Identity as a Service IDaaS
It seems like there is a lot of discussion going on lately about identity. In fact it’s a very hot topic among most of the organizations I speak with. However identity is not a new topic, there are just better technologies available to manage identity and more companies providing identity solutions.
In the past, identity management solutions were deployed on servers and managed within, however more recently as cloud solutions become more prevalent in our organizations Identity as a Service or IDaaS solutions are taking their place. Why? Because often times traditional identity solutions can be complicated to deploy and manage.
As more and more companies move to cloud solutions, there is less of a need for traditional software hosted on premises. However there are unique situations where hosting identity solutions internally make sense.
Fortunately Microsoft has taken steps to expand identity in the cloud. LiveID is one type of cloud identity that’s been available for years. What about corporate identity or identity that meshes with current identity solutions such as Active Directory? Better yet, how about having it all available as a service?
Microsoft’s corporate cloud identity solution is Azure Active Directory (Azure AD) as well as a solution on top of Azure AD called Azure Active Directory Premium (Azure AD Premium).
Let’s differentiate between the two:
Azure Active Directory
Azure Active Directory is a comprehensive identity and access management cloud solution that provides a robust set of capabilities to manage users and groups and help secure access to applications including Microsoft online services like Office 365 and a world of non-Microsoft SaaS applications.
Azure Active Directory Premium
Built on top of a large set of free capabilities in Microsoft Azure Active Directory, Active Directory Premium … provide a set of more advanced features to help empower enterprises with more demanding identity and access management needs.
Source and additional information: https://msdn.microsoft.com/en-us/library/azure/dn532272.aspx
Now that we have an idea of what the identity offerings are and their differences, let’s take a look at capabilities.
Azure Active Directory
Working with Azure AD is very simple, we’re either creating fresh accounts that are solely hosted in Azure or we’re synchronizing existing accounts with Azure AD.
There are a couple methods to synchronize accounts with Azure AD:
Directory Sync (DirSync)
Copies existing Active Directory accounts to Azure AD. Commonly used with Office 365, Dynamics, Azure, and Intune customers. Password sync is available using this option as well. By default Office 365 and the previously mentioned services use Azure AD as the identity provider, thus it the same directory (e.g. available across all mentioned services).
More information here: https://technet.microsoft.com/en-us/library/hh967642.aspx
Azure AD Sync (AADSync) currently in preview
Used for more advanced configurations, AADSync provides additional functionality such multi-forest and non-Active Directory solutions to Azure AD.
More information here: https://social.technet.microsoft.com/wiki/contents/articles/24053.aadsync-frequently-asked-questions.aspx
Single Sign-On (SSO)
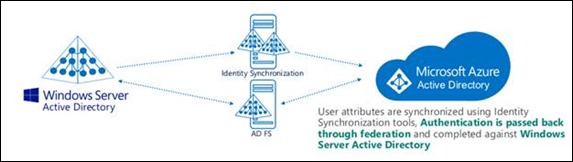
One message I commonly receive from organizations is: “we want SSO for our applications”. However, there is also confusion between Active Directory (Azure or on premises) and SSO. We can start by separating the terms and the technologies. Active Directory and Azure Active Directory provide an identity store for accounts. Single Sign-On is an additive solution that interacts with identity stores.
Single Sign-On is a common request and can be fulfilled with Active Directory Federation Services (AD FS). We can also achieve SSO scenarios using Azure AD Premium (I’ll review that later in this post).
Visually, identity synchronization with Azure AD and single sign-on using Microsoft technologies looks like the following:
Azure Active Directory Premium
Azure Active Directory Premium is an exciting service as it provides self-service group management, self-service password reset and change, Multi-Factor Authentication (MFA), access to Forefront Identity Manager, an access panel for SSO-based user access to SaaS and custom applications, SLA of 99.9%, and reports such as anomaly security reports.
The access panel is where users from any device can access SaaS applications that have been assigned to them. Here’s a peak at what the access panel looks like:
These are applications I’ve selected for this particular user (or group if you prefer using groups).
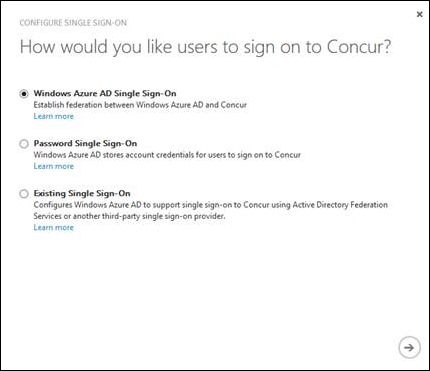
For example, depending on the SaaS application, there can be up to three methods to set up how users will authenticate. Using the Concur application, the following three authentication methods are available:
1. Windows Azure AD Single Sign-On – using Azure AD and the federated identity provider.
2. Password Single Sign-On – users have unique usernames and passwords.
3. Existing Single Sign-On – federation is established already (e.g. AD FS).
Note: authentication or SSO is configured by an administrator not the end user.
Visit https://msdn.microsoft.com/en-us/library/azure/dn308590.aspx to learn more about Azure AD integration with SaaS applications.
Custom Applications
Also notice there are two custom applications (in light blue) available in the access panel, SharePoint Intranet and Operations Manager Portals (web portal for System Center Operations Manager). Using Azure AD Premium we have the ability to publish internal web applications as well. All that is required is an application proxy (a small piece of software that is downloadable from the Azure AD Premium portal and install on a server within your datacenter) and a URL.
Azure Active Directory + Azure Active Directory Premium
Whether accounts already exist or you’re synchronizing existing accounts with Azure AD, accessing it is easy. Simply log into your Azure subscription via the portal and navigate to Active Directory. From here, either create a new directory or select an existing directory. By default any new directories will have the suffix of .onmicrosoft.com. However if you’re already synchronizing accounts from Active Directory there will most likely be a unique domain name, something like yourdomain.com. If not, you can add a custom domain and using the synchronization tools previously discussed to populate accounts from your identity solution.
Licensing
Azure Active Directory is available as part of the Azure subscription whereas Azure Active Directory Premium is a service on top of Azure AD and is licensed per user per month. Another route to licensing Azure Active Directory Premium is via the Enterprise Mobility Suite (EMS). By licensing through EMS you in addition to Azure Active Directory Premium it also grants licenses to Windows Intune and Azure Rights Management.
If you’re a current Azure customer or MSDN subscriber you can enable a 90 day trial of Azure AD Premium right from the Azure Portal. Navigate to Active Directory then the domain you’d like to enable Azure AD Premium on and licenses. From there enable the trial of Azure AD Premium.
If you’re not an Azure customer I encourage you to sign up today: https://azure.microsoft.com/en-us/pricing/free-trial/