Step-By-Step: Configuring Azure Active Directory, SSO and SaaS
Over the last several weeks I have been working with the Canadian Microsoft Partners to help them learn about Azure and grow their Azure practice.
One of the features that garners a lot of attention is using Azure Active Directory to provide single sign-on access to over 2500 SaaS applications. By providing a single sign-on experience for our users, we ensure that they can quickly access the applications they need from a single web portal, and if the user leaves the company we can easily restrict access to the SaaS applications, preventing unauthorized access. An example of this in shown in the following video:
For those of you that have not had the opportunity to look at Azure Active Directory, this feature is your identity and access management for the cloud. Some of the features of Azure Active Directory include:
1. Use single sign-on to access cloud and on-premise web apps
2. Enforce multi-factor authentication with SaaS
3. Integrate with your on-premise Active Directory
Azure Active Directory comes in 3 flavours: Free, Basic, and Premium. Both Free and Basic allow users to use SSO for up to 10 SaaS applications. Premium allows for unlimited SSO to SaaS. For a full comparison of the 3 offerings, see the Azure AAD pricing page.
In this article we will show you how to leverage this functionality to enable your users to seamlessly access the SaaS apps your company uses.
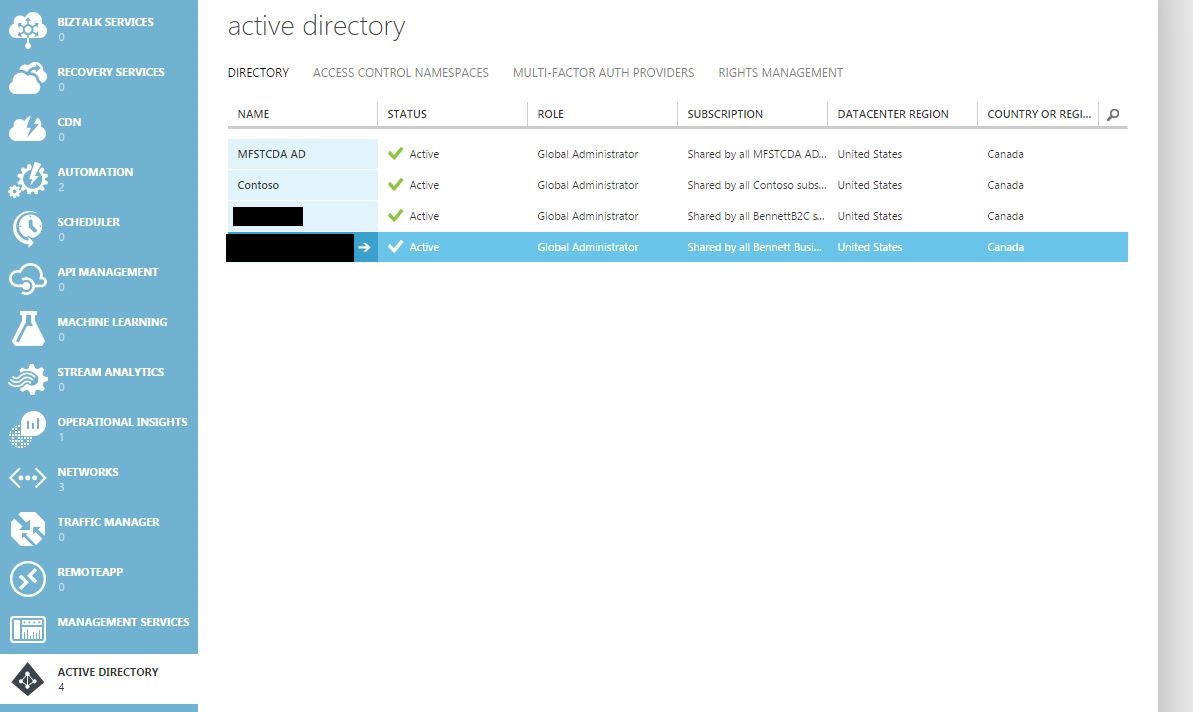
From the Active Directory link from the classic portal, select the active directory you wish to configure.
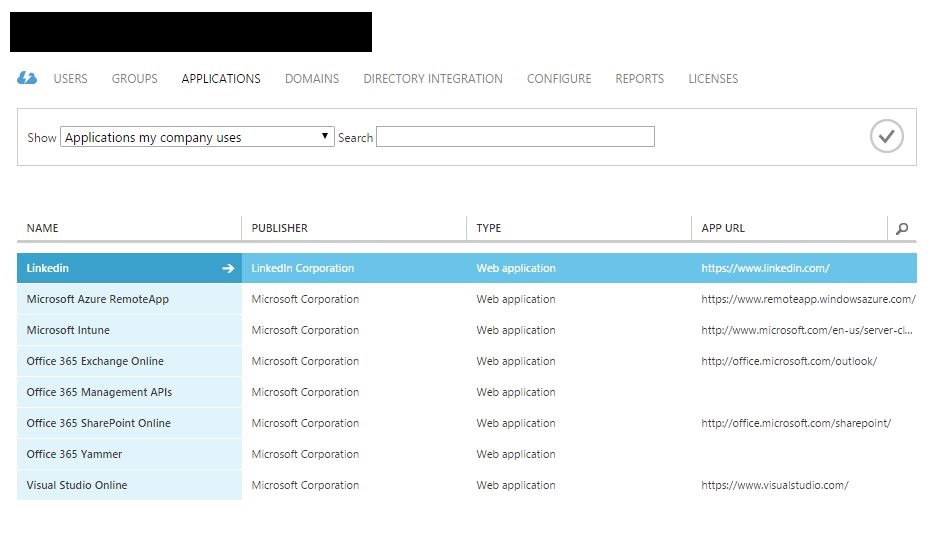
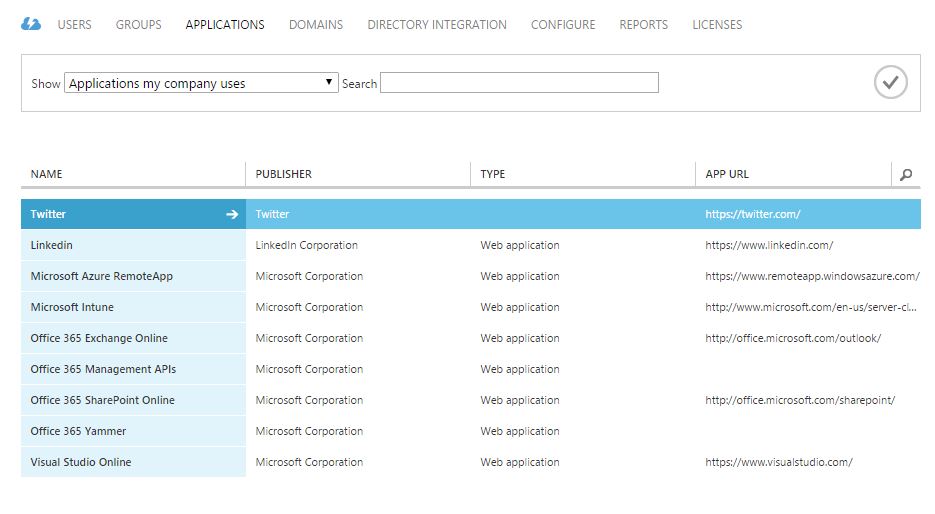
Then select the Applications tab.
In my example, you will see several SaaS applications already configured.
For our example, I am going to add Twitter to my account and provide the "corporate credentials".
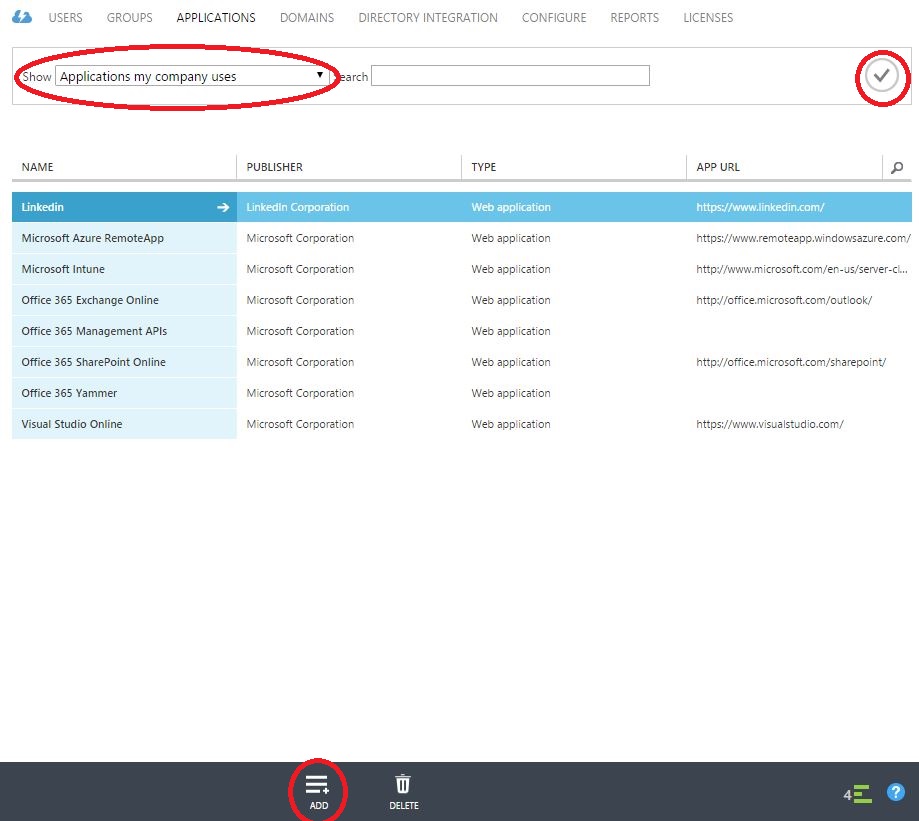
Select Applications my company uses from the Show dropdown at the top of the page. If you have internal applications that you would like to publish, select Applications my company owns. Click the checkmark to the right if necessary, then click Add at the bottom of the page.
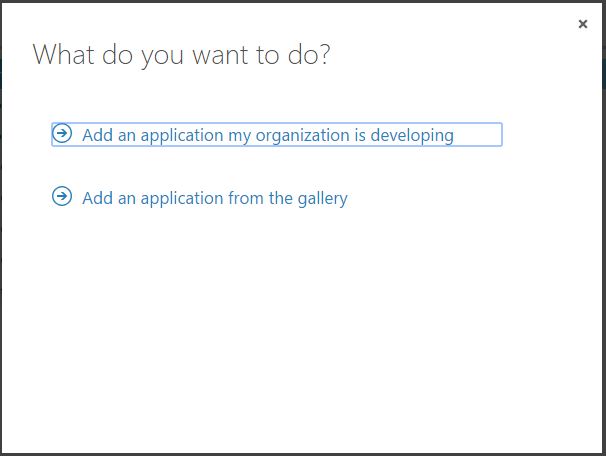
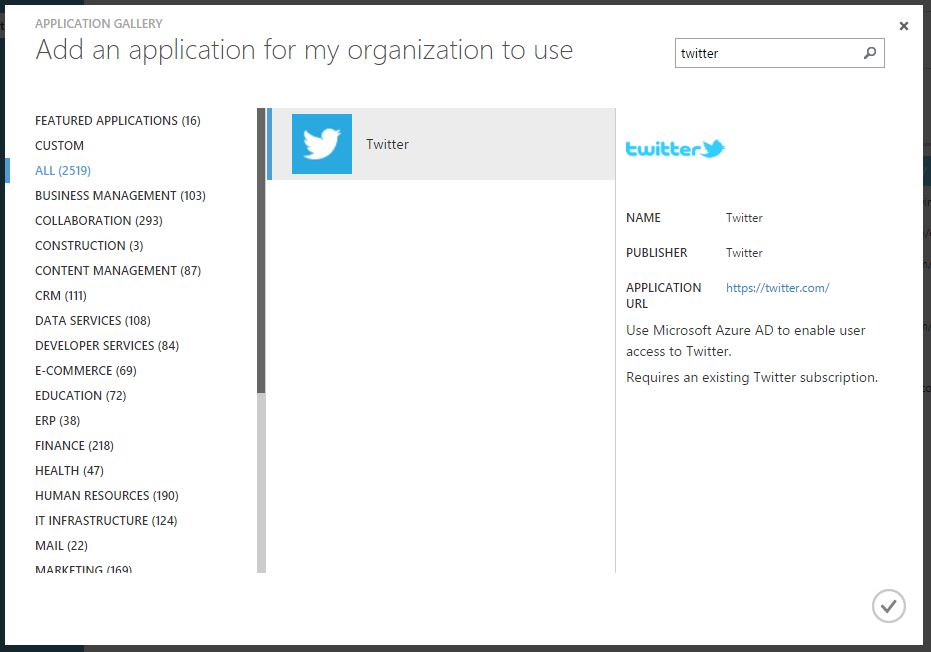
Next, we will select Add an application from the gallery.
As for this writing, November 12th 2015, there are 2519 SaaS applications ready to be added for your users. Next, we will search for Twitter.
Once the Twitter application has been selected, click the checkbox at the bottom right of the page.
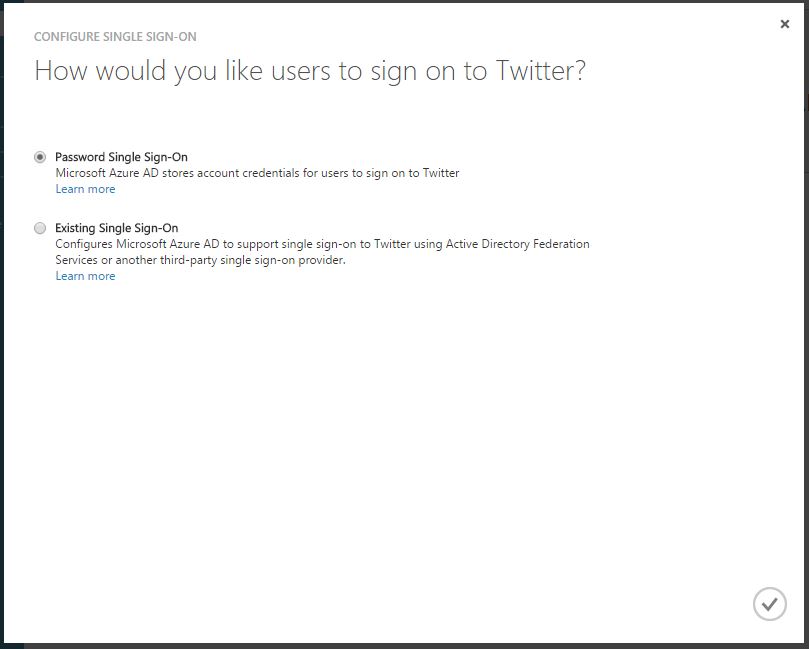
Now we can configure single sign-on for Twitter.
In this case, we have two choices: Password Single Sign-On or Existing Single Sign-On. Existing Single Sign-On enables users to log on to the SaaS application using their Azure AD user account. Password Single Sign-on enables users to be automatically logged in to the SaaS application using the SaaS application credentials. In this case, I will provide the "corporate credentials" to the Twitter account. Do not forget to click the checkmark at the bottom of the page.
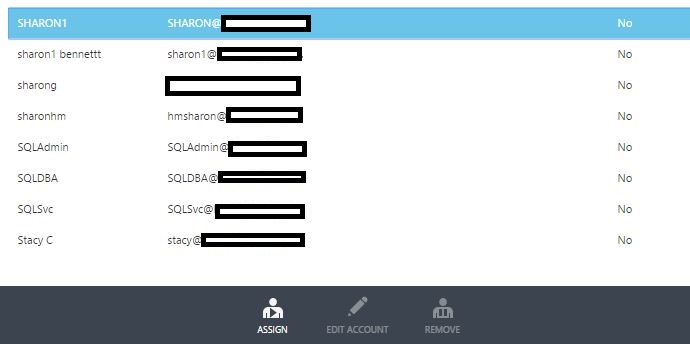
Next we will assign accounts that can access the application. Select the account or group that you would like to have access to the application, then click Assign at the bottom of the page.
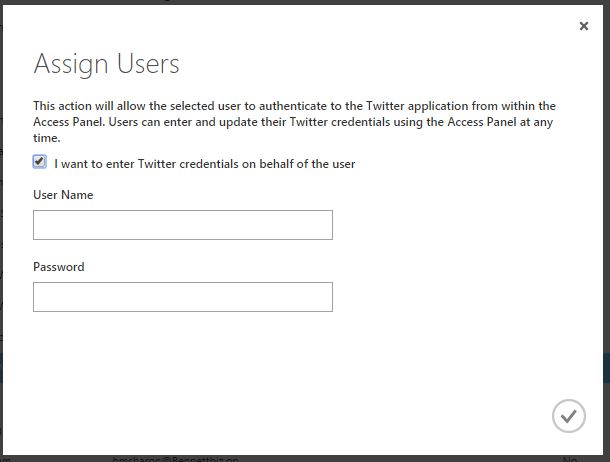
You will now be required to enter the credentials to the Twitter account on behalf of the user. When the user accesses Twitter via the Dashboard, they will be automatically logged in to the account. The user never sees the credentials, therefore protecting your SaaS application from misuse.
Twitter has now been added to the list of SaaS applications my company uses.
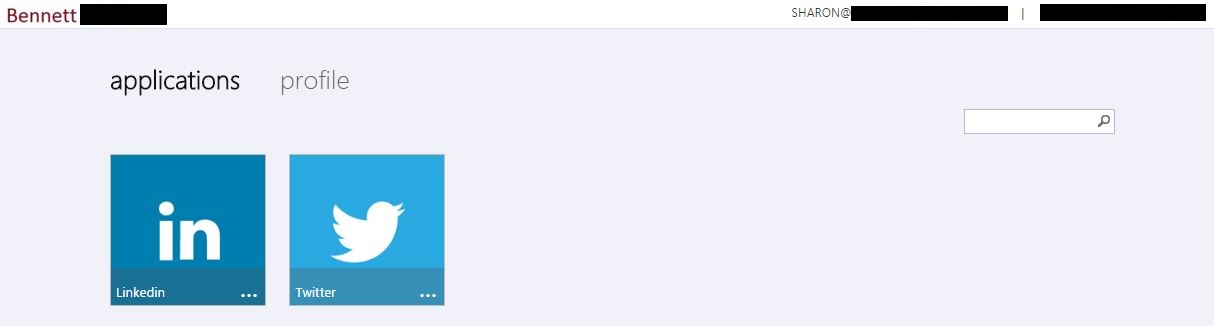
Now when the users access the company application portal, a list of assigned SaaS applications will be listed.
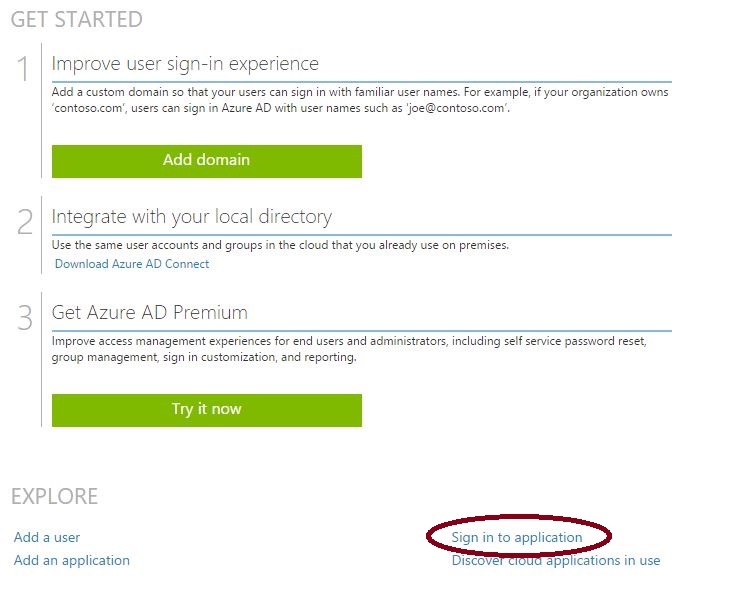
This portal can be accessed via the link on the Quick Start page.
In our example, when the user clicks the Twitter icon, they will be logged in to the company Twitter account automatically.
If our user leaves the company we can easily disable their corporate access to Twitter, preventing any unwanted content from the company account.
In a few short steps, you are now able to provide a quick and easy way for your users to log on to the company applications they need access to (and just as easily restrict access) in a simple easy-to-use web interface. Azure Active Directory is a powerful identity and management tool that can easily be overlooked in the Azure offering. Take a few moments and explore how Azure Active Directory can enable your users.