An approach to automate SCOM service account password change – part 3/3: the script in action
This is part three of my little blog series on how to automate SCOM service account password changes. In part one I set the stage, in part two I explained the individual steps this script performs and now I will show you how the script is working and what result it produces. You can download the script from TechNet Gallery.
CAUTION and NOTE
- This script is a proof of concept to demonstrate how to automate password changes in SCOM. It is neither fully tested nor supported by me or Microsoft in any way. Do not use this script without analyzing the code carefully and maybe adapting it to your needs. Use it at your own risk!
- There are always several way to perform certain tasks. Some are much more elegant than others. I do not claim to always use the most elegant ways in my script *smile*
Ok, let’s get started:
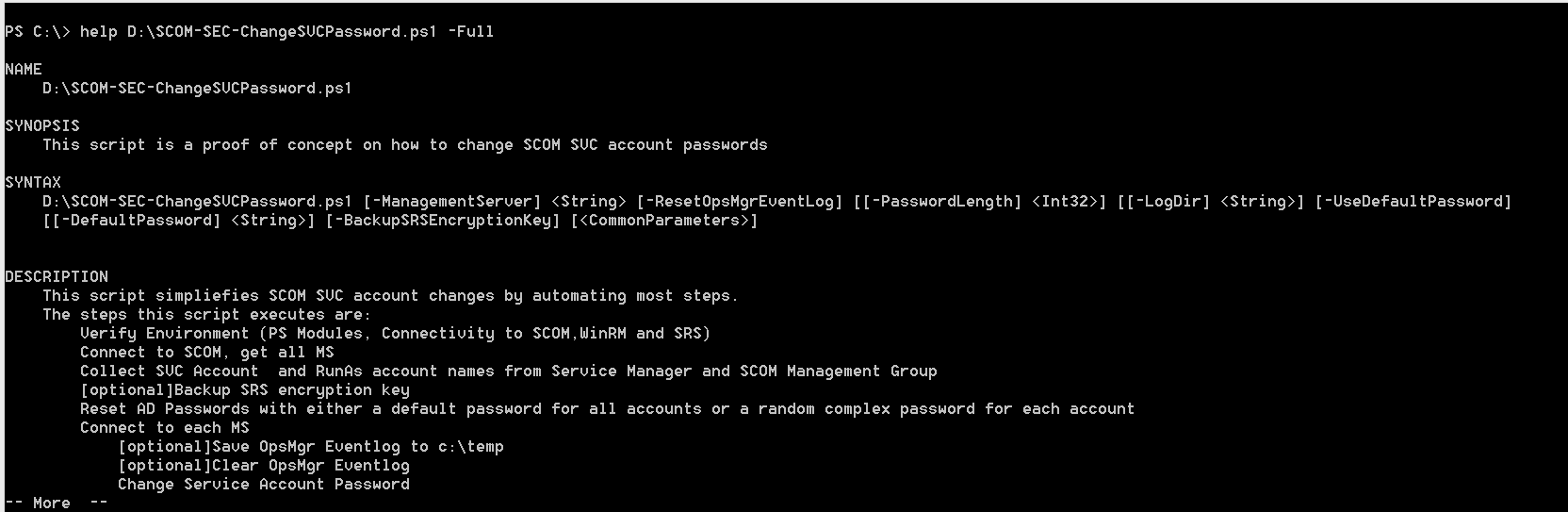
Script help
The script is documented by a command based help:
Script call
Calling the script with random individual passwords (default setting) and backing up the SRS encryption key:
PS> SCOM-SEC-ChangeSVCPassword.ps1 -managementserver myms.domain.com –BackupSRSEncryptionKey
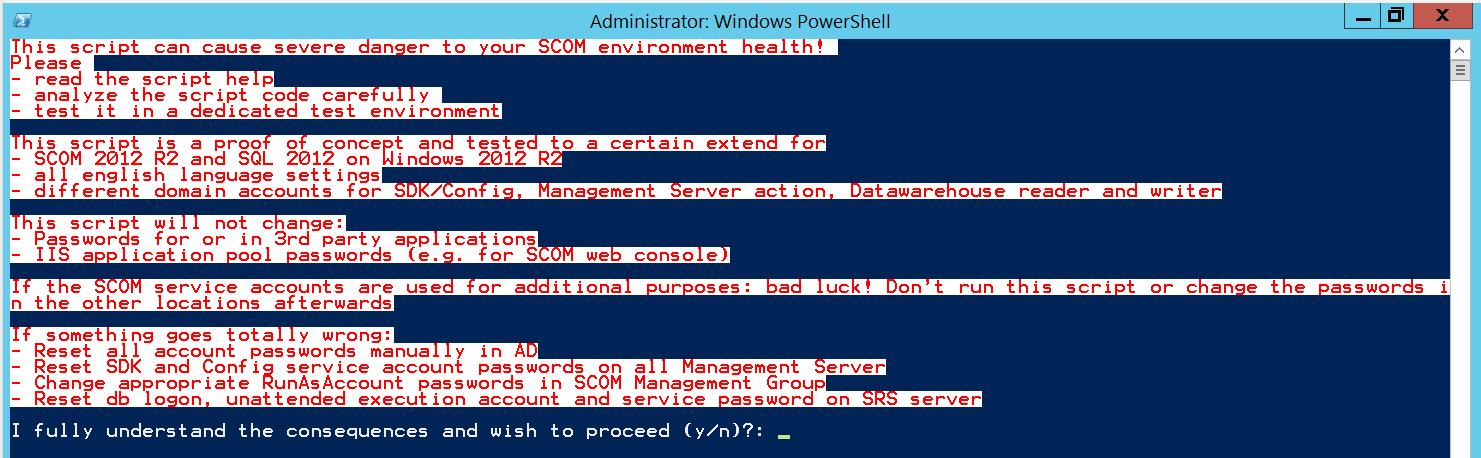
Script consent
To prevent any accidental use of the script:
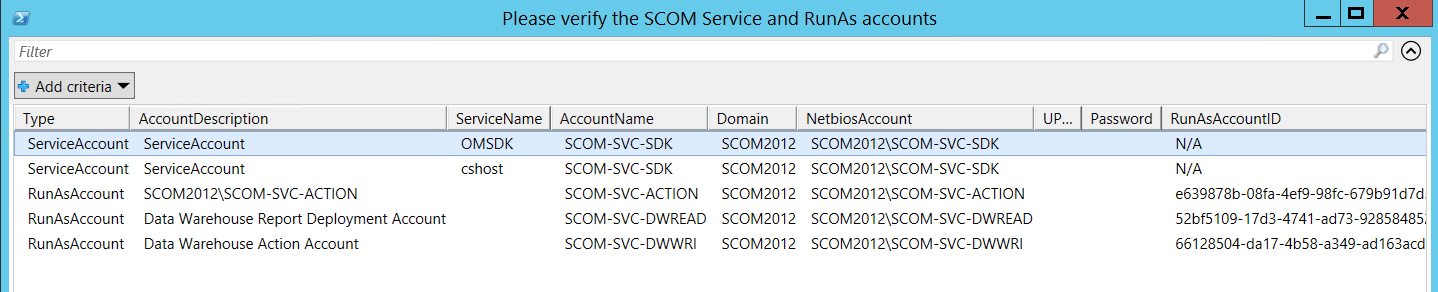
Account verification
After testing the environment and loading the account information the script will present the information to you and ask for your consent:
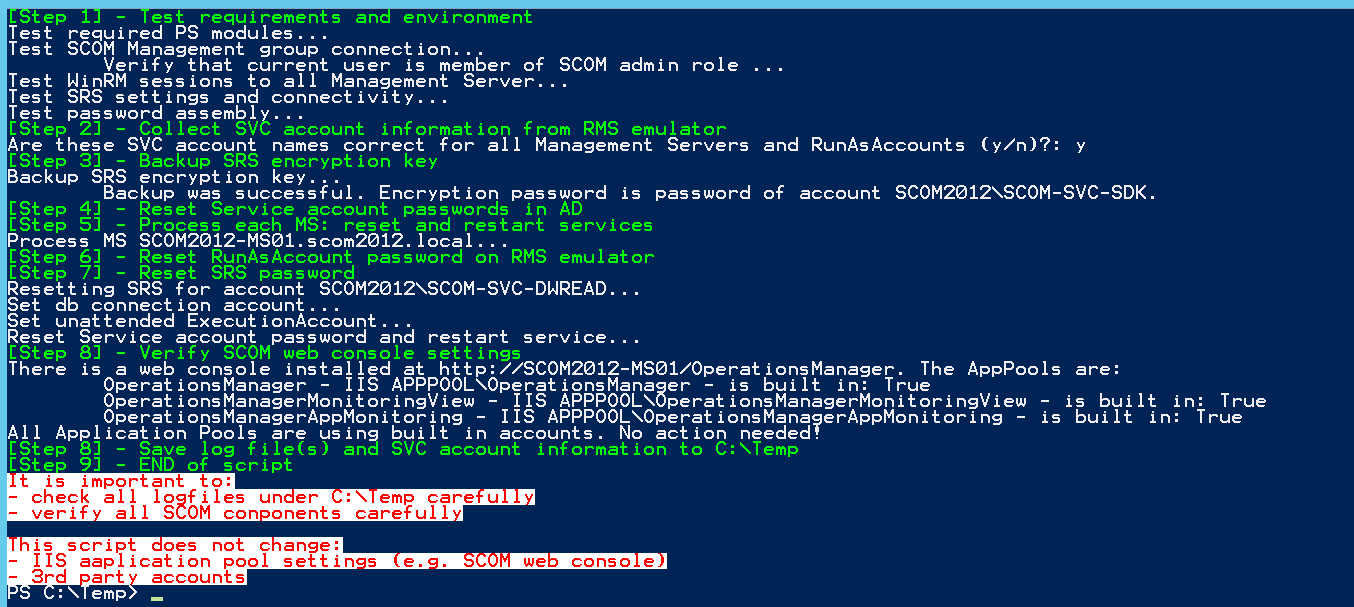
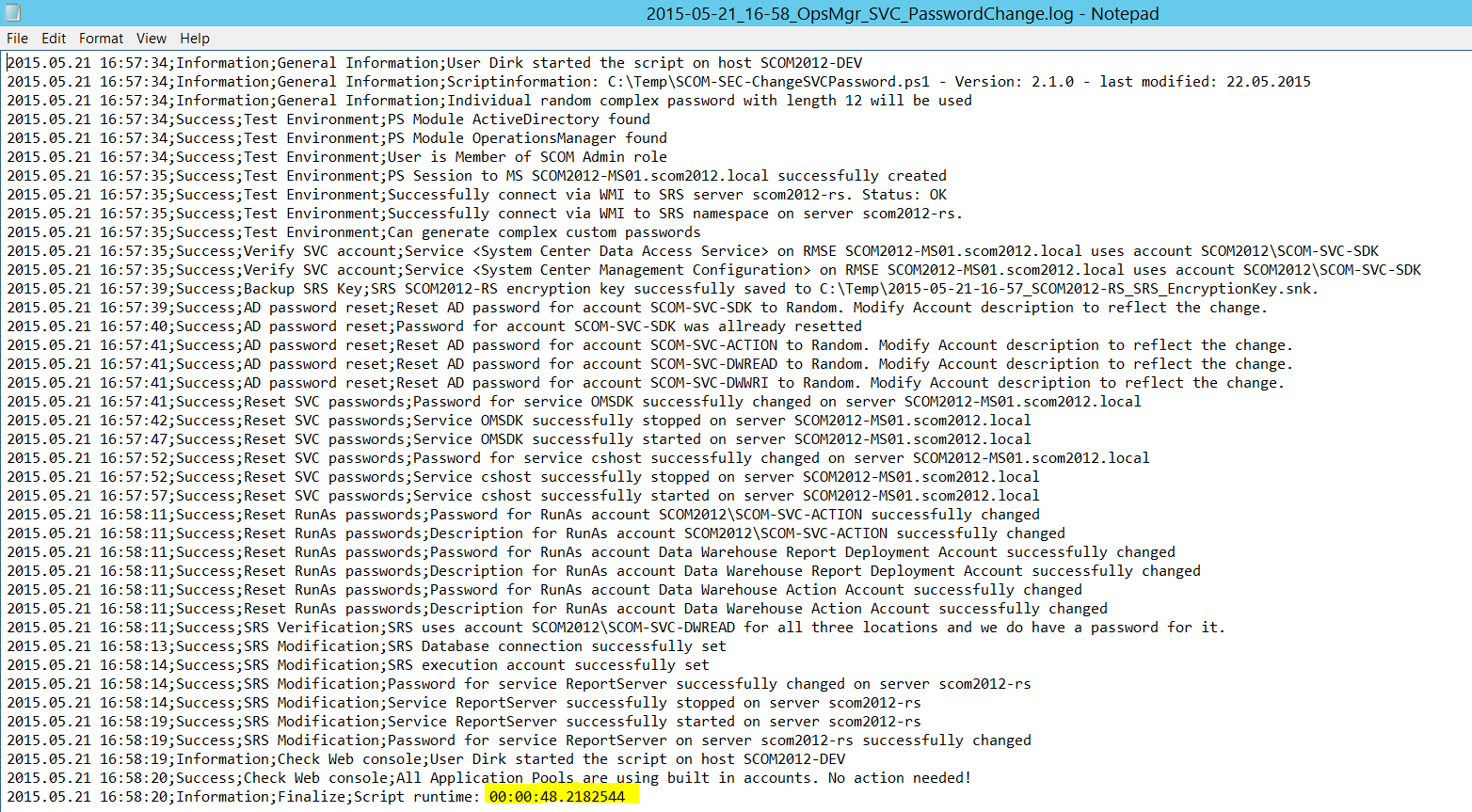
The whole picture
If everything goes fine, you will not get any further consent prompts and the script shell output will look something like that:
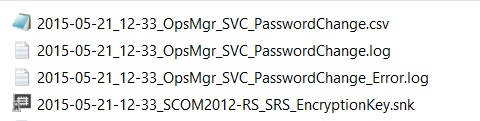
Generated (log) files
The script will generate three or four files:
where
- YYYY-MM-dd_hh-mm_OpsMgr_SVC_PasswordChange.log
contains detailed logging information (without any password information)
- YYYY-MM-dd_hh-mm_OpsMgr_SVC_PasswordChange.csv
contains all account information including the new passwords in clear text - YYYY-MM-dd_hh-mm_OpsMgr_SVC_PasswordChange_Error.log
contains potential PowerShell errors. - [optional] YYYY-MM-dd_hh-mm_[SRS Servername]_SRS_EncryptionKey.snk
contains the SRS encryption key. The password for this key is the password of one of the accounts. Please check the YYYY-MM-dd_hh-mm_OpsMgr_SVC_PasswordChange.log for details
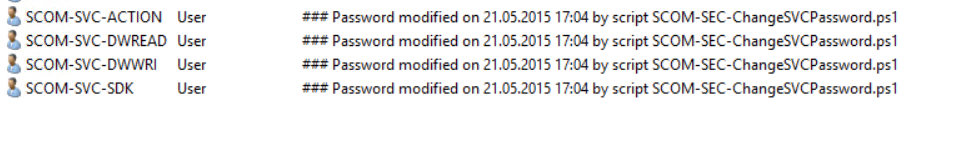
Modifed account description
Each AD account gets a description for better documentation appended:
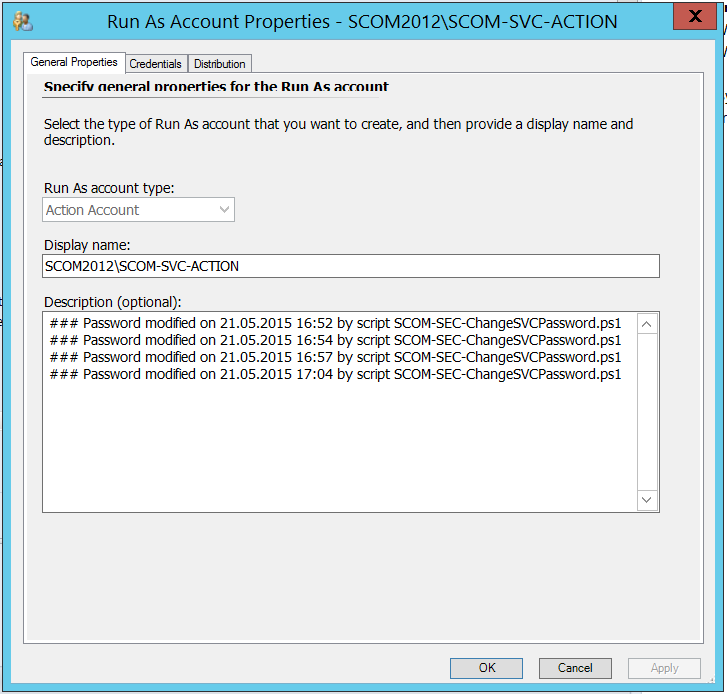
This is also true for RunAs accounts:
Testing and verification
Do not forget to test every single SCOM component after the change! Verify that everything is up and running. If you have 3rd party software which requires password changes as well, please do this now!
Conclusion
By using an automated approach like the demonstrated script
- I can change SCOM service account passwords even in complex environments in under 2 minutes
- Because it is fast it allows more frequent password changes, thus increasing the overall security of your environment
- All steps and actions taken are documented and logged automatically
I hope you found this blog series interesting and it encourages you to create your own automation tools for your SCOM environment(s).
As always I would love to hear your feedback and comments.