The World of Mobility
It’s difficult to ignore the world of mobility. We often carry a one or more devices such as a Windows PC, Mac, iPhone, Android, and so on. Additionally, we bring these devices into the workplace and connect to applications, email, and files. This isn’t anything new, however the complexity of juggling devices and managing them gets harder every day. Why? Because each device manufacturer and the OS software that runs on them is managed differently because of how they’ve designed and published their management APIs. Some device OEMs allow easy management because of the openness of their software; while others control every aspect and only publish a subset of management capabilities and require the use of another software layer with APIs to manage the OS, thus pushing you toward their management solution. There are many mobile device management (MDM) solutions out there today and depending on your business and policy needs, you may only need a subset of those capabilities or the full feature set.
From a Microsoft prospective there are a few mobile device management options to choose from and some solutions have baseline capabilities while others vastly expand on those.
Let’s take a look at each option:
Mobile Device Management (MDM)
Microsoft Exchange ActiveSync - offers capabilities such as remote wipe, password policies, and device encryption policies. It’s fairly basic, however it may address baseline needs to control access to email if that’s really all you need.
For more details please visit: https://technet.microsoft.com/en-us/library/aa998357(v=exchg.150).aspx
Exchange Online (O365) ActiveSync – offers the same capabilities as Exchange ActiveSync described above.
For more details please visit: https://technet.microsoft.com/en-us/library/jj945881(v=exchg.150).aspx
Office 365 MDM
In addition to ActiveSync policies, Office 365 provide light-weight MDM policies across Windows Phone, iOS, and Android including settings such as conditional access, device management (security policies, jailbreak detection), and selective wipe. These are very basic policies; however they may be just enough.
For more details please visit: https://technet.microsoft.com/en-us/library/ms.o365.cc.devicepolicysupporteddevice.aspx
Microsoft Intune
In addition to ActiveSync policies and overall MDM policies (management of the devices features such a camera, passcode, encryption, etc.). Microsoft Intune provides advanced MDM across iOS, Android, Windows Phone, and Windows client OS. For example, Intune can provision and manage Wi-Fi and VPN (device and app-specific), email profiles, selective wipe, conditional access, and much more. Use Intune for your overall MDM policies.
For more details please visit: https://technet.microsoft.com/library/dn646960.aspx
Microsoft Intune vs. Office 365 MDM: https://technet.microsoft.com/en-us/library/dn957912.aspx
System Center Configuration Manager + Intune
Connect Configuration Manager with Intune and it adds Mac, Linux, and Unix management as well as Windows OS deployment, deeper reporting and monitoring capabilities. Configuration Manager also pulls in the Intune settings so you can manage Mac, Linux, Unix, iOS, Android, Windows (PC) and Window Phone from one interface.
For more information please visit: https://technet.microsoft.com/en-us/library/jj884158.aspx
For a comparison across Intune and Configuration Manager 2012 and 2012 R2 please visit: https://technet.microsoft.com/en-us/library/dn957912.aspx
Mobile Application Management
Application Management of apps that leverage the Intune app SDKs is unique to Microsoft as Intune can apply what are called Mobile Application Management (MAM) policies to manage applications such as preventing cut, copy, and paste into non-managed applications (e.g. preventing cut, copy, and paste from Microsoft Outlook to a native email app).
MAM is popular because in addition to controlling the application, policies can be applied to deploy, restrict how content is used, and wipes such as only wipe corporate data while leaving personal data in place (e.g. selective wipe). For example, Outlook can be deployed to an iOS device and if a corporate and personal account is created, a selective wipe will only wipe out the corporate data from the email profiles and leave the personal email profiles intact. Intune also offers the ability make a custom developed app a managed app by using the Intune app wrapping tool available for Android and iOS.
For more details on which applications support MAM policies please visit: https://technet.microsoft.com/en-us/library/dn708489.aspx
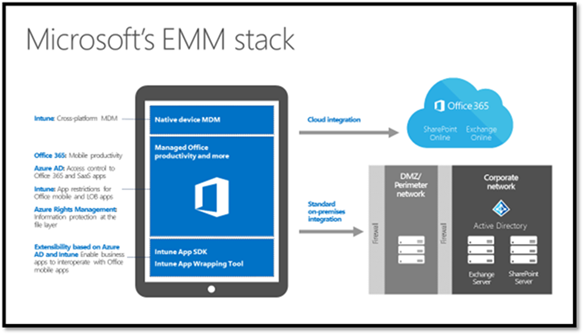
Below, we visualize the management of a device by showing how typical MDM and MAM solutions segregate management on a device:
Overlay Microsoft MDM/MAM solutions and you receive the following:
Let’s discuss two more technologies listed in the diagram above:
Azure Rights Management
What if securing the device and the applications aren’t enough? This brings us to Azure Rights Management Services (RMS). In the past Rights Management was deployed on premises, requires a PKI environment, a few servers and so on. With Azure RMS no infrastructure is required and you can even tie in with existing technologies on premises such as SharePoint and Exchange.
Azure RMS SDK 4.1+ supports Mac OS X, iOS, Android, Windows Phone, Window Store, Portable C++ for Linux OSs (e.g. Ubuntu 14.3, OpenSUSE 13.2, CentOS 7) more details here: https://blogs.technet.com/b/rms/archive/2015/08/31/rms-sdk-4-1-linux-support-is-now-available.aspx
Azure Active Directory
Identity is probably the most discussed topic during my conversations with customers. Identity also ties everything together, for example application access and single sign-on.
Azure Active Directory provides the following capabilities:
Privileged Access – just in time admin access for sensitive accounts (e.g. administrator accounts).
Auditing and Reporting – for example: anomalous logins, irregular sign in activity, and users with leaked credentials. In addition, there is information covering application usage, RMS usage, account provisioning errors and many more.
Multi-Factor Authentication – MFA is built in, no need to set up additional software unless you’re interested in lighting up on premises applications such as custom applications, VPN, Remote Desktop, and so on.
Self Service Password Management – reduce those service desk calls by allowing users to change and reset password right from the login prompt (reset) or from the portal (reset/change).
Group Management – provide self-service group management to end users and offload the effort of managing groups and users within those groups to separate owners. Take it one step further and utilize dynamic group membership for a true hands off experience.
Azure AD Application Proxy - On premises application access through Azure AD Application Proxy allowing you securely publish and assign applications to your users and even apply MFA on a per application basis. For example, you can publish a line of business or intranet application in just a few minutes.
SaaS application integration – with over 2500 pre-integrated SaaS applications or the ability to add custom applications and specify authentication methods such as federating with Azure AD, Active Directory Federation Services or using a unique user name and password to authenticate. Azure AD has what is required to fulfill your business needs. Check out the application gallery here: https://azure.microsoft.com/en-us/marketplace/active-directory/all/
Device Enrollment – enroll devices with Azure AD for tracking and control. Utilize Office 365 or Microsoft Intune to apply conditional access policies allowing only users and devices that your business approves to access Exchange and SharePoint.
Interested in granting secure file server access to your mobile users? View my previous post about WorkFolders here: https://blogs.technet.com/b/cbernier/archive/2015/06/09/mobile-access-of-files-hosted-on-corporate-file-servers-from-windows-and-ios-devices.aspx
To learn more about what happens when users enroll their personal devices with Intune or O365 please visit: https://technet.microsoft.com/en-us/jj738616.aspx
There is so much more to talk about and I’ll continue to post new topics going forward.