Step-By-Step: Protect physical servers with Azure Site Recovery – Part 2
Today we pickup right where we left off last week when we were walking through the steps to protect an on-prem physical server by setting up a recovery site in Azure. Of course as I mentioned last week. there are some great videos from Ignite and other sources that outline the benefits of Azure Recovery Services. you can see them at the following addresses.
- Hybrid Cloud Workloads: Disaster Recovery and High Availability
- Enterprise level Disaster Recovery with Azure Site recovery for fraction of the cost
- Best Practices for Deploying Disaster Recovery Services with Microsoft Azure Site Recovery
- Azure Site Recovery: Microsoft Azure As a Destination for Disaster Recovery
But for now let’s catch up to where we left off last week. Last Monday we took the following steps.
- Step 1: Created a Site Recovery Vault
- Step 2: Deployed a configuration server
- Step 3: Registered the configuration server in the vault
- Step 4: Set up and manage accounts
- Step 5: Deployed the master target server
Today we will complete this solution by taking the following steps.
- Step 6: Deploy the on-premises process server
- Step 7: Create a protection group
- Step 8: Set up machines you want to protect
- Step 9: Enable protection
You understand now why I split this post in 2 different articles.
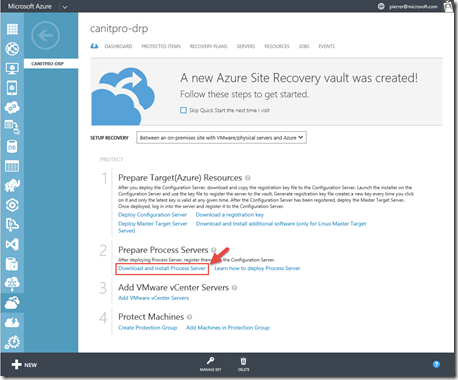
Step 6: Deploy the on-premises process server
This step will download, install the Process Server on a server located on the same network as the machines you will be protecting. We will install and register the Process Server with the Configuration Server we created last Monday using the same passphrase that we generated and saved during the Configuration Server setup.
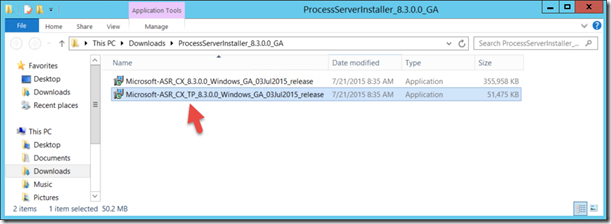
Logon to a server locally that will act as the Process Server. From that machine navigate to the Azure Portal, then to Azure Recovery Services, Click on your Recovery Vault and click Download and install Process Server. this will start the download of “ProcessServerInstaller_8.3.0.0_GA.zip” Please save it locally to be unzipped and executed.
Once you have downloaded and expanded the zip file you will end up with files. These files have different purposes. Microsoft-ASR_CX_TP_8.3.0.0_Windows_GA_03Jul2015_release installs third-party components needed for the deployment. Microsoft-ASR_CX_8.3.0.0_Windows_GA_03Jul2015_release is the bits themselves for the installation of the process server.
let’s install Microsoft-ASR_CX_TP_8.3.0.0_Windows_GA_03Jul2015_release by double clicking the file.
And click install in the dialogue box and finish when it completes. (fairly straight forward…)
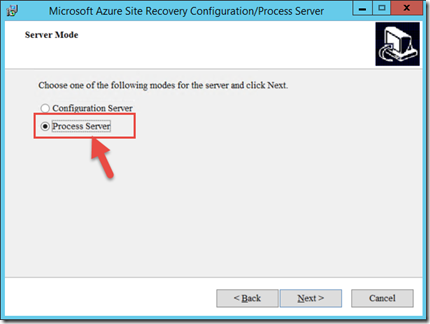
Once the pre-reqs are installed we’ll install the Process server (Microsoft-ASR_CX_8.3.0.0_Windows_GA_03Jul2015_release). CLick Next on the welcome page, and Select Process Server on the Server Mode page.
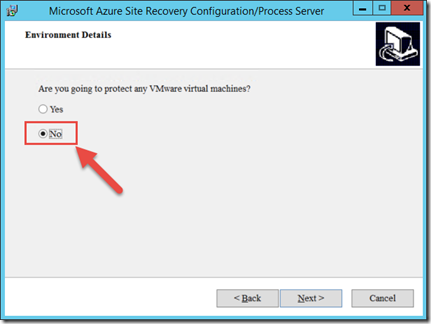
We will select “No” on the Environment Detail page since we are not protecting VMware machines in this post but physical servers.
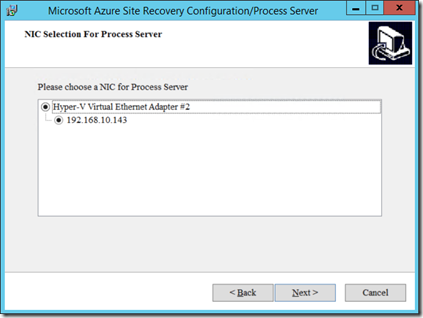
Select the NIC for the process server. in my case my test server only has one NIC. so the decision is easy.
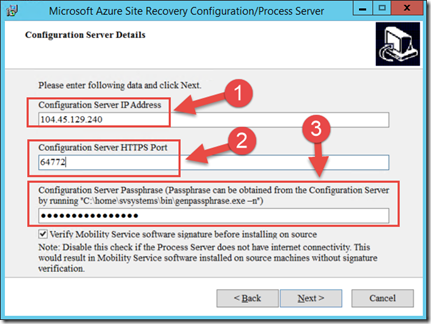
The Next page will ask you about Configuration Server Details. you will need to provide the following:
- The IP address and port. Specify the public virtual IP address (1) and mapped public HTTP endpoint (2) for the Configuration Server VM we created last Monday.
- Type in the passphrase of the configuration server. (3)
Clear Verify Mobility service software signature if you want to disable verification when you use automatic push to install the service. Signature verification needs internet connectivity from the process server.
Click Next.
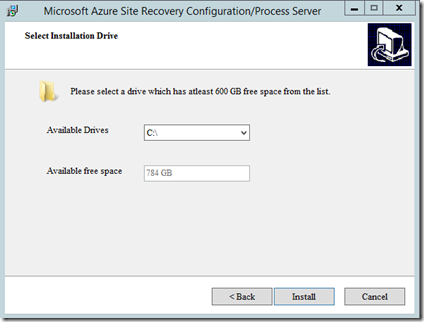
In the next page, select where you want the bits installed. In my case I am installing to the drive E: since the recommended size is 600Gb and my E: drive is an empty 2Tb drive.
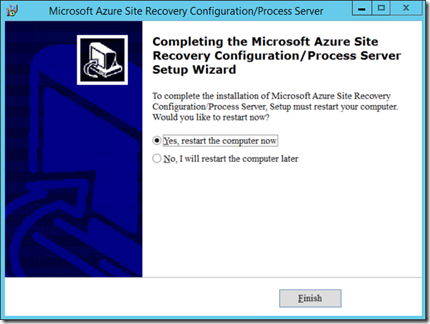
Select “restart the computer now” and click finish.
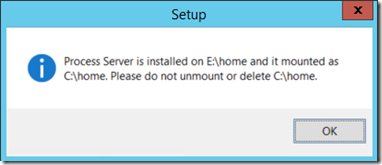
Please note that the install of the Process Server will mount the installation in my E: drive to a directory on the C: drive. The setup process will inform you of that fact before rebooting.
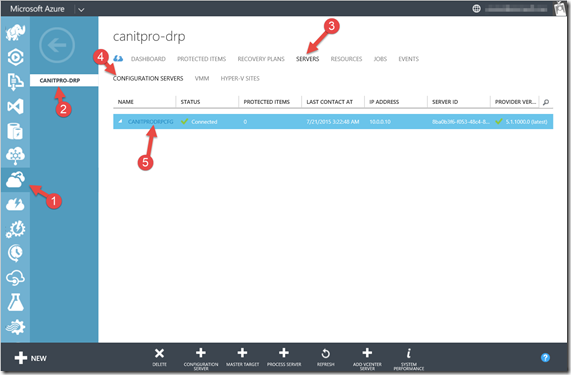
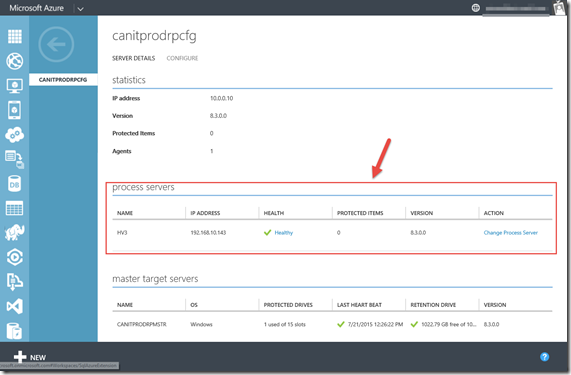
After the reboot, It can take up to 15 minutes after registration is complete. wait for 10-15 minutes and in the portal, in the Recovery Services page (1), in the Vault we created (2) on the Servers tab (3) , in the Configuration Servers page (4) click the configuration server (5) and check that the Process Server is listed as registered on the Server Details tab
as below.
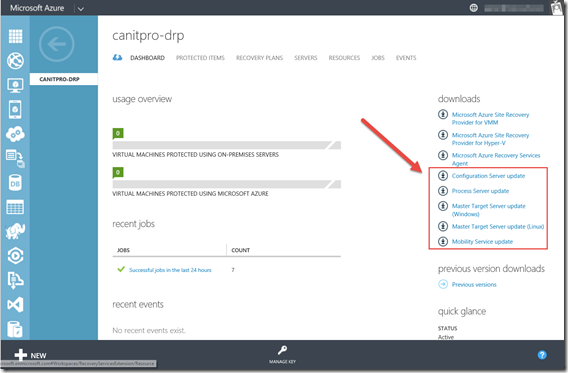
Before proceeding, now that we have our Azure Recovery Services servers setup. just make sure they are updated. On each server one by one in this order:
- Configuration server
- Process server
- Master target server
We will logon our Azure portal and in the Recovery Services Dashboard, we’ll download and install the appropriate update. (since we just installed most of these that should be OK but it’s a good habit to have)
Step 7: Create a protection group
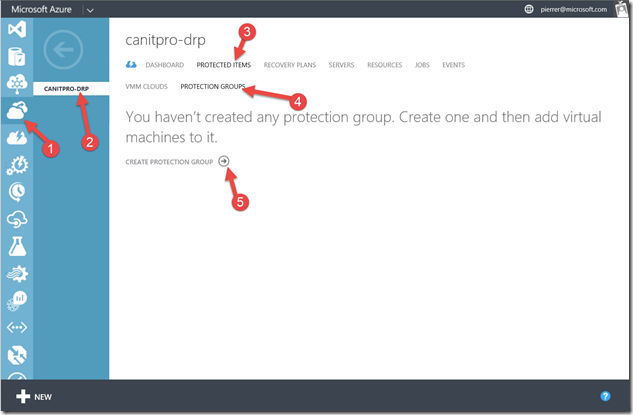
Logon the management portal in Azure and navigate to the Recovery Services (1) , select the recovery vault we created during our last post (2) , Open Protected Items (3) and Protection Group (4) and click to add a protection group (5) .
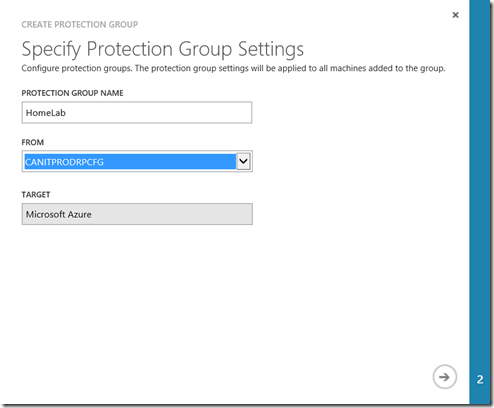
On the Specify Protection Group Settings page specify a name for the group and select the configuration server on which you want to create the group.
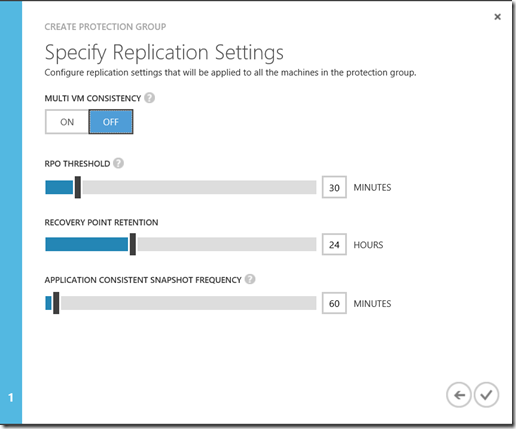
On the Specify Replication Settingspage configure the replication settings that will be used for all the machines in the group. for this test we will leave all the defaults.
Settings:
- Multi VM consistency: If you turn this on it creates shared application-consistent recovery points across the machines in the protection group. This setting is most relevant when all of the machines in the protection group are running the same workload. All machines will be recovered to the same data point. Only available for Windows servers. In my case this is not required.
- RPO threshold: Alerts will be generated when the continuous data protection replication RPO exceeds the configured RPO threshold value.
- Recovery point retention: Specifies the retention window. Protected machines can be recovered to any point within this window.
- Application-consistent snapshot frequency: Specifies how frequently recovery points containing application-consistent snapshots will be created.
You can monitor the protection group as they're created on the Protected Items page.
Step 8: Set up machines you want to protect
You'll need to install the Mobility service the servers you want to protect. As Always, you can do this manually or automated. When you add a server to a protection group the Mobility service is automatically pushed and installed on that machine by the process server. to ensure that this will happen, you need to configure the Windows firewall to allow File and Printer Sharing and Windows Management Instrumentation.
Under Windows Firewall settings, select the option “Allow an app or feature through Firewall” and select the applications as shown below. For machines that belong to a domain you can configure the firewall policy with a Group Policy Object.
The account used to perform the push installation must be in the Administrators group on the machine you want to protect. These credentials are only used for push installation of the Mobility service and you'll provide them when you add a machine to a protection group.
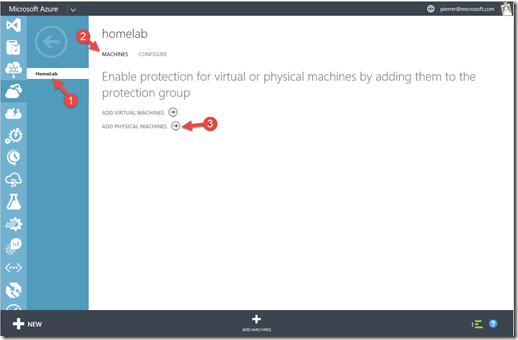
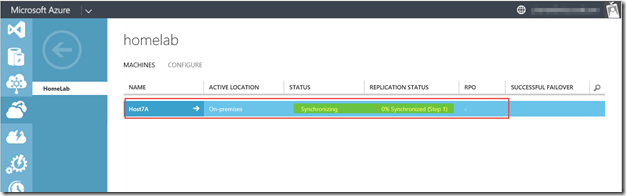
Let’s add our source server to the protection group. In our protection Group (1) we’ll click on Machine (2) and then on Add Physical Machine (3).
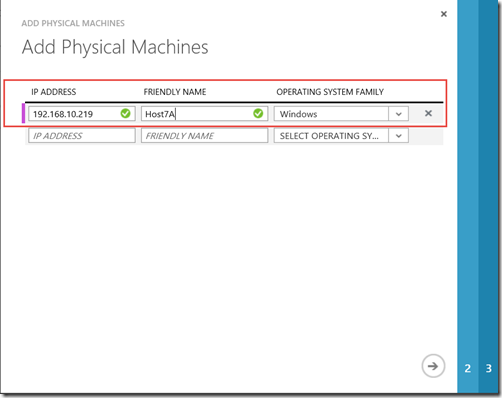
In the “Add Physical Machines” page , fill in the required info for the server you want to protect.
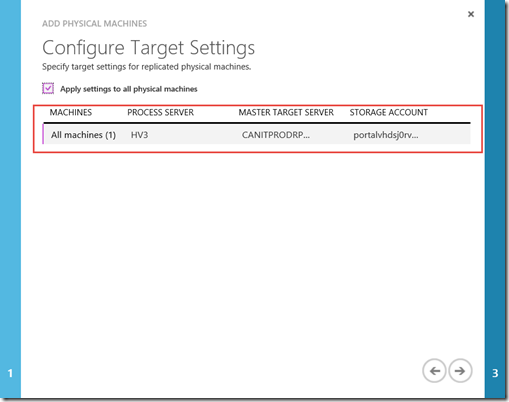
On the next page you will need to configure which Process server, Master Target Server and Storage account you will want to use.
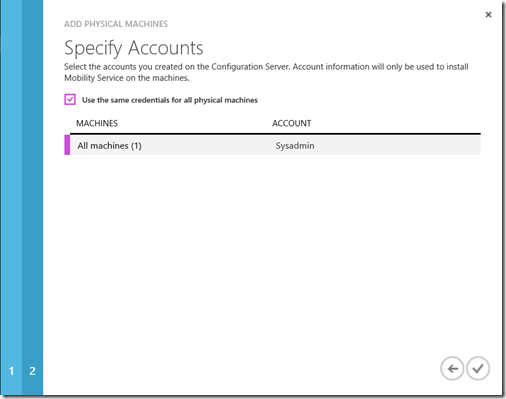
On the last page, you'll need to specify the credentials to be used to install the Mobility Service on the machine. (note: the credentials were provided to the system in Step 4: Set up and manage accounts.)
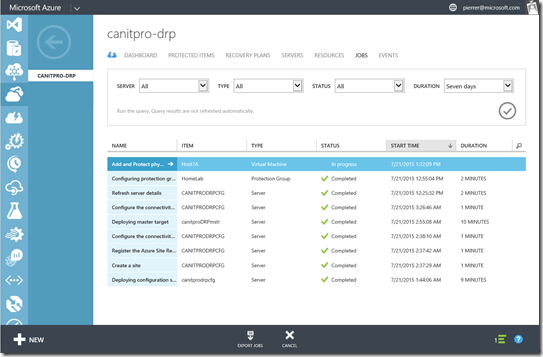
You’ll now have to wait for the push install to be complete. you can monitor the results in the JOBS tab of the Recovery Services Vault.
There you go. you can now use Azure as your very own Disaster Recovery Site and stop worrying about what you’ll do in the event of a disaster.
Next week we’ll actually initiate a Fail over and a Fail back.
I hope this was helpful. as always, feel free to leave comments and let me know if this is the kind of info you’re looking for.
Cheers!
Pierre Roman
@pierreroman