ConfigMgr 2012 R2 Certificate Requirements and HTTPS configuration
We have had a number of recent requests from our customers on the certificate requirements and configuration steps required to configure HTTPS communication in a ConfigMgr 2012 environment.
I would like to give a massive thank you to Ravi Kalwani, a member of the ANZ Microsoft ConfigMgr Premier Field Engineering (PFE) team who put this guide together.
This post contains the step-by-step configuration needed to successfully implement HTTPS communication in your ConfigMgr 2012 R2 environment.
Creating Templates for Site Systems and Clients Certificates
Create a template for ConfigMgr Clients
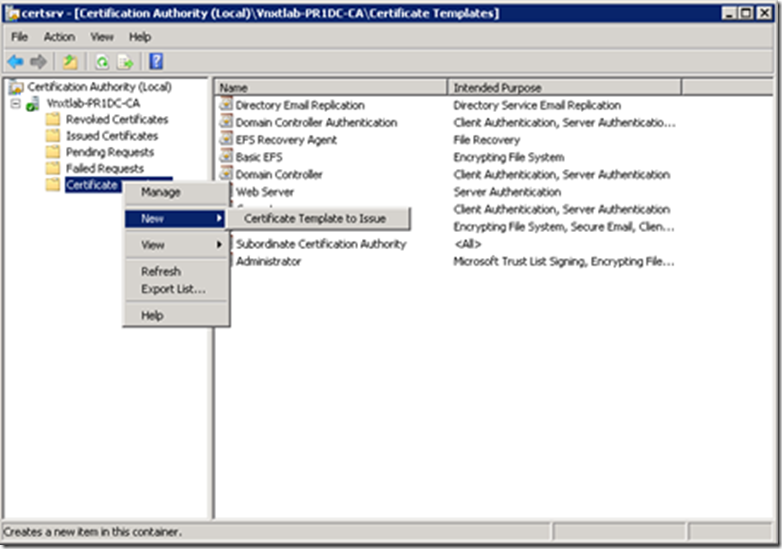
On the issuing Certificate Authority go to Administrative Tools and Open Certificate Authority Console
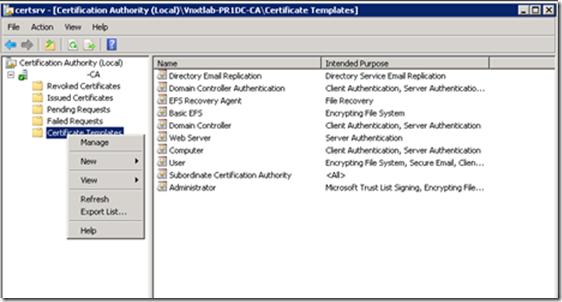
Right Click On Certificate Templates and Click Manage to open Certificate Template Console
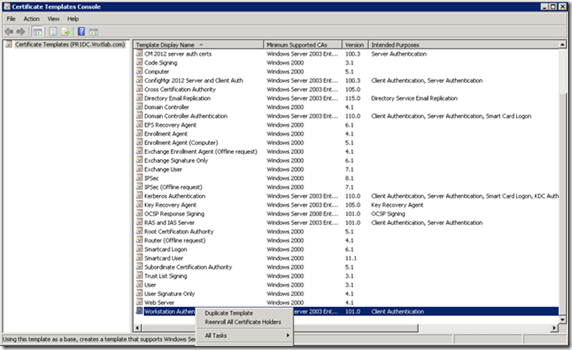
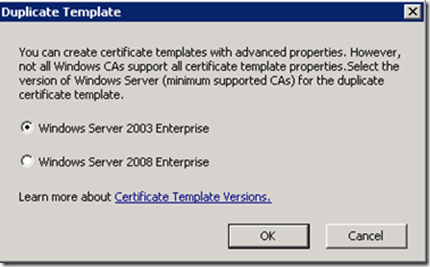
Now right-click on Workstation Authentication and click Duplicate Template
Make sure to use Server 2003, not 2008
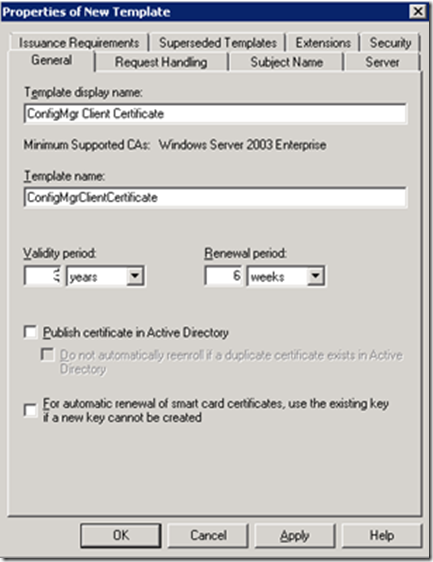
We are first creating Certificate Template for ConfigMgr client Authentication Certificate, so give the Template a Name that would related to what it would generate Certificates for, I have chosen Name “ConfigMgr Client Certificate”
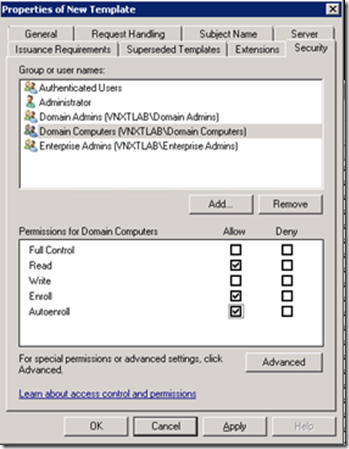
Click on the Security tab, select the Domain Computers group and add permissions of Read and Autoenroll, do not clear Enroll
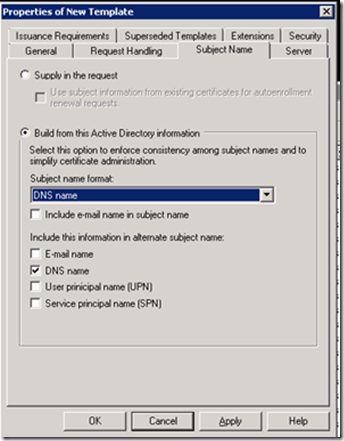
Now Click on the Subject Name Tab, and Select DNS name in Build from this Active Directory information, Then click OK.
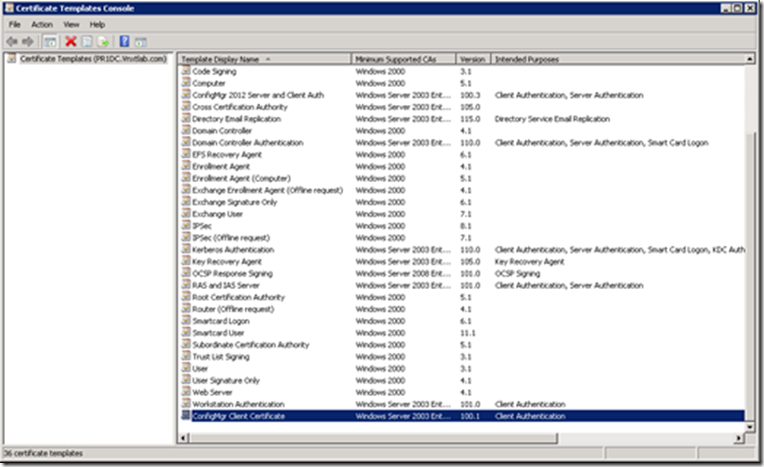
Refresh Certificate Template console to see the new template in there.
Create a template for Site Systems (MP, DP, SUP and/or WSUS)
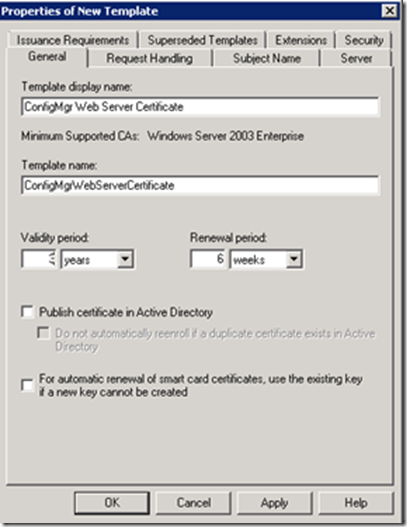
Still in Certification Authority, in the Certificate Templates list we’ll setup the next template. Right-click on the Web Server template, and click Duplicate. On the General tab, change the Template something more appropriate like ConfigMgr Web Server Certificate.
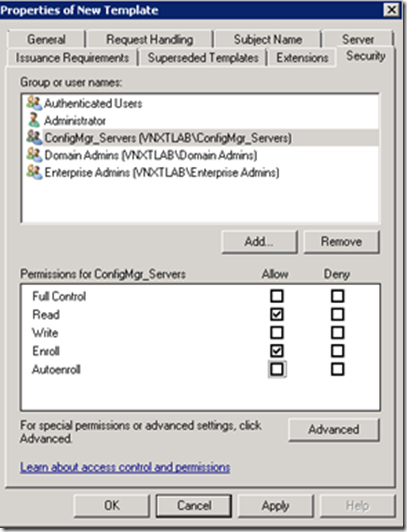
Next click the Security tab, and add your SCCM server to the permissions list and add the Enroll permission.
If you were running a SCCM configuration with multiple sites and servers, it is recommended you create a SCCM Servers Active Directory Security Group. I’ve created an AD security group called ConigMgr_Servers. So I’ve added the Group with Enroll permission.
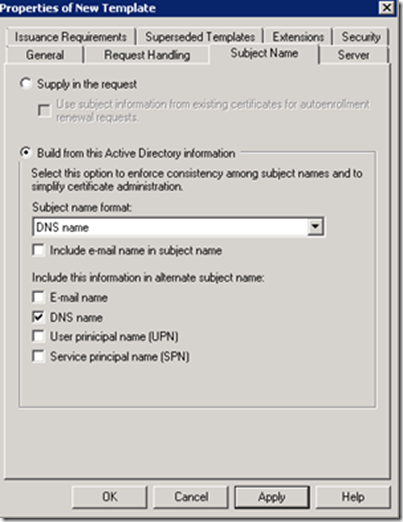
Now Click on the Subject Name Tab, and Select Build from this Active Directory information, and then Select DNS name. Then click OK.
Create a ConfigMgr Client template for WinPE Images
This step is only needed if you have all you MP/DP running in https. In this step we are creating a Client Authentication certificate that will be used to generate certificate for WinPE images, which will later contact MP and DP on Https.
If you don’t have all MP/DPs in HTTPs you can continue to build image via Task Sequence and WinPE images will contact HTTP MP and not HTTPS
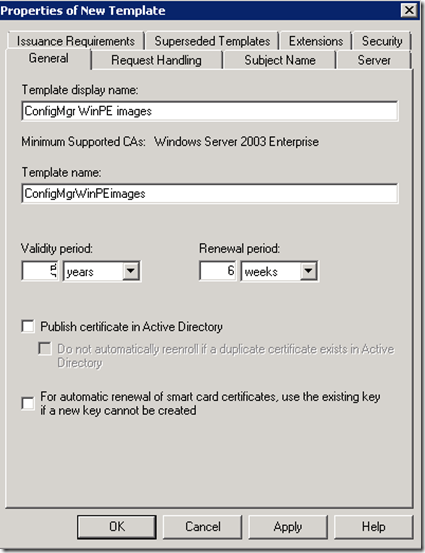
Right-click on the Workstation Authentication template, click Duplicate. Rename the template as ConfigMgr WinPE images, I personally like to give longer validity as WinPE images can’t renew their certificate and it’s a manual process to create and Import certificates in WinPE images before the validity expires. In my lab I’ve given 5 years validity.
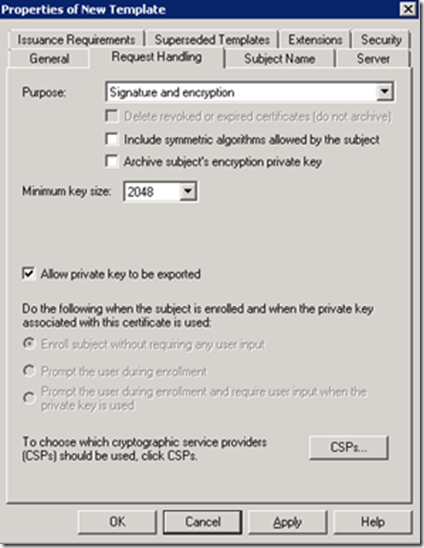
On the Request Handling tab select Allow private key to be exported.
On the Security tab add your SCCM servers group, and give Enroll permission. Click Apply, then OK.
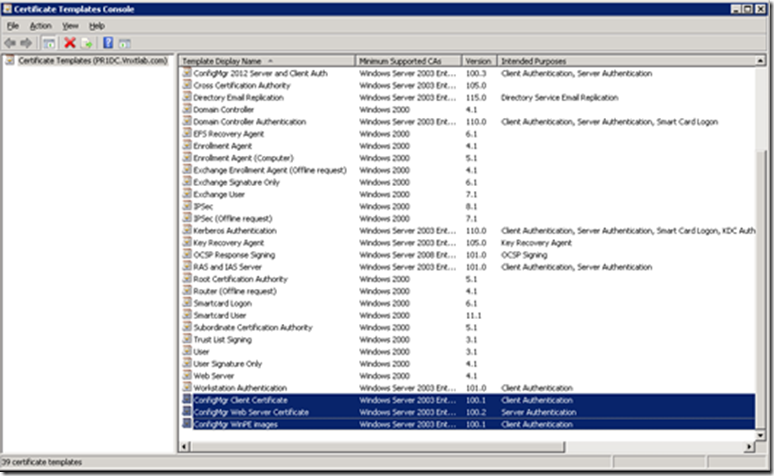
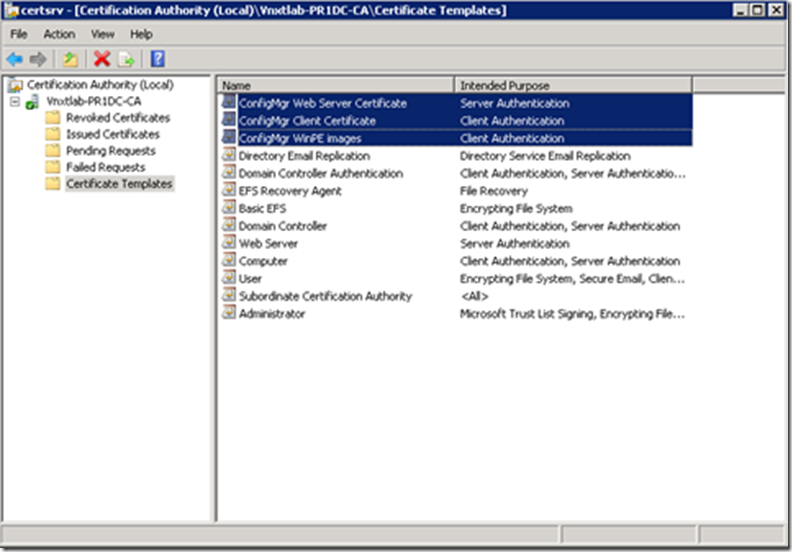
Now if you look at the Certificate Templates Console you will see our three new templates.
We can now close the Certificate Templates Console.
Enable Certificates to be issued
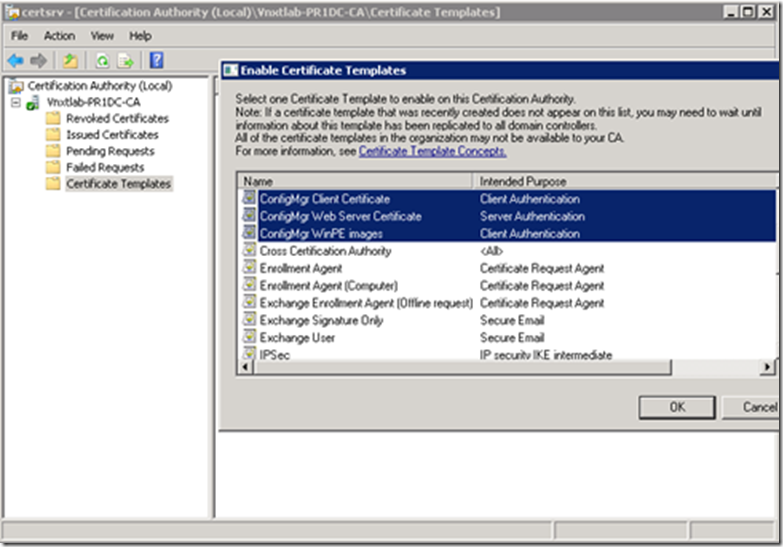
Open Certificate Authority Console-> Right Click Certificate Templates-> Select New-> Certificate to Issue
Select all three of the ConfigMgr templates we created then click OK.
They will then show up in the Certificate Templates listing. Once you verify that, you can close the Certification Authority console.
Create an Auto-Enrol GPO for the Client Certificate template
Now we’ll need to create a Group Policy at the OU of our domain where we want client to get ConfigMgr Client Certificates and only does HTTPS with MP, DP and SUP
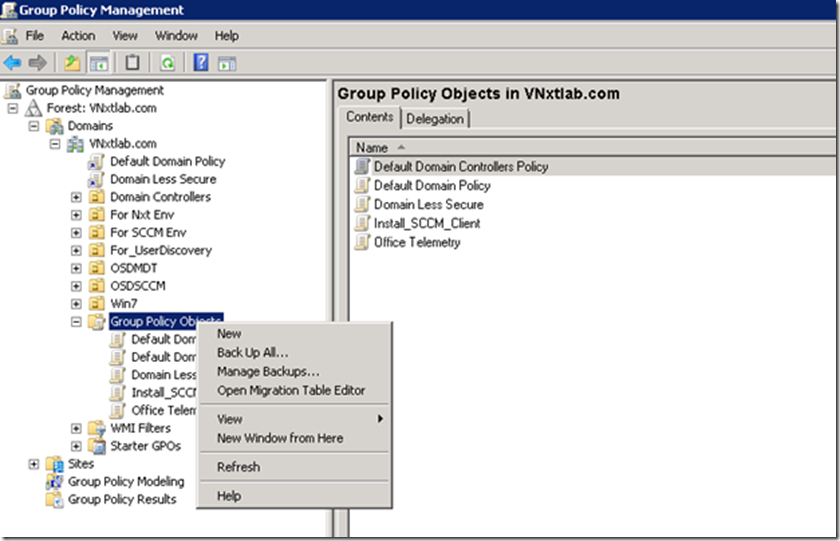
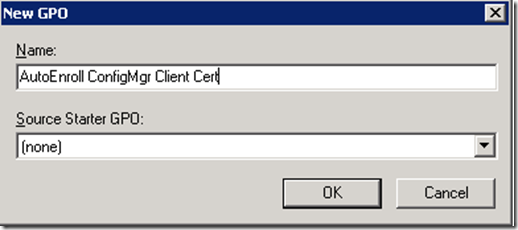
Launch Group Policy Management on your Domain (Start > Administrative Tools > Group Policy Management). Right-click Group Policy Object and select New as we are going to create a new GPO and link it to OU later. Name your GPO appropriately, I have given my GPO Name “AutoEnroll ConfigMgr Client Cert“, then click OK.
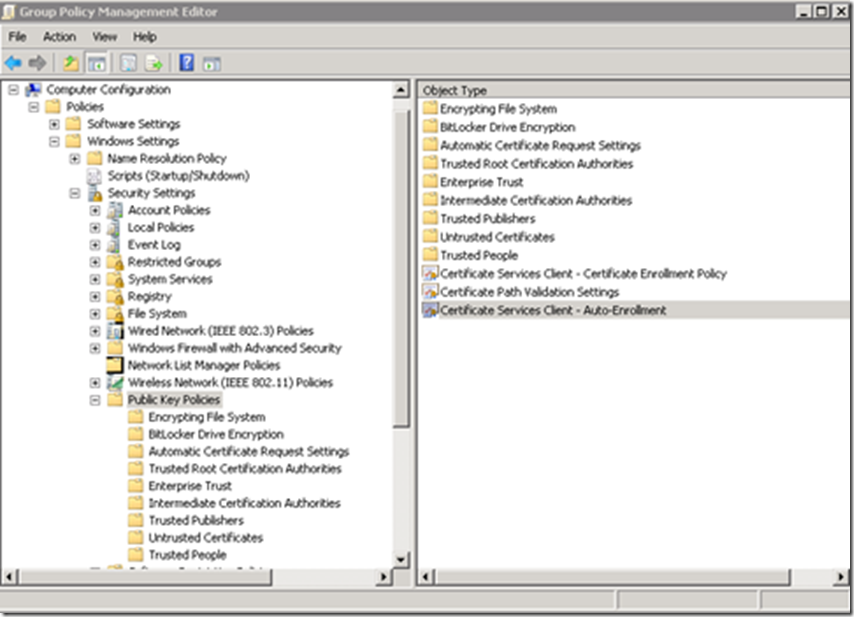
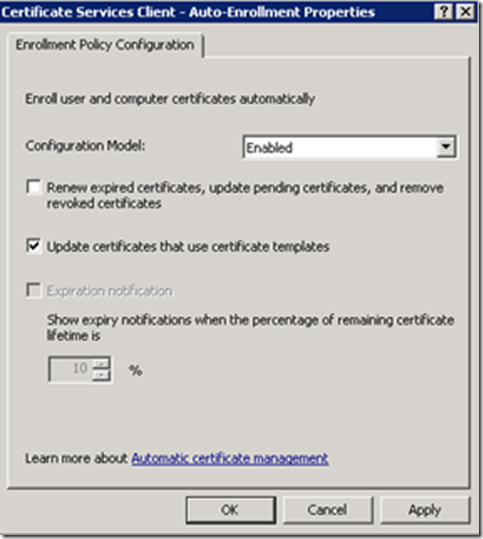
Edit your newly created GPO. Navigate to: Computer Configuration> Policies > Windows Settings > Security Settings > Public Key Policies. Right-click on Certificate Services Client – Auto-Enrollment and then click Properties. Change the Configuration Model: to Enabled, and check the Update certificates that use certificate templates. Then click Apply and OK.
If you recall, we configured the ConfigMgr Client Certificate Template earlier and we set the permissions for Domain Computers to Read, Enroll, and Auto Enroll. Now when you run a “gpupdate /force” or in 15 minutes when GP is re-applied, any machine on the domain communicating with the DC will request and receive a client certificate automatically that will be place in the Local Computer Personal Certificate Store.
Request Web Server Certificate on MP, DP and SUP
Now we need to setup the appropriate certificates on our System Center Configuration Manager Management Point. The first thing you will need to do is reboot your SCCM server. This is so that it will pick up the permissions change that will allow it to register for the Web Server Certificate.
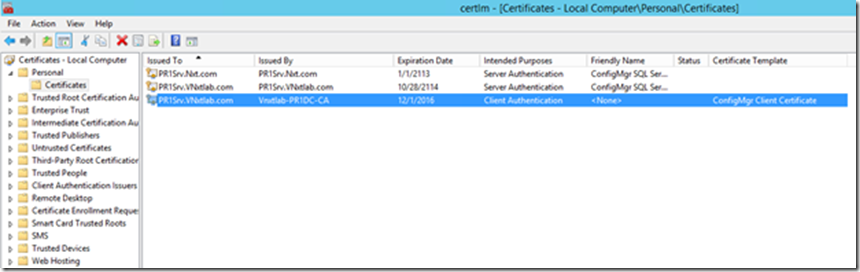
Once the reboot completes, click Start > Run. Type mmc.exe and click OK. Click File > Add/Remove Snap-In, Choose Certificates and click Add. Choose Computer Account, click Next. Choose Local Computer, click Finish. Click OK, and then expand the Certificates tree to the Personal > Certificates folder.
You may notice that your SCCM server has Auto-enrolled for and received its Client Authentication Certificate we just setup.
Right-click in a blank space and click All Tasks > Request New Certificate, You are presented with the Certificate Enrollment wizard. Click Next
Leave the default on this page, and click Next
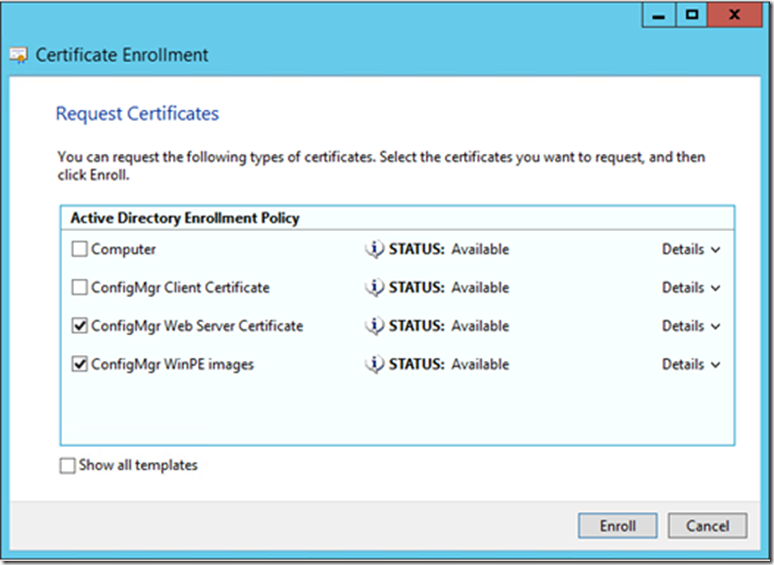
Select ConfigMgr Web Server Certificate Template and Click Enroll.
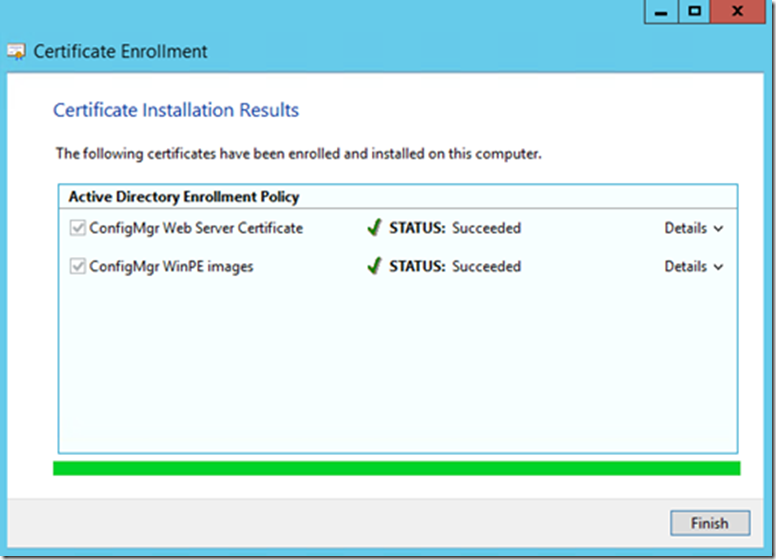
Once you see Status: Succeeded, Click Finish
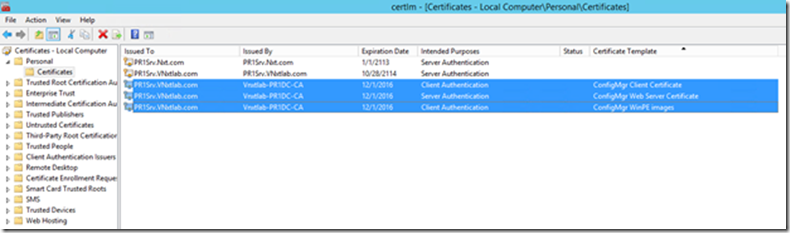
Now you will be able to see both all three Certificates on Certificate Console of Site Server
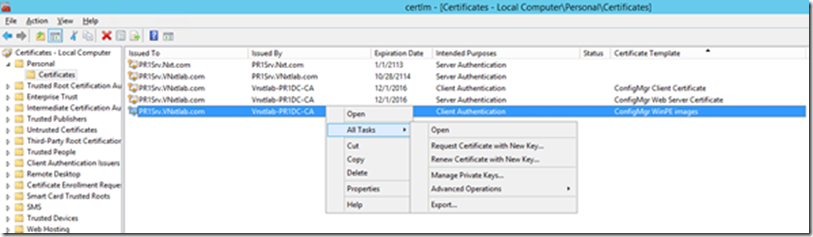
Now we need to export the Client Distribution Point Certificate while we are in the Certificates Management console. Right-click the certificate that shows template name as Certificate WinPE images and click Export.
Click next on the “Welcome to the Certificate Export Wizard
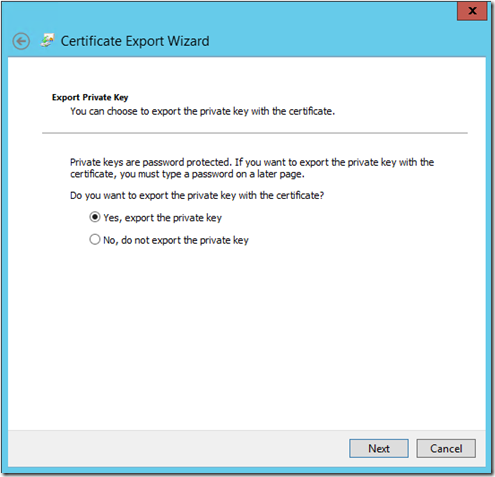
Select “Yes, export the private key”, if you see this option greyed out, you probably have wrong certificate selected.
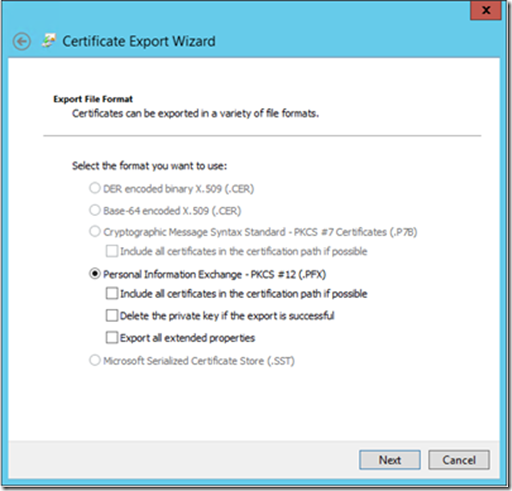
Select “Personal Information Exchange – PCK #12 (.PFX)” and click Next
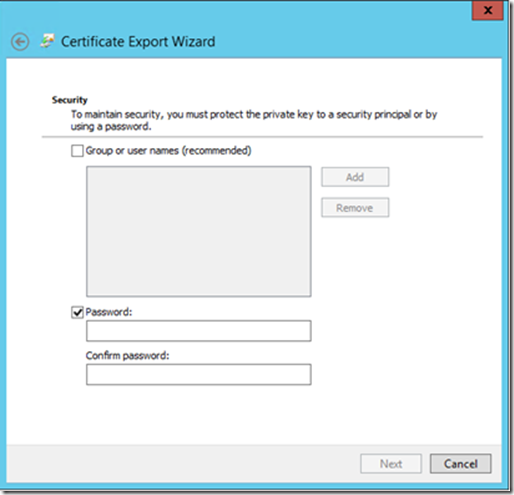
Set a password in this screen and click next, you will need this certificate while importing it to Distribution point property.
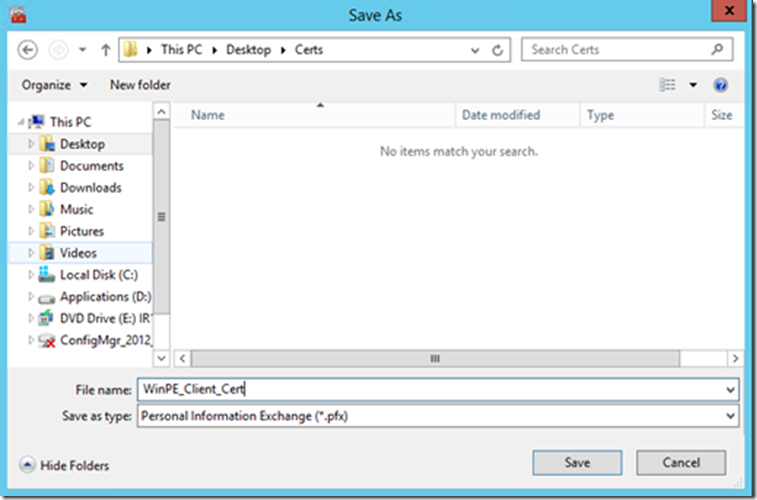
Select Destination where would you like to export the certificate, and give it a descriptive name.
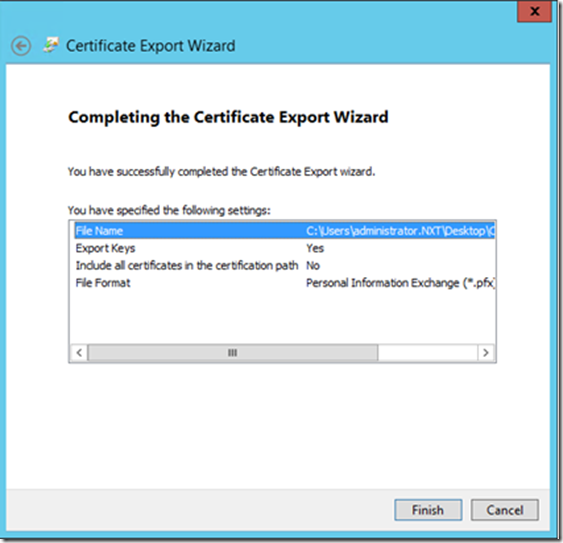
Click Finish
Importing Certificates in IIS
After all the certificates have been requested we need to now import the Web Server Certificate to the Default Website and WSUS Website in IIS.
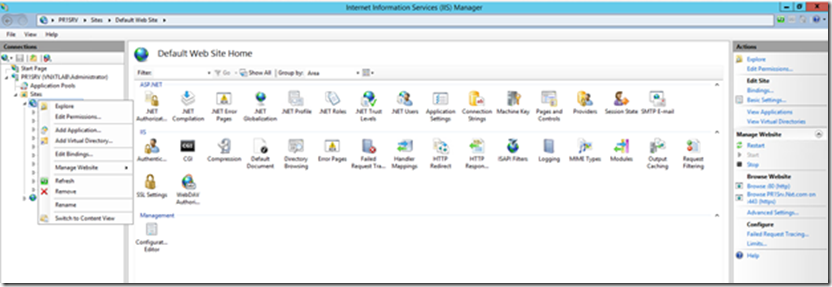
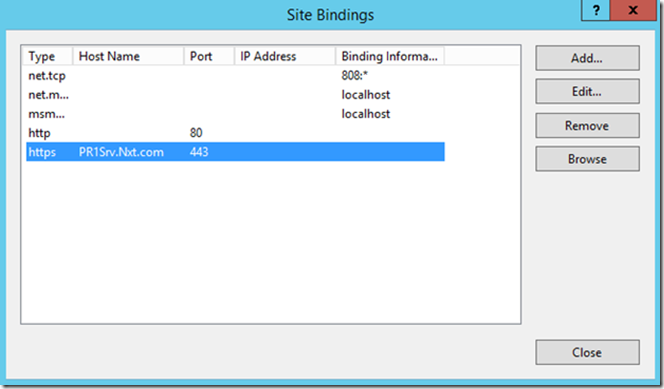
Launch IIS Manager (Start > Administrative Tools > Internet Information Services (IIS) Manager).Navigate to the Default Website, right-click it and select Edit Bindings.
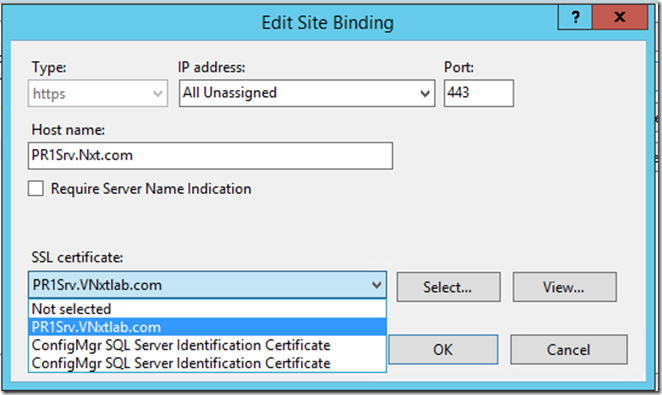
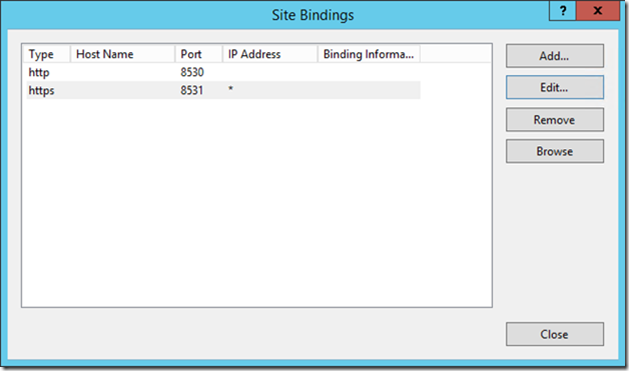
Select the https binding and click Edit
Select the https binding and click Edit. The select the ConfigMgr Web Server Certificate and then click OK. I highly recommend viewing your certificate afterwards, checking the Details tab, to ensure you selected the correct one.
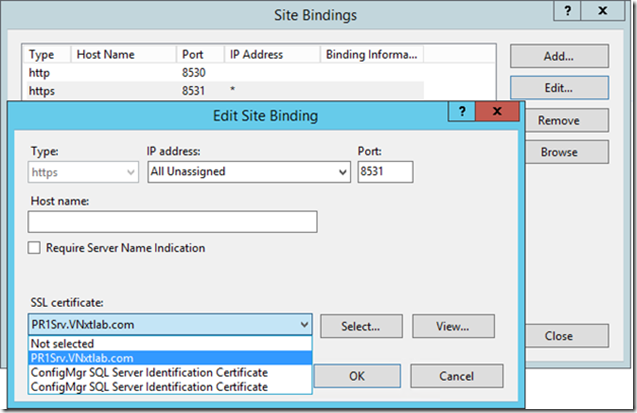
Now do the same on WSUS Website.
Select Appropriate Certificate (not SQL), and click OK.
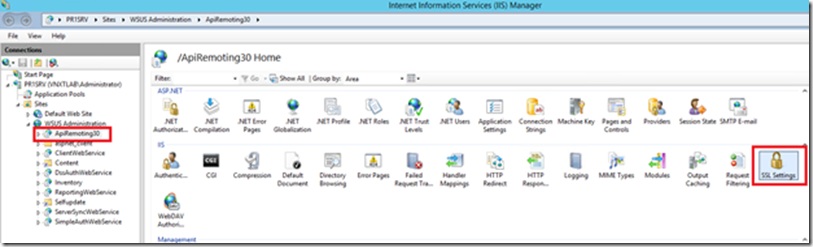
Last Piece of configuration that we need to do is, manually configure five WSUS virtual directories to use SSL. The five Virtual directories are (APIRemoting30, ClientWebService, DSSAuthWebService, ServerSyncWebService, and SimpleAuthWebService)
The Virtual directories has also been definied in the TechNet document https://technet.microsoft.com/en-us/library/bb633246.aspx
Putting ApiRemoting in SSL
Check the box Require SSL and Select Ignore under Client certificates
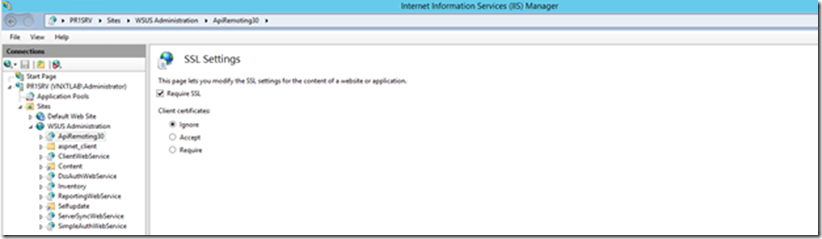
Now do the same for rest of four Virtual directories mentioned above.
Configuring MP, DP and SUP to use SSL
Now that we have completed all our certificates pre-requisites and ready to configure ConfigMgr Components to use SSL.
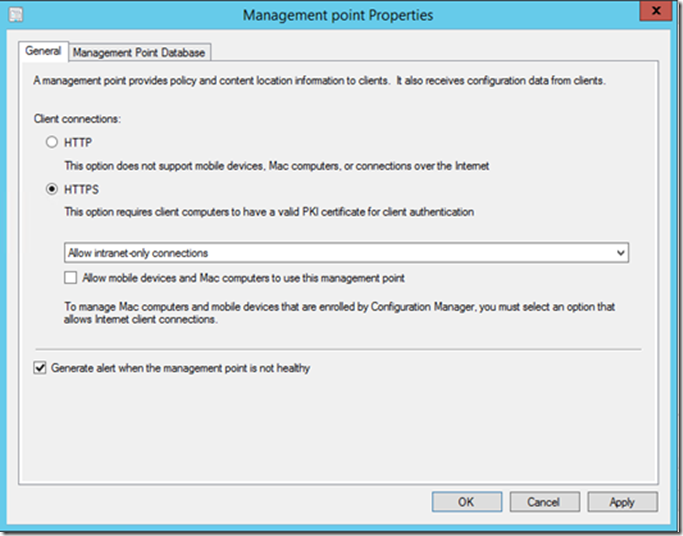
Configuring Management Point to use SSL
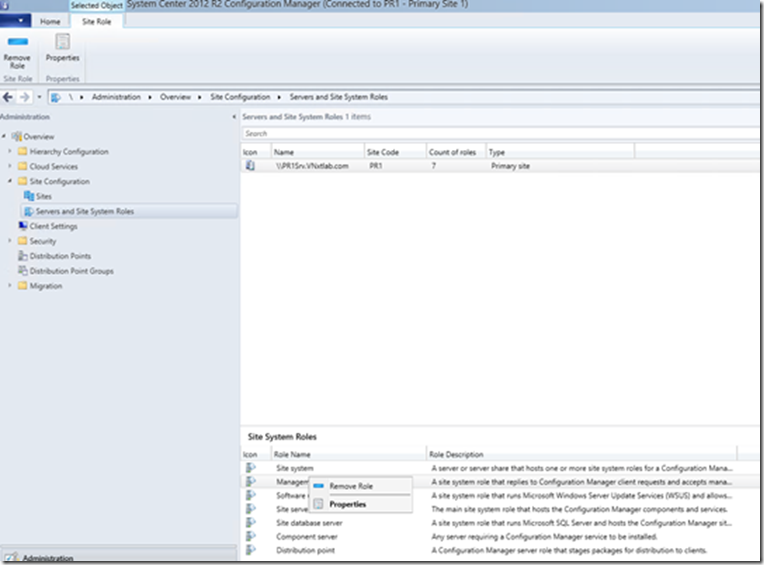
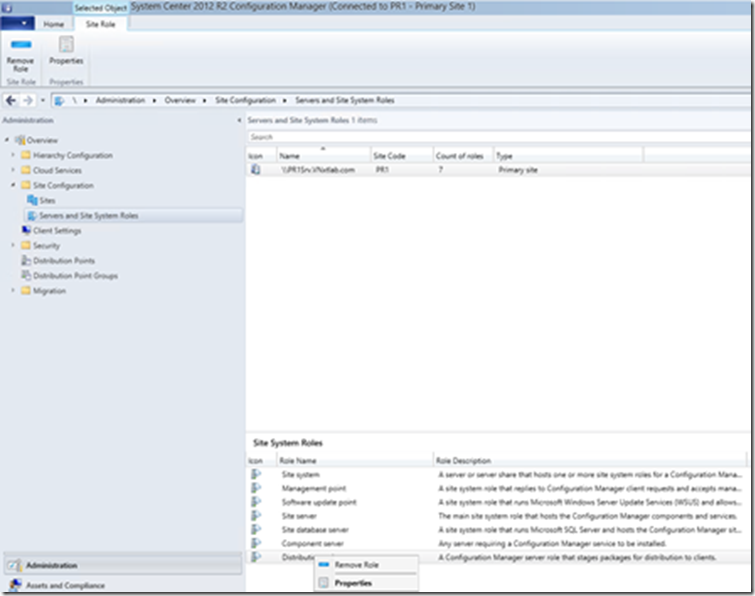
Go to Management Point Property, (Open ConfigMgr console>Administration Workspace>Site Configuration>Servers and Site System Roles>Select Your Sever and Right Click on Management Point Role and Click Property.
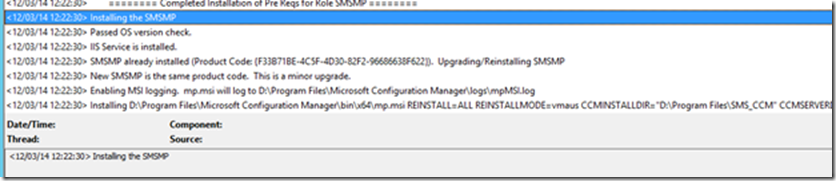
Select HTTPS from the Client Connections options, this will kick off Reinstallation of Management Point, and reconfigure its Virtual directories to use HTTPS communication only.
You can see MP Reinstallation happening in MPSEtup.log
Configuration Distribution Point Role to SSL
Go to Distribution Point Property, (Open ConfigMgr console>Administration Workspace>Site Configuration>Servers and Site System Roles>Select Your Sever and Right Click on Distribution Point Role and Click Property
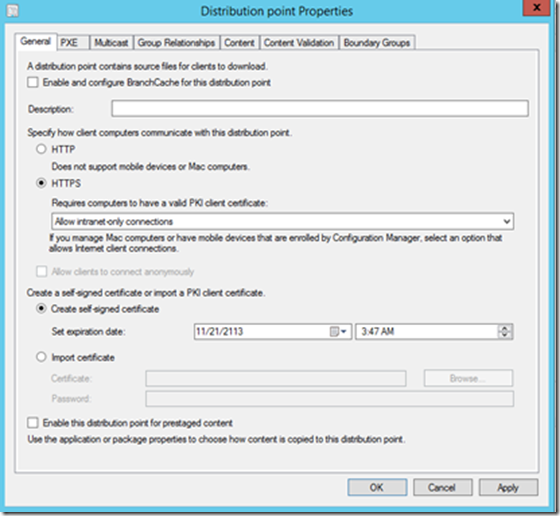
Select HTTPS under Specify how client computers communicate with this distribution point
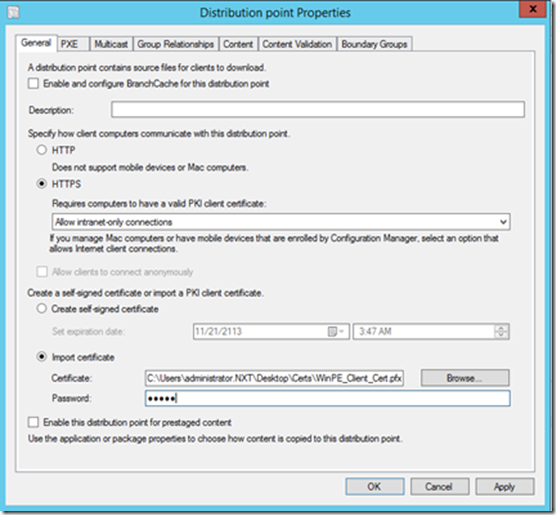
If you would like Clients to communicate back to DP on HTTPS even during Task Sequence than you would need to Select Import Certificate under Create a self-signed certificate or import a PKI client certificate
Click Apply, This will reconfigure this Distribution Point virtual directory to Use Only HTTPS communication
Configure WSUS/SUP to use HTTPs
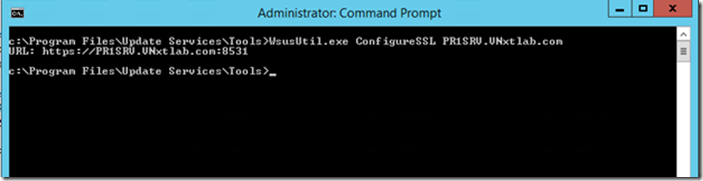
Open up command prompt in Admin Context on WSUS server and change working directory to WSUS installation path Tools directory and run following Command
WSUSUtil.exe ConfiguresSSL <Intranet FQDN of WSUS Server>
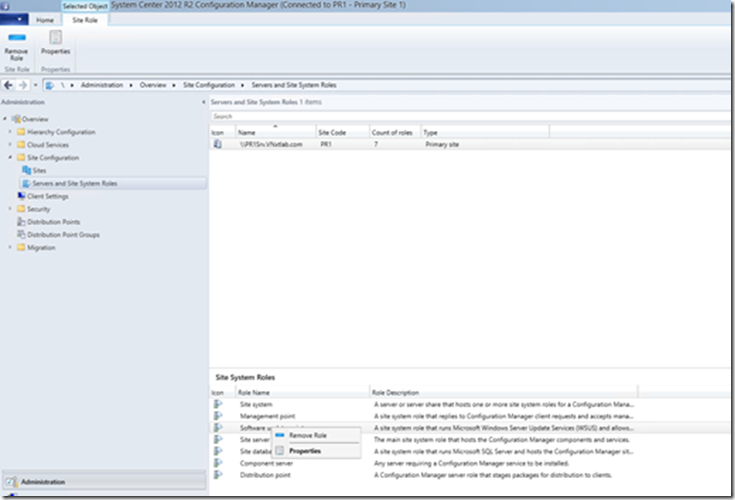
Go to Software Update Point Property, (Open ConfigMgr console>Administration Workspace>Site Configuration>Servers and Site System Roles>Select Your Sever and Right Click on Software Update Point Role and Click Property
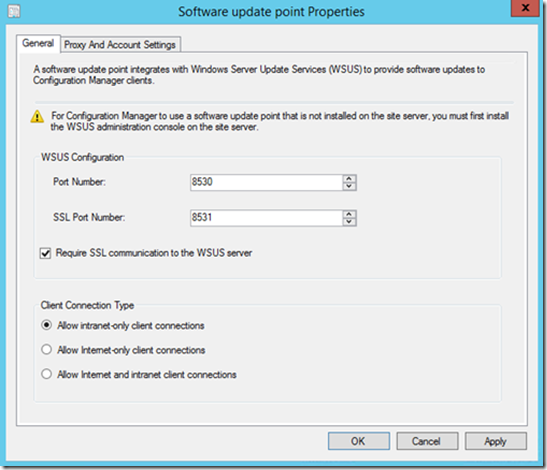
Check the box Require SSL communication to the WSUS Server and Click Apply
This as well will reinstall Software Update Point Role with new settings.
Site Server Settings
Change your ConfigMgr setting to ensure client communicates with HTTPs Enabled MP when there is a client authentication cert is present.
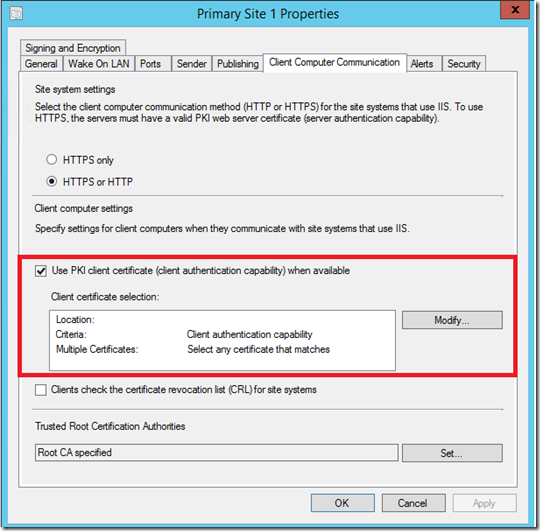
Launch ConfigMgr Console> Administration Workspace> Site Configuration> Sites> Right Click your Primary Site> Properties and Go to Client Computer Communication Tab.
Check the box “Use PKI Client certificate (client authentication capability) when available”
Review clients that have Client Authentication Cert to make
sure they are communicating to MP in HTTPs.
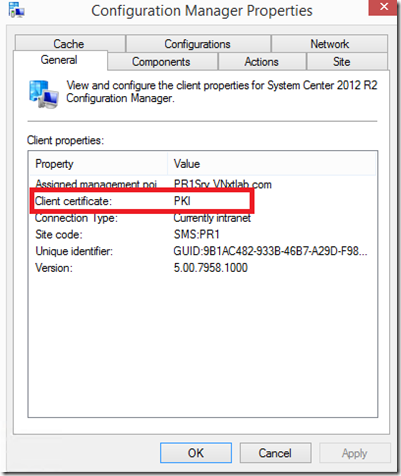
A Client that has ConfigMgr client cert installed will see changes made to ConfigMgr Server via Published information in Active Directory, and will switch to HTTPs if it detects a Valid Client Cert Present on Computer’s Personal Store.
References
PKI Certificate Requirements for Configuration Manager
https://technet.microsoft.com/en-us/library/gg699362.aspx
System Center 2012 Configuration Manager: R.I.P. Native Mode
Step-by-Step Example Deployment of the PKI Certificates for Configuration Manager: Windows Server 2008 Certification Authority