When to use Forefront Endpoint Protection 2010 Threat Overrides
On the FEP Support team, we occasionally receive cases from customers who need to allow a “known threat” to run in their environment for various reasons. Most of these have tried (unsuccessfully) to make this work by using File, Folder, or Process exclusions. While it may be possible to achieve this goal using these methods, this would be an unsupported use of exclusions, and this is really “the wrong tool for the job.” The recommended and supported method for allowing known threats to run is with the Threat Override policy.
Before we get too far into this, you may be thinking, “Why would Iever allow malware to run on my computers?” There are several typical reasons:
1. Your business requires a certain application, typically in the Remote Control Software, Monitoring Software, or Potentially Unwanted Software categories, that you have licensed and use for legitimate purposes. So even though Forefront Endpoint Protection classifies it as ‘malware’, in your environment, it is legitimate, licensed software. Note: many of the threats in these categories are also used by attackers for nefarious purposes.
2. You are in the IT Security department and are examining the behavior of malware in a controlled environment (lab).
3. You are part of a company’s IT Security department and use some tools that are classified as malware as penetration testing tools.
OK, back to the customer issues we see occasionally, here is one recent example:
“Problem Description: FEP is currently flagging some 'malware' on a couple of our servers. It's not necessarily a false positive as it can be used for nefarious purposes. However, I would like to exclude it from the scans on a few of our servers. The problem I'm encountering is that I haven't been able to figure out how to exclude it using wildcards. I've searched for documentation, but examples and explanations are currently lacking. Here are some of the sites I've looked at:
https://technet.microsoft.com/en-us/library/gg398037.aspx
https://technet.microsoft.com/en-us/library/ff823837.aspx
https://blogs.technet.com/b/clientsecurity/archive/2010/03/08/wildcards-in-path-exclusions.aspx
If I put in the full path to the ISO file, it's no longer scanned. However the path to the ISO file can (and does) vary from server to server, including different drive letters. I would rather not have to enter 5-10 (or more) hard coded exclusion paths for the same exclusion, I would rather be able to use wildcards to exclude this ISO file regardless of it's location on a given server.”
Here was my response to the customer:
Hi <customer>, what you’re trying to do (allow a known threat to run) is accomplished by using the ‘Threat Override’ feature of Forefront Endpoint protection. The file/folder/process exclusions are provided primarily for performance and compatibility reasons, not for allowing known threats to run. So, for example, if you had a folder with a huge number of data files (i.e. millions) created by an application, and FEP was taking a long time to scan that folder, or a folder structure with many complex/nested zip files, you might need to exclude those files/folders. Or, for process exclusions, if you had an application that performed poorly with FEP enabled, then you would exclude that process from being scanned by FEP.
The ‘Threat Override’ policy is the supported method for allowing known threats (executables which could potentially do ‘bad things’) to run.
It’s very easy to create and deploy a threat override.
Our documentation on creating policy and defining threat overrides is located here:
Either you edit an existing policy or you create a new policy. A procedure to create a new policy can be found here: https://technet.microsoft.com/en-us/library/ff823835.aspx
When you have your policy, you need to modify it to define a threat override. For guidance on how to edit a policy, see https://technet.microsoft.com/en-us/library/gg398037.aspx
Here is an example:
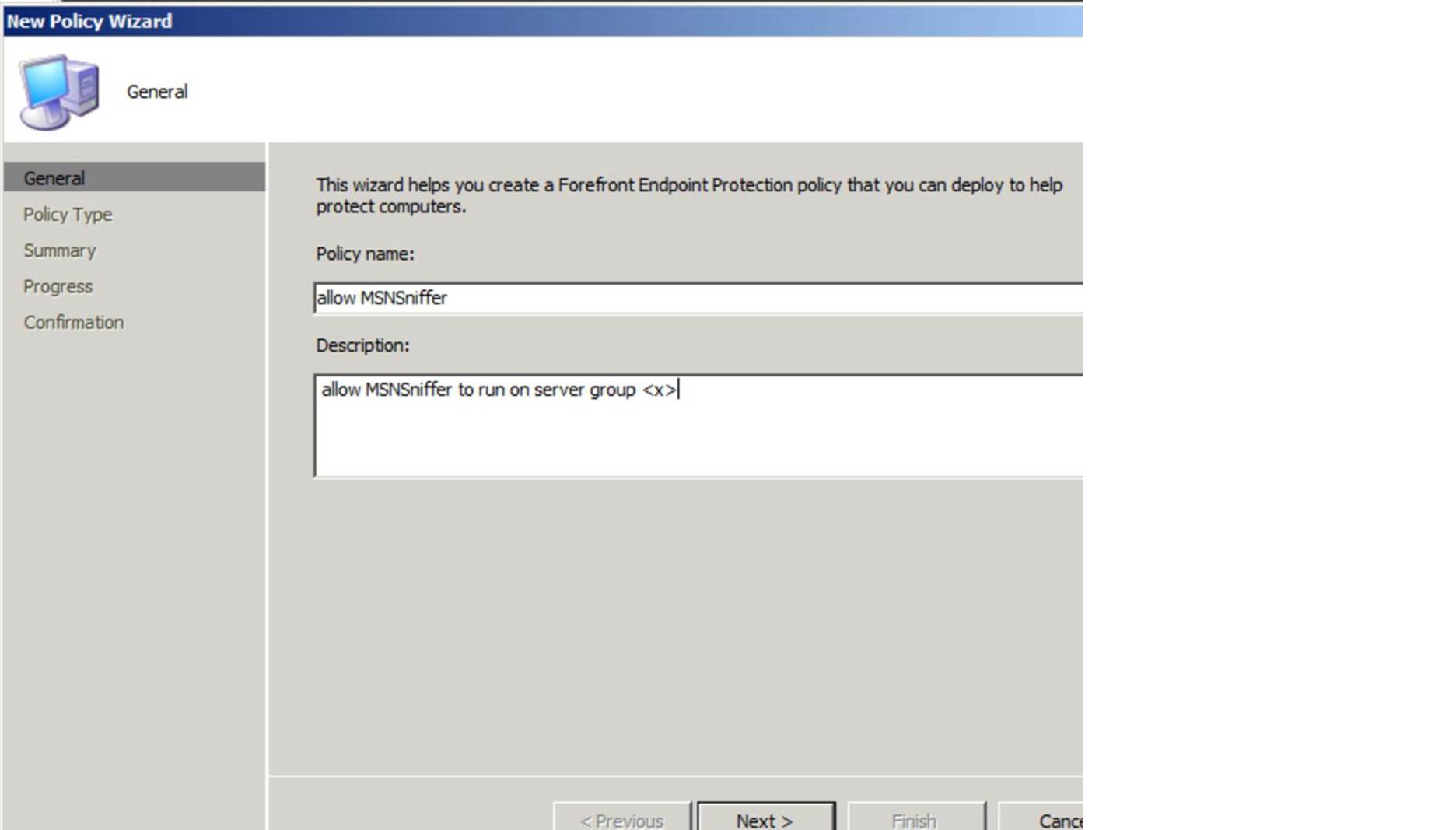
To enable a Threat Override, you would create a policy like this:
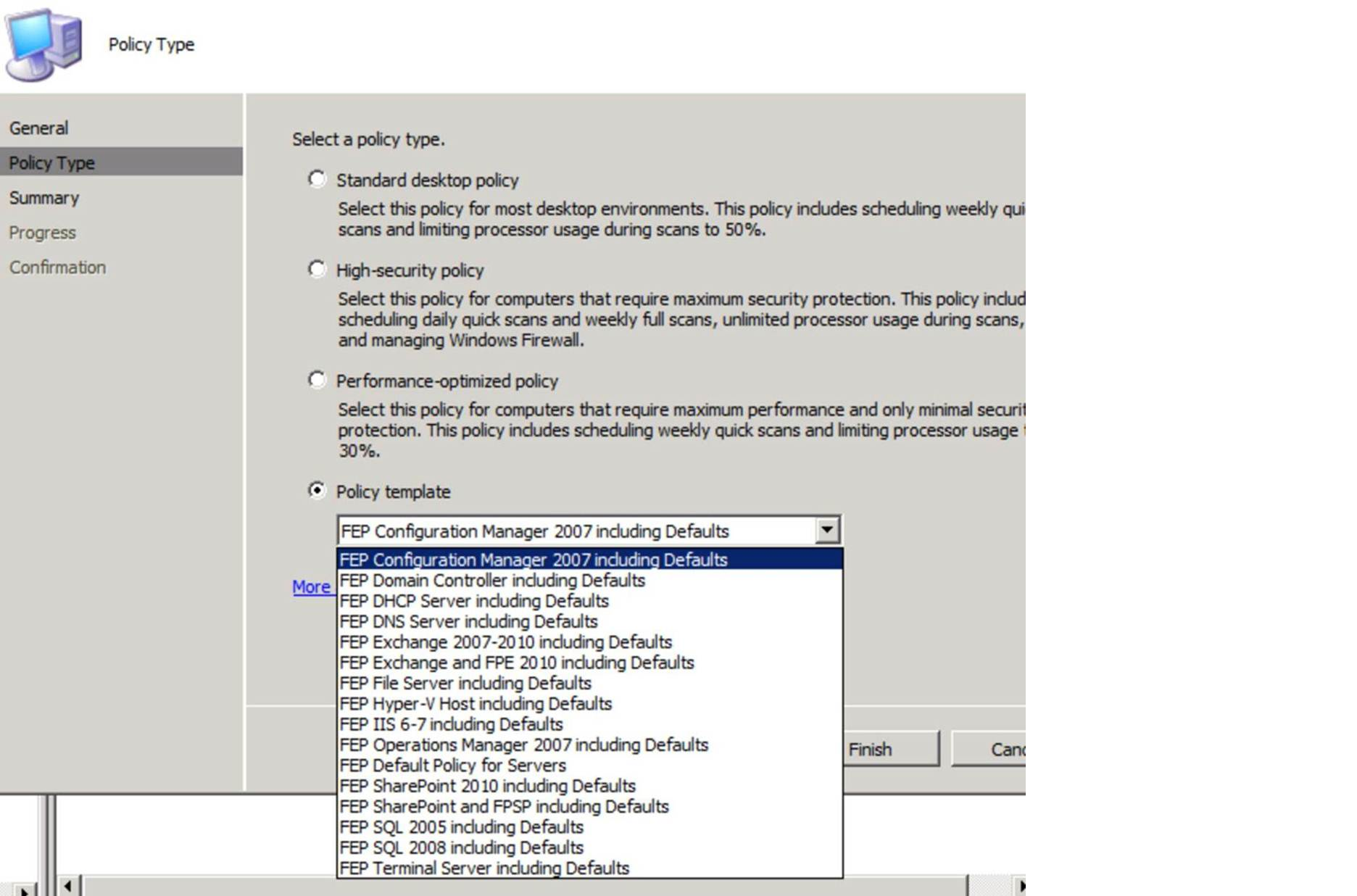
Then select a policy template, such as this:
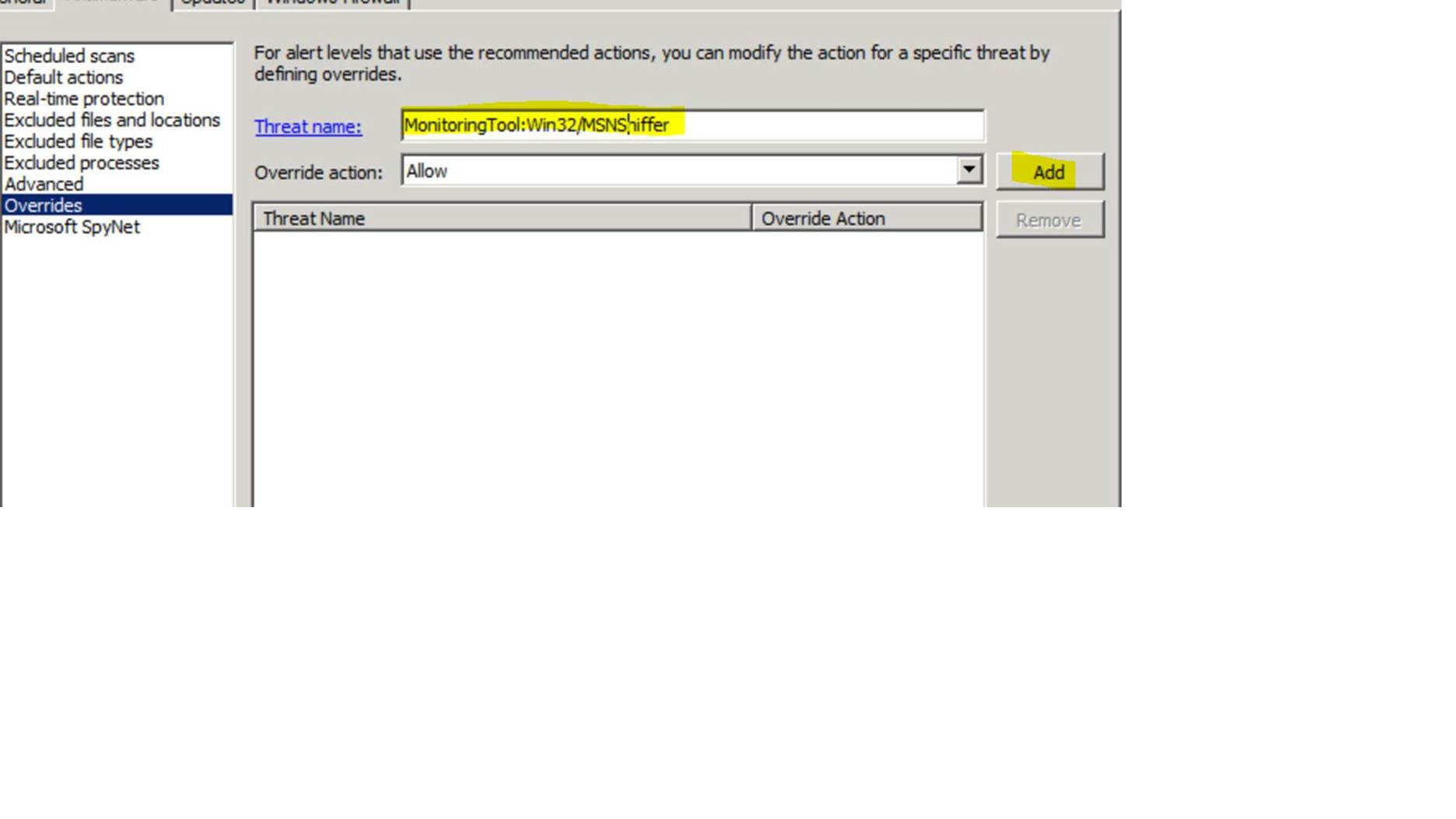
Then finish creating the policy, and go to the Properties for the new policy, and click on the ‘Antimalware’ tab, and click ‘Overrides’ on the left hand side.Type in ‘MonitoringTool:Win32/MSNSniffer’, ensure the ‘Override action’ is set to the default (Allow), and click ‘Add’.
Note: If you aren’t sure of the exact threat name, go to the System Event log on the client where the threat was detected, and there should be an event with ‘Source: FCSAM’ and an Event ID of 3004. The Description field will include the link to the Microsoft Security Portal entry for that particular threat, including the Threat Name that you enter below.
Then click ‘OK’, and assign that policy to computers where you want to allow this to run.
Please let me know if you have questions about this.
Here was the customer’s response, once he enabled the Threat Override:
“Faron,
Thank you for the additional information, it was very helpful. Once I added
the Threat Override, it no longer flagged during the scans.
Thanks for your help on this.”
For reference, here are links to more information on creating & editing FCS/FEP policy:
Creating a policy: https://technet.microsoft.com/en-us/library/ff823835.aspx
Editing a policy: https://technet.microsoft.com/en-us/library/gg398037.aspx
Hopefully this article is helpful in explaining the correct purpose and usage of Threat Overridesin Forefront Endpoint Protection.
Faron Faulk
Microsoft Platforms Security Technical Lead