TPM Lockout
Hello everyone. It’s Rafal Sosnowski from Microsoft Dubai Security PFE Team. Today, I am going to talk about TPM Lockout state.
TPM (Trusted Platform Module) is a small chip on the motherboard (discrete TPM) or part of the CPU implementation (firmware TPM) which can be used to securely store small amount of information (certificates, private keys, virtual smartcards, Bitlocker keys etc.). That data is completely isolated from HDD and partially from OS thus giving it maximum protection.
To get access to that information from OS level user has to present some kind of authorization value. For example, Bitlocker PIN to get access to the Bitlocker Keys, Virtual smart-card PIN to get access to the certificates and private keys etc.
However, TPM has special anti-hammering logic which prevents malicious user from guessing that authorization data indefinitely. Number of possible PIN failures varies across TPM specification:
- For TPM 1.2 – each vendor has different lockout logic, even different TPM models from the same vendor might have different numbers implemented.
- For TPM 2.0 – specification created by TCG (Trusted Computing Group), clearly states that maximum number of failed attempts should be defined, after which TPM gets locked out. Microsoft defines that maximum number of failed attempts in Windows is 32 and every single attempt is forgotten after 2 hours. This is configured by the Operating System at the time of taking ownership of the TPM
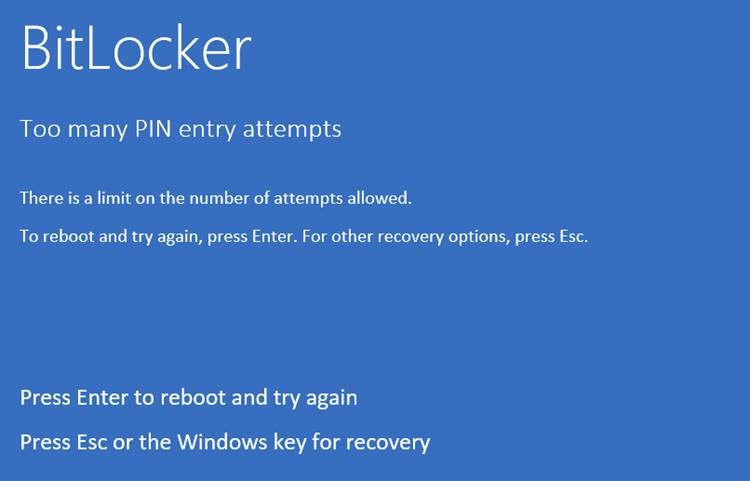
Assuming you failed 32 times to enter correct Bitlocker PIN you will see message saying "Too many PIN entry attempts":
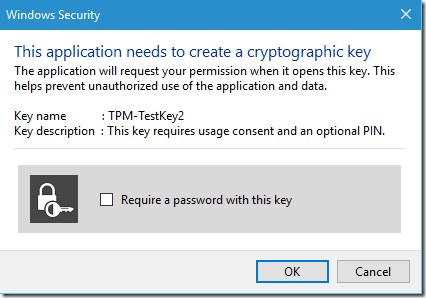
TPM can be locked out by any application / software component that uses keys stored in the TPM and protected by PIN/password. For example, we can produce secure data-blobs, encrypted by the keys generated in the TPM. Access to these keys depending on administrator’s configuration will require or request a PIN:
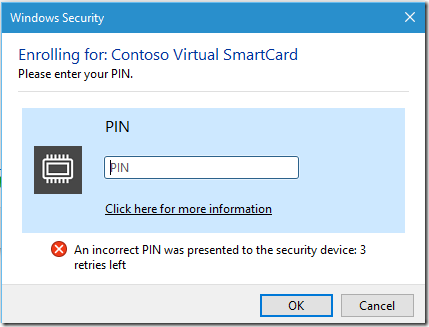
Other example is use of Virtual Smartcards, where certificate alongside with private key is stored in the TPM. Starting from Windows 8.1 , Virtual Smartcards have their own lockout logic, where user has only 5 possible tries. Still, each attempt will increment the TPM counter by 1, but it is less possible that TPM gets locked out.
If your TPM got locked out, it means it will not accept any authorization data, even if it’s correct (correct PIN).
Now you have 4 solutions:
1) Unlock the TPM using the TPM.msc and TPM Owner Password.
2) Wait some time and enter correct PIN (TPM 2.0 will forget 1 attempt every 2 hours)
3) Wait x hours to completely reset TPM lockout counter (for TPM 2.0: 64 hours)
4) Clear TPM (that means all your data stored in TPM will be lost)
If your TPM is locked, you will see its status in the “tpm.msc” as "TPM is locked out" or “Ready for use with limited functionality”. The second status can appear on virtual TPMs and few hardware TPMs which is a glitch.
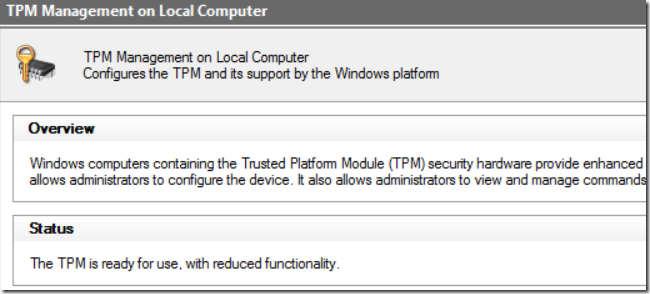
Note: “Ready for use with limited functionality” might also mean that TPM has been initialized by the previous operating system. So it is always better to check the status using PowerShell:
Get-TPM
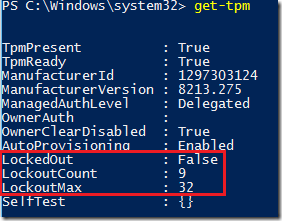
Since Windows 10 (1511) we have added also lockout counters (for TPM 2.0) shown in above screenshot.
To unlock the TPM from tpm.msc you need to be an administrator of the machine and be in possession of the TPM Owner Password. We will talk about TPM Owner Password in details in one of the future posts.
Of course this method will not work when TPM is locked out by Bitlocker PIN (before you get into the Windows). For Bitlocker related lockouts you need to wait as there is no working workflow to unlock the TPM in this scenario, except using other protector, for instance 48-digit Recovery Password to get into Windows.
Some of you probably have already noticed 3 new GPO policies (added in Windows 8) that supposed to influence the TPM build-in anti-hammering logic by introducing some kind of software layer that would accumulate failed PIN attempts before forcing TPM into hardware lockout. Idea is to reduce number of true, hardware lockouts. However, according to my tests these policies don’t work on any of the tested systems (Win8, Win8.1, Win10) so I am trying to get confirmation from our developers what’s going on. Once I get some information I will update this post.
GPO I am talking about can be located in:
Computer Configuration\Administrative Templates\System\Trusted Platform Module Services\
Standard User Individual Lockout Threshold (default: 4)
Standard User Total Lockout Threshold (default: 9)
Standard User Lockout Duration (default 8 hours)
Hope this post was informative for you and I wish you good day.