Associating your Intune DirSync Directory with your Azure tenant
Cloud identity is one of the core features and benefits of using the Azure platform. Fortunately, Microsoft Intune uses the same back end to store your users cloud identities.
This guide is for admins who have setup and configured DirSync for Intune, and want to retroactively add that synchronized domain to their organizations Azure tenant.
First, browse to https://manage.microsoftazure.com and login using your organizations Service Administrator account.
Note: for these steps to work, you may need to be using an MSA account (hotmail.com, outlook.com, etc). If you don’t receive the “use existing domain” option when creating your Azure AD domain, create a co-administrator with an MSA account. Login using this account and the option should appear.
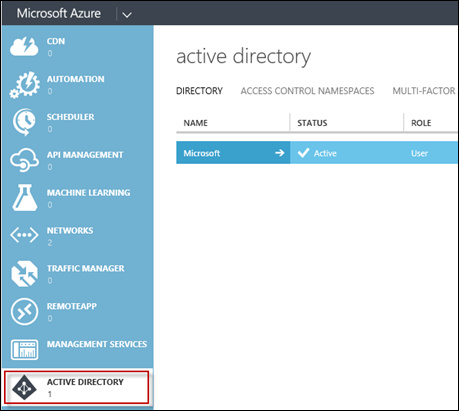
Go to the Active Directory tab. You’ll see just the default Microsoft directory is present.
Select the + New button in the bottom left hand corner
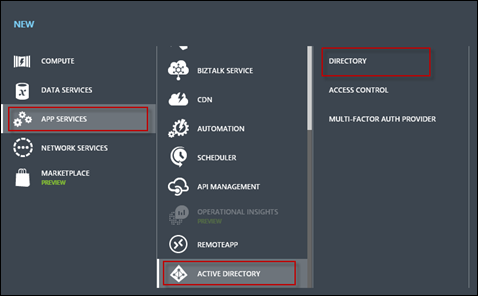
You’ll receive the New blades fly-in. Select App Services > Active Directory > Directory
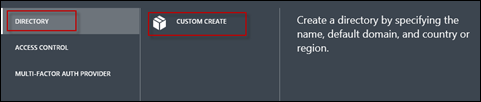
The blade will expand. Select Custom Create
This will produce a pop-up to Add directory
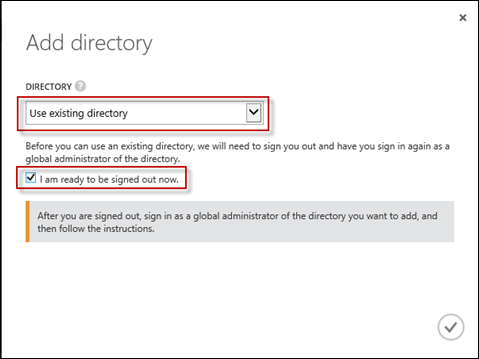
Select Use existing directory, and check the box for I am ready to be signed out now. When ready, click the tick in the bottom right. You’ll then be signed out and prompted for your Intune Tenant credentials.
Enter your Intune credentials
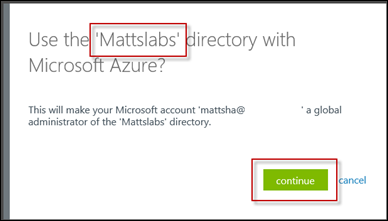
You’ll automatically be asked if you want to associate the Intune directory with your Azure AD tenant. Select Continue
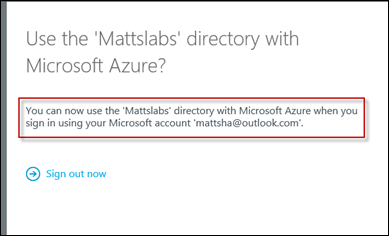
Success! You can now sign out and back to your main Azure tenant
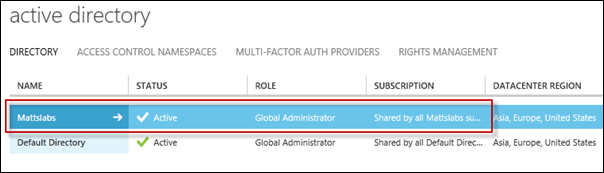
You can now see that the Mattslabs domain has been added into my Active Directory section in my main Azure tenant
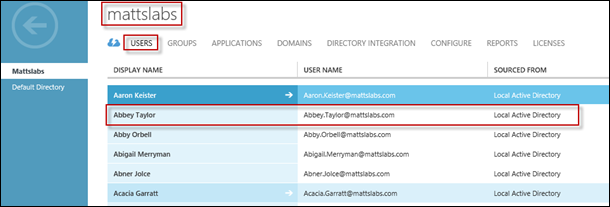
Just to be sure it’s all working nicely, click on the new domain to view the users
You can see my users with mattslabs.com UPN is now in my Azure console.
You’re now good to go. In this guide we’ve successfully associated our previously synced Microsoft Intune directory into our organizations Azure Active Directory.
Matt Shadbolt