Provisioning your Private Cloud in VMM 2012–Getting Started 101
In our group, we have several highly-available sets of clusters that service various needs. We have one cluster dedicated to running our Team Foundation Services (TFS) and all the System Center management infrastructure to support all clusters. These clusters include our Development teams cluster (we do test, etc. here), our VDI cluster (where many of our developers house a VDI Windows 7 workstation with Aero-enabled), and soon we will have a Test cluster for ensuring that we have the right resources dedicated for our continuous deployment needs. As you can imagine, we could certainly help having the benefits of a Private Cloud but for years we’ve not.
In VMM 2008 R2, we managed the environments using the below heuristics-
Cluster Name |
Security Role Type |
Requirements |
| TFS Production | Administrator |
|
| Dev Lab | Delegated Administrator |
|
| VDI Workstations | N/A | N/A |
As you read this table, you are quickly going to start asking questions. The first that comes to mind is why would we make a Delegated Administrator group that has all Dev team members in it. Furthermore, why would you create a group for TFS Production at all if this is actually production – don’t you want to limit rights?
The questions are good but the answer is even better – because we didn’t have true cloud-enabled capabilities with Virtual Machine Manager 2008 R2. The capabilities of the Self-service role in VMM 2008 R2 were limited. In VMM 2012, end-users can do a great deal more to enhance their ability to interact with the infrastructure.
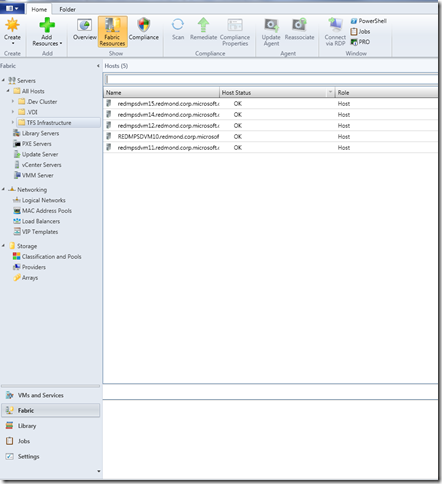
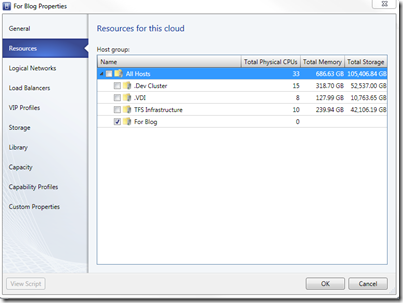
Administrator's View in VMM 2012
As opposed to those of end-users, Administrators can see the actual fabric that makes up your “Private Cloud”. If you contrast this with the view you see when logging in as a self-service user in the administration console -
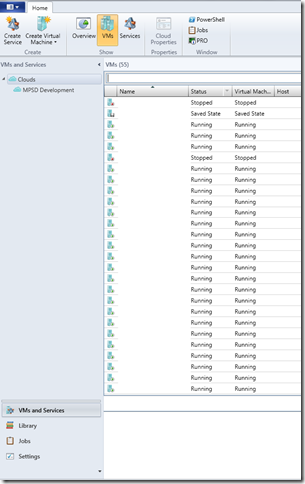
Cloud Self-Service User View in VMM 2012
This greatly simplifies the experience for the end-user (consumer) of the Private Cloud.
General Concepts behind Private Cloud with Microsoft Virtual Machine Manager (VMM)
A highly debated question that exists in IT today is, “What is the definition of Private Cloud”. I know that within my organization, and many others, you can easily spot discrepancies in definitions when you are looking for them. As I write this, the very thing on my mind is that I want to be super careful as to define a private cloud in the wrong way to spur a lengthy debate that has been hotly contested for well over a year. Instead, though, I prefer to just put some principles out there that I believe as a owner of a private cloud I care about. Let’s discuss…
- Every Private Cloud has to have a robust security model that allows end-users to be placed and scoped appropriately based on needs
- Through the use of some sort of technology, the ability to provision virtual assets, whether defining the hardware characteristics, OS setup, and lastly any software provisioning is provided out-of-the-box
- Provide detail level control of virtual assets (VMs, VHDs, ISOs, and more) to consumers of the cloud is required
This is a loose set of information but it meets what I currently envision as the basis of a Private Cloud.
With that said, let’s speak to how we’ve effectively used principle #1, #2, and #3 by using our security model needed as it is applied to VMM 2012.
Definitions of our needed Security roles:
- Administrators: These end-users are actual owners of the Fabric resources that are part of Cloud
- Platform Delegated Admin Group: Provides platform infrastructure staff access to a set of hosts via Host Groups
- TechWriter Perms: This is a specialized group of permissions whereby the end-users have access to a subset of machines within the Private Cloud infrastructure
- Development: These end-users can view, share, and interact with any set of resources within the cloud as they are actively using the resources to do development, testing, etc.
- Production Managers: This role provides end-users limited rights to the production cloud with some key exceptions such as access to the Fabric. These individuals are mainly focused on managing the guests in the production cloud.
- VDI Client Users: This set of end-users have access to the VDI cloud where their private virtual desktops await them
- Stock Trader Service Manager: This role grants access to users to manage a service, hosted in the cloud, called StockTrader 1.0
Let’s map roles, security, and requirements in the VMM 2012 world…
Using the table above, I wanted to circle back around and share a few more details with you on some strategies used now that we are on VMM 2012. VMM 2012 offers a lot of flexibility in their Role-based Security model (RBAC) that you need to understand to properly enable to empower your end-users.
To illustrate this purpose, I thought it would be useful to share the same table but instead focusing on how it is implemented in VMM 2012 utilizing all the features -
To summarize, here is the table from above that shares some of the key pieces of information needed when thinking about role-based provisioning in VMM -
Cloud Name
Security Role Type
Security Role Name
Requirements
TFS Infrastructure
Administrator
Administrators
· Access all physical hosts
· Access all VM assets via VMM (not within the OS, thought)
· Access all library assets
· Administrator Compliance of physical hosts
· Manage security for Cloud
Delegated Administrators
Platform Admin Group
· Access all physical hosts
· Access all VM assets via VMM (not within the OS, thought)
· Access all library assets
Self-Service User
Production Managers
· Ability to create new VMs
· Ability to create new template definitions
· Ability to manage VMs as administrators
· Ability to Start, Stop, Pause, Save, etc. VMs
· Ability to store or deploy VMs
Development
Administrator
Administrators
· Access all physical hosts
· Access all VM assets via VMM (not within the OS, thought)
· Access all library assets
· Administrator Compliance of physical hosts
Manage security for Cloud
Self-Service User
Development Team
· Ability to create new VMs
· Ability to create new template definitions
· Ability to manage VMs as administrators
· Ability to Start, Stop, Pause, Save, etc. VMs
· Ability to store or deploy VMs
Self-Service User
Tech Writers
· Manages specific machines within the cloud
· Runs with Local Administrator privileges on VM
· Ability to Remotely Connect to those VMs
Self-Service User
Stock Trader Service Mgr
· Ability to manage VMs, including provisioning of additional machines, related to services they own
VDI Cloud
Administrator
Administrators
· Access all physical hosts
· Access all VM assets via VMM (not within the OS, thought)
· Access all library assets
· Administrator Compliance of physical hosts
· Manage security for Cloud
Self-Service User
VDI Client Users
· Ability to view their own VM and manage configuration relating to their VM
What the table above is outline some of the requirements your roles will need. This is just a good exercise to go through prior to creating your Private Cloud. Of course, if you follow this blog often, you know I didn’t do this and that this is after-the-fact work of mine. <g>
Creating Host Groups in VMM 2012 for managing Physical Hosts
VMM 2012 offers cloud administrators the ability to present clouds of various hypervisor’s to end-users. This is very useful as the end-users are abstracted from the differences presented by running more than a single hypervisor and they focus on what is important to them – provisioning, managing, and running VMs. In our case, we have a love fest with the Microsoft Hyper-V hypervisor so we really can’t show this support easily. However, it is easy concept to grasp.
Upon adding a Hyper-V host, or cluster, you are asked which Host Group to add the host to. This is not the time to think through your strategy for creating Host Groups, instead, I’d suggest that you create your host groups before you start adding hosts.
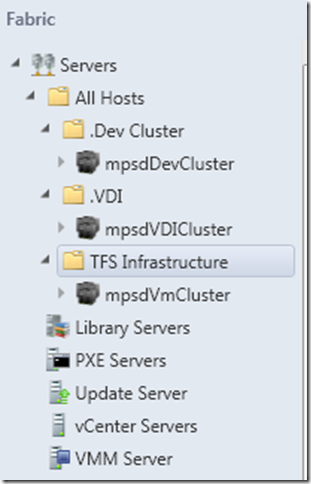
In our environment, we created 3 Host groups that mirror pretty much our clouds-
- TFS Infrastructure (for all TFS assets)
- VDI (for all VDI assets)
- Dev (for all Dev assets)
After adding each physical host to the appropriate group during installation, your VMM 2012 console should look like the following in the console under Fabric -
Host groups are the building blocks for Private Clouds in VMM 2012. Let’s move on to creating a cloud…
Creating Private Cloud: Let’s assign some stuff…
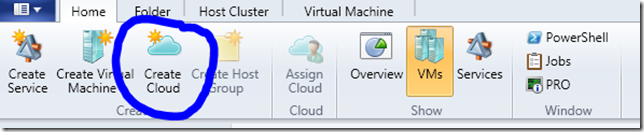
To create a cloud in VMM 2012, you actually do not do this under Fabric in the UX. Instead, you move to the VM Services tab that exposes the Clouds node. You can easily detect the cloud section by the  section in the UX. To create a cloud, in the ribbon, click Create Cloud-
section in the UX. To create a cloud, in the ribbon, click Create Cloud-
Follow these steps during the Create Cloud Wizard:
- Provide a Name for your Cloud & enter a description for this Cloud and Click Next
- When the resources screen is available, select your Host Group
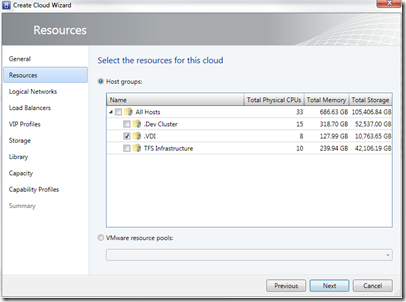
- Select the logical network this cloud is capable of using
- For the next four screens, might I suggest that you skip these if you’ve not already familiarize yourself with the features (later blog)
- Under Capability Profiles, please select the Hyper-V capability profile
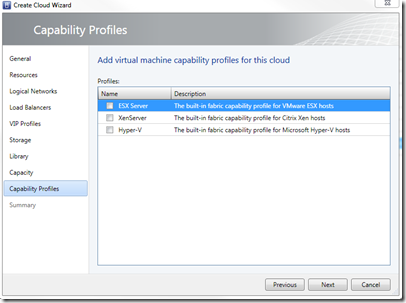
- Click Finish on the Summary page
You should now have a cloud that enables capabilities as soon as you assign users to that cloud. It is important to note that I intentionally left out some information through the wizard process. This information, albeit helpful and important, are not vital to the creation of your cloud.
Create Private Cloud Self-Service Role…
Lastly, you will need to assign the cloud to resources who can utilize it. This is done in one of two ways in VMM, though, for purposes of this blog I will do it the easiest method possible. Let’s assign resources to use the Cloud -
- In the VMs and Services wunderbar, under Clouds, right-click your cloud and select Assign Cloud
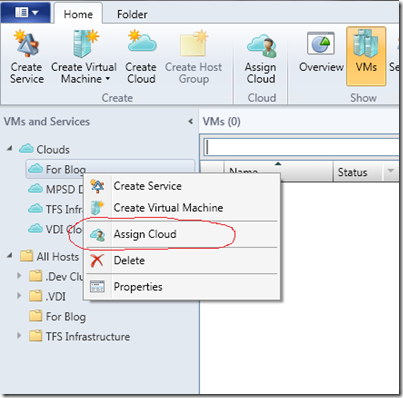
- In the Assign Cloud screen, choose to use an existing role or to create a new role. In our case, select new role…
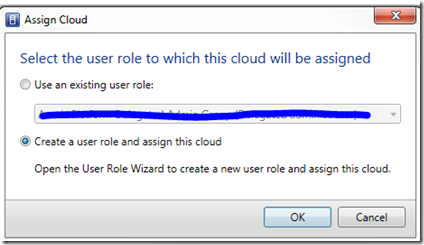
- In the Create User Role wizard, provide a general name
- For profile, enter Self-service user
- Under Members, add any users you’d like to be able to use this cloud
- Under Scope, provide the linkage to the Cloud created earlier
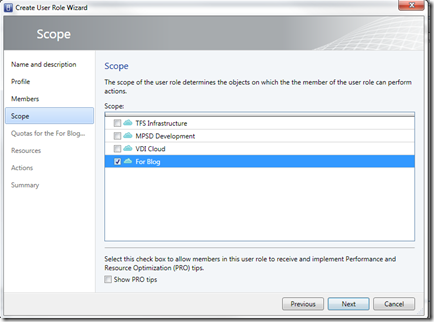
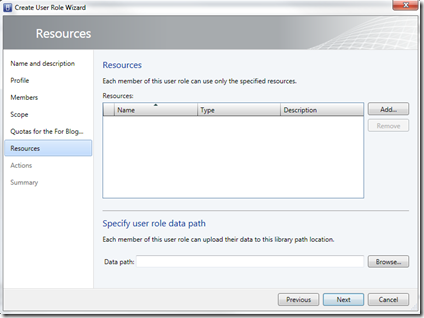
- If you’d like to limit scope to specific VMs (see TechWriter early), you would scope them in the Resources page
- Provide the actions the cloud user can do against their VMs they have access to
- Click Finish on the Summary page
What you’ve done thus far is created a cloud, linked it to a set of resources to utilize, and the end-users can now (based on actions allowed) interact with the cloud. You should note that if you created this role and the resources tab looks like this -
The users of this role can see the cloud but it looks boring, or as I like to say, empty. <g>
Let’s get these cloud users access to some existing VMs as it is very likely that they are already using VMs hosted on the fabric. They will be angry if they can’t access their VMs in the console (learned experience!)
Adding Existing Guest VM’s to the Private Cloud
The last step will provide a single user role access to a VM (rinse, repeat if you have more than 1). For VMs that are created by the end-user, the VMs are automatically owned by the end-user but if they were not the creator they will not have access. To grant access to view their VM in VMM 2012, do the following-
- Click on VMs and Services in wunderbar
- Click the Host group, and select your physical host
- In the right-pane, you will see a list of Virtual Machines currently hosted on that host
- Right-click on the virtual machine, select properties
- Under the General tab, you will see a Cloud: drop-down menu. Select the Cloud from the drop down.
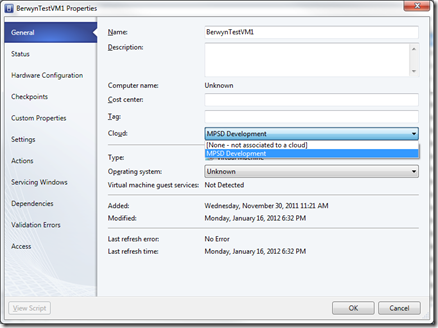
This associates the Virtual Machine is now a part of the cloud. This means that the VM is present to those who have Access. As I mentioned above, one of the key principles of a cloud is to not make all resources available to everyone just through “membership” of the cloud. Instead, you have to grant explicit access to the resource.
To do this, you will do the following-
- Continuing from above through properties of VM
- Click Access
- Click Select to provide a self-service Owner
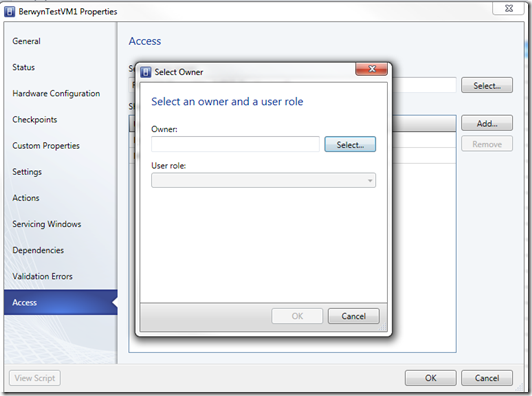
- To share this VM resource with the entire cloud role, click Add under Shared Self-Service users or roles
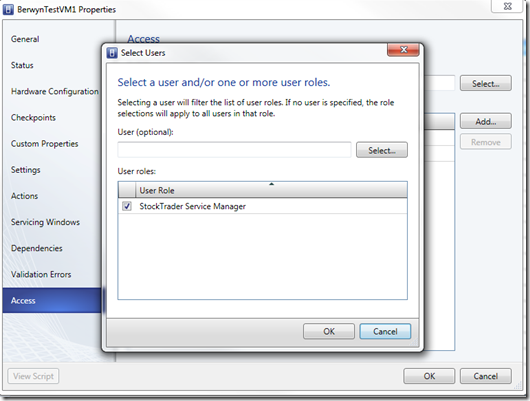
- Click OK
The end result is you now have a host group, that is a member of a Private Cloud, that is now presented to a set of users through a role, and lastly has a set of access to the resources within that cloud.
Easy, right? No problem… You now have a bouncing baby Private Cloud  ! Be careful and gentle…
! Be careful and gentle…
Putting it all Together
That’s it. It isn’t nearly complete and if this was a legal case in the USA, the jury would certainly say that we’ve not met our burden of proof (no matter if civil or criminal!) However, we have in a brief manner shared more details to get you started building your private cloud and I hope that it also helps you think through what you need to do.
In this example, I’ve moved most infrastructure straight over from VMM 2008 R2 to VMM 2012 though I’ve not enabled some of the powerful features such as Fabric management. This can be details for a later time. However, if you follow these steps you can easily get self-service users managing their infrastructure assets (virtual machines, ISOs, VHDs, templates, etc.) while you spend your time focusing on the fabric.
In a future post, I will share some strategies I’ve taken to ensure that our development team utilizes assets in the library correctly… Stay tuned.
Enjoy!
Thanks,
-Chris