Understanding how Forefront Client Security responds to potentially unwanted software
Analysts at the Microsoft Malware Protection Center (MMPC) apply objective criteria to software to determine if it should be classified as malicious or potentially unwanted. When software is classified as malicious or potentially unwanted, Microsoft adds it to a definition library used by Client Security during scans. Once the software is added to the definition it is assigned a severity or alert level; severity and alert levels are described here and summarized below:
Severe or High
Programs that might collect your personal information and negatively affect your privacy or damage your computer, for example, by collecting information or changing settings, typically without your knowledge or consent.
Medium
Programs that might affect your privacy or make changes to your computer that could negatively impact your computing experience, for example, by collecting personal information or changing settings.
Low
Potentially unwanted software that might collect information about you or your computer or change how your computer works, but is operating in agreement with licensing terms displayed when you installed the software.
A challenge that the designers of Client Security faced is how to respond to potentially unwanted software. For example, imagine Contoso is a company that publishes a remote management tool named ContosoPro. If Microsoft’s definitions contain a categorization for RemoteAccess:Win32/ContosoPro, the MMPC encyclopedia entry for this type of threat might contain the following text:
The software is a remote control application that allows control of the machine where it is installed. The software can be installed for legitimate purposes, but it can also be installed from a remote location by an attacker with malicious intent.
Given this, should Client Security remove RemoteAccess:Win32/ContosoPro if it is detected? If so, what if the computer is legitimately using the software for remote access? In an effort to secure the computer, has Client Security now made the software inaccessible?
To avoid this and similar problematic situations, Client Security will warn about threats classified with medium or low severity, and a user can choose to take action upon them; however, by default, it will allow them to run. Threats with a severe or high severity will be suspended; a user can choose to take action upon them, or the configured action (configured in the definitions by default, or configured by the administrator) will be taken during routine cleaning.
As this behavior could allow potentially unwanted software to run in your environment, Client Security enables administrators to override this default behavior, depending on their organizations’ risk tolerances. As described in TechNet documentation, spyware and potentially unwanted threats can be overridden by threat, category, or severity. If you want to change the behavior of Client Security to suspend all threats, including potentially unwanted software, but excepting legitimate programs you want to retain on your machines, you should take the following actions:
1. Identify any legitimate potentially unwanted software to be retained on your computers
- Install Client Security in a non-production environment on a computer system with the software that is used in production and monitor for software detections for desired software.
- Search the MMPC malware encyclopedia for software used in your environment; typically these are remote access software.
- Take note of the exact name used in the detection by Microsoft.
2. Using the exact name, create a threat override to allow any software discovered in the previous step.
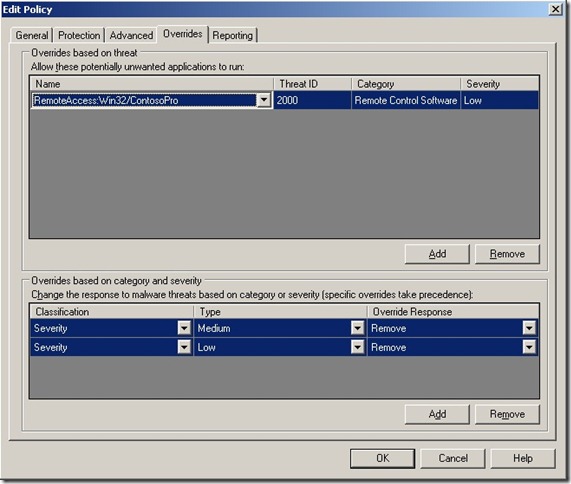
3. Create overrides for medium and low severity threats to remove or quarantine.
When these steps are taken, Client Security suspends all software threats, except those which were excluded in step #2 above. Using the RemoteAccess:Win32/ContosoPro example above, the Client Security policy console would look as shown below:
Thanks,
Craig Wiand
Microsoft Forefront Escalation Engineer