UAG 2010 SP1: DirectAccess Always Managed & Managed Only
Always managed
One of the reasons I really like DirectAccess is that client computers can always be managed, regardless of location. This means that whenever a user turns the laptop on and connects to the Internet, management agents on the client laptop can synchronize with corporate management servers, report on their health status, and download updates.
The user doesn’t have to be in the office in order for the laptop to have the latest patches, the most updated software, and the current policy settings. Desktop managers always know what the state of the laptop is, and don’t have to wait until the user explicitly connects to the corporate network with her credentials.
In addition to these things happening in the background, the user can also perform self-help actions remotely, such as changing an expired password.
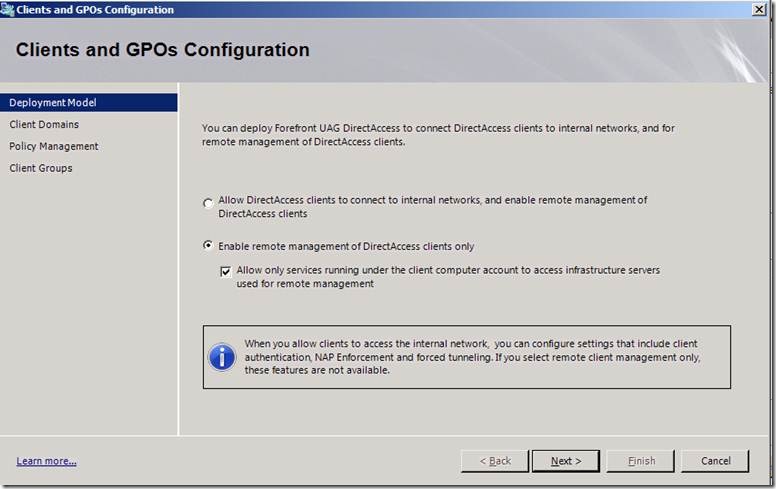
Manage Only
For some customers, having the clients always managed is the trigger for installing DirectAccess, and they aren’t initially interested in the availability of a seamless connection to internal application servers on the internal network. In fact, they want a way of blocking users from connecting to the application servers over the second (intranet) tunnel, allowing only the first (infrastructure) tunnel to connect.
In SP1 we’ve created a simple step in the DirectAccess wizard which enables the admin to select “manage only”. Furthermore, the admin can select to only accept connections from agents or services running under the machine account, while dropping connections from the logged on user. This is configured by selecting a single checkbox.
Note that some functionality is affected by not having the second tunnel. For example, while NAP monitoring will work, NAP enforcement will not. Force tunneling of client Internet traffic also will not work in the “manage only” mode, because there is no second tunnel to send the user traffic through. Similarly, user authentication with username/password; one time password (OTP), and smartcard authentication is not supported. This is because user authentication takes place when creating the second tunnel, which is not created in this mode.
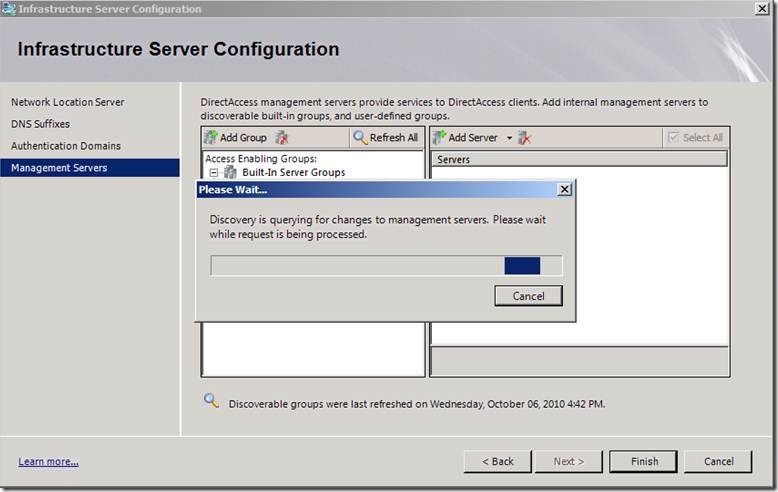
Auto-detecting management servers
Managing the list of servers on the infrastructure tunnel becomes all the more important in the “always managed” scenario. In SP1 we added auto-detection of NAP Health Registration Authority (HRA) servers and of System Server Configuration Manager (SCCM) servers, so that you can refresh the list and any change in the servers is detected.
We have already received some positive feedback from our early adopter customers around these features, and we hope you find them useful as well.
Noam Ben-Yochanan