OAuth Certifcate in Lync Server 2013
When requesting certificates in your Lync Server 2013 environment, you will notice that there is a new certificate type that needs to be requested, OAuthTokenIssuer. What is OAuth and what do we use it for in Lync Server 2013?
OAuth (Open Authorization) is a protocol for server-to-server authentication and authorization. With OAuth, user credentials and passwords are not passed from one computer to another. Instead, authentication and authorization is based on the exchange of security tokens; these tokens grant access to a specific set of resources for a specific amount of time. Lync Server 2013 supports three server-to-server authentication scenarios. With Lync Server 2013 you can:
- Configure server-to-server authentication between an on-premise installation of Lync Server 2013 and an on-premises installation of Exchange 2013 and/or Microsoft SharePoint Server.
- Configure server-to-server authentication between a pair of Office 365 components (for example, between Microsoft Exchange 365 and Microsoft Lync Server 365, or between Microsoft Lync Server 365 and Microsoft SharePoint 365.
- Configure server-to-server authentication in a cross-premises environment (that is, server-to-server authentication between an on-premises server and an Office 365 component).
You can read more about OAuth and it's uses in the Managing Server-to-Server Authentication (Oauth) and Partner Applications TechNet article.
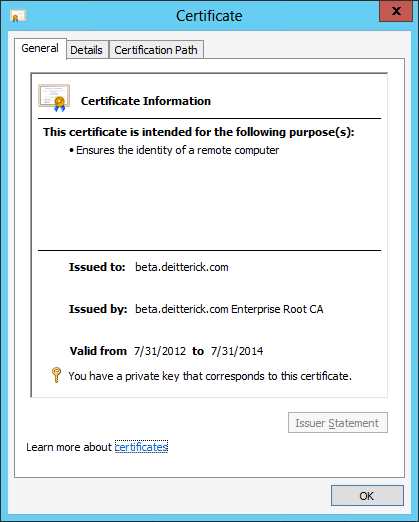
As you complete the request for the OAuthTokenIssuer certificate and view the certificate, you'll see that it looks something similar to:
One important thing to note about the OAuthTokenIssuer certificate, that is different from other certificates in Lync Server 2013, is that the OAuthTokenIssuer certificate is a global certificate:
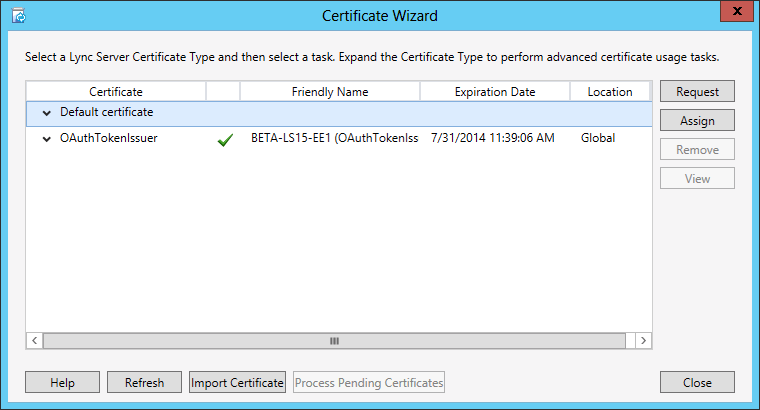
So what does that mean? It means that the same OAuthTokenIssuer certificate needs to be used by all of the Lync Server 2013 servers. In order to assure this, when you assign this certificate, it is replicated via the CMS and is assigned to all of the Lync Server 2013 servers that require OAuth. If you look in the directory where the Lync Server 2013 logs are stored (C:\Users\<username>\AppData\Local\Temp), you will see a log file similar to:
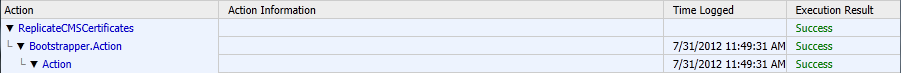
ReplicateCMSCertificates-[2012_07_31][11_49_20].html
If you open that log file it will look something similar to:
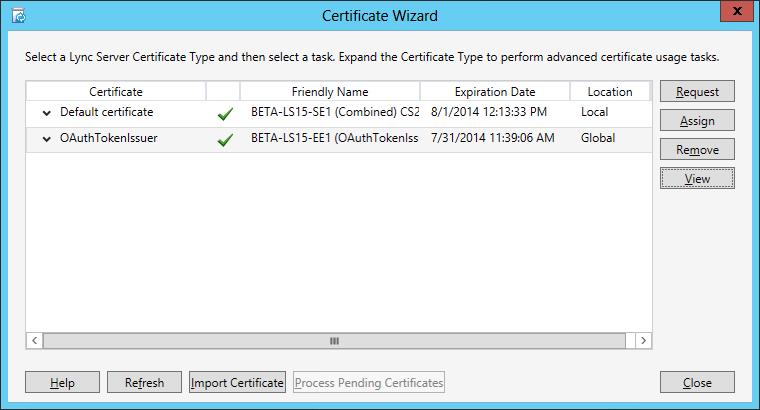
If you wait for replication to succeed and then look at another Lync Server 2013 server, you will see that the OAuthTokenIssuer certificate has been replicated and assigned to that server:
So what happens if I request an OAuthTokenIssuer certificate on multiple servers? In that case whichever certificate is replicated to the CMS last will be used by all of the Lync Server 2013 servers.
So when requesting the OAuthTokenIssuer certificate in Lync Server 2013, remember to only request it once and sit back and let CMS replication take care of the rest!