Deploying your MFA Server On Premises that is integrated with ADFS server (Windows Server 2012 R2)
You can install MFA Server on ADFS server on premises. The installation steps are documented in these KB articles https://azure.microsoft.com/en-us/documentation/articles/multi-factor-authentication-get-started-server/ and https://azure.microsoft.com/en-us/documentation/articles/multi-factor-authentication-get-started-adfs-w2k12/ , respectively.
To install the Azure Multi-Factor Authentication Server locally on the same server as AD FS
Download and install the Azure Multi-Factor Authentication Server on your AD FS federation server.
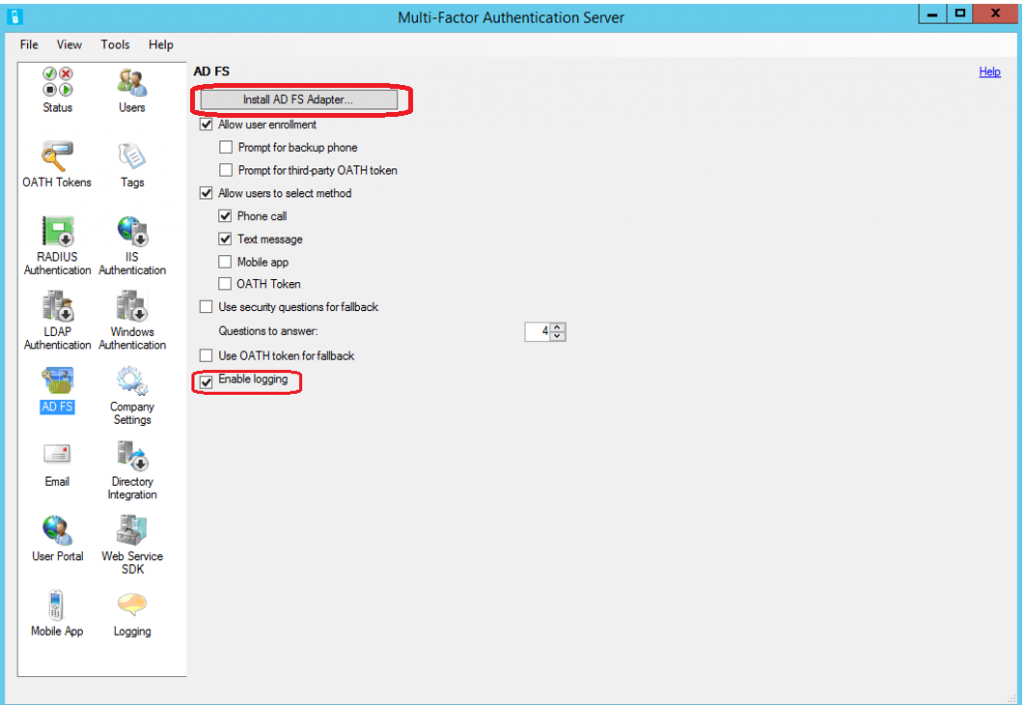
In the Azure Multi-Factor Authentication Server user interface, select the AD FS icon and select options for Allow user enrollment and Allow users to select method.
Select any additional options.
Click Install AD FS Adapter.
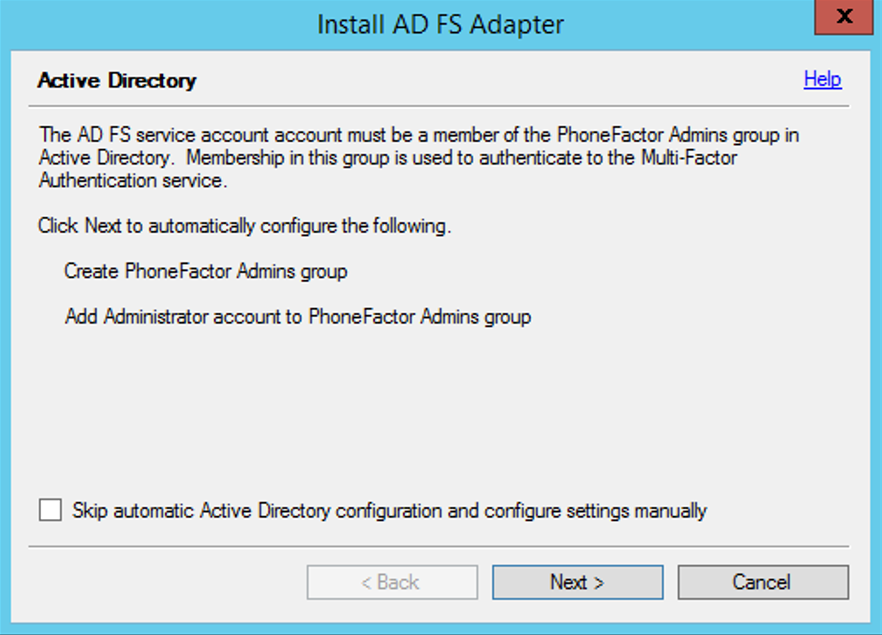
If the computer is joined to a domain and the Active Directory configuration for securing communication between the AD FS Adapter and the Multi-Factor Authentication service is incomplete, the Active Directory step will be displayed. Click the Next button to automatically complete this configuration or check the Skip automatic Active Directory configuration and configure settings manually checkbox and click Next.
If the computer is not joined to a domain and the Local Group configuration for securing communication between the AD FS Adapter and the Multi-Factor Authentication service is incomplete, the Local Group step will be displayed. Click the Next button to automatically complete this configuration or check the Skip automatic Local Group configuration and configure settings manually checkbox and click Next.
This will bring up the installation wizard, click Next to allow the Azure Multi-Factor Authentication Server to create the PhoneFactor Admins group and add the AD FS service account to the PhoneFactor Admins group.
On the Launch Installer step, click Next.
In the Multi-Factor Authentication AD FS Adapter installer, click Next.
Click Close when the installation has completed.
Now that the adapter has been installed, it must be registered with the AD FS. Open Windows PowerShell and run the following: C:\Program Files\Multi-Factor Authentication Server\Register-MultiFactorAuthenticationAdfsAdapter.ps1 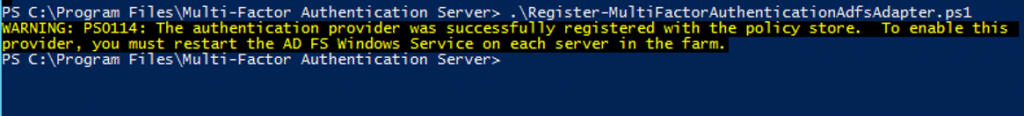
Close the Windows PowerShell command prompt and launch the AD FS Management console from the Tools menu of the Server Manager to finally configure Azure MFA as the additional authentication method.
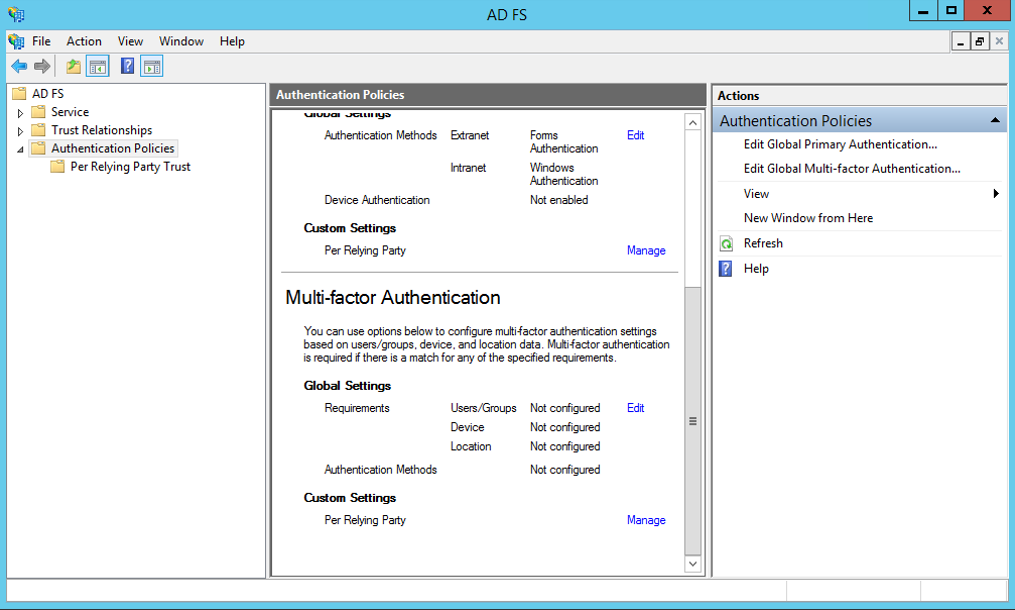
Navigate to the Authentication Policies node, scroll down in the middle pane to the Multi-factor Authentication section.
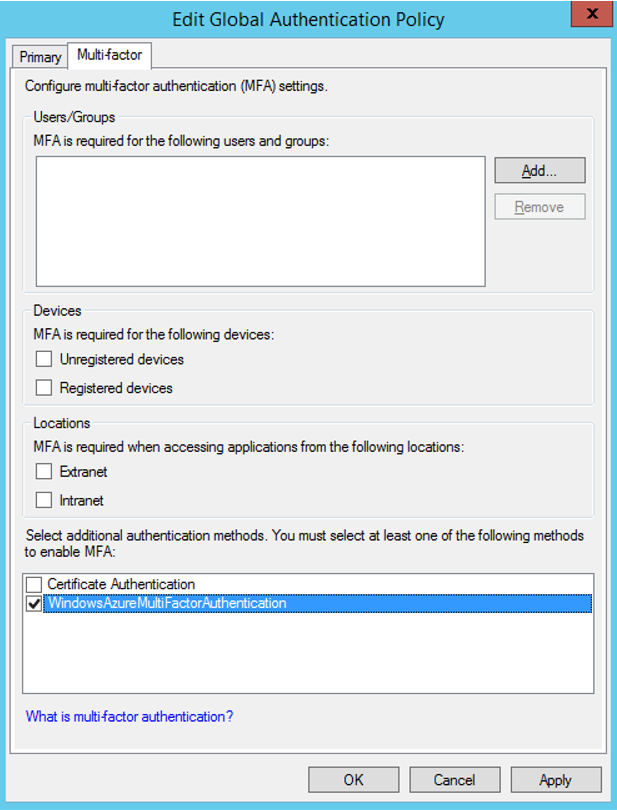
Click Edit next to the Global Settings sub-section. An Edit Global Authentication Policy window brings up.
Select WindowsAzureMultiFactorAuthentication as an additional authentication method, and then click OK.
To set up the multi-factor authentication policy for the Office 365 Relying Party Trust, proceed with the following steps:
- Open an elevated Windows PowerShell command prompt and run the following command to retrieve the Office 365 relying party:
$rp = Get-AdfsRelyingPartyTrust –Name "Microsoft Office 365 Identity Platform"
- Run the following command to specify the claim rule: (only perform MFA on ADFS if the request is not from intranet and the request is coming from web browser)
$MfaClaimTriggerRule = 'c:[Type == "https://schemas.microsoft.com/2012/01/devicecontext/claims/insidecorporatenetwork", value == "false"]
&& c1:[Type == "https://schemas.microsoft.com/2012/01/requestcontext/claims/x-ms-endpoint-absolute-path", Value =~ "(/adfs/ls)|(/adfs/oauth2)"]
=> issue(Type = "https://schemas.microsoft.com/ws/2008/06/identity/claims/authenticationmethod", Value = "https://schemas.microsoft.com/claims/multipleauthn");'
- Run the following command to set the claim rule on the Office 365 relying party:
Set-AdfsRelyingPartyTrust –TargetRelyingParty $rp –AdditionalAuthenticationRules $MfaClaimTriggerRule
The default multi-factor authentication behavior for federated Azure AD/Office 365 tenants has been recently set to occur in the cloud where in the past it was set to occur on-premises. Operations has backfilled to ensure customers that were using multi-factor authentication on-premises will continue to use their on-premises MFA Server.
To perform multi-factor authentication on-premises for contoso.com, run the following command:
Set-MsolDomainFederationSettings -DomainName contoso.com -SupportsMFA $true
Where SupportsMFA as true means that Azure AD will redirect the user to AD FS for multi-factor authentication if multi-factor authentication is required and a claim of type “***https://schemas.microsoft.com/claims/authnmethodsreferences***” with the value “***https://schemas.microsoft.com/claims/multipleauthn***”, which is so-called the MFA claim, is missing.
NOTE: Please be careful about one important caveat. If you are going to deploy and configure On Premises Azure MFA Server integrated with AD FS server, you should not enable Azure AD MFA for Azure AD users additionally at the same time, even if you can technically do this. Otherwise this will make things very complicated while handling claims. On Premises MFA Server and Azure AD MFA are two separate distinct mechanisms which are not aware of each other.
In order to be on the safe side, you can implicitly disable Azure AD MFA for all users within AD FS claims, by performing the following configuration on ADFS.
To enable the claim to be sent from ADFS to Azure, follow these steps:
Open the AD FS Management console on your ADFS Server.
Select AD FS, then Trust Relationships, and then Relying Party Trust
Right click on “Microsoft Office 365 Identity Platform” and select Edit Claim Rules
Click Add Rule on the Issuance Transform Rules tab
Select the rule template Pass Through or Filter an Incoming Claim and click next
In the incoming claim type, select Authentication Methods References and leave Pass through all claim values selected and click Finish
Click OK to save the Claims Rules
Now any Azure service that requires Multi-Factor will honor the https://schemas.microsoft.com/claims/authnmethodsreferences claim value set to https://schemas.microsoft.com/claims/multipleauthn from ADFS to Azure AD MFA so that Azure AD MFA will never trigger on Azure AD MFA after ADFS provider based MFA and this will prevent any potential loops.