Step-By-Step: Deploying PowerShell Web Access
Hello Folks,
Last night after delivering an IT Camp for a partner organization, I went out with some friends and we were discussing remote management capabilities of Windows Server 2012 R2. ( I know, I'm loose downtown Montreal, and we are talking about remote management…. I’m a geek… what can I say? )
Anyway, It got me thinking about not having to RDP in a remote server in order to use PowerShell to manage my environment. Because, really, that’s the way I've been doing it. it’s easy, it works… Why fix what is not broken? Well just for kicks I setup a PowerShell Web Access Gateway in my environment. Actually I put it in the Azure public Facing Subnet I setup a few weeks ago.
- Step-By-Step: Create a Site-to-Site VPN between your network and Azure
- Step-By-Step: Setting up Network Access Control Lists (ACLs) in Azure
I did add two endpoints to my VM in Azure to allow access to HTTP and HTTPS. (port 80 and 443)
Windows PowerShell Web Access acts as a gateway that provides a web-based Windows PowerShell console that is targeted at a remote computer. It enables IT Pros to run Windows PowerShell commands and scripts from a Windows PowerShell console in a web browser, with no Windows PowerShell, remote management software, or browser plug-in installation necessary on the client device.
All that is required to run the web-based Windows PowerShell console is a properly-configured Windows PowerShell Web Access gateway, and a client device browser that supports JavaScript® and accepts cookies.
Step 1: Getting Started
- Download Windows Server 2012 R2
- Setup you test lab by creating the following computers or VMs
Active Directory Domain Services domain controller (DC)
A server running Windows Server 2012 R2 for the gateway
a client to connect from… in my case a Windows 8.1 enterprise machine
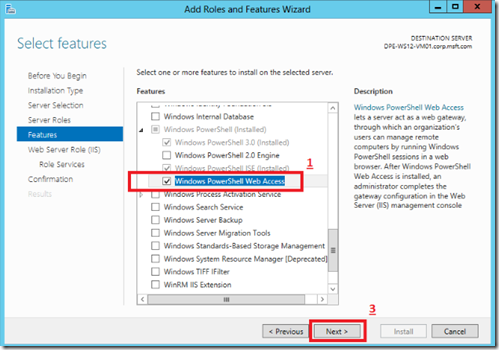
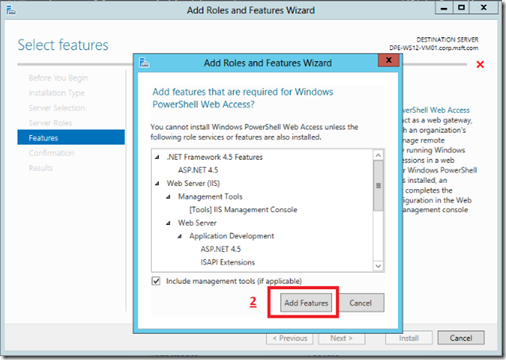
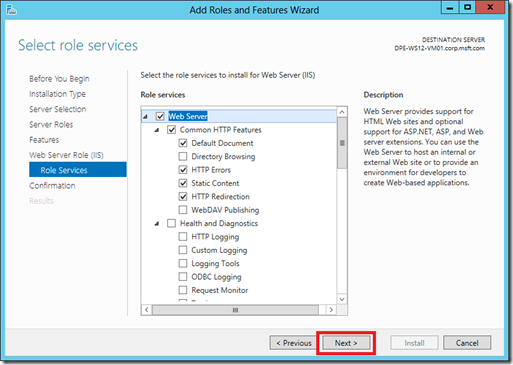
Step 2: Install Windows PowerShell Web Access
Using Server Manager and the Add Roles and Services, I installed the Windows PowerShell Web Access features and accepted the additional features that the wizard mentioned.
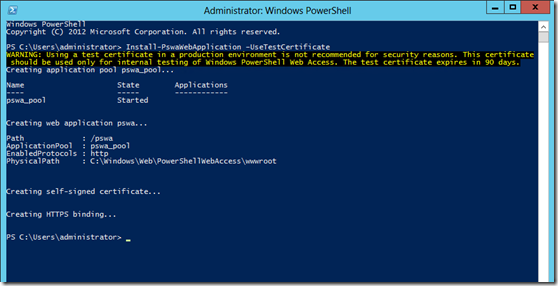
Step 3: Configure the gateway
Configure PowerShell Web Access Gateway using the following PowerShell Cmdlet.
- Install-PswaWebApplication –UseTestCertificate
The UseTestCertificate parameter should only be used in a private test environment. For a secure production environment, I recommend using a valid certificate that has been signed by a CA.
Running the cmdlet installs the Windows PowerShell Web Access web application within the IIS Default Web Site container. The cmdlet creates the infrastructure required to run Windows PowerShell Web Access on the default website, https://<server_name>/pswa. To install the web application in a different website, provide the website name by adding the WebSiteName parameter. To change the name of the web application (the default is pswa), add the WebApplicationName parameter.
Step 4: Configure a restrictive authorization rule
After Windows PowerShell Web Access is installed and the gateway is configured, users can open the sign-in page in a browser, but they cannot sign in until the Windows PowerShell Web Access administrator grants users access explicitly. Windows PowerShell Web Access access control is managed by using the set of Windows PowerShell cmdlets described in the following table. There is no comparable GUI for adding or managing authorization rules.
| Name | Description | Parameters |
|---|---|---|
Adds a new authorization rule to the Windows PowerShell Web Access authorization rule set. |
|
|
Removes a specified authorization rule from Windows PowerShell Web Access. |
|
|
Returns a set of Windows PowerShell Web Access authorization rules. When it is used without parameters, the cmdlet returns all rules. |
|
|
Evaluates authorization rules to determine if a specific user, computer, or session configuration access request is authorized. By default, if no parameters are added, the cmdlet evaluates all authorization rules. By adding parameters, administrators can specify an authorization rule or a subset of rules to test. |
|
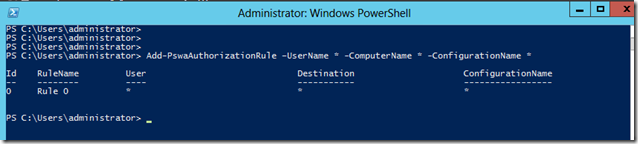
For this lab we will use a wide open authorization rule. but I do recommend you lock that stuff down in production. Better safe than sorry. To add a restrictive authorization rule that would allow any users access to any computer we’ll use the following command.
Add-PswaAuthorizationRule –UserName * -ComputerName * -ConfigurationName *
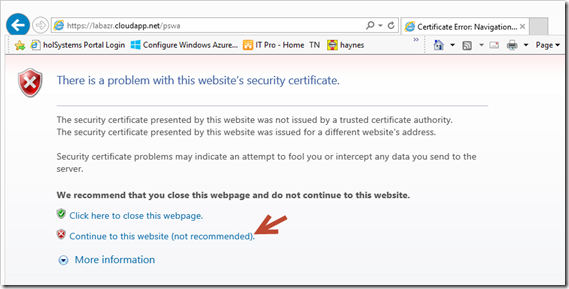
Now that it’s all configured, I can access the gateway from any machine on the internet. However since we used a self signed certificate we will get the following error when connecting to the site.
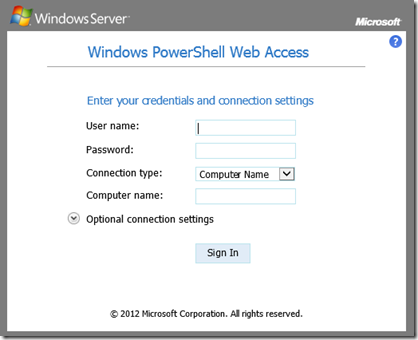
Just select Continue to this website. and the page will open asking you for your credentials, and connection information to open the PowerShell gateway to that box.
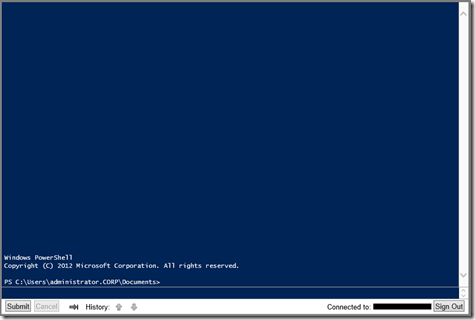
Once the information is entered you’ll be connected through to browser to a PowerShell session on the target computer you defined.
There you go. Another way of setting up remote management. You can even manage your environment using commodity tablets. That’s BYOD.
Cheers!
Pierre Roman | Technology Evangelist
Twitter | Facebook | LinkedIn