Export all NGS rules in ARM for all Subscriptions
You can associate different NSGs to a VM (or NIC, depending on the deployment model) and the subnet that a NIC or VM is bound to. When that happens, all network access rules are applied to the traffic, by priority in each NSG, in the following order:
Inbound traffic
- NSG applied to subnet. If subnet NSG has a matching rule to deny traffic, packet will be dropped here.NSG applied to NIC (Resource Manager) or VM (classic).
- If VM\NIC NSG has a matching rule to deny traffic, packet will be dropped at VM\NIC, although subnet NSG has a matching rule to allow traffic.
Outbound traffic
- NSG applied to NIC (Resource Manager) or VM (classic). If VM\NIC NSG has a matching rule to deny traffic, packet will be dropped here.NSG applied to subnet.
- If subnet NSG has a matching rule to deny traffic, packet will be dropped here, although VM\NIC NSG has a matching rule to allow traffic.
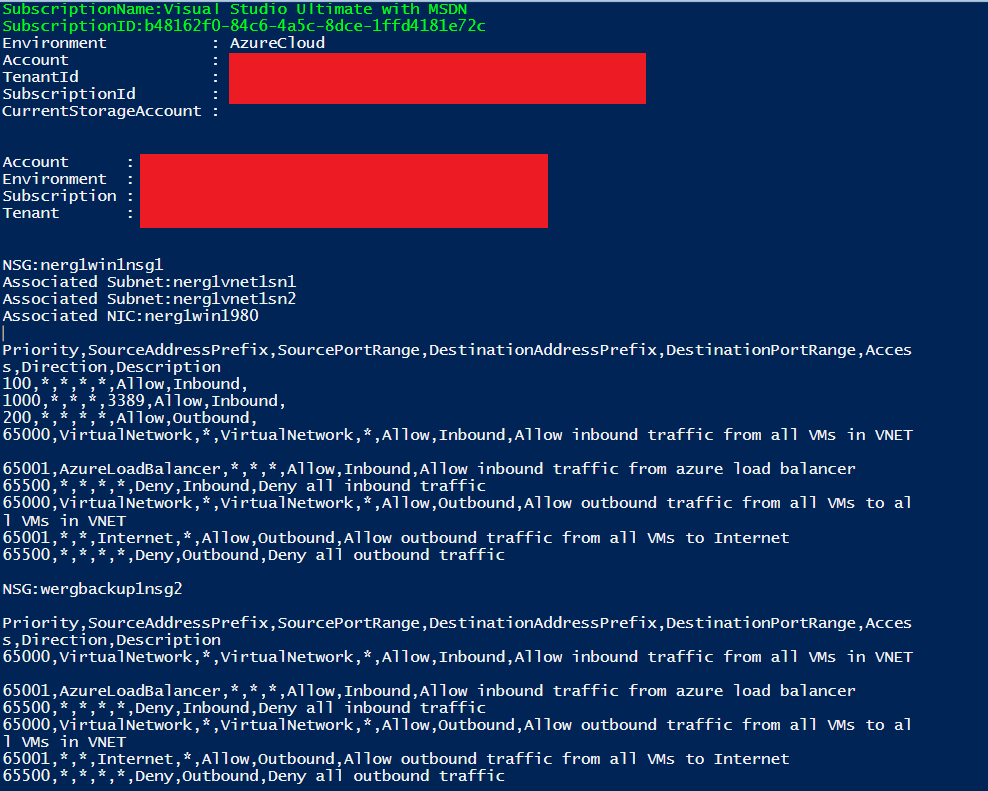
Run the following PowerShell script to export all NSG rules in ARM portal for all subscriptions. The exported output can be easily copied and pasted to Excel for further analysis. Sample screenshot is provided below at the bottom of the blog.
Add-AzureRmAccount
clear-host
$output1 = 'Exporting NSGs from all subscriptions in Azure Resource Manager' + "`r`n"
$subs = Get-AzureRMSubscription
$output1 = "`r`n";
foreach ($subscription in $subs){
$output1 += "`r`n";
$output1 += (‘SubscriptionName:’ + $subscription.Name) + "`r`n";
$output1 += (‘SubscriptionID:’ + $subscription.Id)+ "`r`n";
(Select-AzureRMSubscription -SubscriptionId $subscription.Id) > 0;
$rgs = Get-AzureRmNetworkSecurityGroup
foreach ($rg in $rgs){
$output1 += "`r`n";
$output1 += (‘NSG:’ + $rg.Name) + "`r`n";
$subnets = $rg.Subnets;
foreach ($sn in $subnets){
$arrayid = $sn.id.Split(‘/’).count – 1;
$snarray = $sn.id.Split(‘/’);
$output1 += (‘Associated Subnet:’ + $snarray[$arrayid]) + "`r`n";
};
$nics = $rg.NetworkInterfaces;
foreach ($nic in $nics){
$arrayid = $nic.id.Split(‘/’).count – 1;
$snarray = $nic.id.Split(‘/’);
$output1 += (‘Associated NIC:’ + $snarray[$arrayid]) + "`r`n";
};
$rules = Get-AzureRmNetworkSecurityRuleConfig -NetworkSecurityGroup $rg;
$output1 += "`r`n";
$output1 += (‘Priority’ + ‘,’ + ‘SourceAddressPrefix’ + ‘,’ + ‘SourcePortRange’ + ‘,’ + ‘DestinationAddressPrefix’ + ‘,’ + ‘DestinationPortRange’ + ‘,’ + ‘Access’ + ‘,’ + ‘Direction’ + ‘,’ + ‘Description’) + "`r`n";
foreach ($rule in $rules){
$output1 += ($rule.Priority.ToString() + ‘,’ + $rule.SourceAddressPrefix + ‘,’ + $rule.SourcePortRange + ‘,’ + $rule.DestinationAddressPrefix + ‘,’ + $rule.DestinationPortRange + ‘,’ + $rule.Access + ‘,’ + $rule.Direction + ‘,’ + $rule.Description) + "`r`n";
};
$rules = $rg.DefaultSecurityRules;
foreach ($rule in $rules){
$output1 += ($rule.Priority.ToString() + ‘,’ + $rule.SourceAddressPrefix + ‘,’ + $rule.SourcePortRange + ‘,’ + $rule.DestinationAddressPrefix + ‘,’ + $rule.DestinationPortRange + ‘,’ + $rule.Access + ‘,’ + $rule.Direction + ‘,’ + $rule.Description) + "`r`n";
};
};
};
Write-Output $output1
The expected output would be like below: