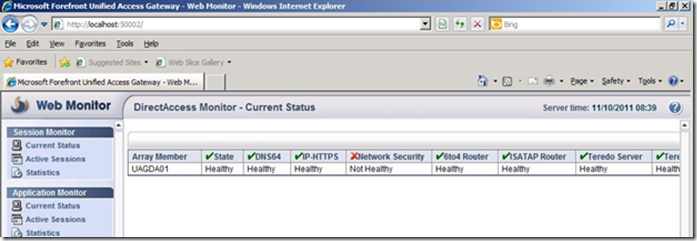
The UAG DirectAccess Web Monitor shows “Network Security” as Not Healthy
Symptom:
When checking the Current Status of DirectAccess using the Web Monitor, you may find that the report shows “Network Security” as Not Healthy.
More Information:
When activating the UAG DirectAccess configuration, the internal interface selected in the UAG DirectAccess wizard is configured with IPsec Denial of Service Protection (DoSP or ipsecdos). DoSP helps to prevent internal computers from being affected by denial of service attack against IPv6-based IPsec computers on your network (i.e. DA clients)
DoSP typically runs on a computer that connects to two or more network, where the networks are Public or Private. If IPSec Denial of Server Protection is not enabled on the interface, the DirectAccess Web Monitor status may show “Network Security” as Not Healthy.
Possible causes:
1. IPSecdos may not be enabled on the Internal ISATAP interface
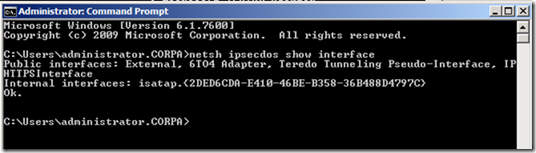
Running ‘netsh ipsecdos show interface’ will the display the list of interfaces with IPSecdos enabled.
For example:
However, you may find that no “Internal interfaces” are listed in the output. If there is no internal ISATAP interface listed, this may be the cause of the problem. To alleviate this problem, you first need to determine the servers’ internal ISATAP interface. Running ‘ipconfig/all’ will display all of the active/usable interfaces on the machine. The internal ISATAP interface will typical have an IPv4 DNS server configured. Once you’ve determined the internal ISATAP interface, run the following command:
Netsh ipsecdos add interface name=”<Friendly name of the interface>” type=internal
Note: Following my example above, the friendly name would equal “isatap.<2DED6CDA-E410-46BE-B358-36B488D4797C>”
2. The UAG servers 6to4 and/or ISATAP interfaces are missing/unusable.
An issue existed in Windows 2008 R2 RTM where, under certain reboot scenarios, a new 6to4 and/or ISATAP adapter may be created. Essentially, when the computer restarts, the Plug and Play service shuts down before the process to enable the “reuse” of the 6to4/ISATAP adapter occurs. Therefore, the 6to4/ISATAP adapter cannot be reused after startup so a new, additional 6to4/ISATAP adapter is created.
Normally, the UAG server should have one virtual 6to4 adapter and three ISATAP adapters (one for each of the two physical NICs and one for the SSL tunnel adapter).
If your computer has experienced this issue, you may notice multiple 6to4 and/or ISATAP virtual adapters listed when running ‘ipconfig /all’. If you notice multiple 6to4 adapters listed, you may find that one or more of them may have a Media State of “Media Disconnected”. Additionally, you may notice multiple ISATAP adapters (i.e. 4 or more).
So why does this cause so much grief for UAG DirectAccess? When UAG DirectAccess is configured, Enabled and Activated, it queries the available adapters and creates the DA policy and forwarding statements based on these interfaces. This includes the ‘useable’ 6to4 and ISATAP interfaces that are available when DirectAccess is Enabled.
If your server experiences this issue during a reboot, the new ‘reusable’ interfaces that are created do not have ipsecdos enabled by default.
Steps to correct the issue:
Typically, there are two avenues you can take. The first is to ‘clean up’ all the 6to4 and ISATAP interfaces, and allow them to be recreated. The second is to configure DirectAccess to make use of new “useable” interface<s> available; while leaving the original ‘non-reusable” interface intact. Both of these steps will enable ipsecdos on the new ‘reusable’ interface<s>.
1. Clean up the interfaces
a. Open the UAG console, select DirectAccess and click the Disable button. After DirectAccess is disabled, Activate and then close the UAG console.
b. At an Administrative command prompt, run the following command: ‘set devmgr_show_nonpresent_device=1’
c. Open Device Manager and select View-Show hidden devices. Then expand ‘Network Adapters’ and delete all 6to4 and ISTAP adapters listed.
d. Open the UAG console, select DirectAccess and click the Enable button. After DirectAccess is enabled, Activate the configuration.
2. Configure UAG to make use of the new (i.e. reusable) interfaces<s>
a. Open the UAG console, select DirectAccess and click Disable button. After DirectAccess is disabled, Activate the configuration.
b. In the UAG console, select DirectAccess and client the Enable button. After DirectAccess is enabled, Activate the configuration.
Additional information:
This Windows 2008 R2 RTM issue has been addressed in Windows 2008 R2 Service Pack 1. However, it should be noted that process of installing Service Pack 1 and rebooting may put the server in this state again. If so, follow the steps above again to correct the behavior. The issue should then be alleviated moving forward.
Author
Richard Barker - Sr Security Support Escalation Engineer, Microsoft CSS Forefront Security Edge Team