Windows 10: Intune + Windows BitLocker management? = Yes
This week’s post is all about Windows BitLocker management with Microsoft Intune. When it comes to data protection, internal and external drive protection is important in the event a device is lost or stolen.
In the past to manage Windows BitLocker we typically needed to create Group Policies or use System Center Configuration Manager (which is still the case with Windows 7, 8.x). However, with Windows 10, Intune now manages BitLocker settings natively right from the admin portal.
To create a new BitLocker policy, navigate to portal.azure.com and locate the Intune admin portal.
- Select Device Configuration –> Profiles –> Create profile
- Name the policy, select Windows 10 and later under Platform, and for Profile type select Endpoint protection:
Next select “Windows Encryption” to configure BitLocker
As we can see, there are many settings for BitLocker that can be configured to meet the security needs of most environments requiring drive encryption.
Syncing the new BitLocker policy from Intune
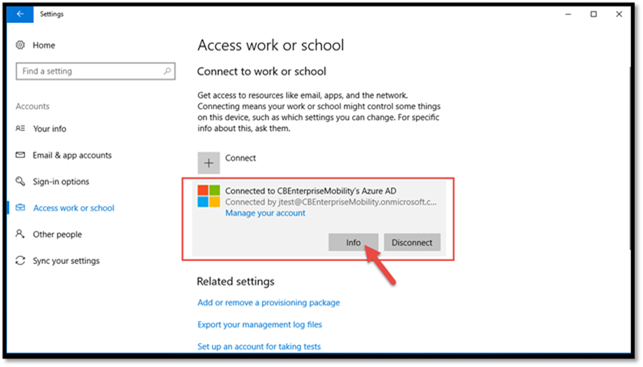
On the Windows 10 client that’s enrolled with Intune via MDM select Settings from the start menu -> Accounts -> Access work or school and find the setting connected to Intune and select it, then select Info:
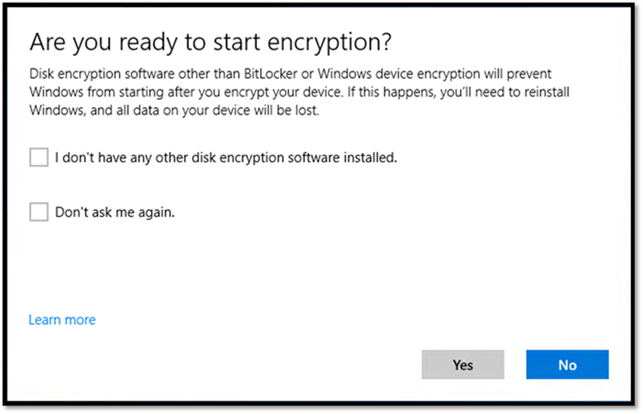
Finally select “Sync” to sync policies from Intune. You’ll see a notification stating encryption is needed as shown below:
Select the Encryption needed notification and begin encrypting the device:
Managing BitLocker using the Configuration Service Provider
Beginning with Windows 10 Creators Update (1703) BitLocker can also be managed and enabled with Microsoft Intune by using Configuration Service Provider (CSP) settings. Note: Windows Business/Enterprise/Education is required.
What is a Configuration Service Provider (CSP)?
A configuration service provider (CSP) is an interface to read, set, modify, or delete configuration settings on the device. These settings map to registry keys or files. Some configuration service providers support the WAP format, some support SyncML, and some support both. SyncML is only used over–the–air for Open Mobile Alliance Device Management (OMA DM), whereas WAP can be used over–the–air for OMA Client Provisioning, or it can be included in the phone image as a .provxml file that is installed during boot.
Source: /en-us/windows/client-management/mdm/configuration-service-provider-reference
Why use a CSP?
CSPs may be used with 3rd party MDM solutions when supported or if settings are not natively available via the MDM admin interface.
Let’s configure BitLocker to require encryption after device enrollment with Intune
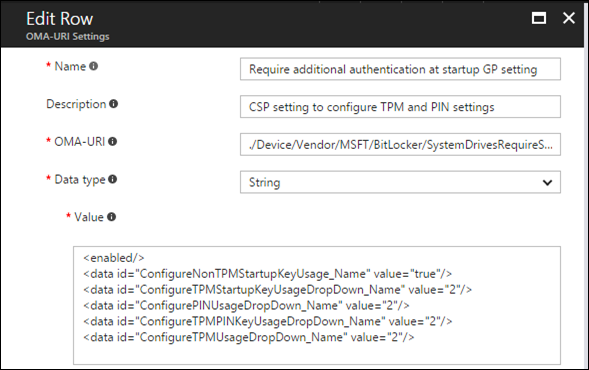
I’ll keep it simple for this post, however the full BitLocker CSP reference is located here including managing TPM and PIN settings: /en-us/windows/client-management/mdm/bitlocker-csp
1. Navigate to Microsoft Intune, select Device configuration -> Profiles -> Create profile
2. Name the profile, select Windows 10 and later as the Platform, then select custom as the Profile type.
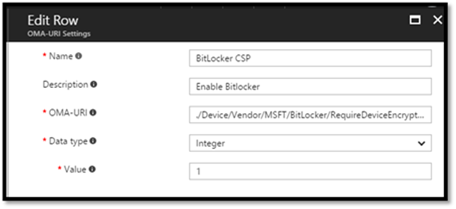
3. Select Add and fill in the spaces as shown below:
(the OMA-URI above is: ./Device/Vendor/MSFT/BitLocker/RequireDeviceEncryption)
4. Save the policy
5. Deploy the policy to an Azure AD group
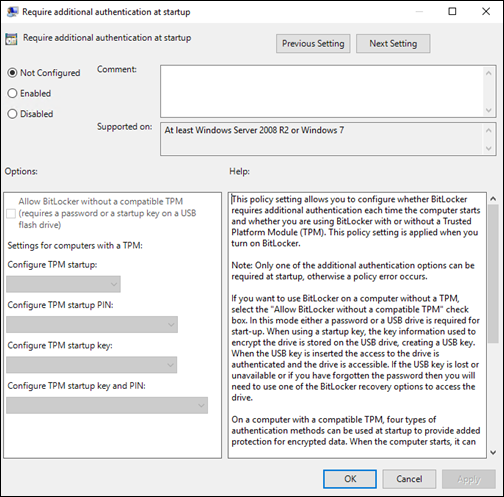
A question you may have is, “how do the BitLocker CSP policies map to Group Policies?” The following is an example of an Active Directory Group Policy vs. a CSP setting in Intune:
Group Policy in Active Directory
Verifying BitLocker is enabled
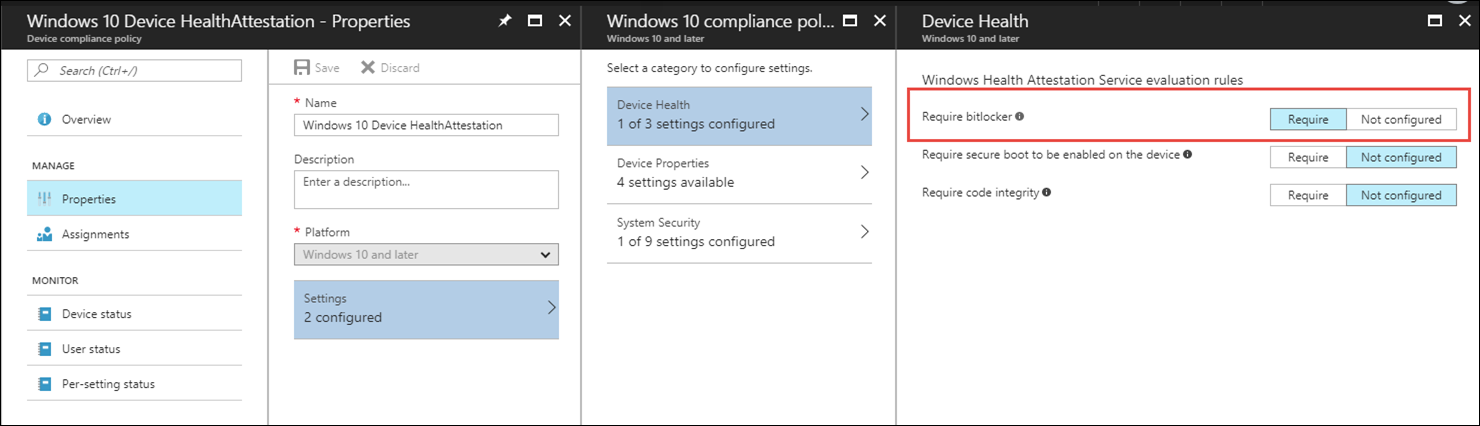
Microsoft Intune will also verify if BitLocker is enabled by using Windows Health Attestation.
Configure Windows Health Attestation by selecting “Device compliance: from the Intune admin portal, then Policies –> Create Policy
Configure the settings as shown below.
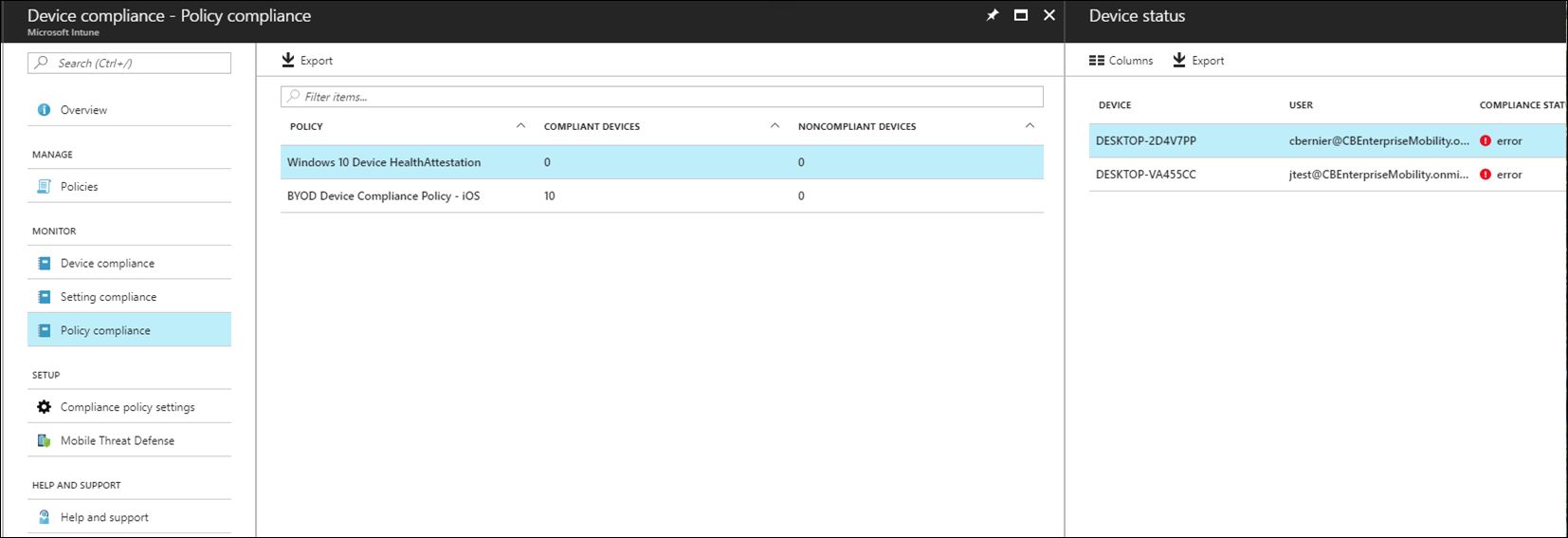
Under the compliance blade select “Policy compliance” to check which devices are compliant or not with BitLocker. As shown below, I have two devices that are not compliant with BitLocker.
That’s it, BitLocker can now be managed by Microsoft Intune for Windows 10.
As we map more Group Policies to CSPs it’s important to know if they’re available or not. Use the following tool to see a report of which existing Group Policies on your devices map to CSPs: https://github.com/WindowsDeviceManagement/MMAT
Troubleshooting
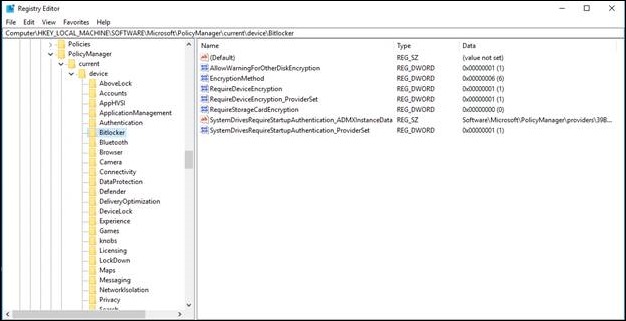
BitLocker settings land under the following registry keys:
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\Bitlocker
- Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\default\Bitlocker
Additional References
To see what Windows CSPs were added by version please visit: /en-us/windows/client-management/mdm/configuration-service-provider-reference#a-href-idnewcspsanew-csps-added-in-windows-10-version-1703
To learn more about the which settings via the Configuration Service Provider (CSP) is supported for Windows 10 please visit the CSP reference: /en-us/windows/client-management/mdm/configuration-service-provider-reference
For a full Policy CSP reference please visit: /en-us/windows/client-management/mdm/policy-configuration-service-provider
Understanding ADMX-backed policies (i.e. Group Policy to CSP mapping): https://docs.microsoft.com/en-us/windows/client-management/mdm/understanding-admx-backed-policies
![clip_image002[1] clip_image002[1]](https://msdntnarchive.blob.core.windows.net/media/2017/07/clip_image0021_thumb.png)
![clip_image004[4] clip_image004[4]](https://msdntnarchive.blob.core.windows.net/media/2017/07/clip_image0044_thumb.png)