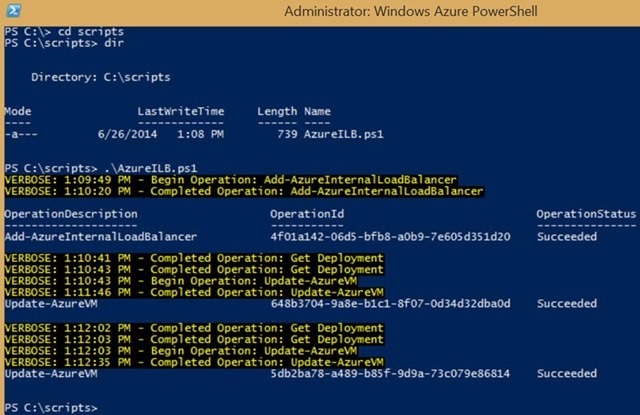
Step-By-Step: Configuring AD FS Servers in an Internal Load-Balanced Set in Azure for Office365 Single Sign-On
After completing the 2 previous posts entitled, Step-By-Step: Enabling A Primary AD FS Server in Azure for Office365 Single Sign-On and Step-By-Step: Enabling A Secondary AD FS 3.0 Server in Azure for Office365 Single Sign-On, you now have our two AD FS 3.0 servers setup in the same cloud service and installed into an AD FS farm configuration. Next step would be to load balance them. Azure has a load balancer built into the product and just requires configuration. Please note that you will want to use the Azure internal load balancer and not want these servers to have an external end point. Follow the process below, so that you can configure the ILB, servers and endpoints.
Goals
1. Connect to Windows Azure with PowerShell
2. Create Azure Internal Load-Balanced Set
3. Add Servers to the Internal Load-Balanced Set
4. Add End Points to the Internal Load-Balanced Set
5. Test
Assumptions:
- Azure account is setup
- Directory Sync is activated, setup and running
- VPN connection setup from Azure to your on-premise network
- Primary and Secondary AD FS servers are setup (see previous posts in this series)
Reference this TechNet Article
Connect to Windows Azure with PowerShell
If you are unsure how to or have never connected to Windows Azure with PowerShell, please reference the following article. This will guide you to install the tools and connect with PowerShell
- Open the Start Screen
- Right Click Windows Azure PowerShell and Run as administrator
- Click Yes to the UAC
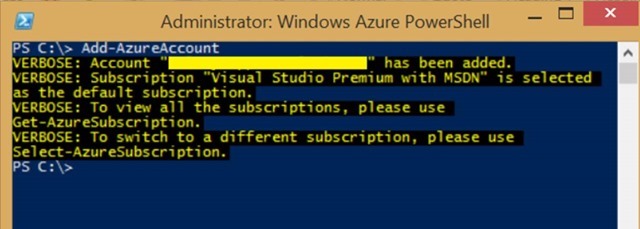
- Type Add-AzureAccount
- Press Enter
- Enter email address used login to your Azure account
- Click Continue
- Enter email address and password used login to your Azure account
- Click Continue
- Azure authenticates your account and then takes you back to the PowerShell window.
Create the Internal Load-Balanced Set Instance
- Before we can continue, we need to gather some information. This information is used to set variables in the PowerShell command that will be used to create the ILB instance
Cloud Service Name - This was created prior to creating the first AD FS 3.0 Virtual Machine and can be found in the Azure Management Portal under Cloud Services
Internal Load-Balanced Instance Name – This is a name that is used to reference the ILB Set
Subnet Name – This was created when Azure Networking was created and can be found in the Azure Management Portal under Networking
IP Address for the Internal Load-Balanced Instance – This can be set or automatically generated
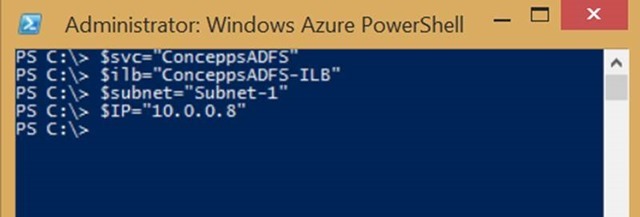
- Set the variables in PowerShell
$svc="ConceppsADFS"
$ilb="ConceppsADFS-ILB"
$subnet="Subnet-1"
$IP="10.0.0.8"
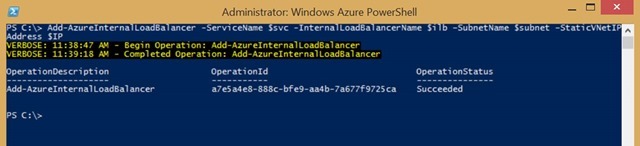
- Execute the command in PowerShell
Add-AzureInternalLoadBalancer -ServiceName $svc -InternalLoadBalancerName $ilb –SubnetName $subnet –StaticVNetIPAddress $IP
Add End Points to the Internal Load-Balanced Set
Below is a script that will set the variables, create the end points and update the Virtual Machines with the configuration.
$svc="ConceppsADFS"
$ilb="ConceppsADFS-ILB"
$prot="tcp"
$locport=443
$pubport=443
$epname="ADFS01"
$vmname="ConceppsADFS01"
Get-AzureVM –ServiceName $svc –Name $vmname | Add-AzureEndpoint -Name $epname –LBSetName “ADFS-SSL” -Protocol $prot -LocalPort $locport -PublicPort $pubport –DefaultProbe -InternalLoadBalancerName $ilb | Update-AzureVM
$epname="ADFS02"
$vmname="ConceppsADFS02"
Get-AzureVM –ServiceName $svc –Name $vmname | Add-AzureEndpoint -Name $epname –LBSetName “ADFS-SSL” -Protocol $prot -LocalPort $locport -PublicPort $pubport –DefaultProbe -InternalLoadBalancerName $ilb | Update-AzureVM
Add DNS Record
Now that we have our farm configured and the servers are load balanced, we need to ensure that the clients can get to them using the virtual IP of the Internal Load-Balanced Set.
In the steps above we created an Internal Load-Balanced set with the IP of 10.0.0.8. We now need to create an A record in the internal DNS, with a name of STS that points to the VIP. In my case sts.office365supportlab.com points at 10.0.0.8
Testing AD FS Sign-On
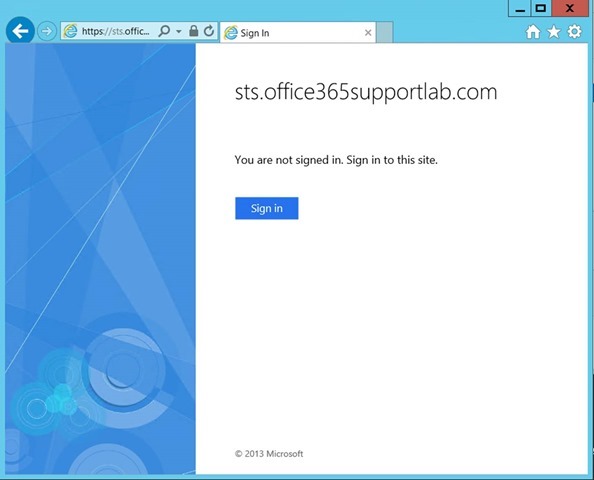
- Open IE
- Browse to the URL - https://sts.domain.com /adfs/ls/IdpInitiatedSignon.aspx
- Click Sign in
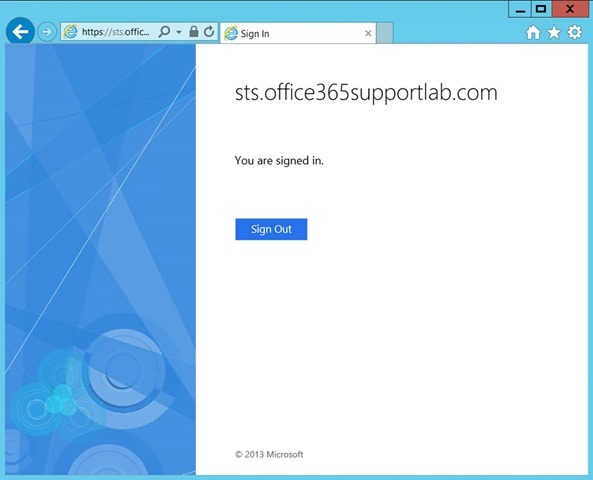
Testing Server High Availability
Shutdown the AD FS Servers one at a time and check that you can still access AD FS with each server offline. This will test the failure of losing one of the servers in the ILB set.
We are now setup with a highly available AD FS solution for all internal users. Continue on with the series to setup the Web Application Proxies (AD FS Proxy) so that the external users have access. Be sure to view Expanding Office 365 with Enterprise Mobility Suite on Microsoft Virtual Academy as a great next step.