So you want to test your NDES/SCEP certificate enrollment?
SCEP (Simple Certificate Enrollment Protocol) and NDES (Network Device Enrollment Service) are the mechanisms we currently use to deploy certificates to our mobile devices via Intune and Configuration Manager. The tech is very (very) cool, but for the average ConfigMgr admin it’s got quite a steep learning curve.
Once you (kinda) understand how it all works, you’ll begin to test your configuration. Testing NDES and SCEP is a pain in the neck, as there are so many moving parts. Worst is having to troubleshoot certificate enrollment on the tiny screens of your mobile devices.
Luckily, we can test & troubleshoot via our Windows workstations.
In my scenario, I’ve got an NDES server hosted in Azure. I know the NDES server is ‘up’ as browsing the URI works fine (https://ndes.mydomain.com/CertSrv/mscep). I want to test that the NDES certificate template is deployed correctly, and the certificate is valid.
First, you’ll need to create an .inf file that will hold some request information. It should include the requests Subject name and the RequestType as a minimum. You can also add all the optional attributes you want or need. For example, my NDES template has a minimum key length of 2048, so I needed to add the KeyLength attribute too. (Certreq.exe INI File Structure)
request.inf
[NewRequest]
Subject = “CN=TestNDESCert”
RequestType = SCEP
KeyLength = 2048
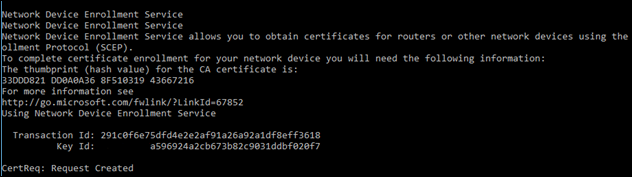
Once we have our request .inf, we need to create a certificate request. From a command line with Admin elevation
certreq –v –config ndes.mydomain.com –username MYDOMAIN\Administrator –p Password –new request.inf scepRequest.req
Lets break this down.
certreq –v –config ndes.mydomain.com is my NDES server that’s publically available. The certreq documentation notes that to use https you must specify the URI instead of the FQDN, however in my testing on Windows 10 I could not get https to work. From my tracing I found certreq dropping a “https://” in-front of any URL that I passed into the command-line. SO, if you’re using https, you may have to enable http for this sort of testing.
-username MYDOMAIN\Administrator –p Password is my test users username and password
-new request.inf scepRequest.req is the verb calling a new request feeding my request.inf (created above) and an output file scepRequest.req
You should get something like this back from the command
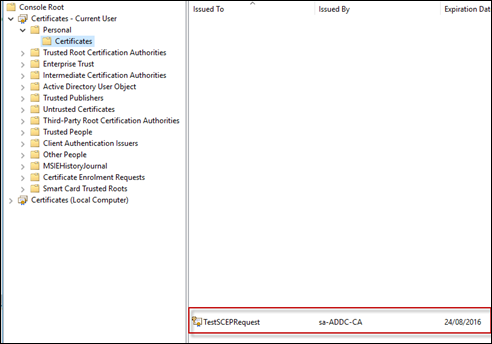
If you now check on the CA, you should see a certificate has been issues to this client
Now that we have our request, we need to submit it to the NDES server to receive our certificate.
certreq -v -config ndes.sa.mattslabs.com -submit scepRequest.req scepCert.cer
This is pretty straight forward. Submit the newly created scepRequest.req request file, and receive a certificate scepCert.cer from the NDES server.
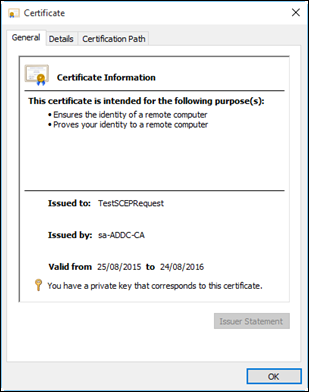
Finally, install the certificate and view it in your Certificates – Current User MMC snap-in
certreq -accept scepCert.cer
Happy testing!
Matt Shadbolt