Step-By-Step: Enable Multi-Factor Authentication in Azure
Hello Folks,
lately I’ve been covering Azure and active directory pretty often. It’s because I believe that it’s crucial for us IT Pros to learn as much as we can about the cloud and the value it can bring our enterprises.
In this next post we will do a simple setup of Multi-Factor Authentication (MFA) using a call back scheme to validate the user’s identity. but I do recommend the following MVA modules as primer for any Azure conversation.
- Automating the Cloud with Azure Automation
- Moving to Hybrid Cloud with Microsoft Azure
- DevOps: An IT Pro Guide
- Transform the Datacenter Immersion V3
- Microsoft Azure IaaS Deep Dive Jump Start
- Mobile Apps to IoT: Connected Devices with Windows Azure
- Get Started with Windows Azure Today Jump Start
- Windows Azure for IT Pros Jump Start
- Windows Azure Security Overview
MFA
Azure MFA helps safeguard access to data and applications while meeting user demand for a simple sign-in process. It delivers strong authentication via a range of easy verification options—phone call, text message, or mobile app notification—allowing users to choose the method they prefer, however today we will setup the phone call method. It also helps protect your business with security monitoring and machine learning-based reports that identify inconsistent log-in patterns. Real-time alerts notify your IT department of suspicious account credentials, to help mitigate potential threats
Create Multi-Factor Authentication provider
Before we can configure how we use MFA we must make sure we have an MFA provider. If you have Office365 you already have this and you don’t ned anything else, if you have AD Premium you’re good also. but you want to validate what you already are paying for to avoid double billing.
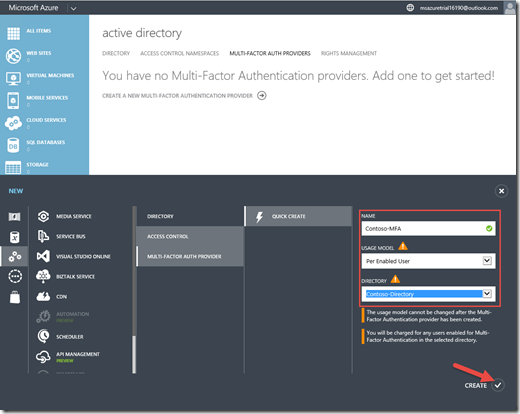
that being said…. let’s do it. In Microsoft Azure, navigate to ACTIVE DIRECTORY.
2- Click MULTI-FACTOR AUTH PROVIDERS, and then click CREATE A NEW MULTI-FACTOR AUTHENTICATION PROVIDER. In NAME, type Contoso-MFA, select the usage model (this will affect your billing and it cannot be changed afterwards. so make sure to select the appropriate one) In my case I selected “Per Enabled User”, selected the Contoso-Directory that I had already created and synced with my on premise AD , and then click CREATE.
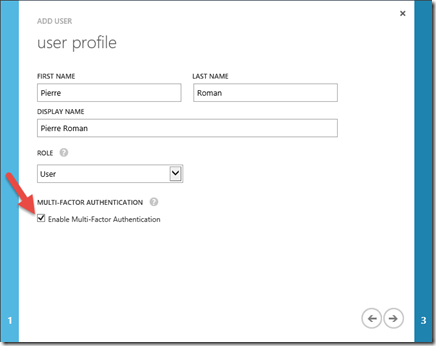
Enable Users in my Directory to use MFA
If you create a new users in your directory all you will need is to do is select the “Enable Multi-Factor Authentication” check box.
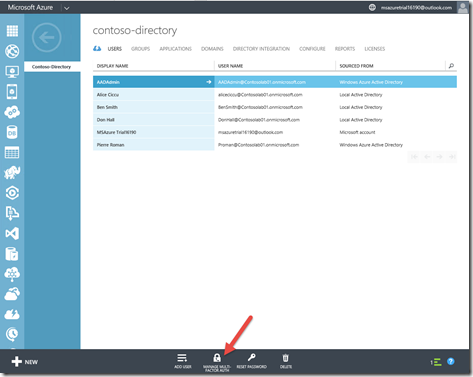
1- For existing users, you will need to activate the MFA. To do that, navigate to your directory in Azure and select the “Manage Multi Factor Auth” in the action bar at the bottom.
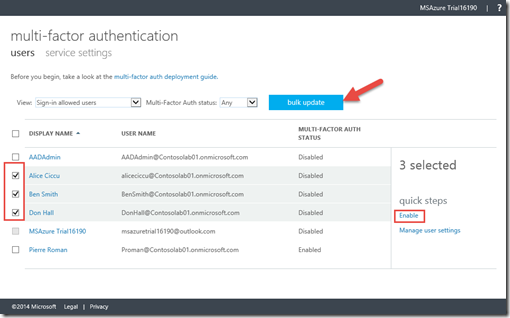
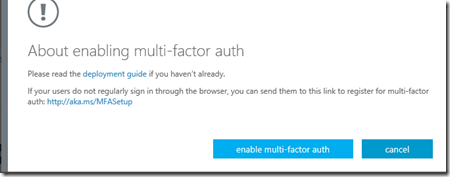
2- Once the Manage Multi Factor Authentication page as loaded, you can select all the users you want to enable MFA for, click Enable and click Bulk update to start the process.
3- It will ask you to confirm and it will provide links to more info about the deployment. click “enable multi-factor Auth”
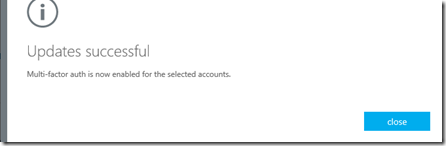
4- and Click ‘Close” to complete.
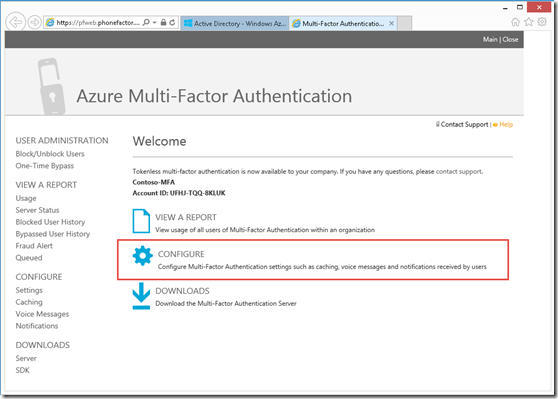
Configure The MFA provider
1-
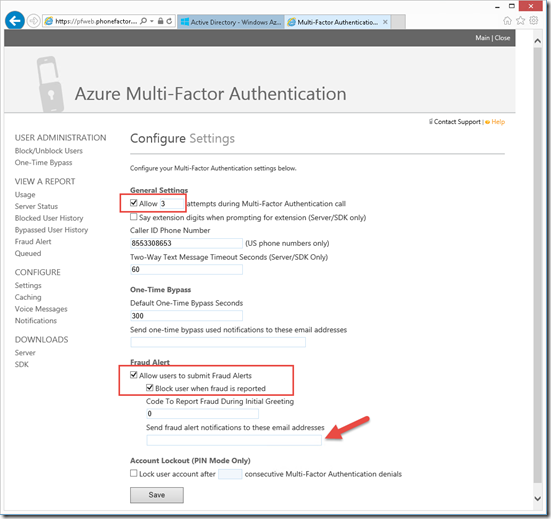
Configure the users MFA settings.
Now that my users in my directory has been configured. that I have configured how the MFA will contact me. Now each users that were enabled will need to configure there MFA settings on the next logon.
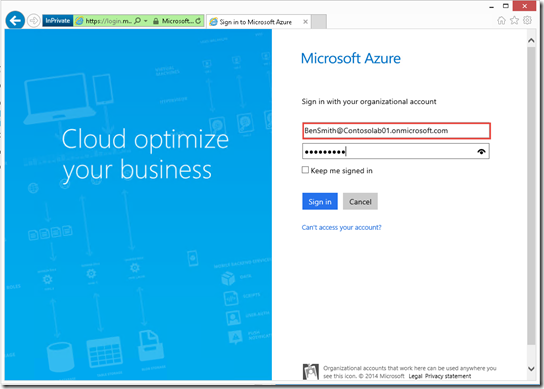
1- I logged on to Azure using the <“BenSmith@Contosolab01.onmicrosoft.com>” address and authenticated using the password that was already setup.
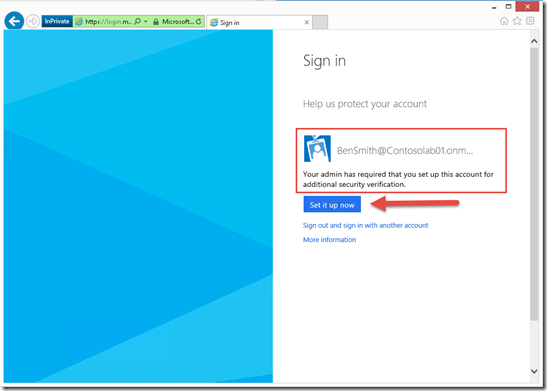
2- Automatically, the system will prompt the user if the MFA setup is needed.
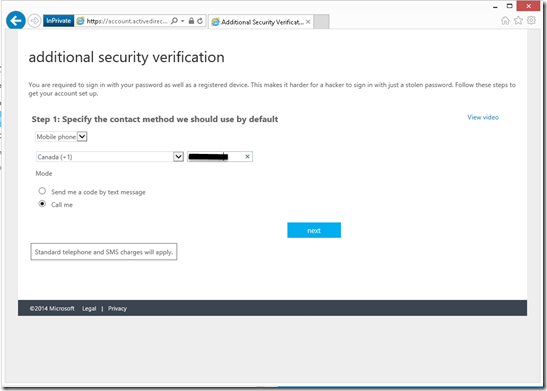
3- As part of the setup Ben needed to enter a phone number that the system will call to validate the login for this user. (notice that I blocked my number since I don’t want midnight calls at my house…)
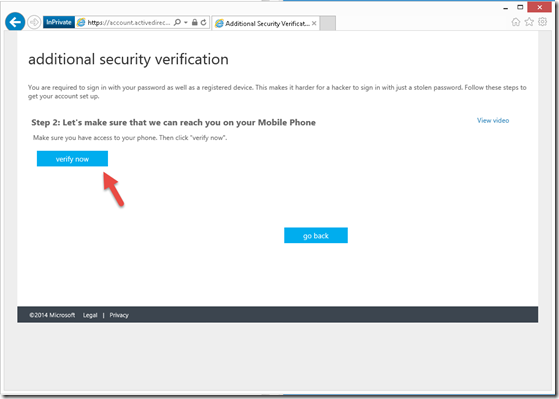
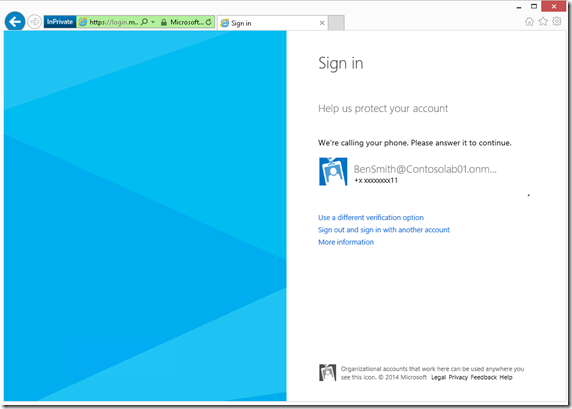
4- By clicking “verify now”, the system will call your phone and ask for you to verify the connection.
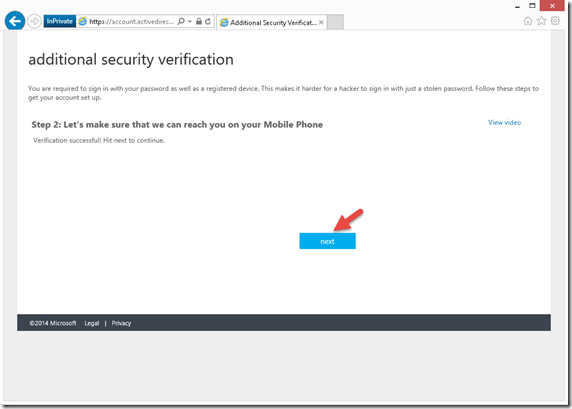
5- After this is done, click Next to continue
6- at this point we will keep the MFA setup pretty simple. We will look at multiple options in the upcoming weeks.
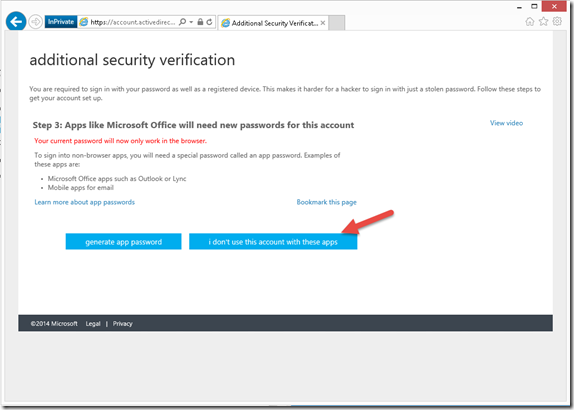
7- Once this is completed. you will received a phone call every time you logon to this account to validate that is is you.
I hope this helps. Feel free to send us comments and let us know what scenarios you want us to explore for you.
Cheers!
Pierre Roman, MCITP , ITIL | IT Pro AdvisorTwitter | Facebook | LinkedIn