Publishing Forefront Security Management Console through IAG 2007
1. Motivation
Recently I received a question from a customer about how to securely access the Forefront Security Management Console from the Internet. His specific request was:
“We have a 24x7 Security Team and they often travel to visit our remote branch offices. While they are traveling they stay in Hotels and connect to the VPN when it is necessary. There were already situations that those guys were unable to connect to the VPN using L2TP/IPSec because of restrictions in the Hotel’s Firewall. We are looking for a central solution where the remote engineer can quickly manage the security state of the servers by connecting to Forefront Security Management Console from outside without using VPN and allowing access only for the administrators. The solution needs to verify if the computer where the remote engineer is connected from is compliance with our security policy. We currently have IAG 2007 and some applications are already published in the Company’s Portal.”
Reading this request it was clear that the customer was looking into the right place to accomplish that. Since he already has an IAG 2007 Portal what we need to do is address the following point: “…manage the security state of the servers by connecting to Forefront Security Management Console from outside without using VPN for the administrators only”.
2. Reviewing Forefront Security Management Console Configuration
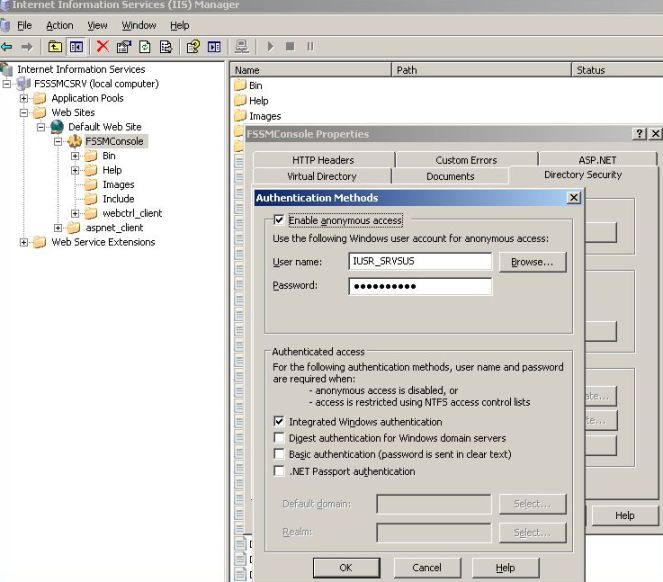
This article assumes that you already have the FSSMC installed and working fine internally. For more information on how to deploy FSSMC in your environment review the Forefront Server Security Management Console – Deployment Guide at Microsoft TechNet. With this assumption, review the IIS configuration for the FSSMC to see how it is configured the authentication and the ports that are listening to.
Figure 1 – IIS Console in the Server that has the FSSMC installed.
3. Creating the Application in the IAG Portal
Open the HTTPS Portal and under the Applications follow the steps below:
1) Click in Add and the window below will appear:
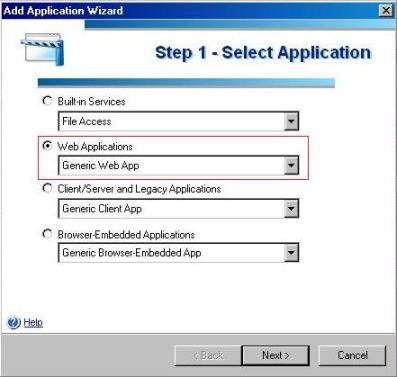
Figure 2 – Choosing the application that you want to publish.
2) Select the option Web Application, choose Generic Web App and click in Next.
3) In the step 2 fill the options according to the window below. Notice that the option All Users Are Authorized is unchecked. This is due the requirement to allow only the administrators to access this application. After finish this window, click in Next.
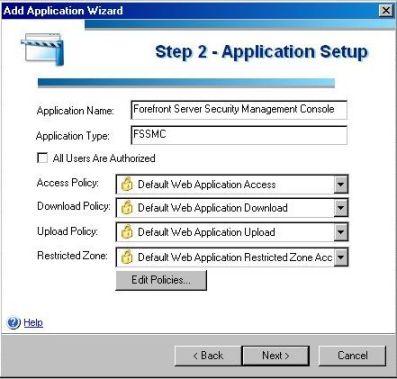
Figure 3 – Application Setup.
4) The step 3 will be to add the FSSMC Server’s name, path and port(s). Before type the address in this window, make sure that you can browse this path from the IAG box itself. After that click in Next.
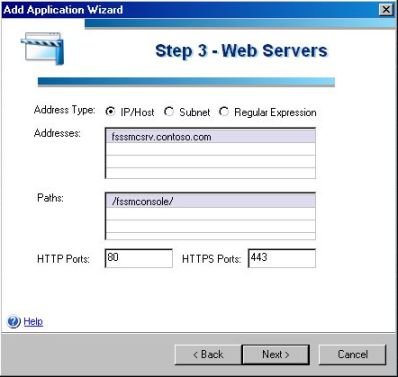
Figure 4 – FSSMC name (FQDN) and ports.
5) In the step 4 you will select the authentication method that IAG will use to reply the web server’s request. Click in Add and choose your Active Directory Repository.
Note: we are assuming that you already have your authentication repository created. In this particular case we are using the name AD, but you can use any other name.
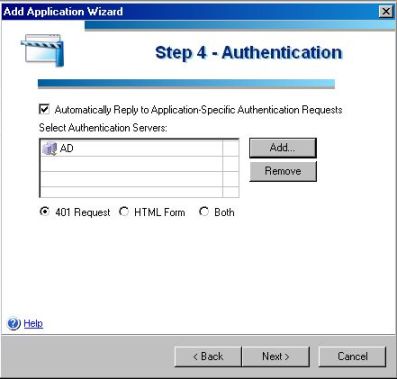
Figure 5 – Authentication.
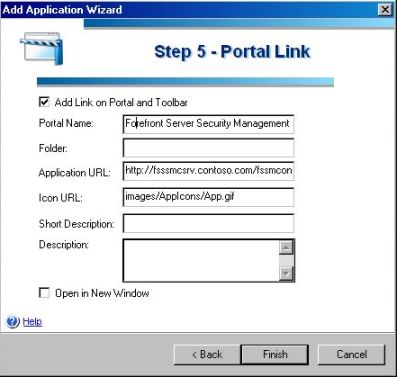
6) The final step in this wizard is to type the portal name and review the link (application URL). Click in Finish.
Figure 6 – Portal Link.
Now the application is already created the next step is to review the authorization.
4. Authorization
Following the request from the customer, the next step is to configure which group of users has authorization to launch this application. Open the properties of the application and follow the steps below:
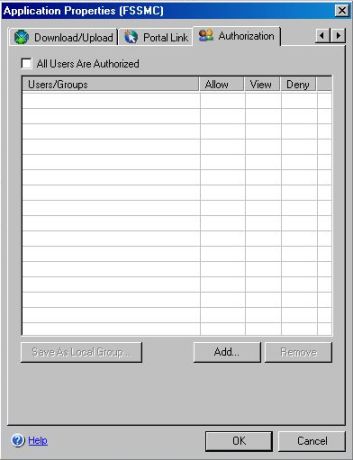
1) Click in the Authorization tab and the following window will appear:
Figure 7 – Authorization window.
2) Click in the Add button.
3) In the Look in option, choose AD (which is the repository name that I’m using for this application). Double click in the Users container and choose Domain Admins. Click in Add and click OK.
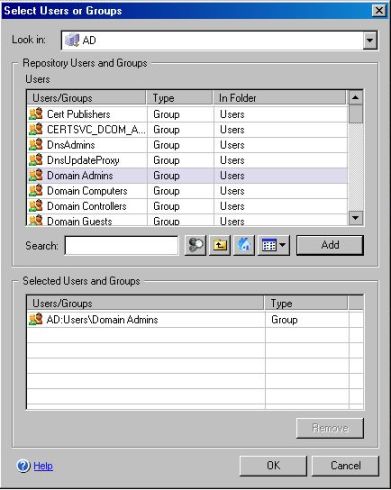
Figure 8 – Users and groups.
4) Notice that the Authorization window will appears like the one below:
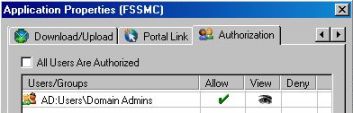
Figure 9 – Authorization window.
5) Click OK.
Now that you have the application and the authorization configured, click in the Activate button to commit the changes.
5. Testing
Now when the administrator connects from outside and access the application, the Forefront Security Management Console appears in the IAG window like this:
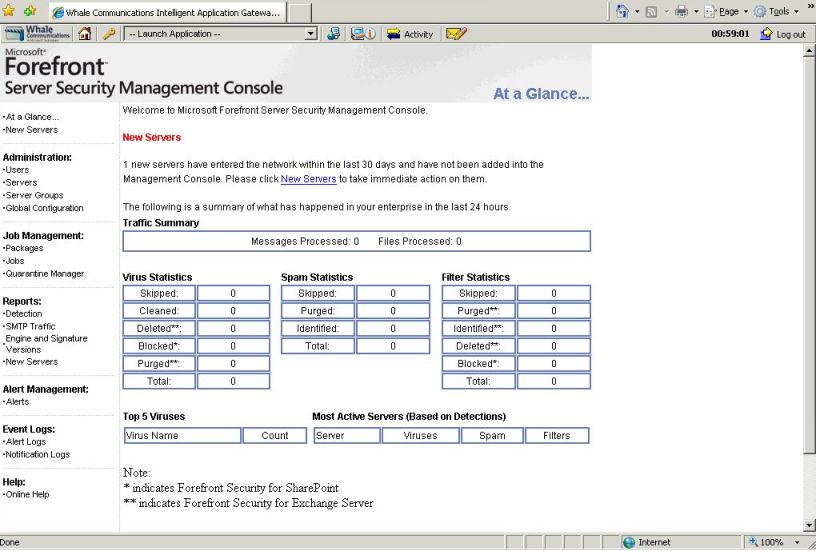
Figure 10 – Accessing FSSMC from IAG.
6. Why not use ISA Server for this solution?
This sound like a MCSE Exam question: choose the most appropriate answer according to the scenario. In this case it is simple to identify the points that makes IAG the correct solution. Let’s review the customer’s requirements:
Requirement |
Why Not ISA? |
IAG, why? |
“..a central solution” |
Customer doesn’t want to access multiple URLs. He wants to connect to a single place where he can launch the applications from there. |
Customer already has an IAG portal implemented. Only one single location and single portal is already in place. |
“The solution needs to verify if the computer where the remote engineer is connected from is compliance with our security policy.” |
It doesn’t do endpoint security policy compliance. |
It allows you to configure endpoint security policy detection very granular. |
What option you will choose for the final deployment will really vary according to your customer’s need. It is important to look at all aspects of the solution so you can address all their needs. There will be situations where the ISA will cover aspects that IAG will not cover. For more information about considerations when to use one or the other (better together) review the following articles:
https://www.microsoft.com/Forefront/edgesecurity/iag/en/us/faq.aspx
https://www.microsoft.com/forefront/edgesecurity/iag/en/us/secure-remote-access.aspx
Author
Yuri Diogenes
Security Support Engineer – ISA/IAG Team
Microsoft – TX
Technical Reviewer
Dan Herzog
Security Support Engineer – IAG Team
Microsoft – WA