Consume SPO REST API in PowerShell with ACS App Only Credentials
I was working with customer who wanted to quickly test his App permissions. He first created the App Credentials (Client ID & Client Secret) via https://tenant.sharepoint.com/sites/yoursite/\_layouts/15/appregnew.aspx page.

Then it gave it some permissions via the https://tenant.sharepoint.com/sites/yoursite/_layouts/15/appinv.aspx page.
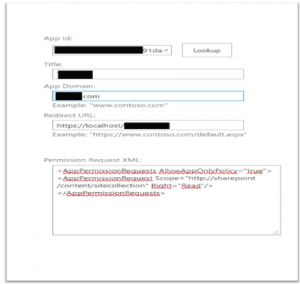
After having created his App, my customer did save its client ID and client secret but didn't save its permissions . He wanted a simple way to check the App permissions and scope : "Scope="https://sharepoint/content/sitecollection" Right="Read".
I proposed him to use the following PowerShell script, which consume SPO REST API via the App credentials :
| #################################################################################### | |
| #This script is provided as an example. It must not be used in Production environment. | |
| #It shows how to obtain a Token to log into the Graph API. The token must be acquired once | |
| #and then stored on the server. Everytime the Graph API is used, it is refreshed before | |
| #being used. | |
| #################################################################################### | |
| Import-Module SharePointPnPPowerShellOnline | |
| Connect-PnPOnline https://<your-tenant>.sharepoint.com/sites/<your-site> -AppId <your_client_id> -AppSecret <your_client_secret> | |
| $PnPAccessToken = Get-PnPAppAuthAccessToken | Clip | |
| $uri = "https://<your-tenant>.sharepoint.com/sites/<your-site>/_api/web/lists/getbytitle('Documents')" | |
| $contentType = 'application/json;odata=verbose' | |
| $Headers = @{} | |
| [Microsoft.PowerShell.Commands.WebRequestMethod]$Method = [Microsoft.PowerShell.Commands.WebRequestMethod]::Get | |
| $Headers["Accept"] = "application/json;odata=verbose" | |
| $Headers.Add('Authorization','Bearer ' + $PnPAccessToken) | |
| $Body = $null | |
| Invoke-RestMethod -Method $Method -Uri $Uri -ContentType $contentType -Headers $Headers -Body $Body |
Indeed, you can modify the REST API : ex: "_api/web/title" to get the title of the spweb and only check the permissions at the Web level.
As you can see this script rely on PnP PowerShell module.
- install it directly in PowerShell :
Install-Module SharePointPnPPowerShellOnline -SkipPublisherCheck -AllowClobber
- install it via an executable file :
https://github.com/SharePoint/PnP-PowerShell/releases
Note: The above script won't work with AAD App Only credentials. You may use the following script for App declared in AAD (and not in ACS).
#####################################################################################This script is provided as an example. It must not be used in Production environment.#It shows how to obtain a Token to log into the Graph API. The token must be acquired once#and then stored on the server. Everytime the Graph API is used, it is refreshed before#being used.####################################################################################
Import-Module SharePointPnPPowerShellOnline
#Connect-PnPOnline
$arrayOfScopes = @("Reports.Read.All")
$ConnectPnPGraph = Connect-PnPMicrosoftGraph -Scopes $arrayOfScopes
$PnPAccessToken = Get-PnPAccessToken
$uri = "https://graph.microsoft.com/beta/" + "/reports/SharePointActivity(view='Detail',period='D7')/content"
# $authHeader = @{
# 'Content-Type'='application\json'
# 'Authorization'= $PnPAccessToken
# }
Invoke-RestMethod -Uri $uri -Headers @{Authorization = "Bearer $PnPAccessToken"}