Security implications of upgrading to Windows 10
Windows 10 has new security features that protect the system from malicious code being inserted in to the system startup process. The foundation of these security features are UEFI and Secure Boot. UEFI requires a new disk format and device firmware changes. These requirements effect the choices and configuration options when migrating from Windows 7 to Windows 10.
Unified Extensible Firmware Interface
Unified Extensible Firmware Interface (UEFI) controls the boot process of the PC. UEFI can operate in one of two modes: UEFI mode or BIOS-Compatibility mode. When operating in UEFI mode, UEFI verifies the signature of the Operating System bootloader to ensure that no malware (rootkits) have been introduced. When in BIOS-Compatibility mode, UEFI allows operating systems to boot in the same manner as they did under the older BIOS system.
Windows 8/8.1 and Windows 10 logo compliant systems, that shipped with Windows 8/8.1 or Windows 10, will have UEFI configured in UEFI mode. Systems that shipped with Windows 7 are configured to use UEFI in BIOS-Compatibility mode.
UEFI mode requires a different disk format then BIOS. UEFI mode requires disks use the GUID partition Table(GPT) as opposed to the older Master Boot Record(MBR) used in BIOS based systems.
For more information on UEFI see https://windows.microsoft.com/en-US/windows-8/what-uefi
Windows 10 Features that require UEFI
Device Integrity
Secure Boot
Secure Boot is a feature of UEFI that insures a personal computer will only boot software that is trusted by the manufacturer. When the PC starts, the firmware checks the signature of each component of boot software: this includes firmware drivers (option ROMS) and the operating system boot loader. If the drivers or boot loader are not signed with a certificate that is in the UEFI firmware database, the system will not boot.
For more information, see https://technet.microsoft.com/en-us/library/hh824987.aspx.
Early Launch Anti-Malware
Early Launch Anti-Malware provides a Microsoft-supported mechanism for anti-malware software to start before any third party boot drivers. This allows the anti-malware software to control the loading of boot drivers and not allow any unknown or infected boot driver to load.
For more information, see https://msdn.microsoft.com/en-us/library/windows/hardware/dn265157(v=vs.85).aspx
Measured Boot
The Measured Boot feature provides anti-malware software with a trusted (resistant to spoofing and tampering) log of all boot components that started before anti-malware software. Anti-malware software can use the log to determine whether components that ran before it are trustworthy versus infected with malware. The anti-malware software on the local machine sends the log to a remote server for evaluation. The remote server initiates remediation actions either by interacting with software on the client, or through out-of-band mechanisms as appropriate. The remote server is necessary because the software running on the local client is not trustworthy if malicious components, that executed before the anti-malware software, tamper with the anti-malware software. This feature has a dependency on a Trusted Platform Module (TPM) 1.2 being enabled on the system.
For more information, see https://msdn.microsoft.com/en-us/library/windows/hardware/dn653311(v=vs.85).aspx 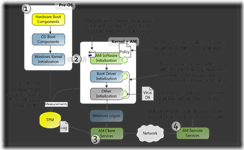
Figure 1: Measured Boot and Early Start Anti-Malware
Virtualization Based Security
Device Guard
Device Guard is a combination of enterprise-related hardware and software security features, that when configured together, will lock down a device, so that it can only run trusted applications. If the application is not trusted it cannot run period.
Device Guard uses the new virtualization-based security in Windows 10 Enterprise to isolate the Code Integrity service from the Microsoft Windows kernel itself, letting the service use signatures, defined by your enterprise-controlled policy, to help determine what is trustworthy. In effect, the Code Integrity service runs alongside the kernel in a Windows hypervisor-protected container.
For more information, see https://technet.microsoft.com/en-us/itpro/windows/keep-secure/introduction-to-device-guard-virtualization-based-security-and-code-integrity-policies
Credential Guard
Introduced in Windows 10 Enterprise, Credential Guard uses virtualization-based security to isolate secrets so that only privileged system software can access them. Unauthorized access to these secrets can lead to credential theft attacks, such as Pass-the-Hash or Pass-The-Ticket.
For more information, see https://technet.microsoft.com/en-us/library/mt483740%28v=vs.85%29.aspx
| Category | Feature | Requires UEFI | Requires TPM |
| Device Integrity | Secure Boot | Yes | No |
| Device Integrity | Early Launch Anti-Malware | Yes | No |
| Device Integrity | Measured Boot | Yes | Yes |
| Virtual Secure Mode | Device Guard | Yes | Yes |
| Virtual Secure Mode | Credential Guard | Yes | Yes |
Migrating from Windows 7
UEFI was available in the Windows 7 timeframe. However, Windows 7 systems typically used UEFI in BIOS-Compatibility mode and MBR disks. This means, that to migrate a Windows 7 system to Windows 10 and take advantage of the new security features, the disk must be repartitioned using the GPT format. The system firmware will also have to be configured to use UEFI mode. Depending on PC vendor, it may be possible to automate the firmware configuration during the ConfigMgr OS deployment task sequence. Repartitioning, during an OS deployment task sequence, requires the system to be on a LAN and that sufficient space is available on a ConfigMgr State Migration Point in order to back up any data on the system. It is possible to detect if a system is on a LAN with sufficient storage, to do the repartition and firmware reconfiguration, or just upgrade, without repartition or firmware reconfiguration, if the system is remote.
This post was contributed by David Hornbaker, a Senior Consultant with Microsoft Services.
Disclaimer: The information on this site is provided “AS IS” with no warranties, confers no rights, and is not supported by the authors or Microsoft Corporation. Use of included script samples are subject to the terms specified in the Terms of Use