Restrict iOS/Android E-mail to Outlook using Conditional Access for MAM
One of the most common discussions I have with customers is how does an IT Pro ensure that corporate data is only being accessed by approved, managed email applications.
Intune Mobile Application Management (MAM) provides a rich set of Data Loss Prevention (DLP) features that ensures no corporate data is leaked outside of the corporately managed apps. The Outlook app for iOS and Android is by far the most popular MAM enabled app, as it provides the most secure and user-friendly experience for accessing Exchange Online.
But how does an organization restrict access to their Exchange Online data to only the Outlook protected app?
Traditionally, we’ve had some very complex solutions utilizing Exchange Allow/Block/Quarantine (ABQ) rules and ADFS claim rules to ensure users can only use the Outlook app. ABQ rules to restrict the client, and ADFS claims to restrict the authentication method, for example.
This month, we released a new feature which will simplify this ask a whole lot – Conditional Access for MAM.
CA for MAM will allow an IT Pro to restrict Exchange Online to only the MAM enabled apps for iOS and Android. All other third party clients (for example, the native e-mail apps on iOS/Android) will not be able to connect to Exchange Online.
The feature is available for MAM Without enrollment (MAMWE), meaning your devices don’t even need to be enrolled to enable this functionality.
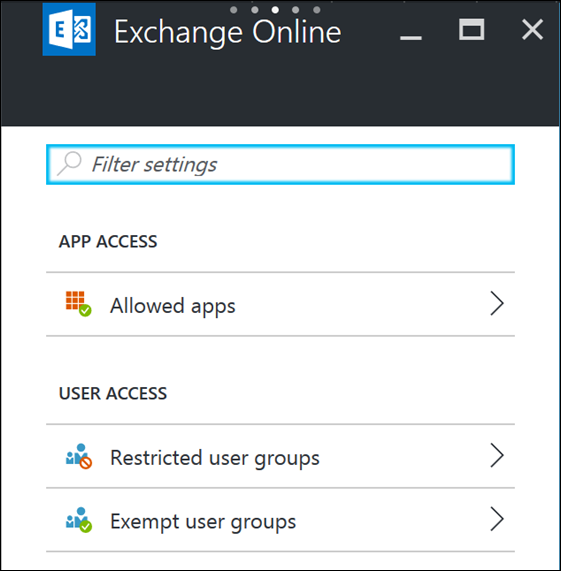
In the new Intune Portal, you’ll see a new blade called Conditional Access 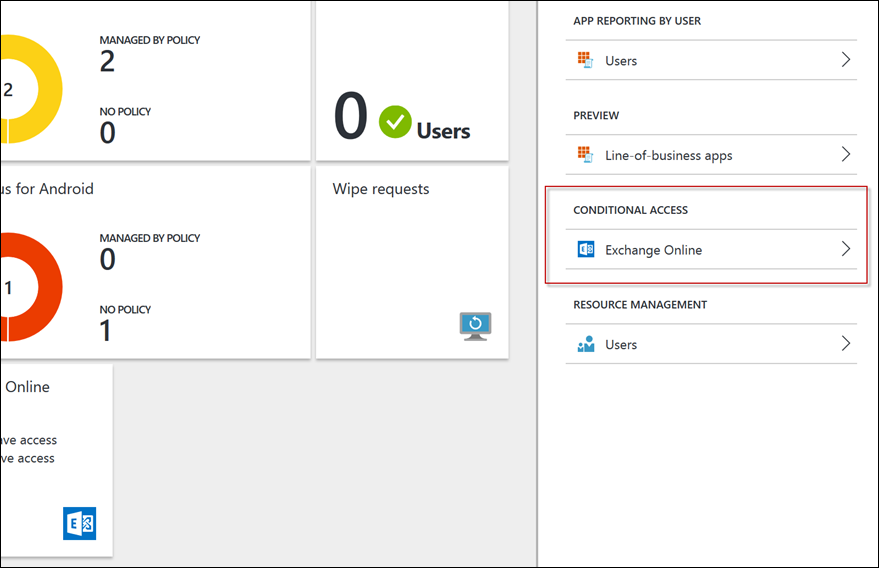
Select the Exchange Online option to expand out the options.
Here you can set up which apps can access the data, and which users are/aren’t targeted by the policy.
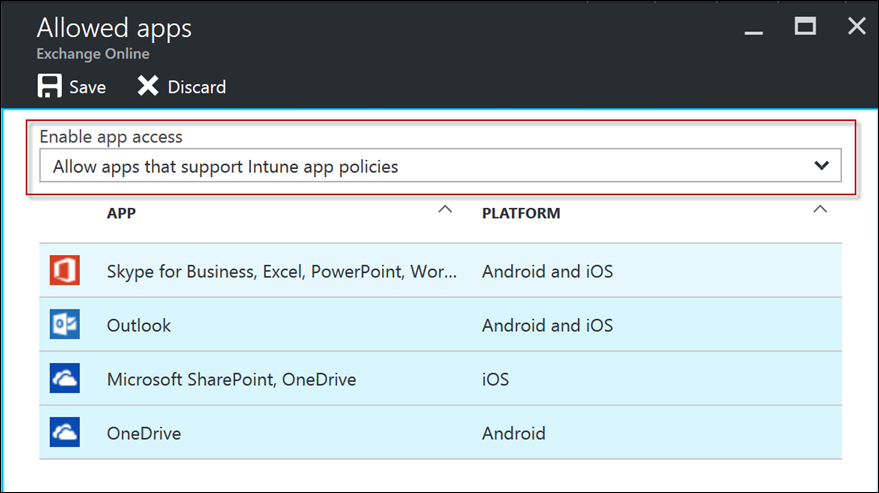
Select Allowed apps to configure the policy setting.
Select Allow apps that support Intune app policies and press Save
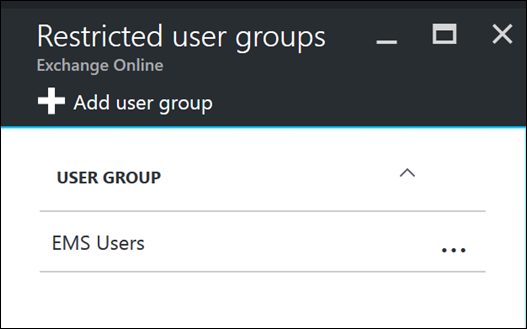
Then target the Restricted user groups with your desired AAD group
And you’re done! The users in the targeted AAD group will now be required to install the Outlook app to access their Office 365 e-mail.
There are some minor prerequisites you should be aware of. For the MAM CA to work, iOS users must have the Microsoft Authenticator app installed and logged in and Android users must have the Company Portal app installed and logged in. If the users do not have these apps installed, they will be prompted to install them before e-mail access is granted.
Edit 5/22/17: Users do not have to login to the Authenticator or Company Portal app for MAM CA to work. Just the presence of the app should be enough.
Also note that for Device CA targeted users (traditional CA), if a user is targeted for both policies the compliance is determined in a logical OR.
For example, if the device is managed by Intune and CA compliant the device will have full e-mail access, including the native EAS mail apps. OR, if the device is not managed but has the Outlook app it will have full access via the Outlook app only. This is really a very good experience for BYO vs COD scenarios, where we’d enroll a corporate owned device, but require Outlook and MAM for a personally owned device.
Edit 8/9/17: With the introduction of Azure AD in the Azure Portal, using MAM CA and AAD CA in Azure will allow a logical AND.
For example, if you want to enforce device enrollment AND the use of the Outlook app for Exchange Online, configure both the AAD CA in Azure policy AND the MAM CA policy in Intune. This is a great experience for organizations that want to manage devices, but ensure MAM DLP is applied to their corp data. This should also avoid the need for ADFS claims rules/ABQ's/etc to enforce the Outlook app! For more info on AAD CA see here.
Edit 16/10/17: In September the functionality to allow customers to select the AND/OR operator as desired was shipped!
To configure the OR operator:
- Login to portal.azure.com
- Browse to the Azure Active Directory Node, and select Conditional Access
- Find your Conditional Access policy and edit it
- Under Access controls > Grant you'll find a new option "Require approved client app (preview)"
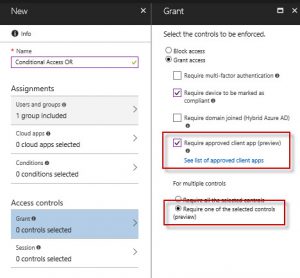
- Select this option and the Require one of the selected controls and save your policy.
This effectively enables Conditional Access to require an Intune compliant device OR an approved app such as Microsoft Outlook, OneDrive, etc. If you want to set the operator to AND (ie, enrolled device AND Outlook app), select the "Require all the selected controls" . For more detail, visit the following link
/en-us/azure/active-directory/active-directory-conditional-access-technical-reference
Matt Shadbolt
Senior Program Manager
Enterprise Client and Mobility – Intune