Azure AD B2B…how to work with partners and subsidiaries
Azure AD Business-to-Business or Azure B2B is a topic of interest among nearly every organization I speak with. Today many organizations either have a 3rd party IDPs (identity providers) or ADFS deployed and federate with their business partners. Federation establishes a trust whereby providing two-way or one-way access to company resources and applications.
However, with the abundance of SaaS applications that now drive many business functions and processes, companies require a method to allow business partners access to those applications as well.
For example, business partner visibility into inventory management systems, CRM, marketing, O365, and even HR applications is necessary to ease the flow of the business partnerships and allow for collaboration on projects.
Fortunately, Azure Active Directory offers what is called Azure AD B2B where users from an external organization may be invited to access applications of the company who invited them. Another use for Azure B2B is working with subsidiaries or mergers/acquisitions to provide company wide access to resources.
To learn more about Azure AD B2B please visit: /en-us/azure/active-directory/active-directory-b2b-what-is-azure-ad-b2b
Inviting external users to Azure AD
There are a few options that may be utilized when inviting a user to your Azure AD tenant:
- Azure AD admin portal
- PowerShell – single invite or bulk upload
- Microsoft Graph
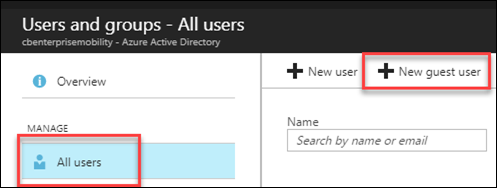
Azure AD admin portal invitation process
- Navigate to portal.azure.com as the admin for the tenant you’d like to invite the external user to.
- Locate Azure Active Directory and select User and Groups
- Select All users
- Select New guest user as shown below
- Fill in the email address of the user you’re inviting, add a personalized message if necessary and select Invite. From there, the invited user will receive a mail that I display later in this post.
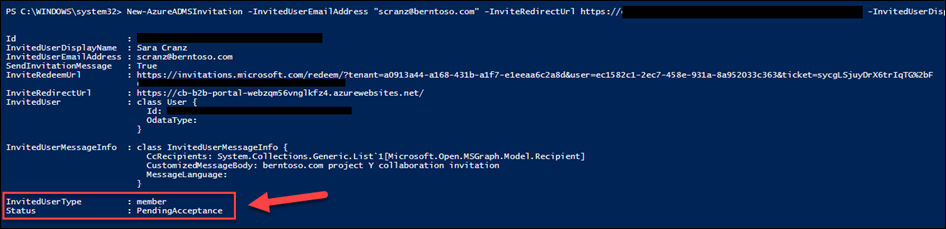
PowerShell single user invitation process
Using PowerShell to invite an external user is self-explanatory. However, open PowerShell, sign on as an administrator to Azure AD and make the necessary changes to the script below and execute.
New-AzureADMSInvitation -InvitedUserEmailAddress "scranz@berntoso.com" -InviteRedirectUrl https://myapps.microsoft.com -InvitedUserDisplayName 'Sara Cranz' -InvitedUserMessageInfo $messageInfo -InvitedUserType member -SendInvitationMessage $true
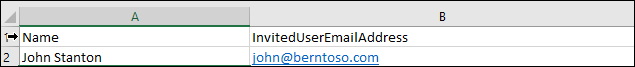
PowerShell invitation process - Bulk upload
If a bulk user invitation process is desired, users and email addresses may be pasted into a .csv file and used for upload.
Example .csv file
More details about bulk upload here: /en-us/azure/active-directory/active-directory-b2b-code-samples
Note: make sure the .csv is in proper format or the script will fail.
Guest user invitation redemption process
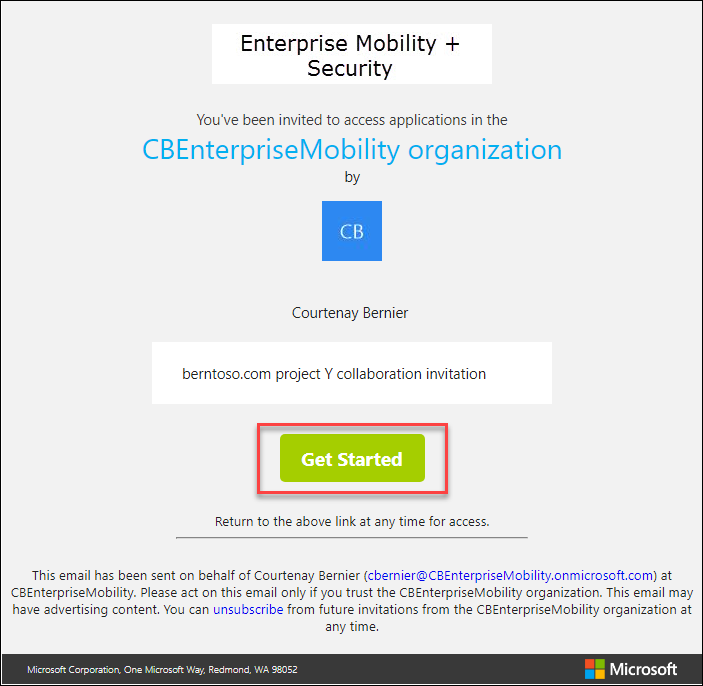
Once the user(s) receive an invitation mail, they’ll see something similar to the image below. The user will then select “Get Started” from the email to begin the invitation redemption process.
Dynamic Groups
Once external users exist in a tenant, dynamic group memberships may be used to automatically assign users to group, for example, any user with @contoso.com may be dynamically assigned to Group A. Group A can also be assigned to SaaS applications or assigned to SharePoint Online/OneDrive sites, so as soon as a user is assigned to a group they’ll have immediate access to the app(s) assigned to it.
Dynamic group membership eases the management process of adding and removing users to applications. Simply assign a group to the application permission and use dynamic group rules to automatically assign and remove users. You can even use attributes such as employeeId, mail, or companyName as attributes to look for, however there are many more attributes to choose from and depending where the users originates from, you may want to get creative. Finally, for applications that support provisioning, guest users may be automatically provisioned and provisioned to SaaS applications which provides full user lifecycle management.
For more details about Azure AD Dynamic Groups please visit: /en-us/azure/active-directory/active-directory-groups-dynamic-membership-azure-portal
Azure AD B2B Licensing
Certain Azure AD B2B scenarios have licensing implications and the following site addresses licensing scenario best: /en-us/azure/active-directory/active-directory-b2b-licensing
For example, even though users may have the role of guest or member, depending on where they originated from, additional licensing may be needed. For example, if a user is invited that is from a subsidiary, Azure AD Premium would be required for that user, however if the user was invited from an external partner, they may be covered under the Azure AD B2B license.
Refer to the link above to make sure you have a clear understanding of which licenses are required and when.
April 2018 update
Allow or block invitations to Azure AD B2B users from specific organizations: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-b2b-allow-deny-list
Pay close attention to the following please:
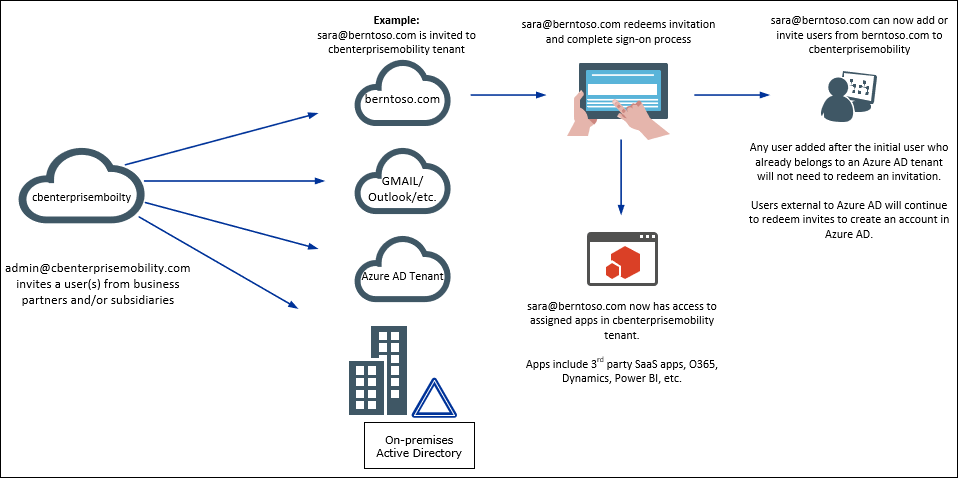
If invited users already have an existing O365 or Azure AD tenant for their own or MSA will not need to go through the invitation process, however tall users will presented with consent (see May 2018 update below). After which, the external user that belongs to the partner tenant can now add users can from their tenant, and those users will not need to go through the invite redemption process either. This is only true if there are only Azure AD tenants or MSA in play.
However, if users are external to Azure AD (e.g. gmail.com, AD on prem, or another email address) the first user added to the tenant can invite other users, however those users still need to go through the redemption and consent processes as there are no accounts for those users that exist in an Azure AD tenant of their own.
In summary, any user that doesn’t already have an Azure AD tenant for their org or MSA and is invited to Azure AD, still needs to go through the invitation redemption process.
May 2018 update:
Exciting improvements to the B2B collaboration experience: https://cloudblogs.microsoft.com/enterprisemobility/2018/05/14/exciting-improvements-to-the-b2b-collaboration-experience/
Guest user invitation redemption process – continued
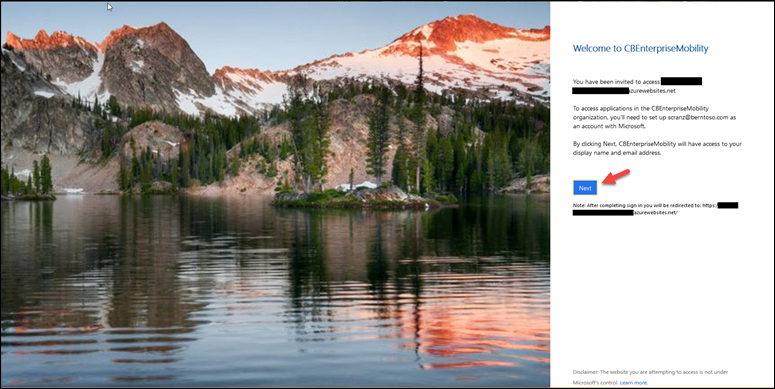
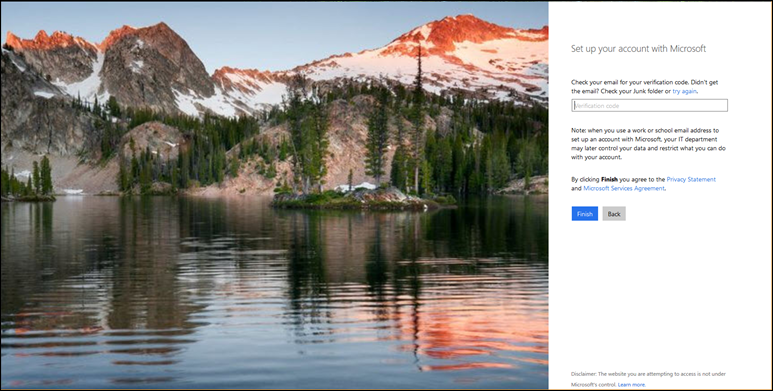
Because I invited a user that is not part of an existing Azure AD tenant, they’ll need to run through the account setup process as shown below. If the user already resides in an Azure AD tenant of their own, they would simply sign on and access application assigned to them.
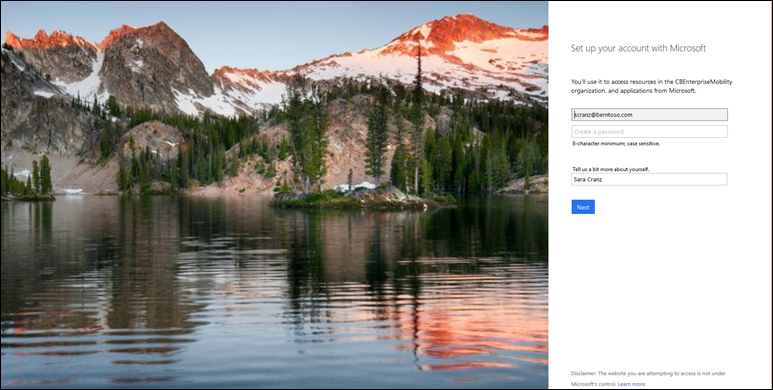
Here the user associates a password with their account (under the covers a new Azure AD tenant is created for berntoso.com and users are added to it).
The user will receive a verification code in their inbox they’ll need to use to finish.
Once the verification code is verified the account is created in the Azure AD tenant:
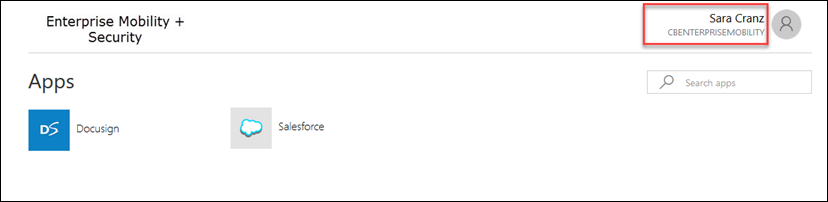
Once the redemption process is completed they’re taken to the URL that was provided in the invitation process the administrator performed (e.g. myapps.microsoft.com) and the user now has access to SaaS applications in your tenant as shown below. Send users links to SharePoint Online, Dynamics, Power BI, OneDrive, etc. for direct access to those applications.
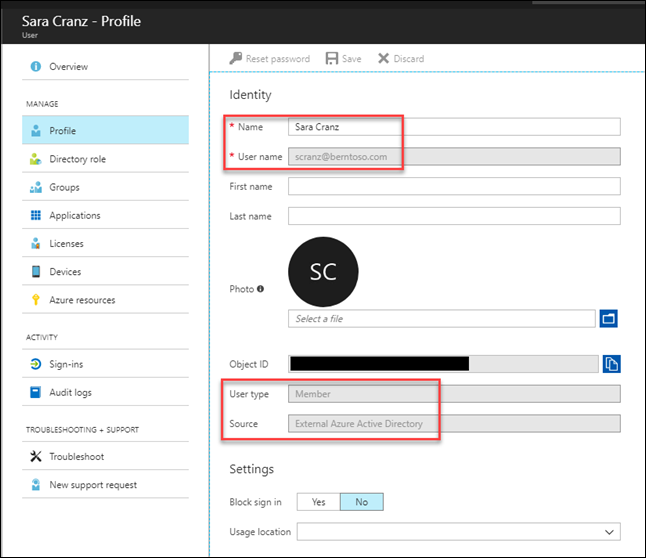
User details
By navigating to Azure AD and locating the user we see the following:
Does the user have to be a member? No, they can be a guest as well and still be able to invite users from their tenant.
Application/Group Assignments
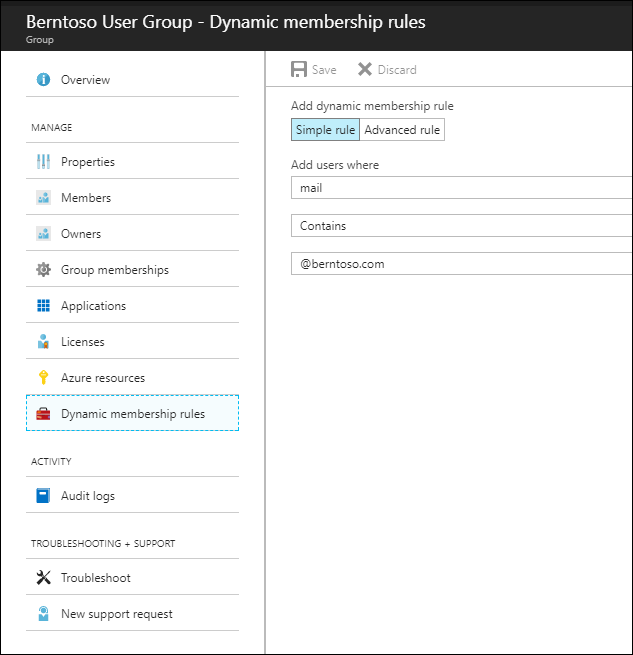
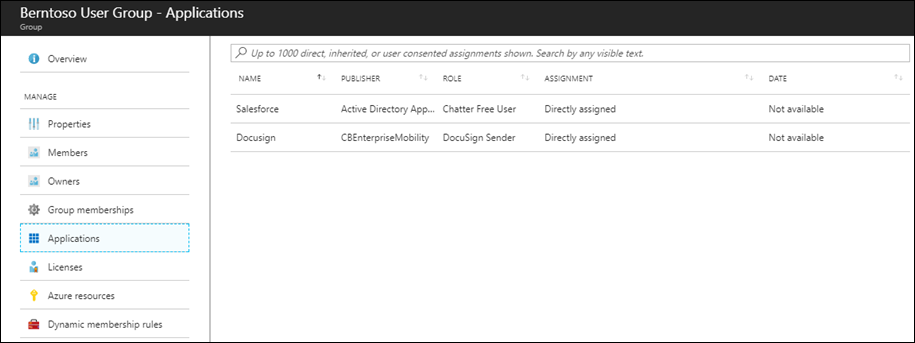
Dynamic groups may also be utilized to automatically add users to a group or groups as well as a group may be assigned to integrated SaaS applications to provide SSO or even provisioning. For example, I have a dynamic group assigned to OneDrive and configured to automatically add any user with the @berntoso.com mail address:
Any user that has the @berntoso.com email address is automatically assigned to the “Berntoso User Group” which is already associated with a SaaS application.
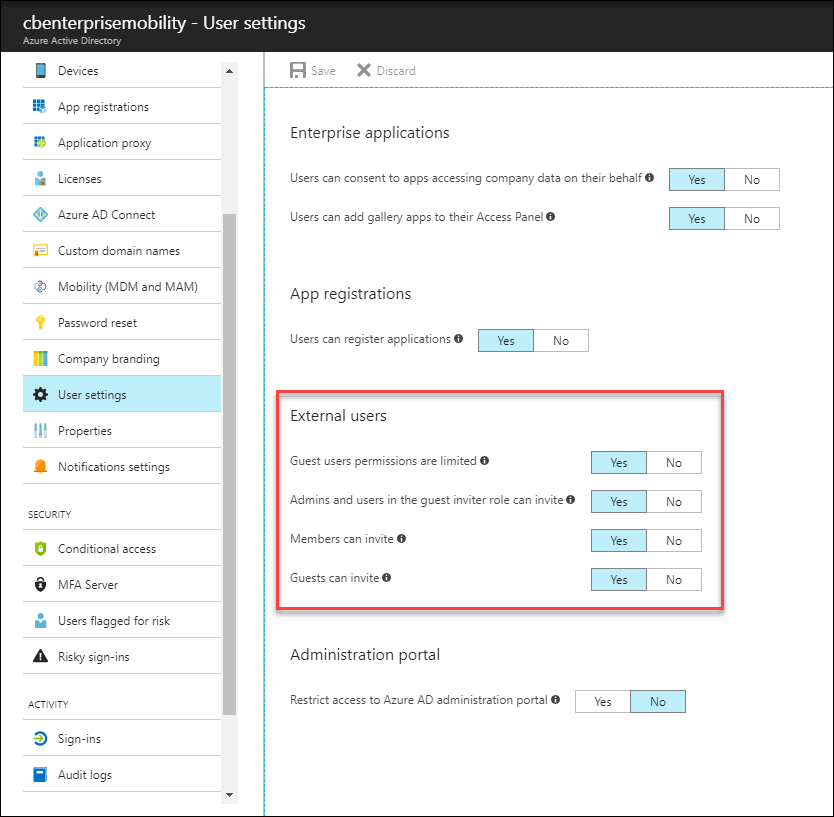
To modify what type of permissions guest users, have within your Azure AD tenant navigate to Azure Active Directory and select “User settings”. There we see external user settings as shown in the image below.
For more details, please visit: /en-us/azure/active-directory/active-directory-b2b-delegate-invitations
Converting the user type, i.e. Guest/Member
Although this is optional and really not recommended, however users may be converted from guest to members and vice versa using the “UserType” attribute (although they’re one in the same and typically only changed for identification purposes, e.g. external user vs. subsidiary user). If guest permissions are limited, see image above, you may want to designate certain users as members, so they can add and/or invite users.
Add the user as a member type instead of a guest. If the user is already a guest, you can promote users to member using the following PS command:
Set-MsolUser -UserPrincipalName user_contoso.com#EXT#@contoso.com -UserType Member
For additional details about user properties and UserType scenarios please visit: /en-us/azure/active-directory/active-directory-b2b-user-properties
Azure AD B2B custom admin and self-service portal
By utilizing Microsoft Graph, organization may create their own Azure B2B admin and self-service portals. For example, the invitation redemption process may be customized to have the user fill out additional fields such as company name, city, state, phone, etc. Those fields will be populated in the corresponding fields in Azure AD for the user. In addition, users must agree to your terms of service before requesting access. The options for the self-service portal are endless and may be developed to meet your organizations requirements.
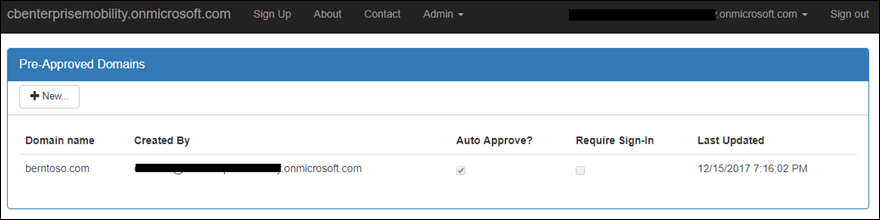
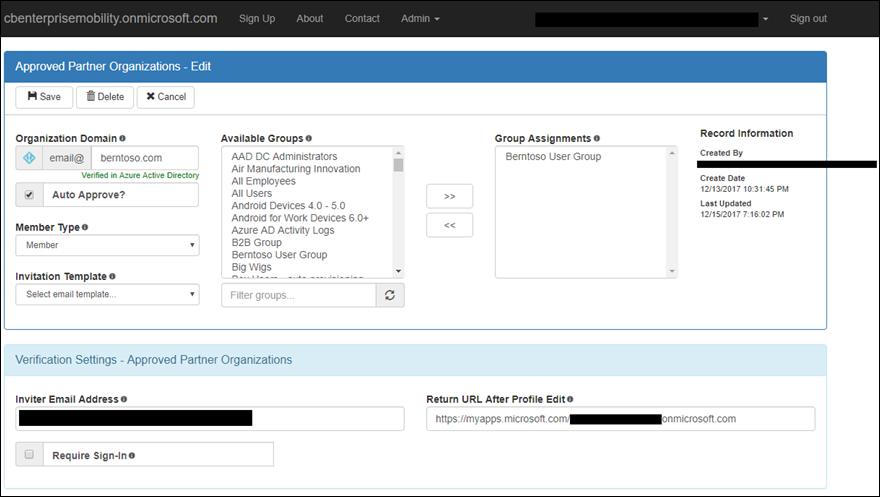
The sample admin portal provides the ability to add different partner domains as shown below:
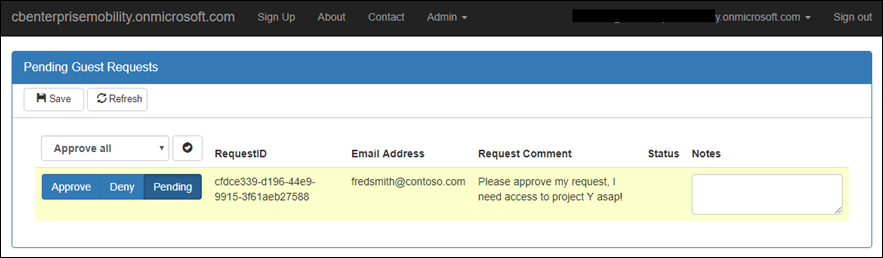
Users who request access via the self-service portal can either be auto approved or added to an a queue for approval as shown below. Admins will then approve or deny the user access.
For each of the partner domains, additional settings may be added as shown below. I my example below, I auto approve users who sign in with @berntoso.com, users are added as members (not guests), and they’re automatically assigned to groups (dynamic groups may be used instead of group assignments) the admin experience customizable by you and a developer.
For more details on creating and customizing an Azure B2B admin and self-service portals, including downloading a sample portal please visit: https://github.com/Azure/active-directory-dotnet-graphapi-b2bportal-web
Additional developer resources
Create Invitation: https://developer.microsoft.com/en-us/graph/docs/api-reference/v1.0/api/invitation_post
Invitation Manager: https://developer.microsoft.com/en-us/graph/docs/api-reference/v1.0/resources/invitation
Azure Active Directory B2B collaboration API and customization: /en-us/azure/active-directory/active-directory-b2b-api
Delegate invitations for Azure Active Directory B2B collaboration: /en-us/azure/active-directory/active-directory-b2b-delegate-invitations
Conclusion
We covered a lot of details about Azure AD B2B, whether you’re looking to invite business partners or employees from subsidiaries, Azure AD has your collaboration scenarios covered.