Windows Azure and Virtual Networking – Getting Started–Step–by-Step (31 Days of Windows Servers (VMs) in the Cloud–Part 10 of 31)
https://aka.ms/IaaSSeries is where you can catch up or review the previous posts in the 31 Days of Windows Servers (VMs) in the Cloud series
Yesterday’s blog post introduced Windows Azure Virtual Networks, so after reading that post, the next logical question is “How do I get started?” The first step (if you haven’t already done so) is to get a Windows Azure Trial Subscription so you can start to get familiar with Windows Azure and the Windows Azure Portal where you can create virtual machines, set up and configure the Virtual Network to your organization, and much, much more. Another great step is to sign up for Microsoft Virtual Academy where you can take FREE e-Learning courses on Windows Azure as well.
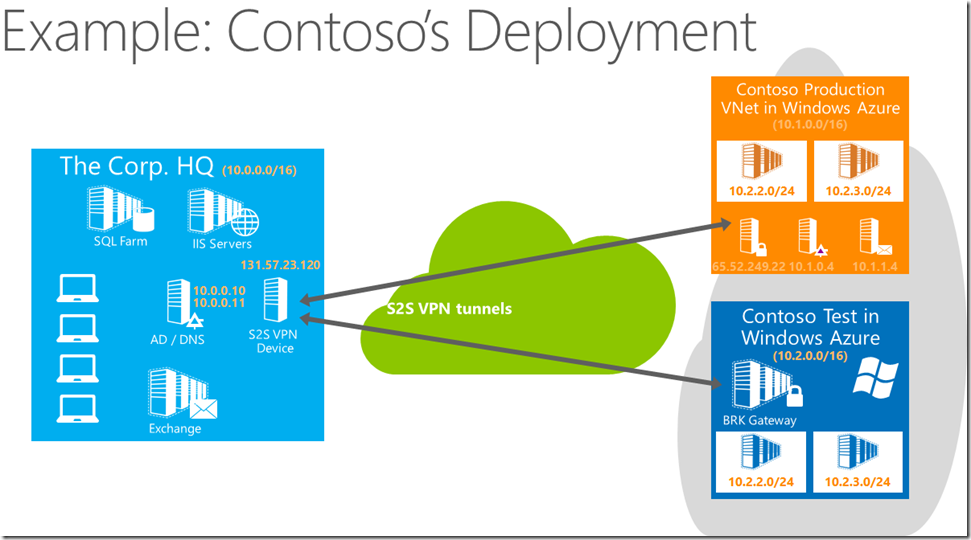
Before we get started, it’s important to set the stage of what we’re trying to accomplish. The Windows Azure Virtual Network you are about to create establishes a Site to Site (S2S) VPN between your company’s network and the Windows Azure Cloud Service using the steps outlined below, and requires that you have an already installed VPN device on your premise. The list of currently supported VPN devices is located here. Windows Azure currently supports up to 5 S2S VPN tunnels, allowing you to have multiple Virtual Networks hosted in Windows Azure, such as a Test Network and a Production Network.
So let’s get started.
To create a virtual network that connects to your company's network:
Log in to the Windows Azure (Preview) Management Portal.
In the lower left-hand corner of the screen, click New.
In the navigation pane, click Network, and then click Custom Create.
On the Virtual Network Details screen, enter the following information, and then click the next arrow.
NAME: Type YourVirtualNetwork.
AFFINITY GROUP: From the drop-down list, select Create a new affinity group. Affinity groups are a way to physically group Windows Azure services together at the same data center to increase performance. Only one virtual network can be assigned an affinity group.
REGION: From the drop-down list, select the desired region. Your virtual network will be created at a datacenter located in the specified region.
AFFINITY GROUP NAME: Type YourAffinityGroup.
On the Address Space and Subnets screen, enter the following information, and then click the next arrow. Address space must be a private address range, specified in CIDR notation 10.0.0.0/8, 172.16.0.0/12, or 192.168.0.0/16 (as specified by RFC 1918).
NOTE: After adding each address space, click the plus button.
ADDRESS SPACE: Type 10.4.0.0/16.
SUBNETS: Enter the following:
- FrontEndSubnet, 10.4.2.0/24
- BackEndSubnet, 10.4.3.0/24
- ADDNSSubnet, 10.4.4.0/24
On the DNS Servers and Local Network screen, enter the following information, and then click the forward arrow.
- DNS SERVERS: Type YourDNS, 10.1.0.4.
- Configure connection to local network: Check this box.
- GATEWAY SUBNET: Type 10.4.1.0/24.
- LOCAL NETWORK: Select the default Create a new local network.
On the Create New Local Network screen, enter the following information, and then click the check mark in the lower right-hand corner. Your virtual network will be created in a few minutes.
NOTE: You get the VPN Device IP Address from your network administrator.
NAME: Type YourCorpHQ.
VPN DEVICE IP ADDRESS: Enter the public IP address of your VPN device. The device should not be behind a NAT. For more information about VPN devices, see About VPN Devices for Virtual Network.
ADDRESS SPACE: Type 10.1.0.0/16.
You now have a virtual network in Windows Azure, which you can see on the portal's Virtual Network tab.
Start the Gateway
To start the gateway:
When your virtual network has been created, the networks screen will show the Status is Created.
In the Name column, click YourVirtualNetwork to open the dashboard.
On the Dashboard page, on the bottom of the page, click Create Gateway. When prompted to confirm you want the gateway created, click YES.
When the gateway creation starts, you will see the message as shown in the screenshot below.
It may take up to 15 minutes for the gateway to be created.
After the gateway has been created, you need to gather some information to send to your network administrator so they can configure the VPN device. The next steps walk you through this process.
On the dashboard, copy the Gateway IP Address:
Get the Shared Key. Click VIEW KEY at the bottom of the dashboard, and then copy the SHARED KEY in the dialog box.
Download the VPN configuration file. On the dashboard, click DOWNLOAD.
On the Download VPN Device Config Script dialog, select the vendor, platform, and operating system for your company's VPN device. Click the check button and save the file.
For additional supported VPN devices and script templates, see About VPN Devices for Virtual Network.
Send your network administrator the following information:
- Gateway IP address
- Shared key
- VPN configuration script
Configure the VPN Device (Network Administrator)
This procedure should be done by your network administrator. Because each VPN device is different, this is only a high-level procedure.
You can get the VPN configuration script from the Management Portal or from the About VPN Devices for Virtual Network section of the MSDN library.
For more information, see Establish a Site-to-Site VPN Connection and your VPN device documentation.
This procedure assumes the following:
- The VPN device has been configured at your company.
To configure the VPN device:
Modify the VPN configuration script. You will configure the following:
a. Security policies
b. Incoming tunnel
c. Outgoing tunnel
Run the modified VPN configuration script to configure your VPN device.
Test your connection by running one of the following commands:
Cisco ASA
Cisco ISR/ASR
Juniper SSG/ISG
Juniper SRX/J
Check main mode SAs
show crypto isakmp sa
show crypto isakmp sa
get ike cookie
show security ike security-association
Check quick mode SAs
show crypto ipsec sa
show crypto ipsec sa
get sa
show security ipsec security-association
Once the Virtual Network tests out, you’re ready to go.
Enjoy!
Next Steps:
Sign up for a FREE Microsoft Virtual Academy subscription to learn more about Windows Azure.
Read the other posts in the 31 Days of Windows Servers (VMs) in the Cloud Series by visiting https://aka.ms/IaaSSeries