Windows 8.1 Preview Security Re-visited
Hello Folks,
A while back Anthony Bartolo wrote on this site about the Enterprise Enhancements For Windows 8.1 there were a lot of information in that post regarding the following points:
- Support for BYOD (Bring Your Own Device)
- Increased capabilities in Mobility
- Increased Security features and capabilities
- Enhanced User Experience
Following that post I wrote about the steps you need to setup and manage the “Boot directly to the Desktop in Windows 8.1 Preview”. That post generated a lot of side conversation regarding the difference between a registry hack and managed way of doing things. But it also started a conversation on LinkedIn where it was asked if we could dive a little deeper in the security enhancements of Windows 8.1 for enterprise.
So here goes…
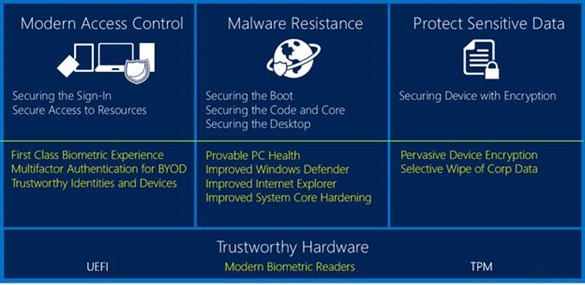
Here are the areas in Windows 8.1 where we made significant improvements.
- Malware Resistance
- Data protection
- Modern Access Control.
These three areas sitting on top of Trustworthy Hardware.
Let’s dive in each of these areas.
Malware Resistance
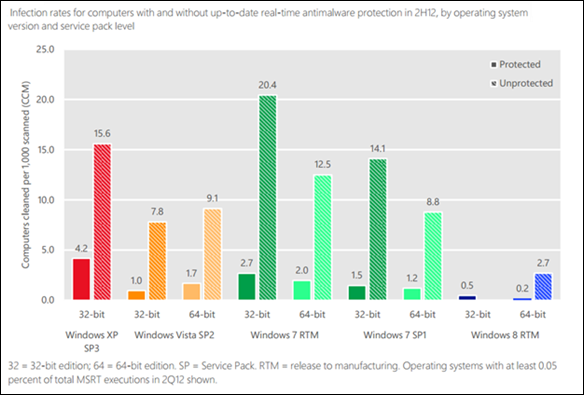
According to the Microsoft Security Intelligence Report, Volume 14, July through December, 2012
Running Unprotected: Measuring the Benefits of Real-Time Security Software,
If you are running Windows 8 or Windows 8.1, you are approximately 6 times less likely to be infected to be infected by malware then if you were running Windows 7. 21 times less likely to be infected then if you are running Windows XP (which will no longer be supported after April 2014).
In the real world just like in cyber world there are 2 type of change
- Evolution
- Revolution
As security threats continue to evolve, we evolves our countermeasure. Bad find a security hole to exploit, we patch the hole. They develop a new method we develop protection for that new method….. Wash, rinse, repeat. Still… We invest in our built-in malware protection.
- We’ve improved Windows Defender: We are introducing high performance behaviour monitoring to Windows Defender that enable Defender to detect certain bad behaviours in memory, the registry, or the file system; even before signatures have been created.
- We’ve improved Internet Explorer: Currently, malicious websites can sometimes access sensitive data by exploiting vulnerabilities in binary extensions (such as ActiveX controls). These are executed immediately, bypassing the antimalware solution. In Windows 8.1, we offer an API for Internet Explorer that enables anti-malware solutions to make a security determination before a binary extension is loaded. In addition, Enhanced Protection Mode is on by default in Internet Explorer 11, helping to ensure safer browsing.
Data Protection
We’ve also put a lot of thought into how businesses can protect their data even when it resides on employees’ personal devices.
- Pervasive Device Encryption: With Windows 8.1, device encryption is now available on all editions of Windows for devices that support Connected Standby (InstantGo). If the device supports Connected Standby, device encryption can be automatically enabled. As Connected Standby will be available on the vast majority of devices, this functionality will be pervasive throughout the enterprise. Windows 8.1 Pro and Windows 8.1 Enterprise also benefit from the full feature functionality of BitLocker, including BitLocker To Go, additional key protectors such as the network key protector, automatic recovery key escrow to Active Directory, and other powerful enterprise features ensuring a physical drive won’t be compromised when machines are lost or stolen.
- Selective Wipe of Corporate Data: With Windows 8.1, we introduce Remote Data Removal which will allow an IT department to wipe corporate data (e.g. emails, attachments, corporate data that came from Work Folders) off a BYOD device without affecting personal data.
Modern Access Control.
With Windows 8.1, we’ve focused a lot of attention on the controls that IT departments can place on devices to restrict who can physically access a device.
- First Class Biometrics: It’s no secret creating and remembering passwords is a nuisance at best and a gaping security vulnerability for companies at worst. We believe that biometrics is the solution to replace passwords over time. While biometric capabilities have been available since Windows XP, innovations in Windows 8.1, along with the new hardware coming from our hardware partners, will make your fingerprint easier and more secure than anything you’ve used before.
- Biometrics goes beyond swipe, which we previously supported, to capacitive full fingerprint and can be set up on any Windows 8.1 device through Modern Settings using a standard, consistent Windows experience.
- Before, we supported biometrics when a customer first signed into the device. Now any time a user sees a Windows credential prompt, he or she can use biometrics, effectively eliminating the password for logging into secure sites and in-app user account validations.
- Finally, we have created new APIs to support biometrics on the WinRT platform. Using biometrics in a Windows Store app is as simple as making one API call.
- Multifactor Authentication for BYOD: With Windows 8.1, we are building on the work done in Windows 8 to streamline the Virtual Smart Card (VSC) management process. In Windows 8.1 we have added support for enrolment and management via WinRT APIs so all of these scenarios can be supported through a modern app experience. With this, businesses will have more flexibility and control over how devices connect to internal networks and make it easier to securely allow access to personal devices in a BYOD environment.
- Trustworthy Identities and Devices: We have recently seen how Public Key Infrastructures (PKIs) or Certificate Authorities can be targeted by hackers, leaving a system vulnerable to attack. In Windows 8.1, we increase the trustworthiness of the PKI by helping manage and drive certificate best practices and adherence to standards within the ecosystem.
- We have a service now that scans the top two million SSL/TLS sites on the web daily to look for anomalies or bad practices and will notify partners (certificate authorities or companies that had a fraudulent certificate issued in their name) quickly when we see issues.
- We have also taken the “assumption factor” away from the server side of private key verification. For example, if an employee has malware on their personal device, the malware can intercept the private key during enrolment or renewal, effectively compromising your identity. With Windows 8.1, a server or service can require proof (attestation) that private certificates and keys are protected by hardware. If that can’t be proven, access is denied.
Trustworthy Hardware
Often in a BYOD scenario, if an employee buys a new computer, it can be hit-or-miss as to whether the device will have all the tools baked in that an IT department needs to make sure any data on that device is secure. With Windows 8.1 we take away the guesswork.
- The Trusted Platform Module: TPM is a hardware security device or chip that provides a number of crypto functions, including securely storing keys and performing cryptographic measurements. It’s a great tool for the enterprise, but has been an optional piece of technology for consumer devices.
- TPM 2.0 is required for all Connected Standby (InstantGo) devices which will ensure modern devices are ready for BYOD scenarios. And in Windows 8.1, we expand on the strategy behind TPM, with features such as key attestation, which allows you to ensure your private key is safely bound to hardware instead of malware, and virtual smartcard management WinRT APIs to enable Windows Store apps to set up and manage virtual smartcards.
- We are working towards requiring TPM 2.0 on all devices by January 2015. This helps IT departments be confident that the device their employees bring to work are fully capable of complying with corporate security policies.
keep in mind that these improvements are in addition to all the ones we discussed in a post back in may called Windows 8: More beautiful, more flexible and more secure
in the coming weeks I’ll dive into each of these improvements and look at how we implement those in an enterprise settings.
let’s keep the conversation going. it’s the only way we learn.
Cheers!
Pierre Roman, MCITP, ITIL | IT Pro Advisor
Twitter | Facebook | LinkedIn
![Signature_thumb[1] Signature_thumb[1]](https://msdntnarchive.blob.core.windows.net/media/TNBlogsFS/prod.evol.blogs.technet.com/CommunityServer.Blogs.Components.WeblogFiles/00/00/00/48/12/metablogapi/8407.Signature_thumb1_thumb_5A8E0390.jpg)