Windows Server Network Policy Server + Azure AD NPS Extension = VPN + Azure MFA
On February 6, 2017, the Microsoft Azure AD team announced the public preview of Azure MFA cloud based protection for on-premises VPNs.
This is facilitated via a downloadable extension that integrates directly with the Windows Server Network Policy Server (NPS) role.
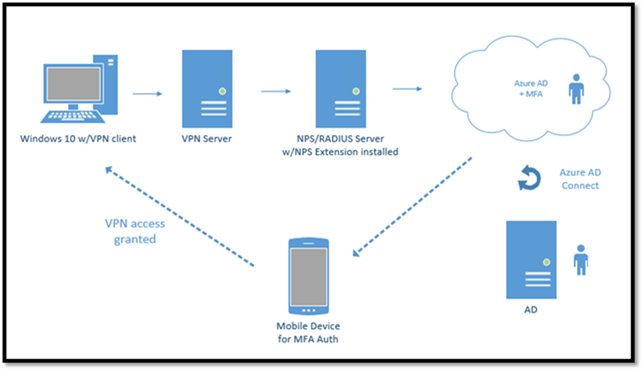
With the NPS Extension for Azure MFA, which is installed as an extension to existing NPS Servers, the authentication flow includes the following components:
- User/VPN Client: Initiates the authentication request.
- NAS Server/VPN Server: Receives requests from VPN clients and converts them into RADIUS requests to NPS servers.
- NPS Server: Connects to Active Directory to perform the primary authentication for the RADIUS requests and, if successful, pass the request to any installed NPS extensions.
- NPS Extension: Triggers an MFA request to Azure cloud-based MFA to perform the secondary authentication. Once it receives the response, and if the MFA challenge succeeds, it completes the authentication request by providing the NPS server with security tokens that include an MFA claim issued by Azure STS.
- Azure MFA: Communicates with Azure Active Directory to retrieve the user’s details and performs the secondary authentication using a verification method configured for the user.
How is it set up?
The setup of Windows Server NPS is very simple, install the Windows Server role, configure NPS for VPN access via RADIUS with a shared secret, set up a connection and network policy and you’re set. More details listed here: https://technet.microsoft.com/en-us/network/bb545879.aspx
Next configure the VPN server to point to your RADIUS server (i.e. NPS), this can be Windows Server RRAS or a 3rd party VPN server. The NPS extension is installed directly on the Windows Server NPS server and registered with an Azure Active Directory tenant where users are enabled for Multi-Factor Authentication.
The following is a diagram of my environment (all hosted on VMs in Azure):
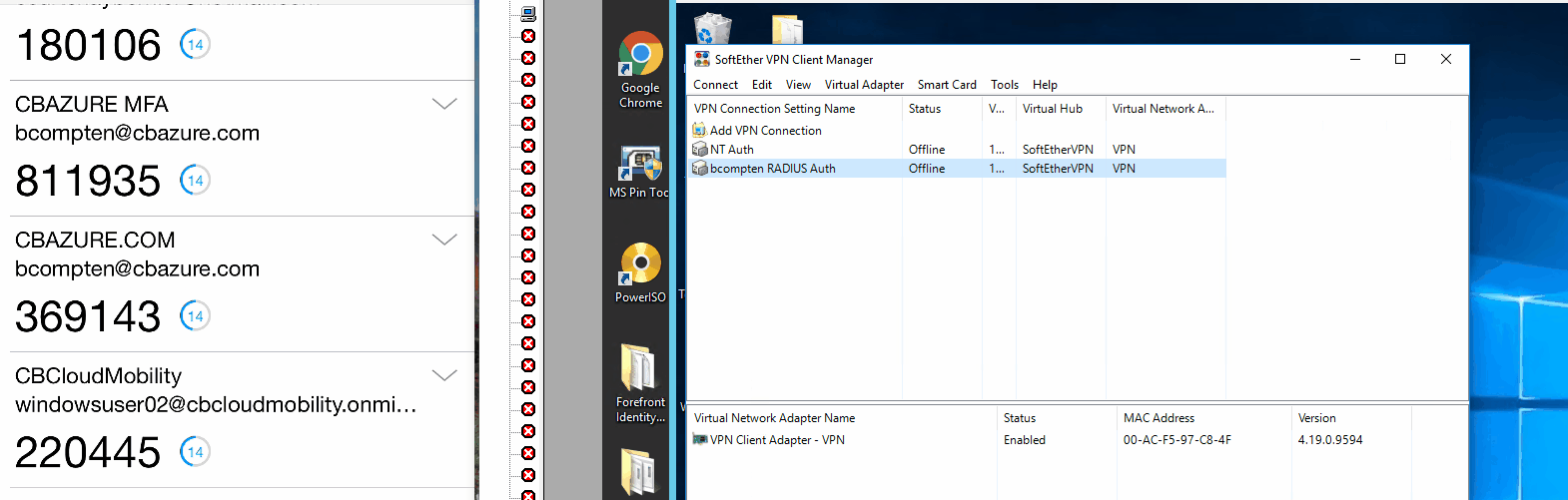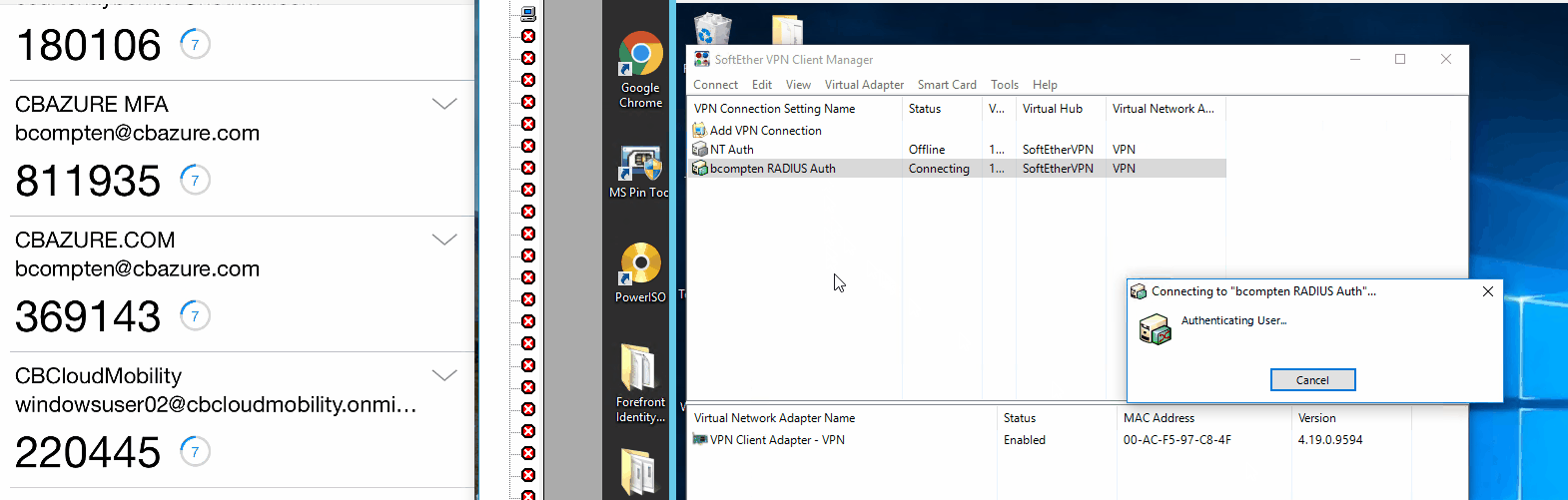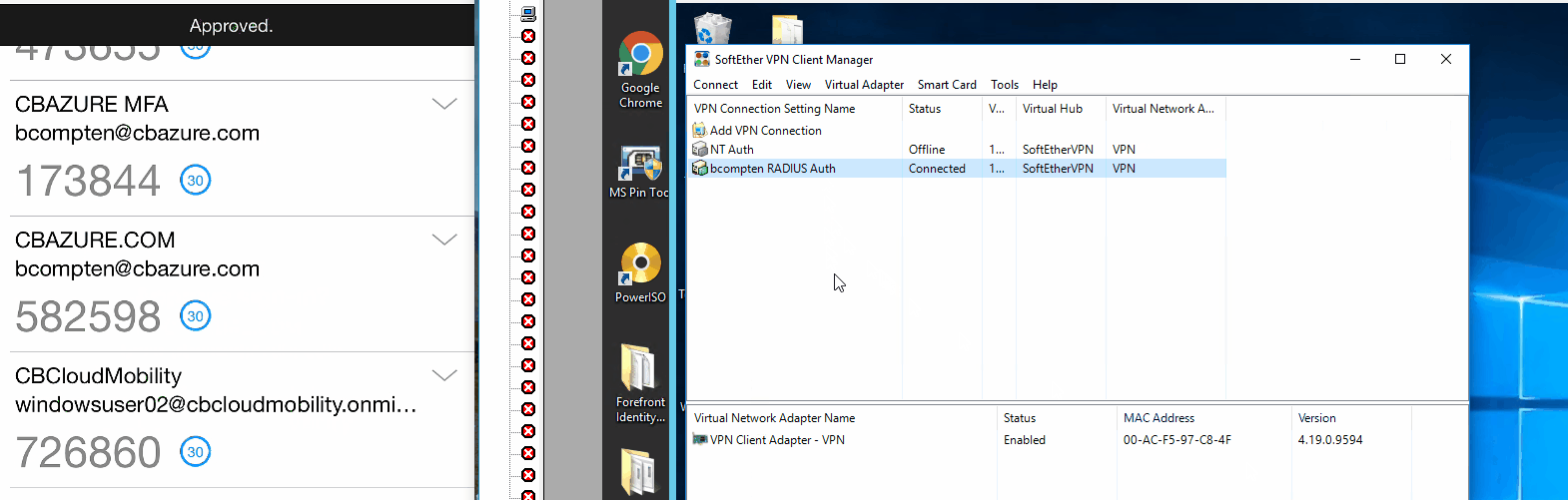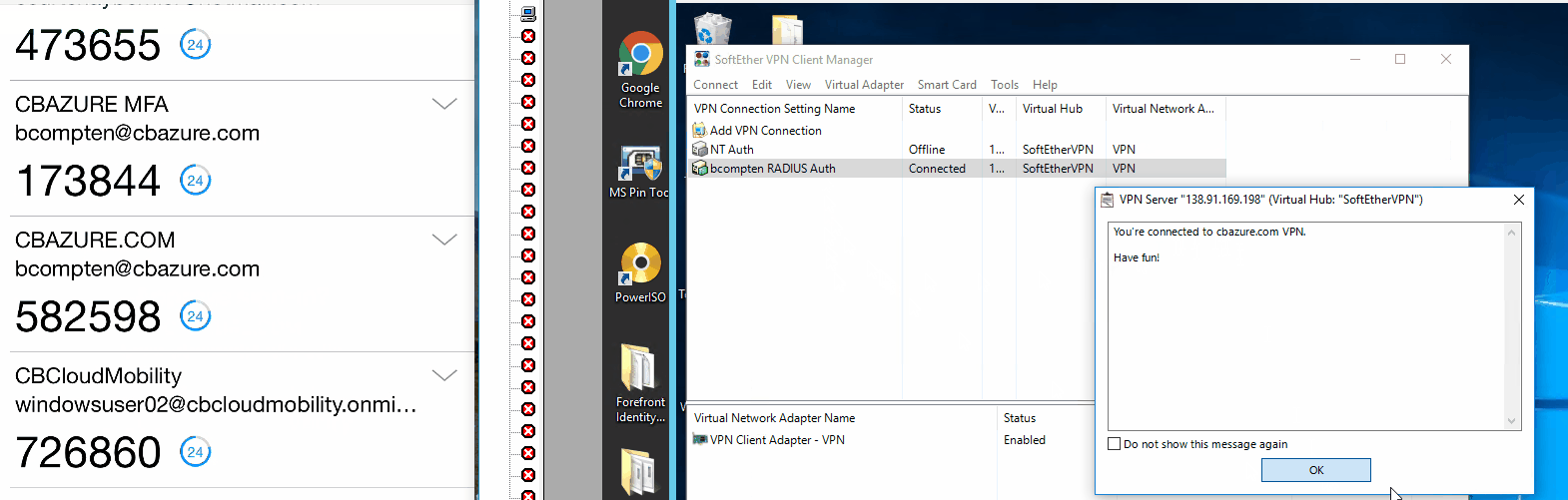
Here is a quick video of it in action:
Note: for this demo I use SoftEtherVPN with RADIUS authentication. Backend is Windows Server 2016 NPS with the NPS extension installed, and Windows 10 with the SoftEtherVPN client enabled for RADIUS authentication.