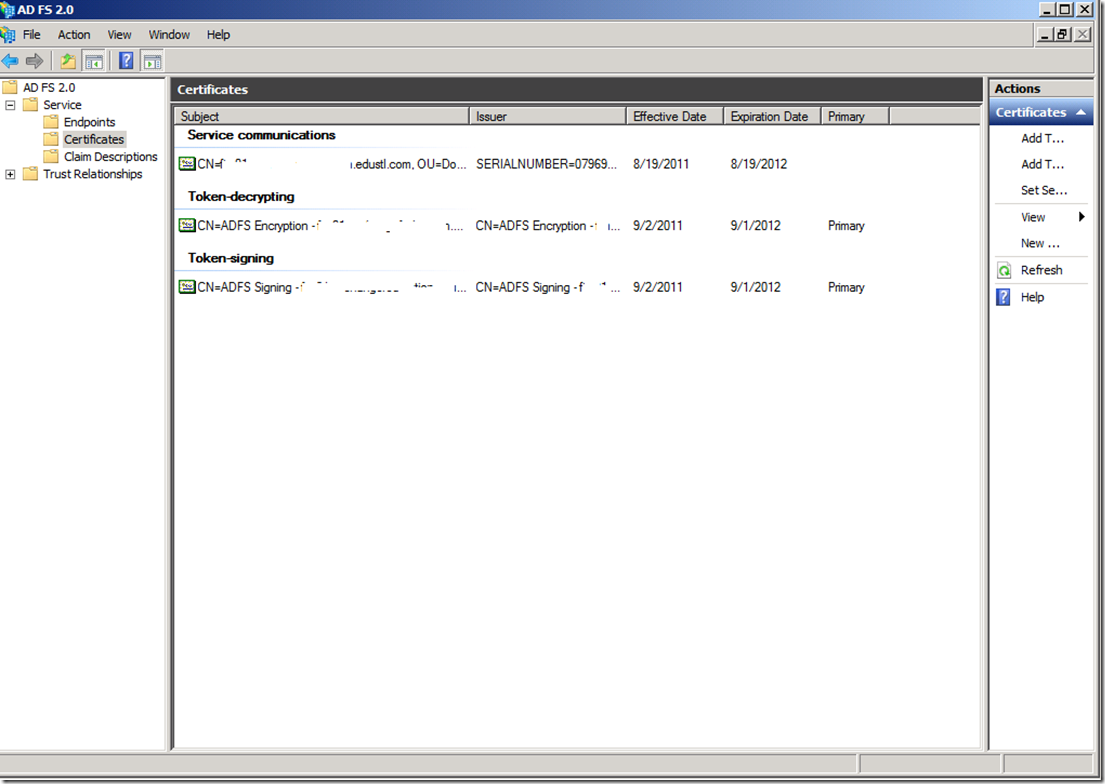
ADFS Server FQDN – my horribly named server. ![]() (In my case I also used the same ADFS server for my account namespace for federation trust – more on that later).
(In my case I also used the same ADFS server for my account namespace for federation trust – more on that later).
Public Certificate – issued by GoDaddy used for the service connector. Other two certificates are self-signed generated as part of the federation trust.
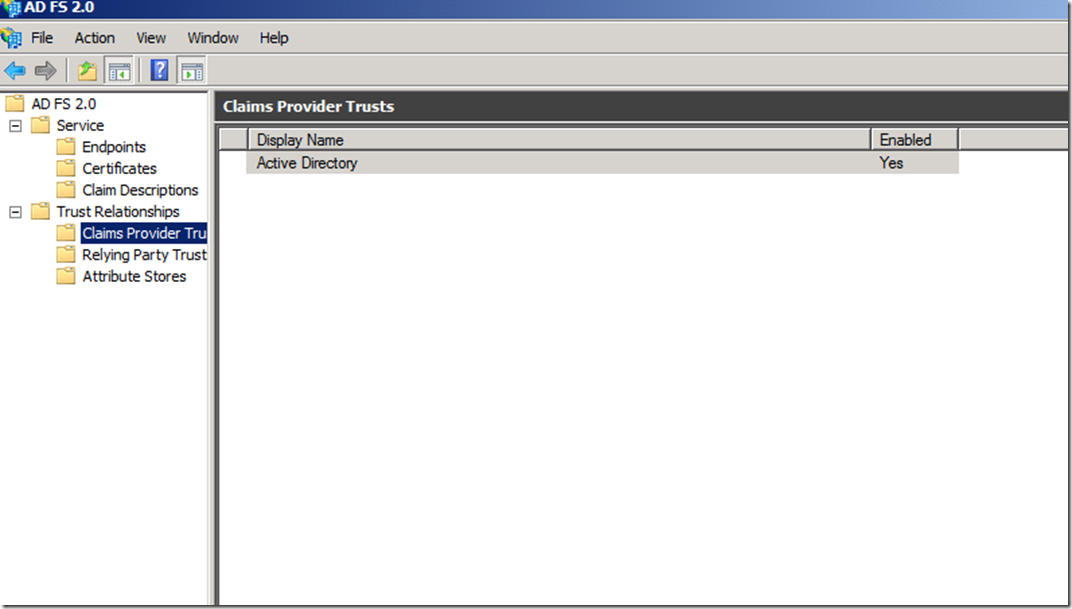
Claims Provider Trust is Active Directory.
Relying Trust is Office 365 iDM platform.
Install ADFS 2.0 Proxy server
- Export public certificate from ADFS internal server and copy to proxy server
- Validate DNS resolution of of your iDP server resolves to internal ADFS server from ADFS Proxy Server (a HOST file can be used for this if needed)
- Validate DNS resolution of UPN resolves to external A record from an internet PC
- Double-click AdfsSetup.exe (this is the ADFS 2.0 RTW download)
- Click Next on the Welcome Screen and Accept the License Agreement
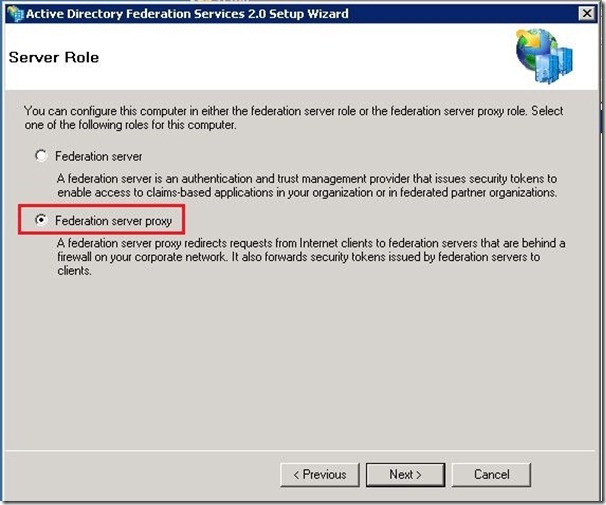
- On the Server Role Option screen, select Federation Server Proxy
- Finish the rest of the wizard, this will install any necessary prerequisites
- At the end of the wizard, uncheck box to Start the ADFS 2.0 Management Snap-in
- Import certificate in IIS and bind certificate to Default Web Site
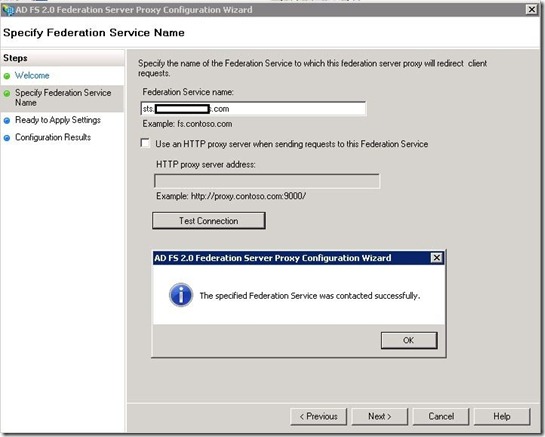
- Configure ADFS proxy by selecting ADFS 2.0 Federation Server Proxy Configuration Wizard
- Finish Wizard
That’s it. Finish ADFS and test.
So the next thing we need to do is setup Dirsync. I’ll discuss this in my next blog. Take care!!!